Create IAM Role for CodeBuild and CodePipeline
Overview
In this step, we will create an IAM Role. This IAM Role will be used by AWS CodeBuild and CodePipeline.
Content
Access IAM
On the left navigation bar, select Policies
Choose Create Policies.
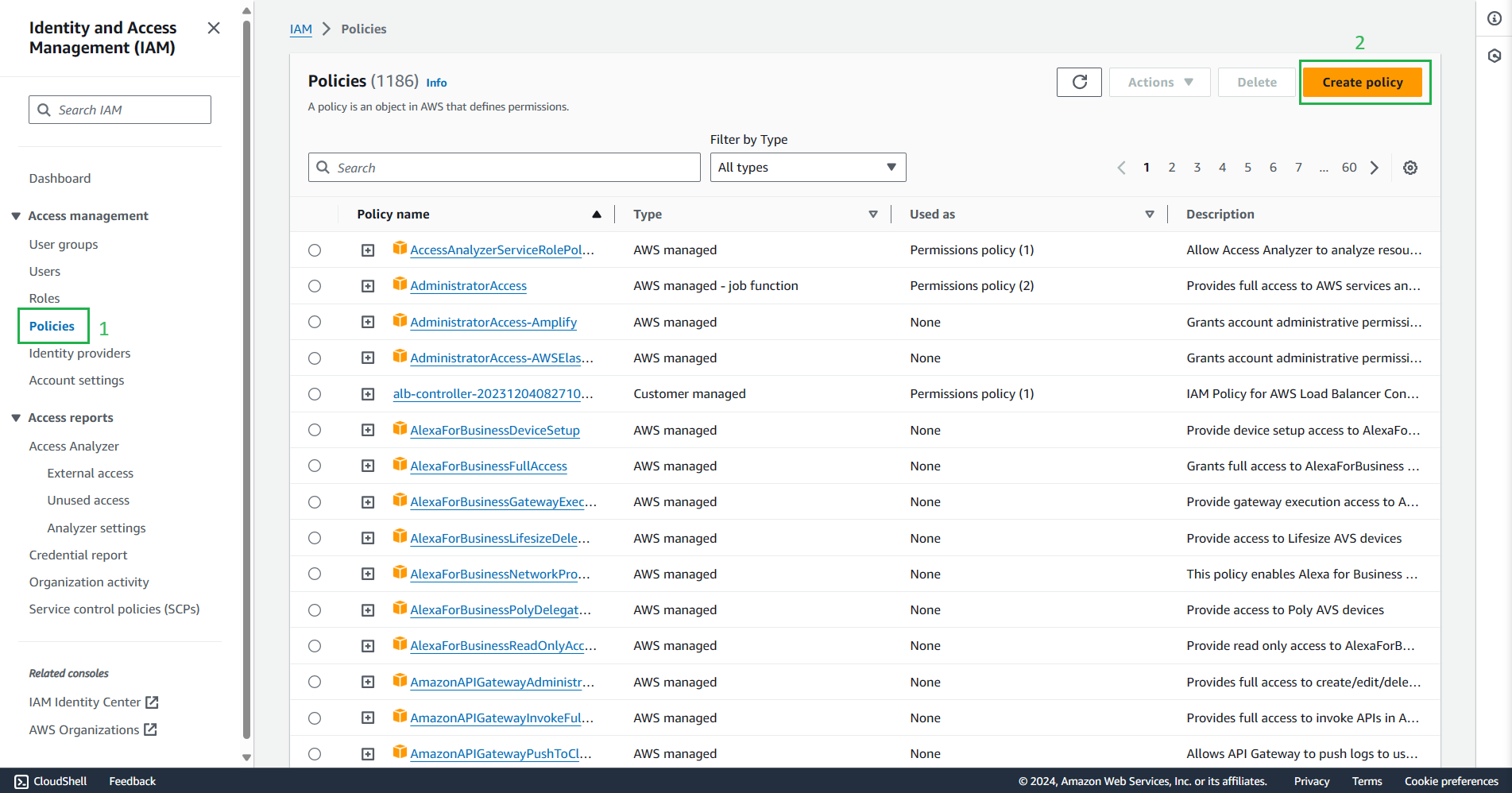
On the Specify permissions interface of Create Policies, switch to the json tab, then paste the following json snippet, and select next
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:*", "cloudwatch:*", "logs:*" ], "Resource": "*" }, { "Effect": "Allow", "Resource": [ "*" ], "Action": [ "codecommit:*" ] }, { "Effect": "Allow", "Action": [ "codebuild:*" ], "Resource": "*" } ] }``
👉 Json Policy Summary
-> The policy declares permissions related to:- S3 (“s3:*”): Storing artifacts and sending files to deploy to S3.
- Cloudwatch (“cloudwatch:*”), Cloudwatch logs (“logs:*”): Logging.
- CodeCommit (“codecommit:*”): Access CodeCommit to get source code for building and deploying.
- CodeBuild (“codebuild:*”): Access CodeBuild operations.
On the Review and create interface
- Enter Policy name:
fcj-workshop
- Review information
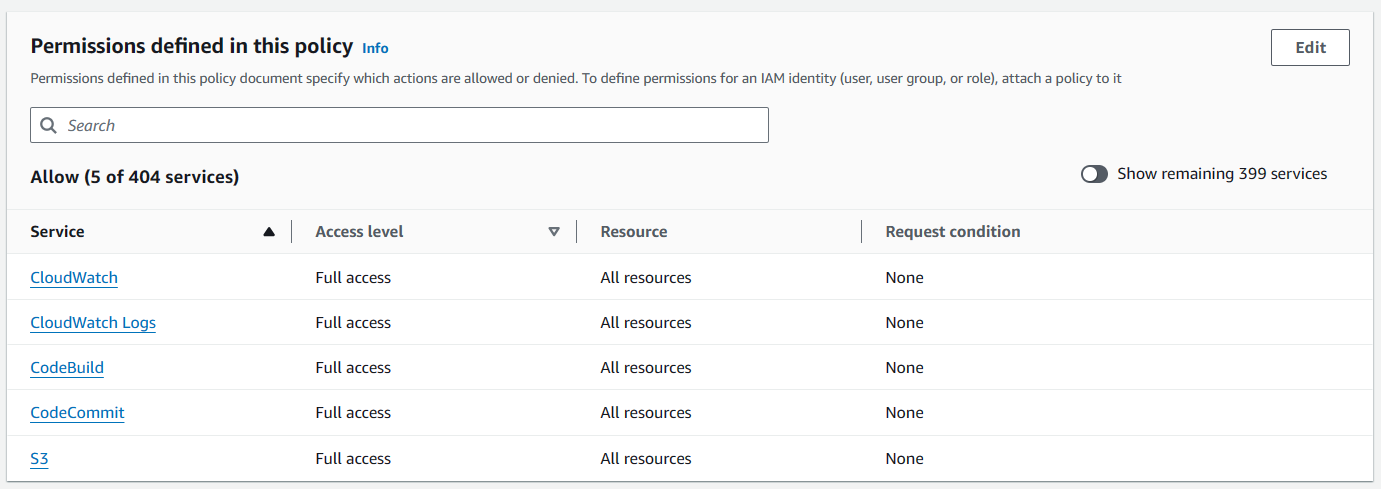
- Tag the policy and select Create policy. (You can skip adding tags, but I prefer to add tags to clean up resources completely after the lab)
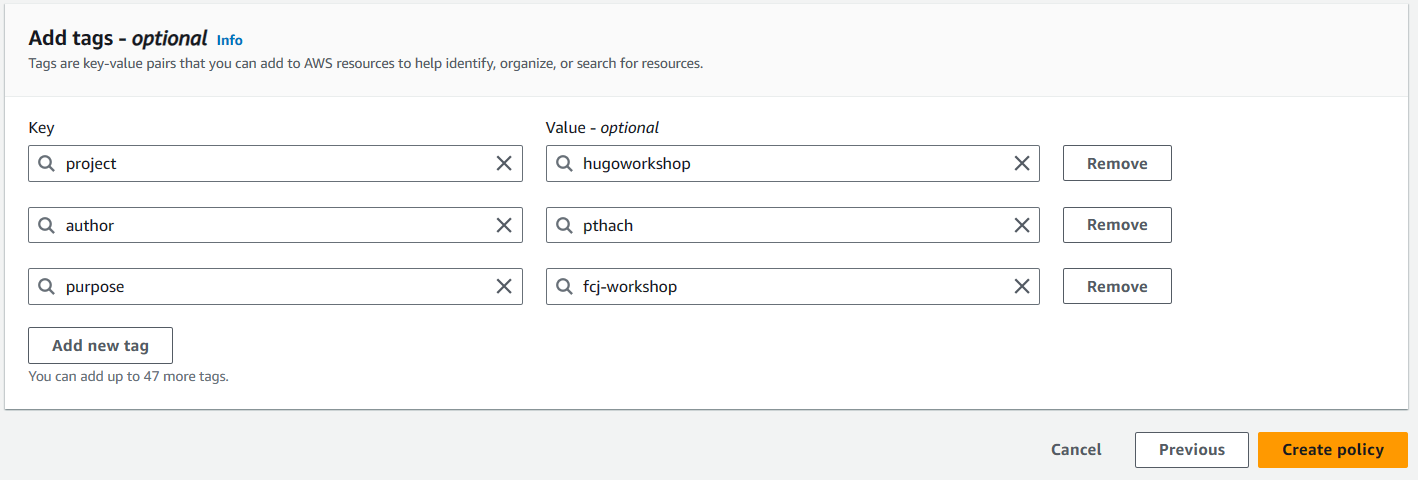
- Enter Policy name:
On the left navigation bar, select Roles
Choose Create Role
On the Select trusted entity, choose
AWS Service, then selectCodeBuildvà click Next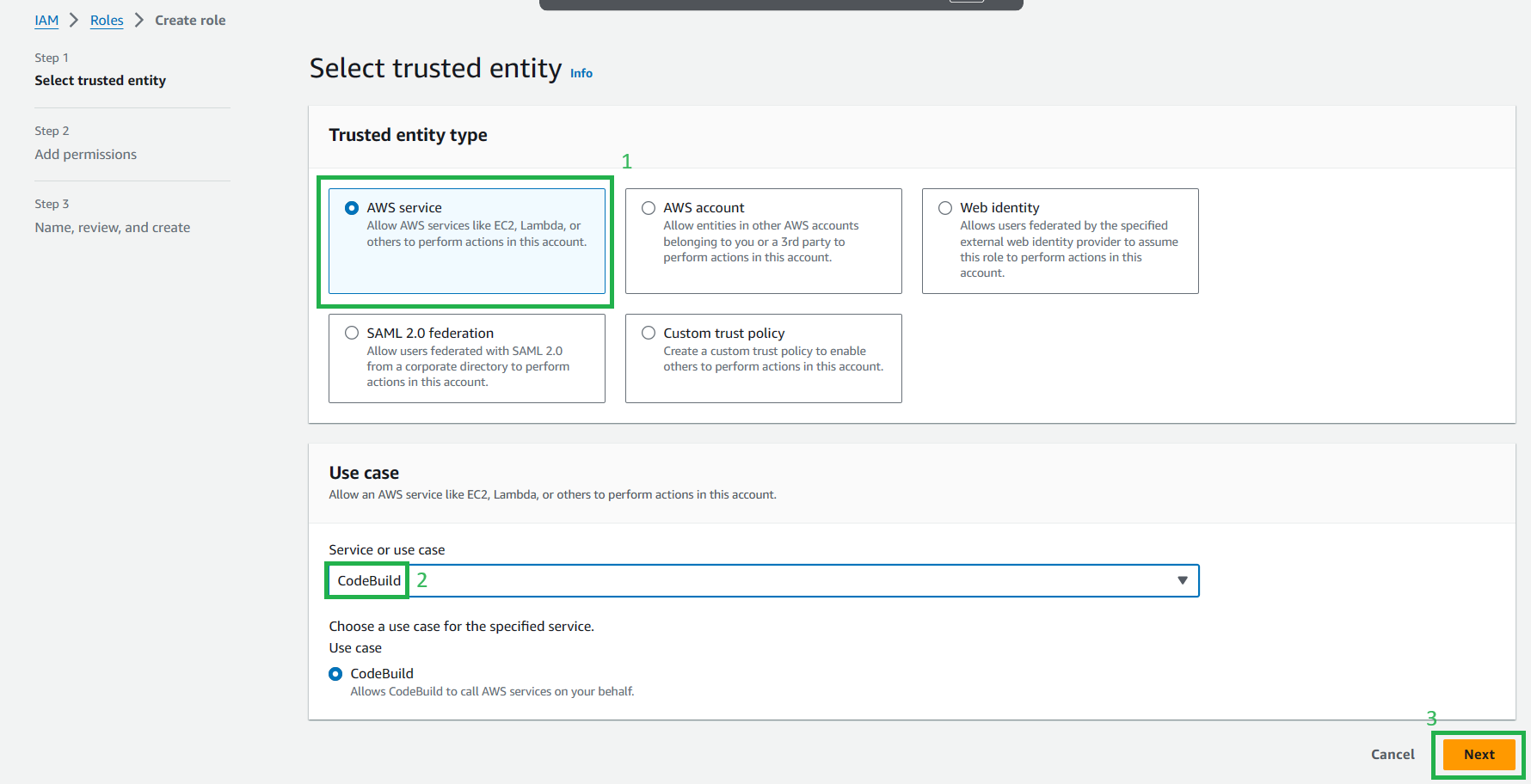
In Add permissions section, choose
fcj-workshopand click next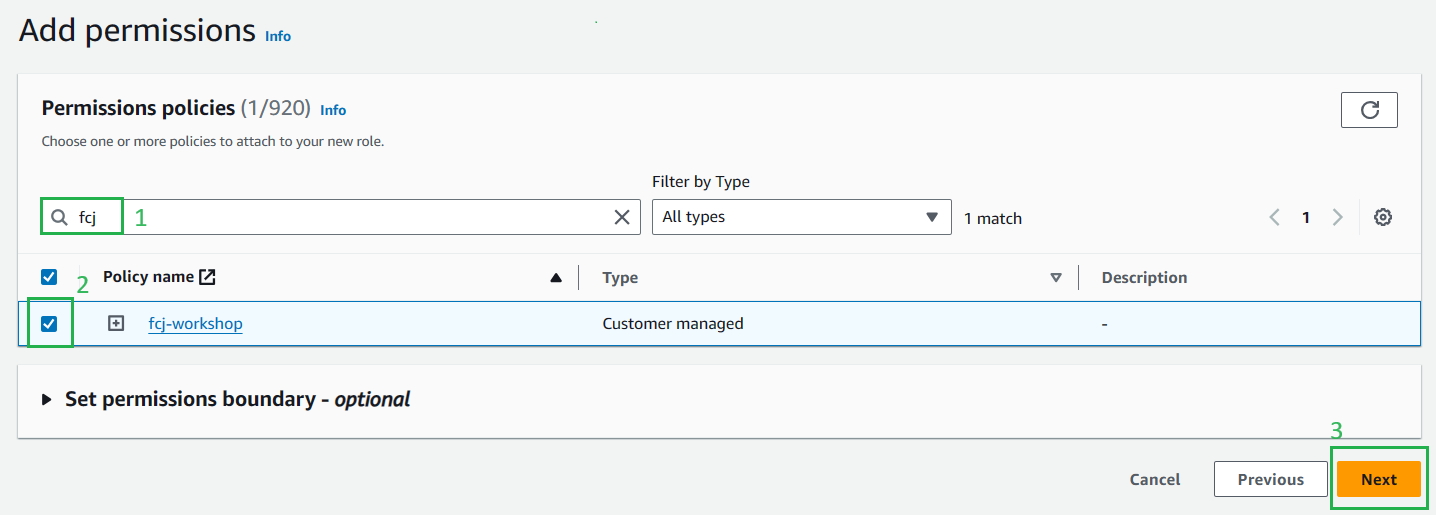
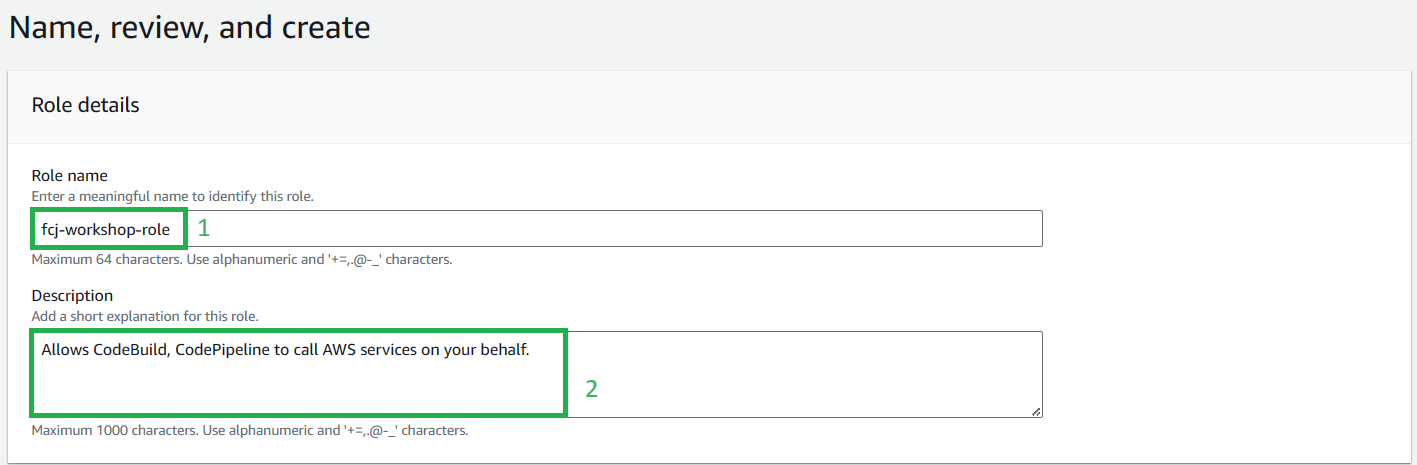
On the Name, review, and create
- Enter Role name:
fcj-workshop-role
- Tag the role and select Create Role.
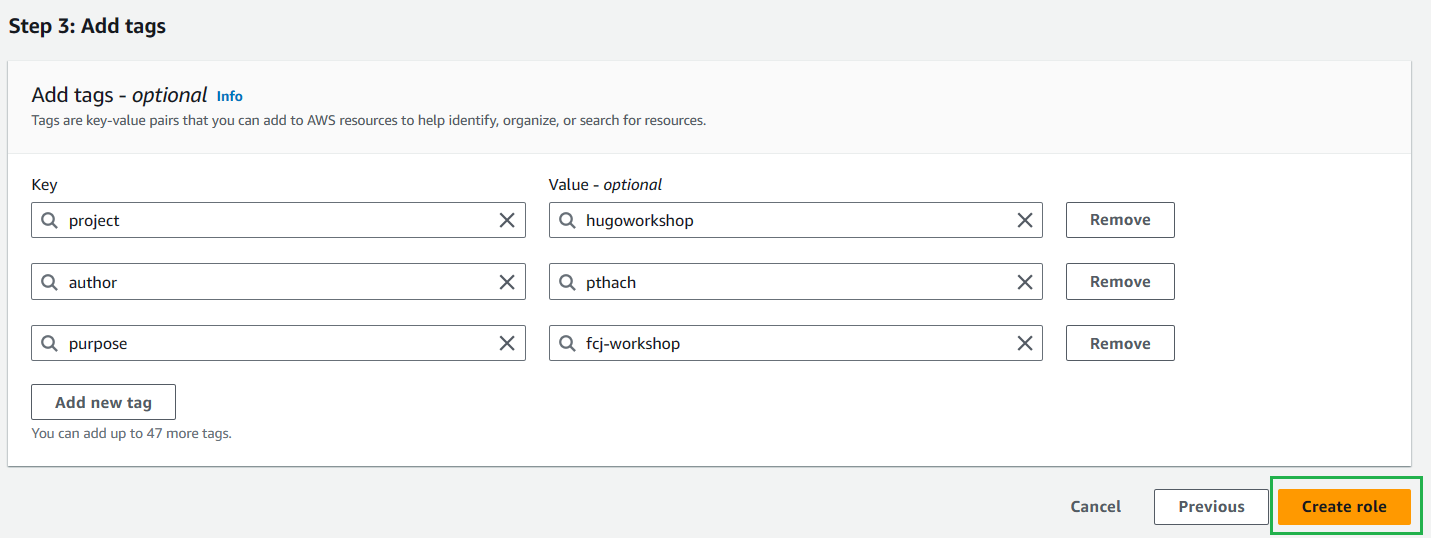
- Enter Role name:
Go back to the Roles, Select the created Role (
fcj-workshop-role)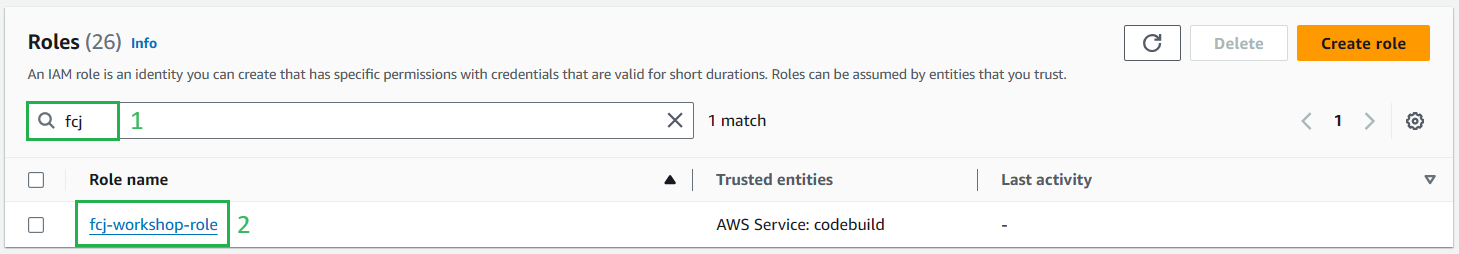
Click on tab
Trust relationshipsthen selectEdit trust policy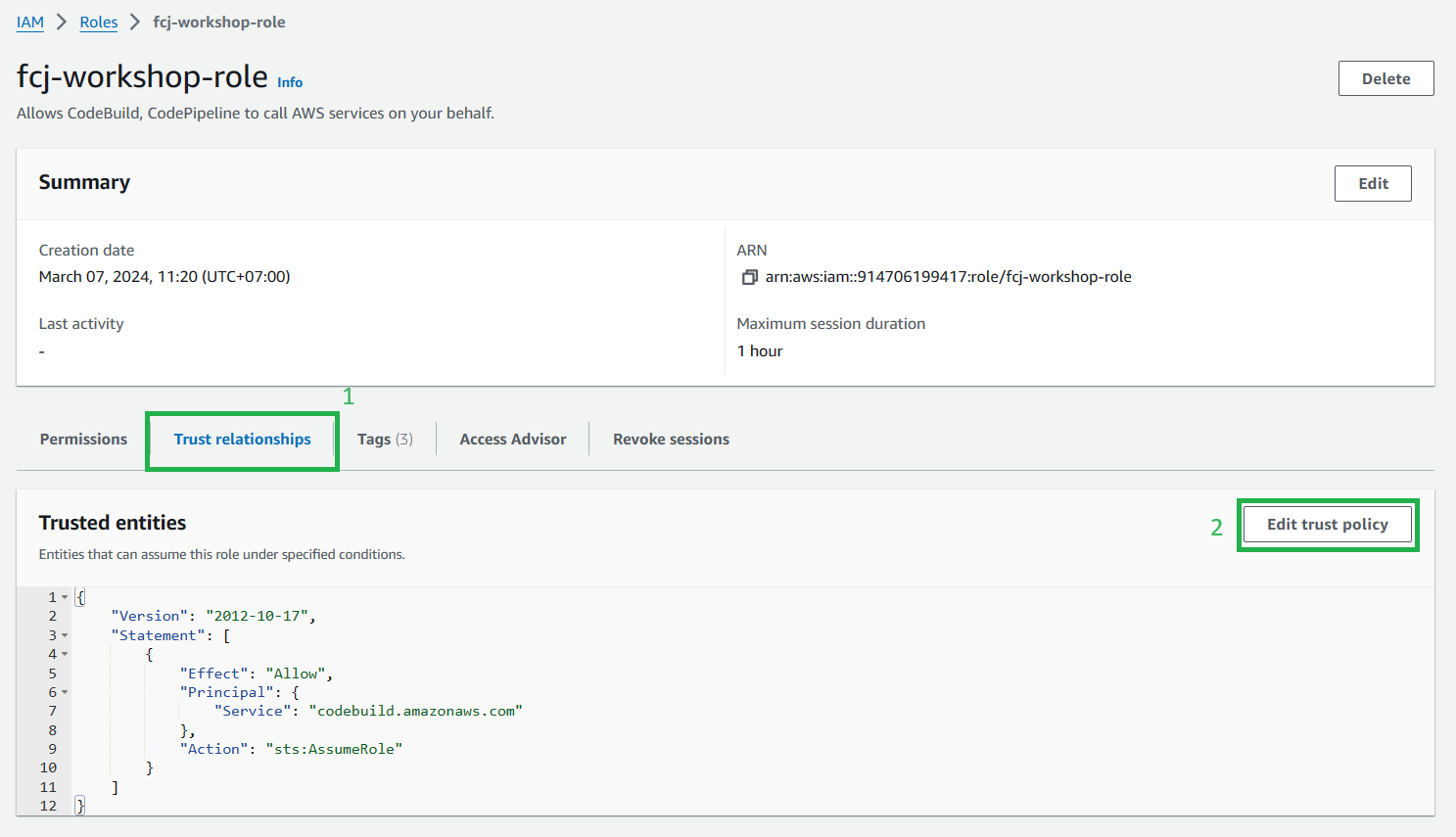
On the Edit trust policy, paste the following json:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "codebuild.amazonaws.com" }, "Action": "sts:AssumeRole" }, { "Effect": "Allow", "Principal": { "Service": "codepipeline.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }👉 Brief
IAM Role initially only had permissions assigned to CodeBuild (Step 8), but since I want to use one role for two services, I will add sts:AssumeRole to allow CodePipeline to also use this role.In this json, I add:
{ "Effect": "Allow", "Principal": { "Service": "codepipeline.amazonaws.com" }, "Action": "sts:AssumeRole" }ℹ️ Note:
However, this is for lab purposes; in practice, roles should be clearly divided for which service to avoid having a role with unnecessary privileges (least privilege) and for easy maintenance.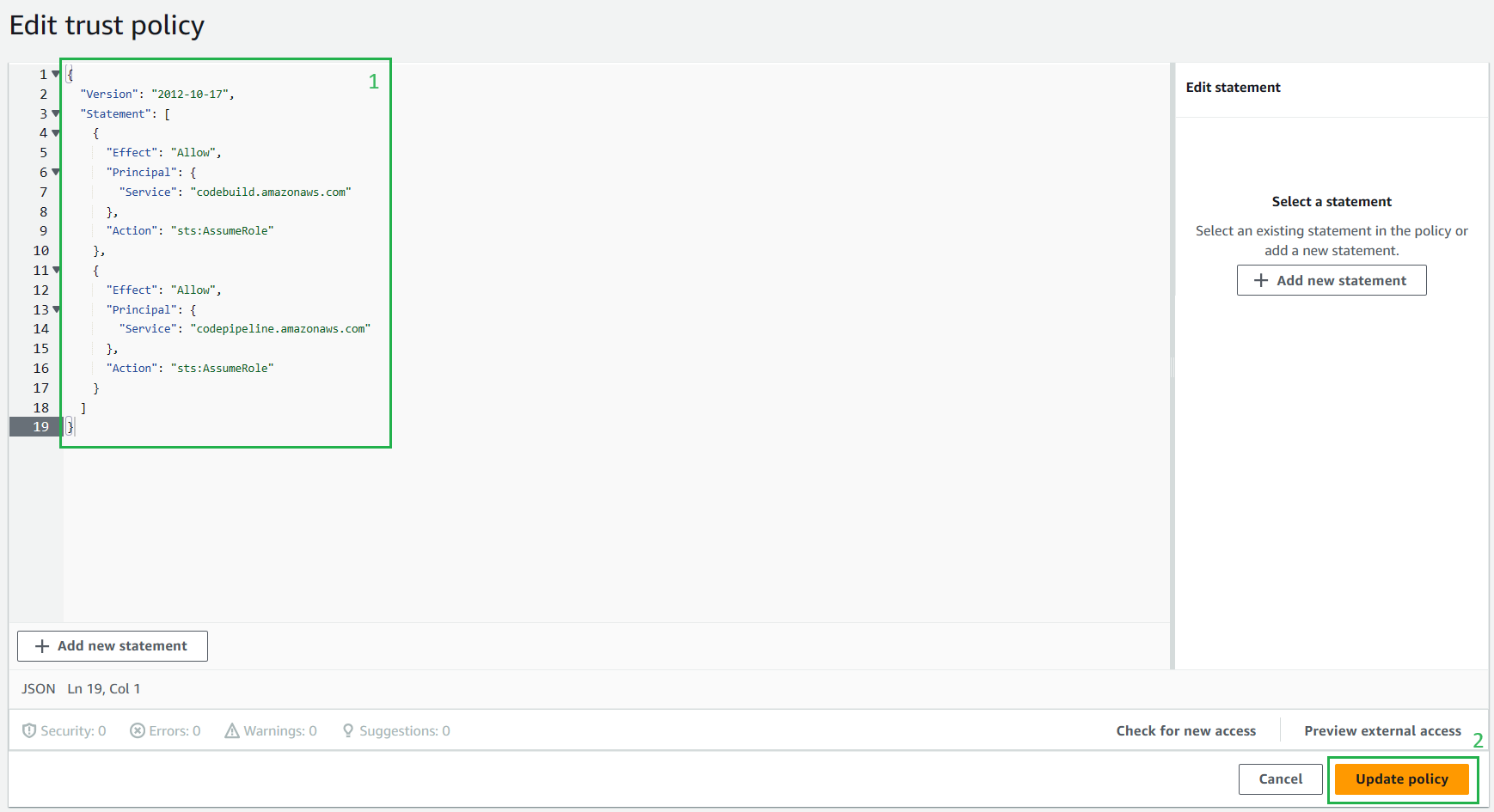
Choose Update policy