





| No. | Domain | Total Question | Correct | Incorrect | Unattempted | Marked for Review |
|---|---|---|---|---|---|---|
| 1 | Manage Azure identities and governance | 18 | 0 | 0 | 18 | 0 |
| 2 | Implement and manage storage | 6 | 0 | 0 | 6 | 0 |
| 3 | Deploy and manage Azure compute resources | 16 | 0 | 0 | 16 | 0 |
| 4 | Configure and manage virtual networking | 8 | 0 | 0 | 8 | 0 |
| 5 | Monitor and back up Azure resources | 7 | 0 | 0 | 7 | 0 |
| Total | All Domains | 55 | 0 | 0 | 55 | 0 |
A company has an Azure subscription that contains the following resource groups.
|
Name |
Lock Name |
Lock type |
|
whizlabs-rg1 |
None |
None |
|
whizlabs-rg2 |
whizlablock1 |
Delete |
The resource group whizlabs-rg1 contains the following resources.
|
Name |
Type |
Lock Name |
Lock type |
|
whizlabstore2090 |
Storage account |
whizlablock2 |
Delete |
|
whizlabnetwork |
Virtual network |
whizlablock3 |
Read-only |
|
whizlabip |
Public IP address |
None |
None |
Would you be able to move the resource whizlabstore2090 from the resource group whizlabs-rg1 to whizlabs-rg2?
- A. Yes
- B. No
Explanation:
Answer — A
Delete lock on a resource group, means that any resource, which is contained by a resource group, cannot be deleted. The idea behind delete lock is to avoid any resource deletion by mistake. Moreover, if an entire resource group is deleted, in production, by a malicious user or by mistake, it can cause serious problems, which may even impact the end-users. Delete lock puts no other restrictions. Resources can always be added to a resource group with a delete lock.
From this explanation, it is clear, that correct A (yes) is the correct answer, and all other answers are wrong.
For more information on resource locks, please visit the following URL:
A company has an Azure subscription that contains the following resource groups.
|
Name |
Lock Name |
Lock type |
|
whizlabs-rg1 |
None |
None |
|
whizlabs-rg2 |
whizlablock1 |
Delete |
The resource group whizlabs-rg1 contains the following resources.
|
Name |
Type |
Lock Name |
Lock type |
|
whizlabstore2090 |
Storage account |
whizlablock2 |
Delete |
|
whizlabnetwork |
Virtual network |
whizlablock3 |
Read-only |
|
whizlabip |
Public IP address |
None |
None |
Would you be able to move the resource whizlabnetwork from the resource group whizlabs-rg1 to whizlabs-rg2?
- A. Yes
- B. No
Explanation:
Answer - A
We would be able to move the resource whizlabnetwork from the resource group whizlabs-rg1 to whizlabs-rg2. The virtual network whizlabnetwork has a Read-only lock. It means that we can't delete or modify this resource without removing the lock. But this lock doesn't prevent us from moving a resource from one resource group to another. The current whizlabnetwork resource group, whizlabs-rg1, doesn't have any locks. The destination resource group, whizlab-rg2, has a Delete lock. This lock prevents the deletion of this resource group and all resources within it. It doesn't restrict the movement of the resources to this group from other groups.
Hence, A is the correct answer.
For more information on resource locks, please visit the following URL-
A company has an Azure subscription that contains the following resource groups.
|
Name |
Lock Name |
Lock type |
|
whizlabs-rg1 |
None |
None |
|
whizlabs-rg2 |
whizlablock1 |
Delete |
The resource group whizlabs-rg1 contains the following resources.
|
Name |
Type |
Lock Name |
Lock type |
|
whizlabstore2090 |
Storage account |
whizlablock2 |
Delete |
|
whizlabnetwork |
Virtual network |
whizlablock3 |
Read-only |
|
whizlabip |
Public IP address |
None |
None |
Would you be able to move the resource whizlabip from the resource group whizlabs-rg1 to whizlabs-rg2?
- A. Yes
- B. No
Explanation:
Answer – A
We would be able to move the resource whizlabip from the resource group whizlabs-rg1 to whizlabs-rg2. The public IP address whizlabip and it's resource group, whizlabs-rg1, don't have any locks. The destination resource group, whizlab-rg2, has a Delete lock. This lock prevents the deletion of this resource group and all resources within it. But it doesn't restrict the movement of the resources to this group from other groups.
For more information on resource locks, please visit the following URL-
A company has an Azure subscription and an Azure tenant named whizlabs.onmicrosoft.com. The following users are defined in the tenant.
|
Name |
Role |
Scope |
|
whizlabusr1 |
Global Administrator |
Azure Active Directory |
|
whizlabusr2 |
Global Administrator |
Azure Active Directory |
|
whizlabusr3 |
User administrator |
Azure Active Directory |
|
whizlabusr4 |
Owner |
Azure Subscription |
The user whizlabusr1 creates a new directory named staging.whizlabs.onmicrosoft.com.
New users need to be added to the new tenant.
The company asks whizlabusr1 to create user accounts.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
whizlabusr1 user has the Global Administrator role and has created the new directory. The user would have the required permissions to create new users in the directory.
For more information on creating a new directory, please visit the following URL-
A company has an Azure subscription and an Azure tenant named whizlabs.onmicrosoft.com. The following users are defined in the tenant.
|
Name |
Role |
Scope |
|
whizlabusr1 |
Global Administrator |
Azure Active Directory |
|
whizlabusr2 |
Global Administrator |
Azure Active Directory |
|
whizlabusr3 |
User administrator |
Azure Active Directory |
|
whizlabusr4 |
Owner |
Azure Subscription |
The user whizlabusr1 creates a new directory named staging.whizlabs.onmicrosoft.com.
New users need to be added to the new tenant.
The company asks whizlabusr2 to create user accounts.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The user whizlabusr2 is only the Global Administrator for the whizlabs.onmicrosoft.com directory. To add users to the new staging.whizlabs.onmicrosoft.com directory, whizlabusr2 needs to have the required role in the new directory.
For more information on creating a new directory, please visit the following URL-
A company has an Azure subscription and an Azure tenant named whizlabs.onmicrosoft.com. The following users are defined in the tenant.
|
Name |
Role |
Scope |
|
whizlabusr1 |
Global Administrator |
Azure Active Directory |
|
whizlabusr2 |
Global Administrator |
Azure Active Directory |
|
whizlabusr3 |
User Administrator |
Azure Active Directory |
|
whizlabusr4 |
Owner |
Azure Subscription |
The user whizlabusr1 creates a new directory named staging.whizlabs.onmicrosoft.com.
New users need to be added to the new tenant.
The company asks whizlabusr3 to create user accounts.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The user whizlabusr3 is only the User Administrator for the whizlabs.onmicrosoft.com directory. To add users to the new staging.whizlabs.onmicrosoft.com directory, whizlabusr3 needs to have the required role in the new directory.
For more information on creating a new directory, please visit the following URL-
A company currently has 2 Azure subscriptions: whizlab-staging and whizlab-production.
whizlab-staging has the following virtual networks.
|
Name |
Address space |
Location |
|
vnet-staging-01 |
10.10.10.0/24 |
West Europe |
|
vnet-staging-02 |
172.16.0.0/16 |
West US |
The virtual networks have the following subnets.
|
Name |
Address space |
Location |
|
snet-staging-11 |
10.10.10.0/24 |
vnet-staging-01 |
|
snet-staging-21 |
172.16.0.0/18 |
vnet-staging-02 |
|
snet-staging-22 |
172.16.128.0/18 |
vnet-staging-02 |
whizlab-production has the following virtual network.
|
Name |
Address space |
Location |
|
vnet-production |
10.10.128.0/17 |
Canada Central |
This network contains the following subnets.
|
Name |
Address space |
|
snet-production-01 |
10.10.130.0/24 |
|
snet-production-02 |
10.10.131.0/24 |
Can you establish a VNet-to-VNet VPN connection between vnet-staging-01 and vnet-staging-02?
- A. Yes
- B. No
Explanation:
Answer – B
To create a VNet-to-VNet VPN between two virtual networks, you need to have a special subnet - gateway subnet. Azure recommends reserve /27 or /28 CIDR blocks for this subnet. The virtual network vnet-staging-01 (10.10.10.0/24) has /24 CIDR blocks of address space. This space is already taken by snet-staging-11 subnet (10.10.10.0/24). This is why there is no sufficient address space to create a gateway subnet and to establish a VNet-to-VNet VPN connection between two VNETs. We need to resize subnet space or create an additional IP address range for the gateway subnet.
For more information on configuring VNet-to-VNet connections, please visit the following URL-
A company currently has 2 Azure subscriptions: whizlab-staging and whizlab-production.
whizlab-staging has the following virtual networks.
|
Name |
Address space |
Location |
|
vnet-staging-01 |
10.10.10.0/24 |
West Europe |
|
vnet-staging-02 |
172.16.0.0/16 |
West US |
The virtual networks have the following subnets.
|
Name |
Address space |
Location |
|
snet-staging-11 |
10.10.10.0/24 |
vnet-staging-01 |
|
snet-staging-21 |
172.16.0.0/18 |
vnet-staging-02 |
|
snet-staging-22 |
172.16.128.0/18 |
vnet-staging-02 |
whizlab-production has the following virtual network.
|
Name |
Address space |
Location |
|
vnet-production |
10.10.128.0/17 |
Canada Central |
This network contains the following subnets.
|
Name |
Address space |
|
snet-production-01 |
10.10.130.0/24 |
|
snet-production-02 |
10.10.131.0/24 |
Can you establish a peering connection between vnet-staging-01 and vnet-staging-02?
- A. Yes
- B. No
Explanation:
Answer – A
The address spaces for the virtual networks don’t overlap. You can establish a peering connection between both virtual networks.
For more information on virtual network peering, please visit the following URL-
A company currently has 2 Azure subscriptions: whizlab-staging and whizlab-production.
whizlab-staging has the following virtual networks.
|
Name |
Address space |
Location |
|
vnet-staging-01 |
10.10.10.0/24 |
West Europe |
|
vnet-staging-02 |
172.16.0.0/16 |
West US |
The virtual networks have the following subnets.
|
Name |
Address space |
Location |
|
snet-staging-11 |
10.10.10.0/24 |
vnet-staging-01 |
|
snet-staging-21 |
172.16.0.0/18 |
vnet-staging-02 |
|
snet-staging-22 |
172.16.128.0/18 |
vnet-staging-02 |
whizlab-production has the following virtual network.
|
Name |
Address space |
Location |
|
vnet-production |
10.10.128.0/17 |
Canada Central |
This network contains the following subnets
|
Name |
Address space |
|
snet-production-01 |
10.10.130.0/24 |
|
snet-production-02 |
10.10.131.0/24 |
Can you establish a peering connection between vnet-staging-01 and vnet-production?
- A. Yes
- B. No
Explanation:
Answer – A
The address spaces for the virtual networks don’t overlap. You can establish a peering connection between both virtual networks.
For more information on virtual network peering, please visit the following URL-
A company has the following virtual machines defined as part of their subscription.
|
Name |
Operating System |
Connect to |
|
vmwhizlab1 |
Windows Server 2019 |
SubnetA |
|
vmwhizlab2 |
Windows Server 2019 |
SubnetB |
- Public IP addresses are assigned to the virtual machines.
- At the operating system level, incoming remote desktop connections have been allowed.
- Both of the subnets are in the same virtual network.
- A network security group named nsg-whizlab1 has been assigned to SubnetA. This network security group only has the default rules.
- A network security group named nsg-whizlab2 has been assigned to the network interface of vmwhizlab2. This network security group has an additional rule with the following details.
- Priority: 100
- Name: nsgrule
- Port: 3389
- Protocol: TCP
- Source: Any
- Destination: Any
- Action: Allow
Is it possible to remote desktop into vmwhizlab1 from the Internet?
- A. Yes
- B. No
Explanation:
Answer – B
If you look at an example of the default network security rules, only traffic inbound within the virtual network and traffic from the load balancer is allowed. Otherwise, all other traffic is denied. Hence here also the traffic will be denied.
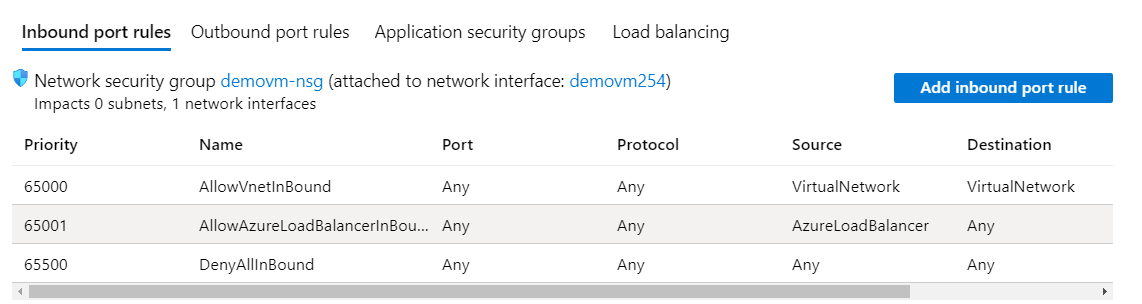
For more information on network security groups, please visit the following URL-
A company has the following virtual machines defined as part of their subscription.
|
Name |
Operating System |
Connect to |
|
vmwhizlab1 |
Windows Server 2019 |
SubnetA |
|
vmwhizlab2 |
Windows Server 2019 |
SubnetB |
- Public IP addresses are assigned to the virtual machines.
- At the operating system level, incoming remote desktop connections have been allowed.
- Both of the subnets are in the same virtual network.
- A network security group named nsg-whizlab1 has been assigned to SubnetA. This network security group only has the default rules.
- A network security group named nsg-whizlab2 has been assigned to the network interface of vmwhizlab2. This network security group has an additional rule with the following details.
- Priority: 100
- Name: nsgrule
- Port: 3389
- Protocol: TCP
- Source: Any
- Destination: Any
- Action: Allow
Is it possible to remote desktop into vmwhizlab2 from the Internet?
- A. Yes
- B. No
Explanation:
Answer – A
Since there is a rule that allows remote desktop connections from any source, connections are possible into vmwhizlab2.
For more information on network security groups, please visit the following URL-
A company has the following virtual machines defined as part of their subscription.
|
Name |
Operating System |
Connect to |
|
vmwhizlab1 |
Windows Server 2019 |
SubnetA |
|
vmwhizlab2 |
Windows Server 2019 |
SubnetB |
- Public IP addresses are assigned to the virtual machines.
- At the operating system level, incoming remote desktop connections have been disabled.
- Both of the subnets are in the same virtual network.
- A network security group named nsg-whizlab1 has been assigned to SubnetA. This network security group only has the default rules.
- A network security group named nsg-whizlab2 has been assigned to the network interface of vmwhizlab2. This network security group has an additional rule with the following details.
- Priority: 100
- Name: nsgrule
- Port: 3389
- Protocol: TCP
- Source: Any
- Destination: Any
- Action: Allow
Is it possible to remote desktop to the Public IP of vmwhizlab1 from vmwhizlab2?
- A. Yes
- B. No
Explanation:
Correct Answer - B
The reason, since we have created a Windows VM, for security reasons the RDP port is by-default disabled in both virtual machines
- In the given scenario, we are creating a new NSG called nsg-whizlab1, and it does not have an RDP port added to it. We need to get it added by creating a new rule.
- you cannot connect to an Azure Windows virtual machine (VM) because the Remote Desktop Protocol (RDP) port is not enabled in the network security group (NSG).
Due to this reason "remote desktop" to vmwhizlab1 from vmwhizlab2 is not possible.
Hence, B is the correct answer.
A company has the following resource groups defined as part of their Azure subscription.
|
Name |
Region |
|
rg-wl-01 |
West Europe |
|
rg-wl-02 |
North Europe |
The following virtual machines are then created in the subscription.
|
Name |
Resource group |
Region |
Operating system |
|
vmwl1 |
rg-wl-01 |
West Europe |
Windows Server 2016 |
|
vmwl2 |
rg-wl-01 |
North Europe |
Windows Server 2016 |
|
vmwl3 |
rg-wl-02 |
West Europe |
Windows Server 2016 |
|
vmwlA |
rg-wl-01 |
West Europe |
Ubuntu Server 18.04 |
|
vmwlB |
rg-wl-01 |
North Europe |
Ubuntu Server 18.04 |
|
vmwlC |
rg-wl-02 |
West Europe |
Ubuntu Server 18.04 |
The following recovery service vault is also defined as part of the subscription.
|
Name |
Region |
Resource group |
|
vaultwl2090 |
West Europe |
rg-wl-01 |
The company wants to ensure that as many virtual machines as possible are backed up using the recovery services vault vaultwl2090.
Which of the following virtual machines can be backed up using the Recovery Services vault?
- A. vmwl1 only
- B. vmwl1 and vmwl3 only
- C. vmwl1, vmwl3, vmwlA and vmwlC only
- D. vmwl3 and vmwlC only
- E. vmwl1, vmwl2, vmwl3, vmwlA, vmwlB and vmwlC
Explanation:
Answer — C
The Recovery Services Vault(RSV) should be in the same region, in which VM's exist, in order to back up the VM's. RSV vaultwl2090, vmwl1, vmwl3, vmwlA and vmwlC are in same region — Western Europe .
It is clear that C is the right answer and all other answers are incorrect.
Kindly note that Resource Group (RG) g-wl-01 and rg-wl-02 are in Western and Northern Europe respectively. VM vmwl1 and vmwl3 are in RG rg-wl-01 and rg-wl-02. RG can be in different regions because they contained only metadata about the resources, not the actual resource.
For more information on backing up Azure virtual machines using the Azure backup feature, please visit the following URL-
A company currently has the following resources defined as part of its subscription.
|
Name |
Type |
Location |
|
vnet-whizlab |
Virtual Network |
East US |
|
IP-whizlab |
Public IP address |
West Europe |
|
route table |
Route table |
North Europe |
The company wants to create a network interface named nic-whizlab and attach it to a virtual machine that is present in the virtual network of vnet-whizlab . In which of the following region/regions can you create the new network interface?
- A. In East US and West Europe only
- B. In West Europe only
- C. In East US, West Europe and North Europe
- D. In East US only
Explanation:
Answer - D
The network interface needs to be created in the same region as the virtual network.
Below is an excerpt from the Microsoft documentation on the creation of a network interface.
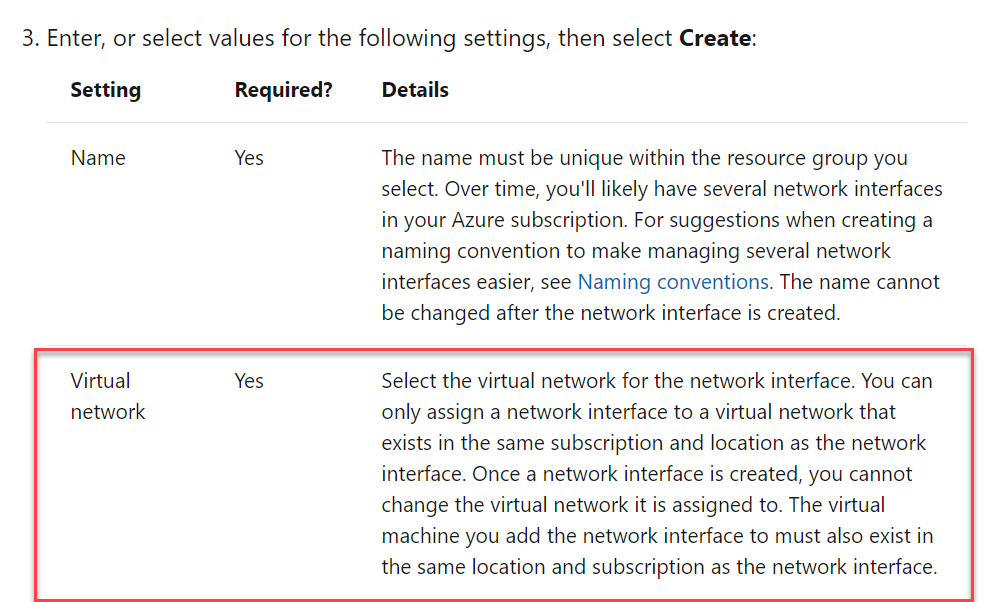
Since this is clear from the Microsoft documentation, all other options are incorrect.
For more information on network interfaces, please visit the following URL-
A company has the following resources defined as part of the Azure subscription.
|
Name |
Type |
|
whizlabcontainer |
Blob container |
|
whizlabshare |
Azure File share |
|
whizlabdb |
SQL Database |
|
whizlabtable |
Azure Table |
The company is planning to use the Azure Import/Export service. From which resource can you export the data using the service?
- A. whizlabcontainer
- B. whizlabshare
- C. whizlabdb
- D. whizlabtable
Explanation:
Answer – A
The Azure Import/Export service supports only data export from Azure Blob storage.
The Microsoft documentation mentions the following.
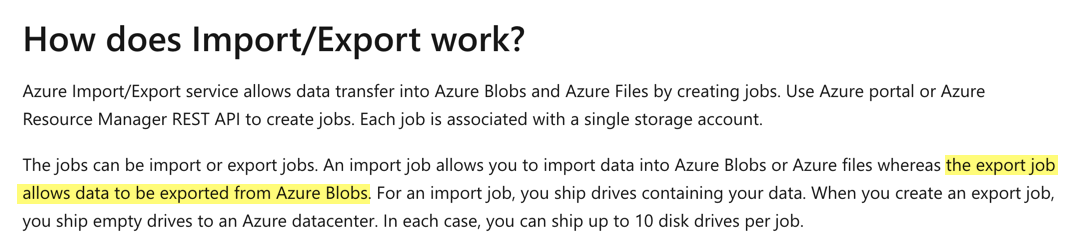
Since this is clear from the Microsoft documentation, all other options are incorrect.
For more information on the Azure Import/Export service, please visit the following URL-
Your company has the following resources defined as part of its Azure subscription.
- 100 Azure virtual machines
- 10 Azure SQL databases
- 50 Azure file shares
You need to create a daily backup of all resources by using Azure Backup. What is the minimum number of backup policies you have to create for this requirement?
- A. 1
- B. 2
- C. 3
- D. 100
- E. 160
Explanation:
Answer – B
In this task, there are three types of resources that require a backup. One of them is the Azure SQL database. We don't need to create a daily backup for Azure SQL Database because Azure provides a backup as an automatic service for every database by default. Azure SQL Database is Azure fully managed platform-as-a-service (PaaS) database engine. It includes automatic patching, monitoring, and backups. Azure SQL Database service is different from SQL Server that runs in Azure VM. SQL Server in VM requires the user to provide database maintenance and set up backups.
For two other types, Azure VM and Azure File shares, we need to create daily backup policies. For multiple VMs, Microsoft recommends creating a Recovery Services vault and add backup policies from the Backup policies option.
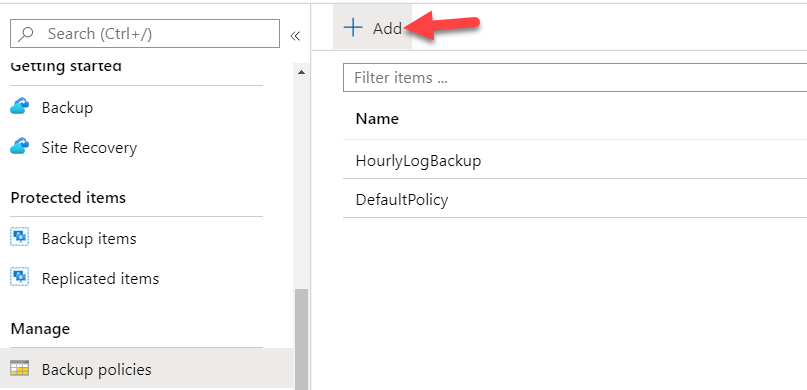
When we push the "Add" button, the following policy types are available for us to choose from.
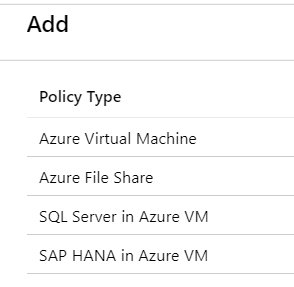
So, we can create two daily backup policies: one for all our Azure virtual machines and one for all Azure file shares.
All other options are incorrect.
For more information on an example of using the Azure backup service, please visit the following URLs-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Location |
Resource Group |
|
rg-whizlabs-1 |
Resource group |
East US |
Not applicable |
|
rg-whizlabs-2 |
Resource group |
West US |
Not applicable |
|
vaultwhizlab |
Recovery services vault |
West Europe |
rg-whizlabs-1 |
|
storewl2070 |
Storage account |
East US |
rg-whizlabs-2 |
|
storewl2080 |
Storage account |
West US |
rg-whizlabs-1 |
|
storewl2090 |
Storage account |
West Europe |
rg-whizlabs-2 |
|
log-wl-1 |
Log Analytics workspace |
East US |
rg-whizlabs-1 |
|
log-wl-2 |
Log Analytics workspace |
West US |
rg-whizlabs-2 |
|
log-wl-3 |
Log Analytics workspace |
West Europe |
rg-whizlabs-1 |
The company is planning to configure the Diagnostic settings for the Recovery Services vault to store the Azure Backup Reports.
Which of the following storage accounts can be used to store the backup reports?
- A. storewl2070 only
- B. storewl2080 only
- C. storewl2090 only
- D. storewl2070, storewl2080 and storewl2090
Explanation:
Answer – C
The storage account must be in the same region as the Recovery Services vault to store the reports. This is why storewl2090 is the correct answer.
The example below shows the configuration of the diagnostics setting for a vault. When we are selecting the "Archive to a storage account" option, the portal automatically takes the location of the recovery services vault. It limits us to storage accounts that are in the same region as the Recovery Services vault.
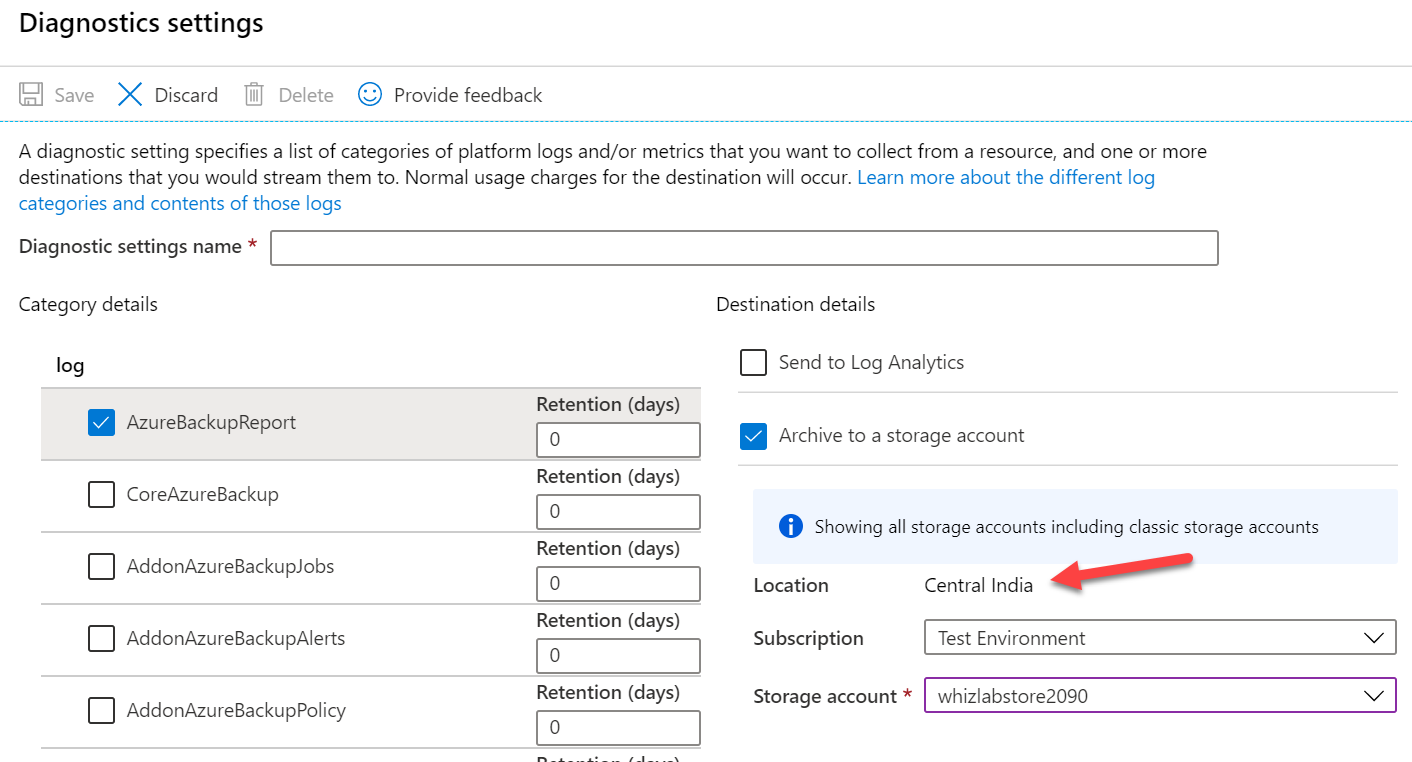
All other options are incorrect.
For more information on configuring Azure Backup reports, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Location |
Resource Group |
|
rg-whizlabs-1 |
Resource group |
East US |
Not applicable |
|
rg-whizlabs-2 |
Resource group |
West US |
Not applicable |
|
vaultwhizlab |
Recovery services vault |
West Europe |
rg-whizlabs-1 |
|
storewl2070 |
Storage account |
East US |
rg-whizlabs-2 |
|
storewl2080 |
Storage account |
West US |
rg-whizlabs-1 |
|
storewl2090 |
Storage account |
West Europe |
rg-whizlabs-2 |
|
log-wl-1 |
Log Analytics workspace |
East US |
rg-whizlabs-1 |
|
log-wl-2 |
Log Analytics workspace |
West US |
rg-whizlabs-2 |
|
log-wl-3 |
Log Analytics workspace |
West Europe |
rg-whizlabs-1 |
The company is planning to configure the Diagnostic settings for the Recovery Services vault to store the Azure Backup Reports.
Which of the following Log Analytics workspaces can be used to store the backup reports?
- A. log-wl-1 only
- B. log-wl-2 only
- C. log-wl-3 only
- D. log-wl-1, log-wl-2 and log-wl-3
Explanation:
Answer – D
The Log Analytics workspace can be in any region. It does not need to be in the same region as the recovery services vault.
Below is an example screenshot of choosing a Log Analytics workspace as part of the Diagnostic setting. Here the recovery services vault is in the Central India region. But the Log Analytics workspace is in the Central US region.
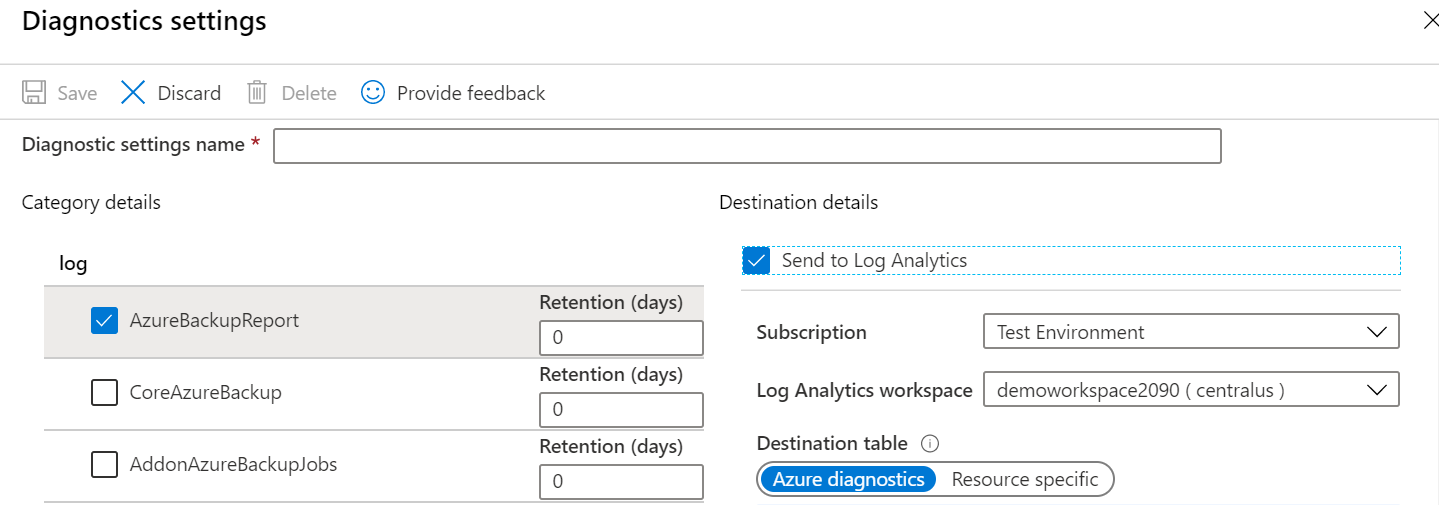
Since this is clear from the implementation, all other options are incorrect.
For more information on configuring Azure Backup reports, please visit the following URL-
Your organization has several offices. You need to reflect the organization structure in Azure AD by creating administrative units.
Please select the tools you can use to create administrative units.
- A. Azure AD Portal
- B. Microsoft Office Admin center
- C. PowerShell
- D. Power Platform Admin center
- E. Azure CLI
- F. Microsoft Graph
Explanation:
Correct Answers: A, C and F
For better management of the various organization entities, Azure AD provides the Administrative units' functionality. The administrative units are the containers that include Azure AD objects, groups, and users that are localized within the unit's boundaries. You can define the administrative roles to manage users and their access only within the administrative unit. You need to have an Azure AD Premium license for the unit's administrators. For the users, you use the free Azure AD license.
You can create administrative units using Azure AD portal blade, PowerShell, and Microsoft Graph.
On the Azure Active Directory blade (Number 1), you select the Administrative Units item (Number 2). Then, on the Administrative units screen, you can add a new unit (Number 3) or select the units from the table (Number 4) for editing.
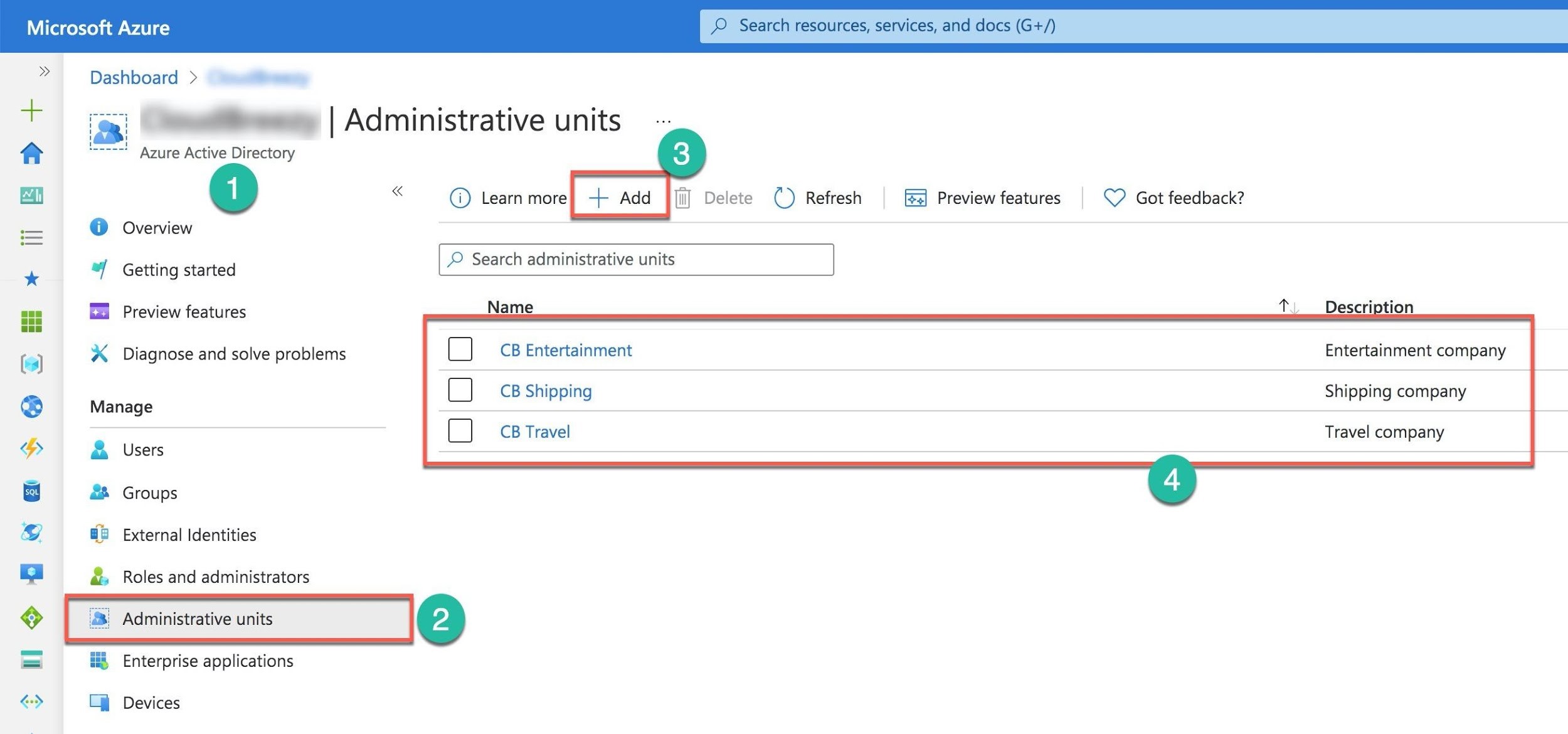
There are several built-in roles that Azure AD defines for the units. You can review them when you open the unit (Number 1) and select the Roles and administrators (Number 2). The new screen presents the table with built-in roles to assign to the unit’s users (Number 3).
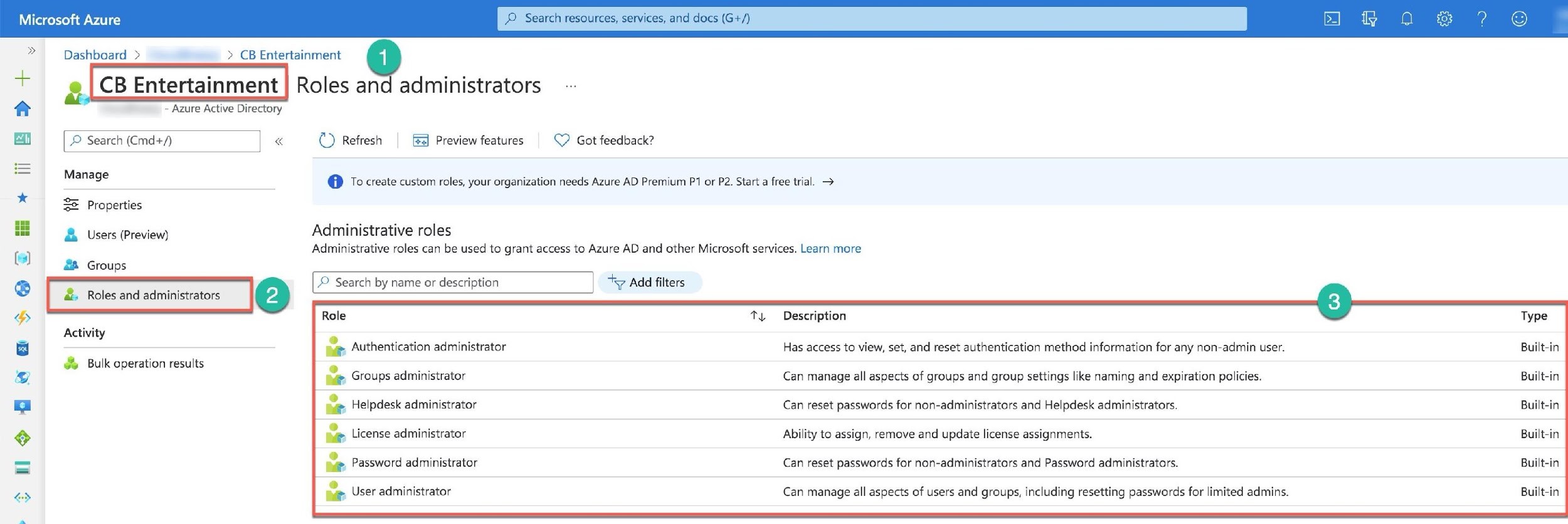
In the case of the PowerShell, you need to use the New-AzureADMSAdministrativeUnit command. And for Microsoft Graph API, you post the HTTP Request: POST /directory/administrativeUnits to create a new unit.
- Option B is incorrect because you can use the Microsoft Office Admin center for the users' management, but not for creating the administrative units.
- Option E is incorrect because the Azure CLI does not have the functionality to create and manage administrative units.
For more information about Azure AD administrative units, please visit the below URLs:
You create Azure AD administrative units for the subsidiaries of your organization. Each of the subsidiaries includes several hundred employees. You need to add these employees as administrative unit members.
Please select the tool you can use to achieve your goal.
- A. Microsoft Office Admin center
- B. Azure AD Portal
- C. Microsoft Graph
- D. PowerShell
- E. Azure CLI
Explanation:
Correct Answer: B
For better management of the various organization entities, Azure AD provides the Administrative units' functionality. The administrative units are the containers that include Azure AD objects, groups, and users that are localized within the unit's boundaries. You can define the administrative roles to manage users and their access only within the administrative unit. You need to have an Azure AD Premium license for the unit's administrators. For the users, you use the free Azure AD license.
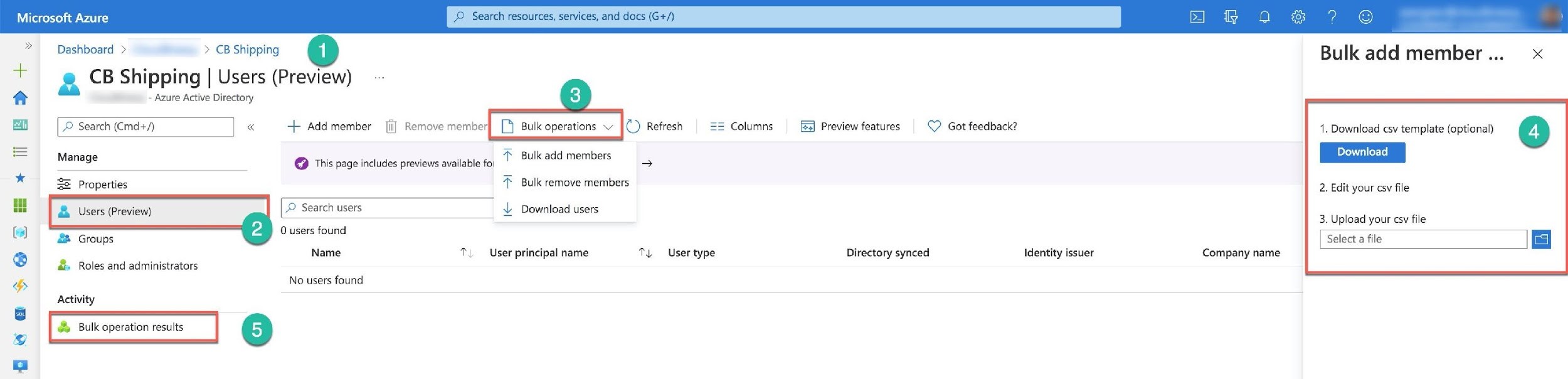
To add the list of users to the administrative unit, you need to use the bulk operations. Only the Azure AD portal provides the bulk operation functionality. On the administrative unit blade (Number 1), you select the Users (Number 2). Next, you can choose one of the Bulk operations (Number 3) options. If you select the Bulk add members, the portal opens a new panel to the right with the steps to add the unit's members (Number 4). After you add the list, you can monitor and verify the results using the Bulk operation results screen (Number 5).
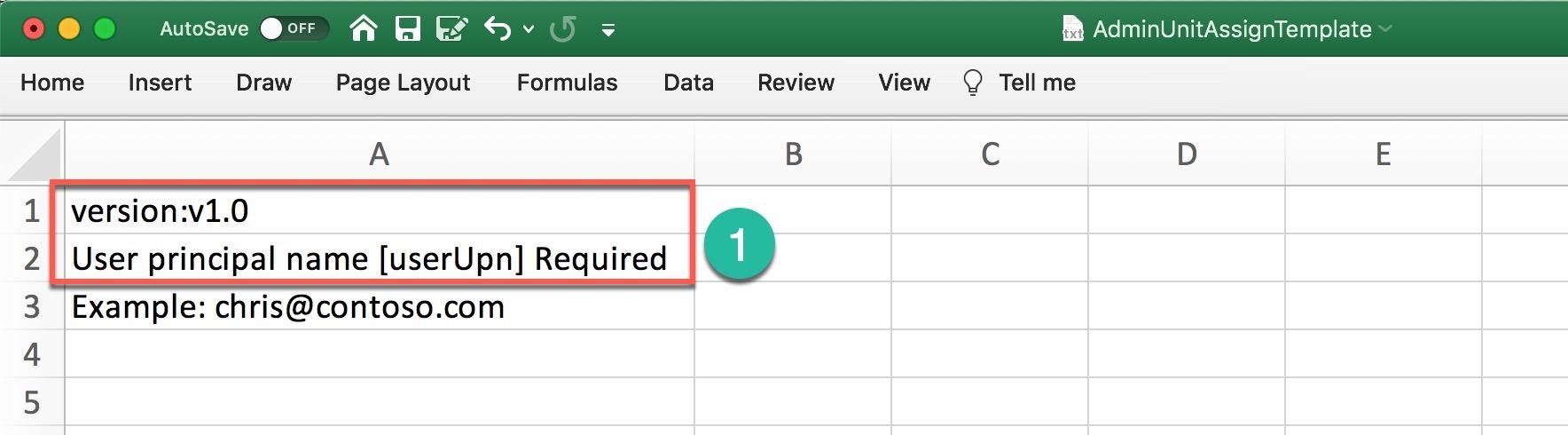
You can provide a prepared CSV list with the employees or download the template and create such a list. You need to keep the first two rows intact (Number 1) and add the members after.
You can remove the unit's members using the CSV list as well. You need to select the “Bulk remove members” option and supply the list.
- Options A, C, and D are incorrect because Microsoft Office Admin center, Microsoft Graph, and PowerShell can manage individual users in the administrative units but not the list of the users in a bulk manner.
- Option E is incorrect because the Azure CLI does not have the functionality to create and manage administrative units.
For more information about the management of the Azure AD administrative units, please visit the below URLs:
You need to use the Azure Monitor Insight for Networks.
What are the three main monitoring components the Azure Monitor Insight for Networks provides?
- A. Connectivity
- B. Capacity
- C. Traffic
- D. Availability
- E. Network health and metrics
- F. Performance
Explanation:
Correct Answers: A, C and E
Azure Monitor Insights for Networks brings several diagnostics and monitoring tools under one roof. It includes the following components:
- Network health and metrics — provides the integrated view of the networking resources' health, metrics, and alerts. Users can filter resources by subscriptions, resource group, and type.
- Connectivity — provides insights into the Connection Monitor tests. Test Information is divided into two categories: Sources and Destinations. Users can filter resources by subscriptions, resource group, source and destination types, and reachability criteria.
- Traffic — provides information about all NSGs and their Flow logs and Traffic Analytics configurations.
There is an additional set of the tools — Diagnostics Toolkit. It helps to troubleshoot the networks. The toolkit includes the following services: Capture packets on virtual machines, Troubleshoot VPN, Troubleshoot connectivity, Identify next hops, Diagnose traffic filtering issues.
You can examine the main network monitor components on the Monitor Networks screen (Number 1) by selecting the Networks (Number 2) item in the Insights section. There are three tabs: Network health (Number 3), Connectivity (Number 4), and Traffic (Number 5). On the first tab, you can review the health of the networking resources. When you click on the resource panel buttons (Number 7), the portal opens the table with the details on the bottom of the screen (Number 8).

If you need access to the diagnostics tools, click on the Diagnostics Toolkit dropdown (Number 6).
All other options are incorrect.
For more information about the Azure Monitor Insights for Networks, please visit the below URLs:
Your company has the following users defined as part of their Azure AD tenant. The tenant is also synced with an on-premise Active Directory using Azure AD Connect.
|
Name |
Type |
Source |
|
wlusr1 |
Member |
Azure AD |
|
wlusr2 |
Member |
Windows Server Active Directory |
|
wlusr3 |
Guest |
Microsoft account |
|
wlusr4 |
Member |
Windows Server Active Directory |
The users have the following attributes.
|
Name |
Office phone |
Mobile phone |
|
wlusr1 |
111-222-3333 |
222-333-4444 |
|
wlusr2 |
null |
null |
|
wlusr3 |
333-444-5555 |
444-555-6666 |
|
wlusr4 |
555-666-7777 |
null |
You have to ensure Multi-Factor Authentication is enabled for all users.
As part of the solution you decide to add a mobile phone number for wlusr2 and wlusr4?
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
When configuring MFA to a user we need to provide valid options to validate the action.
In the given table, wlusr2 does not have a valid mode of getting MFA request approved i.e., neither Office Phone / Mobile Number is provided for validating. For this reason, by providing Mobile Phone Number MFA request can be validated.
In the given table, wlusr4 already has an Office Phone assigned, and that is enough for validating MFA in case if the user is working from Office. If the user is working remotely, then MFA validaiton fails and for that adding a Mobile Phone Number will allow the login successful.
Due to these reasons, the answer is Yes.
For more information on Azure MFA, please visit the following URL-
Your company has the following users defined as part of their Azure AD tenant. The tenant is also synced with an on-premise Active Directory using Azure AD Connect.
|
Name |
Type |
Source |
|
wlusr1 |
Member |
Azure AD |
|
wlusr2 |
Member |
Windows Server Active Directory |
|
wlusr3 |
Guest |
Microsoft account |
|
wlusr4 |
Member |
Windows Server Active Directory |
The users have the following attributes.
|
Name |
Office phone |
Mobile phone |
|
wlusr1 |
111-222-3333 |
222-333-4444 |
|
wlusr2 |
null |
null |
|
wlusr3 |
333-444-5555 |
444-555-6666 |
|
wlusr4 |
555-666-7777 |
null |
You have to ensure Multi-Factor Authentication is enabled for all users.
As part of the solution you decide to add an office phone number for wlusr2.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - A
The premise given here is for all the users and this question is asking if "adding" of "office phone number" to wlusr2 will allow MFA assigned?
And this is possible, reason in order to configure MFA we need to have a valid contact number and in this case we are adding "office phone number". The authentication call will be coming on the given phone number before authorizing the user.
For more information on Azure MFA, please visit the following URL-
Your company has the following users defined as part of their Azure AD tenant. The tenant is also synced with an on-premise Active Directory using Azure AD Connect.
|
Name |
Type |
Source |
|
wlusr1 |
Member |
Azure AD |
|
wlusr2 |
Member |
Windows Server Active Directory |
|
wlusr3 |
Guest |
Microsoft account |
|
wlusr4 |
Member |
Windows Server Active Directory |
The users have the following attributes.
|
Name |
Office phone |
Mobile phone |
|
wlusr1 |
111-222-3333 |
222-333-4444 |
|
wlusr2 |
null |
null |
|
wlusr3 |
333-444-5555 |
444-555-6666 |
|
wlusr4 |
555-666-7777 |
null |
You have to ensure Multi-Factor Authentication is enabled for all users.
As part of the solution you decide to create a new user account for wlusr3 in Azure AD.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, since MFA can't be enabled for external user accounts. Even if MFA is enabled for all users, it is not enabled for the external accounts. User wlusr3 has type "Guest" in Azure AD. To force wlusr3 to use MFA, we have to create a new user account for him in Azure AD.
Suppose you invite an external user, and then you go to the MFA settings page, you will not select the user to enable MFA.
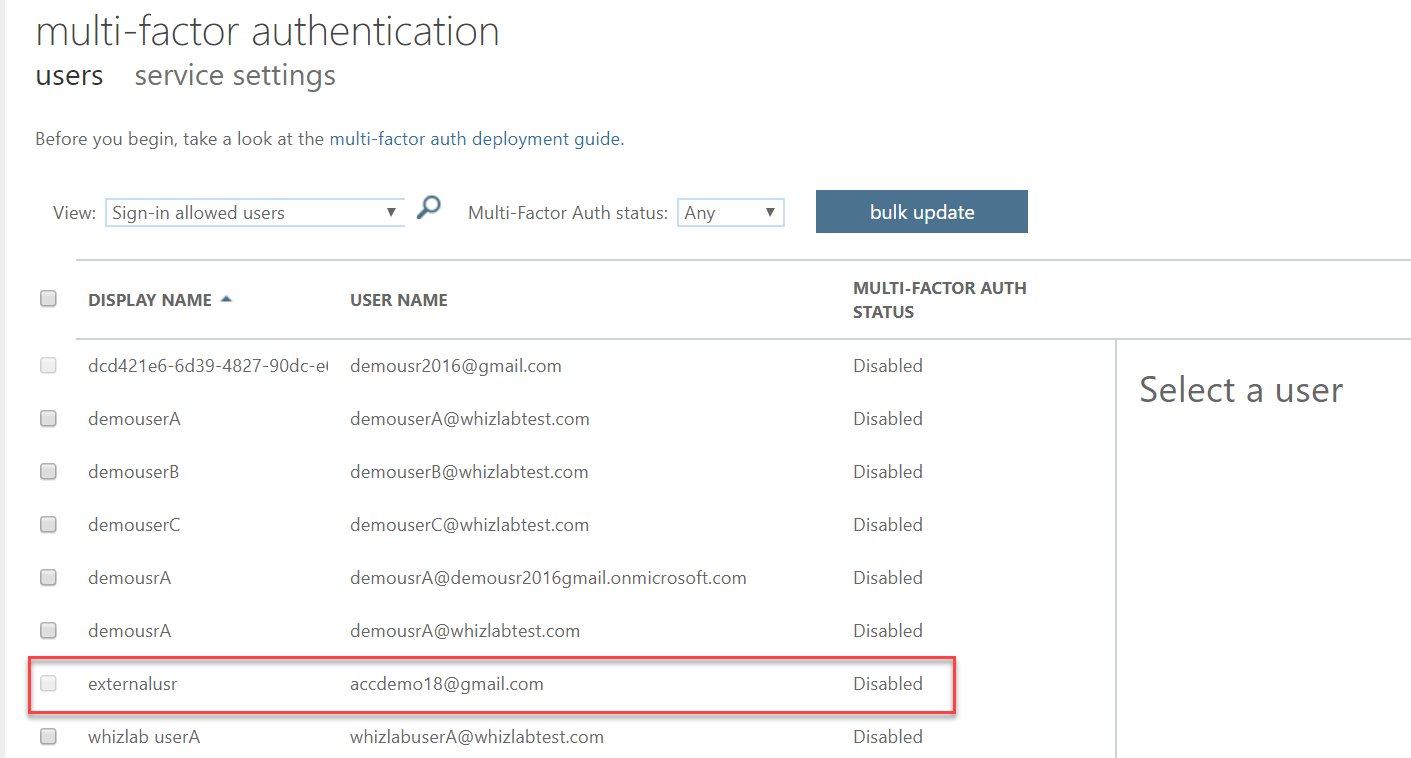
If we implement the Conditional Access option, we would not be required to add this user to Azure AD. Conditional Access will force wlusr3 to use MFA.
For more information on Azure MFA, please visit the following URL-
Your company has an Azure storage account named storewl8080, which has the following properties.
|
Location |
West US |
|
Performance |
Standard |
|
Access Tier |
Cool |
|
Account type |
General-purpose v2 |
|
Replication |
Read-access geo-redundant storage |
|
Advanced Thread protection |
Enabled |
The company wants to change the replication type of storage account from Read-access geo-redundant storage to Zone redundant storage by requesting Azure support for live migration. Which of the following must be carried out first to fulfill this requirement?
- A. Ensure to change the performance of the storage account.
- B. Ensure to change the Access tier of the storage account.
- C. Ensure to change the Account kind of the storage account.
- D. Ensure to change the Replication technique of the storage account.
Explanation:
Answer – D
The Microsoft documentation clearly states, that the replication type of the storage account, can be changed to Zone redundant storage, only, if the current replication technique is either LRS or GRS.
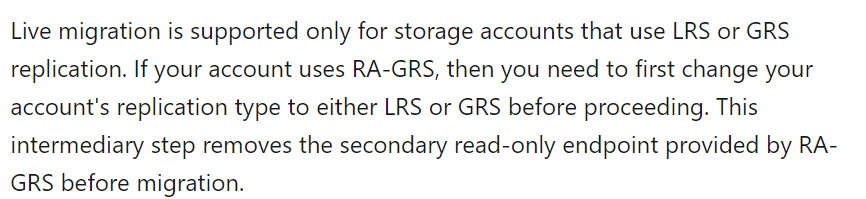
Hence, D is the correct answer and all other answers are wrong.
For more information on migrating the replication technique, please visit the following URL-
A company is planning to deploy two Azure Kubernetes clusters. Each cluster has different requirements as given below.
- clusterA – Here you have to ensure that the nodes get an IP address from the Azure virtual network subnet. And the pods receive an IP address from a logically different address space.
- clusterB – Here you have to ensure that every pod gets an IP address from the subnet and can be accessed directly.
Which of the following needs to be used to fulfill the requirement for clusterA?
- A. Service endpoint
- B. kubenet
- C. Azure Container Network Interface
- D. Network Security Groups
Explanation:
Answer – B
Kubernetes cluster can have vnet connectivity in two ways
- Kubenet (By default)
- Azure CNI interface by choice
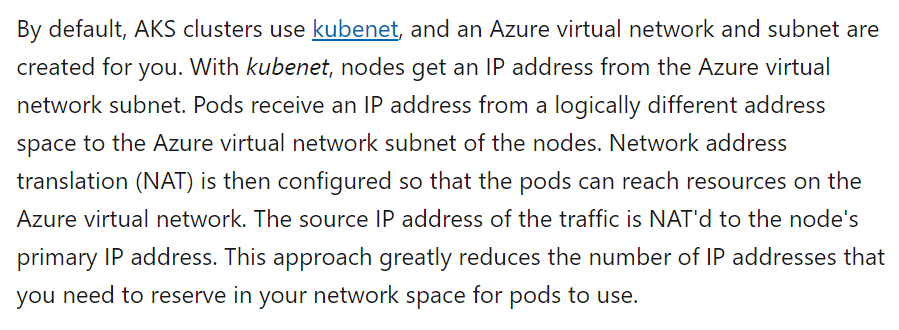
Deployment of AKS cluster is always in a vnet, with multiple pods in separate subnets of the same vnet. Pods in an AKS cluster run on node, which is invariably an Azure VM.
With kubenet, each of AKS nodes get an IP address from the subnet range, but pods get an IP address from an overlay network. Such IP addresses are from a logically different IP address space outside vnet range.
Such IPs are is not routable outside the vnet/subnet. For example, pods can talk to a DB, which is out the vnet/subnet, only via an additional hop, which will be the IP address of the node/Azure VM. Kubenet has some other disadvantages like:
- It does not support window containers.
- It does not support network and security policies definition from a centralized control plane.
- Additional user-defined routes (UDRs) lead to additional admin overhead.
- Extra hop has minor adverse effect on network performance
With Azure CNI, every pod gets an IP address from the subnet range. Such IPs are routable, outside the vnet/subnet range, without requiring any extra hop.
CNI stands for container networking interface. CNI is an open standard for Kubernetes network plugin. With AzureCNI has the following advantages:
- Pods get full virtual network connectivity and can be directly reached via their private IP address from connected networks. No additional hop is required.
- It supports window containers
- It provides centralized control for security and network policy
In view of above, B is obviously the correct answer as kubenet meet the requirements of cluster A. All other answers are wrong.
Azure CNI details are given below:
For more information on networking in Kubernetes, please visit the following URL-
A company is planning to deploy two Azure Kubernetes clusters. Each cluster has different requirements as given below.
- clusterA – Here, you have to ensure that the nodes get an IP address from the Azure virtual network subnet. And the pods receive an IP address from a logically different address space.
- clusterB – Here, you have to ensure that every pod gets an IP address from the subnet and can be accessed directly.
Which of the following needs to be used to fulfill the requirement for clusterB?
- A. Service endpoint
- B. kubenet
- C. Azure Container Network Interface
- D. Network Security Groups
Explanation:
Answer – C
Kubernetes cluster can have vnet connectivity in two ways
- Kubenet (By default)
- Azure CNI interface.
AKS cluster can be deployed in a vnet with multiple pods in separate subnets of the same vnet. Pods in an AKS cluster run on a node, which is invariably an Azure VM. With kubenet each of the AKS nodes gets an IP address from the subnet range. Such IPs are routable outside the vnet/subnet without requiring any extra hop... However, pods get an IP address from an overlay network. Such IPs are is not routable outside the vnet/subnet. For example, Pods can talk to a DB, which is out the vnent/subnet, only via an additional hop which will be the IP address of the node/Azure VM. This has an adverse effect on network performance.
Kubenet has some other disadvantages like
- It does not support window containers.
- It does not support network and security policies definition from a centralized control plane.
- additional routes have to be manually managed and maintain for user-defined routes (UDRs)
CNI stands for container networking interface. CNI is an open standard for the Kubernetes network plugin. With Azure, CNI has the following advantages over Kubernetes
- Pods get full virtual network connectivity and can be directly reached via their private IP address from connected networks. No additional hop is required.
- It supports window containers
- It provides centralized control for security and network policy
So, C is obviously the correct answer.
For this requirement, the AKS clusters can use the Azure Container Networking Interface. This is also given in the Microsoft documentation.

So based on the documentation, all other options are incorrect.
For more information on networking in Kubernetes, please visit the following URL-
A company has the following App Service Plans defined as part of their Azure subscription.
|
Name |
Location |
Operating System |
|
wlplanA |
East US |
Linux |
|
wlplanB |
East US |
Windows |
|
wlplanC |
UK South |
Windows |
The company is planning on deploying the following Azure Web App Instances.
|
Name |
Location |
Runtime stack |
|
wlapp1 |
East US |
.Net Core 3.1 |
|
wlapp2 |
East US |
ASP.NET V4.7 |
Which of the following App service plans can you use for wlapp1?
- A. wlplanA only
- B. wlplanB only
- C. wlplanA and wlplanB only
- D. wlplanB and wlplanC only
- E. wlplanA, wlplanB and wlplanC
Explanation:
Answer – C
You can deploy a DotNet Core applications on either Window OS or a Linux OS. Web apps and service plans should also be in the same region.
Wlapp1, wlplanA and wlplanB are in East US region.
In view of this. C is the correct answer and all other answers are wrong.
If we want deployment in a pre-defined region, This is same as moving a web app to this region, the Microsoft documentation mentions the following.
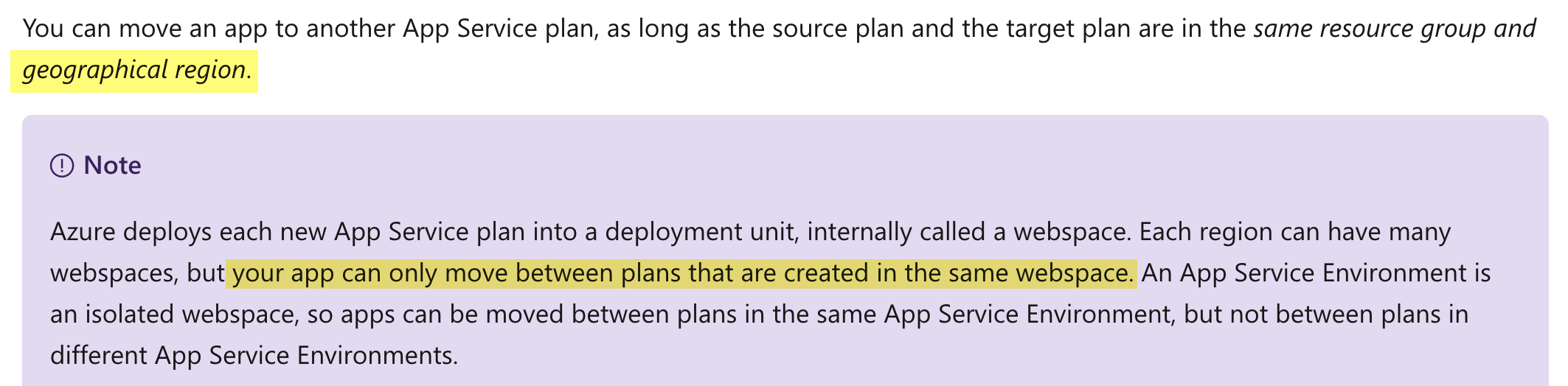
Because of this reasoning, all other options are incorrect.
For more information on the Linux App Service Plan, please visit the following URL-
A company has the following App Service Plans defined as part of their Azure subscription.
|
Name |
Location |
Operating System |
|
wlplanA |
East US |
Linux |
|
wlplanB |
East US |
Windows |
|
wlplanC |
UK South |
Windows |
The company is planning on deploying the following Azure Web App Instances.
|
Name |
Location |
Runtime stack |
|
wlapp1 |
East US |
.Net Core 3.1 |
|
wlapp2 |
East US |
ASP.NET V4.8 |
Which of the following App service plans can you use for wlapp2?
- A. wlplanA only
- B. wlplanB only
- C. wlplanA and wlplanB only
- D. wlplanB and wlplanC only
- E. wlplanA, wlplanB and wlplanC
Explanation:
Answer – B
An ASP.NET v4.8 application CANNOT be deployed to Linux in Azure. Below is the screenshot from the Create Web App screen in Azure Portal.
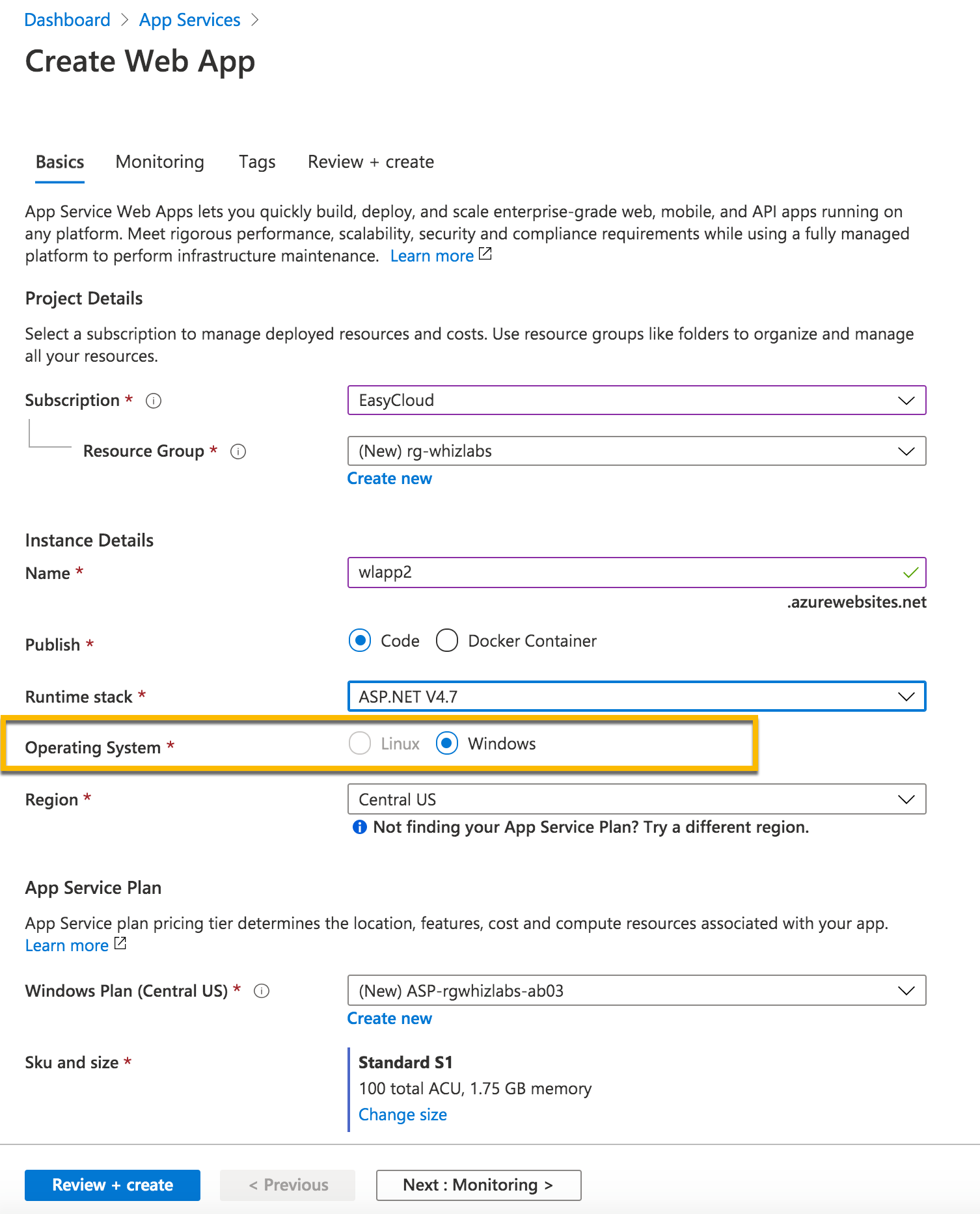
As you can see Linux option is disabled.
All other options are incorrect.
For more information about App Service Plans and Web Apps, please visit the following URL-
A development team has just launched an Azure Kubernetes cluster. They have images placed in an Azure container registry. They want to deploy an application to the cluster using an image from the Azure container registry. Which of the following command could be used to fulfill this requirement?
- A. az kubernetes deploy
- B. kubectl apply
- C. docker run
- D. docker build
Explanation:
Answer – B
To deploy an application to the cluster, you have to use a Kubernetes manifest file. This YAML file contains information about which ACR image to run. Then you can use kubectl apply command to deploy the application to the cluster.
An example of this is provided in the Microsoft documentation.
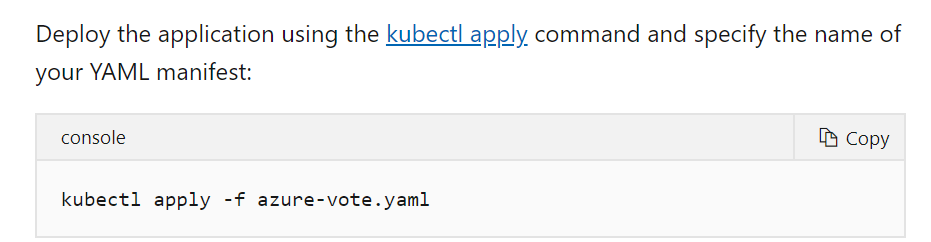
All other options are incorrect.
For more information on working with Kubernetes, please visit the following URL-
Your company has an Azure subscription that contains a Log Analytics workspace named log-staging. You have to get the error events from the table named Event. Which of the following query would you run in the workspace?
- A. Get-Event Event | where ($_.EventType -eq “error”)
- B. Get-Event Event | where ($_.EventType == “error”)
- C. select * from Event where EventType==”error”
- D. search in (Event) “error”
Explanation:
Answer – D
To work with Log Analytics data, you need to use the Kusto Query language (KQL).
An example of this is also given in the Microsoft documentation.
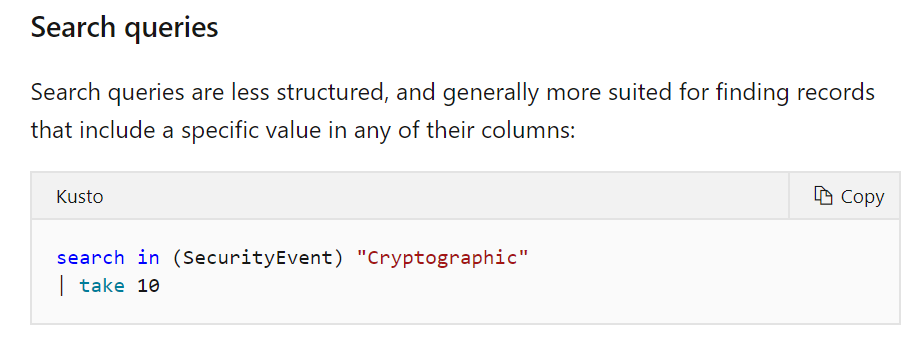
Since this is clearly mentioned in the documentation, all other options are incorrect.
For more information on working with queries in Azure Monitor, please visit the following URLs-
A company has an Azure subscription that contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following resources have been deployed to the subscription.
|
Name |
Resource type |
Resource group |
|
wlnic1 |
Network Interface |
wlgrpA |
|
wlip1 |
Public IP address |
wlgrpA |
|
wlnetwork |
Virtual Network |
wlgrpA |
|
wlstore1 |
Storage account |
wlgrpA |
The network interface is attached to a virtual machine that is located in the wlnetwork virtual network.
Would you be able to move the storage account wlstore1 to the resource group wlgrpB?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, since this is an isolated resource, so it can be moved to the resource group.
For more information on moving Azure resources, please visit the following URL-
A company has an Azure subscription that contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following resources have been deployed to the subscription.
|
Name |
Resource type |
Resource group |
|
wlnic1 |
Network Interface |
wlgrpA |
|
wlip1 |
Public IP address |
wlgrpA |
|
wlnetwork |
Virtual Network |
wlgrpA |
|
wlstore1 |
Storage account |
wlgrpA |
The network interface is attached to a virtual machine that is located in the wlnetwork virtual network.
Would you be able to move the network interface wlnic1 to the resource group wlgrpB?
- A. Yes
- B. No
Explanation:
Answer – A
The network interface can be moved to another resource group, even if it is part of an existing virtual network. We do not need to move the associated resources of network interface along with it. It is "optional" i.e., we can ignore moving of resources. Below is the screenshot of the same.
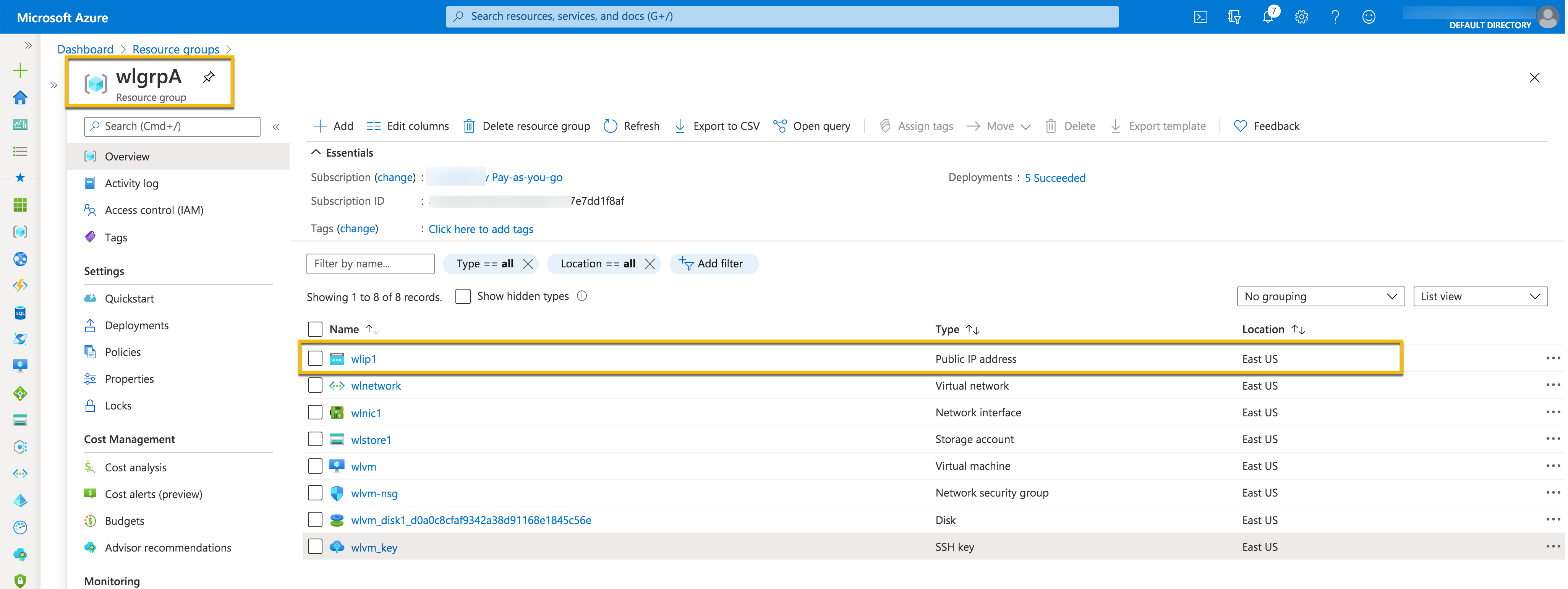
Here is the screenshot of wlgrpA before we move wlnic1 to resource group wlgrpB.
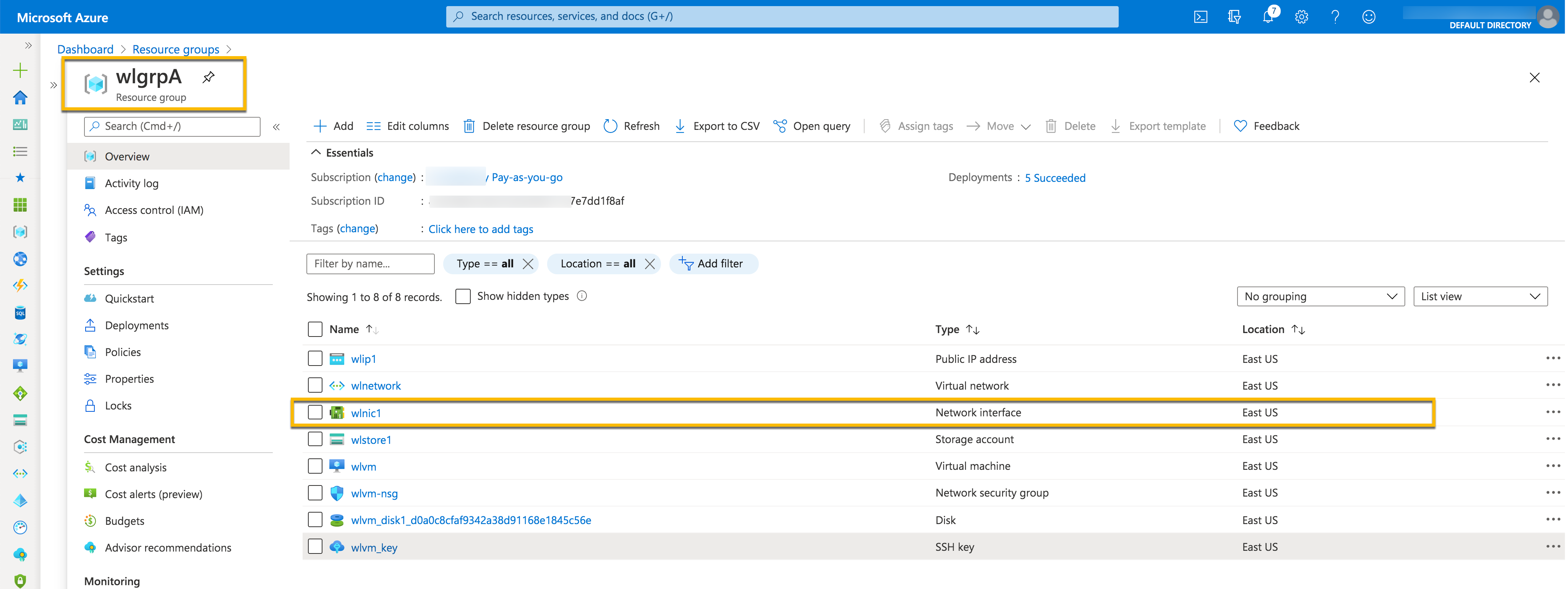
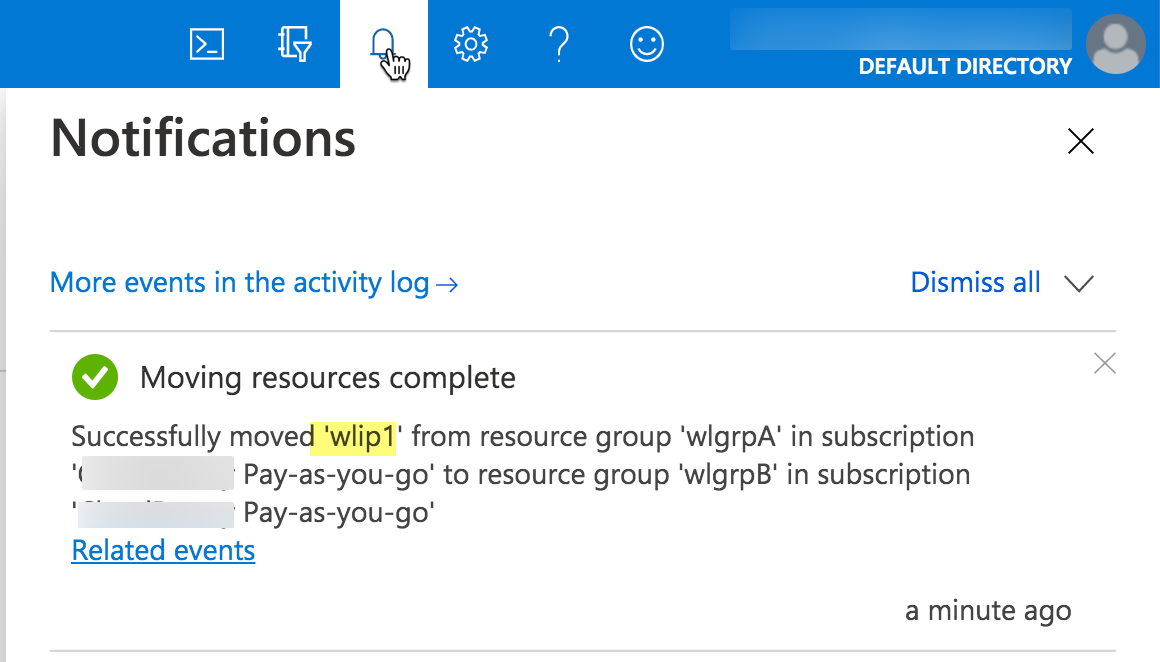
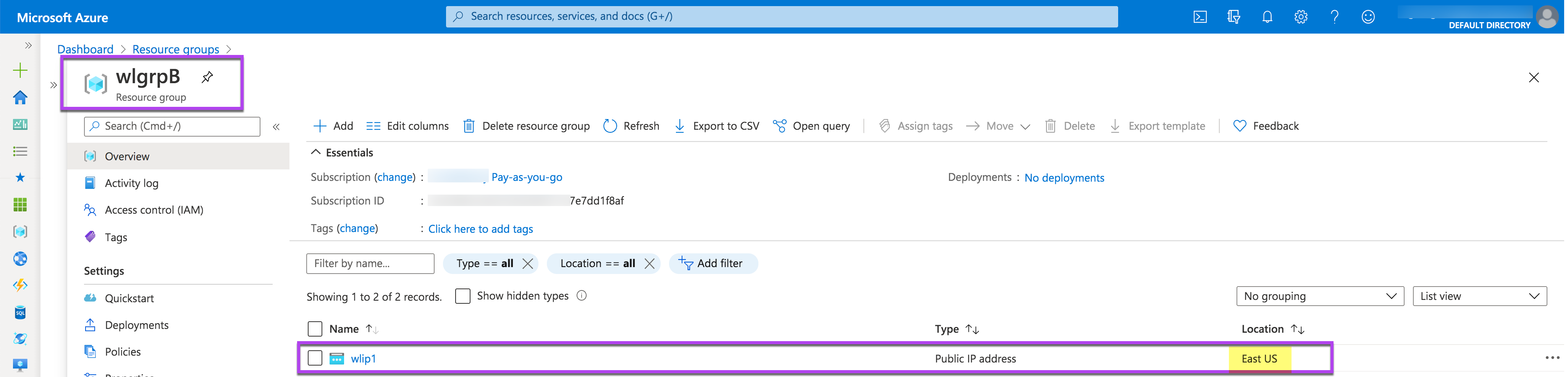
And here are the Notification about the successful move and the screenshot of wlgrpB after the move.

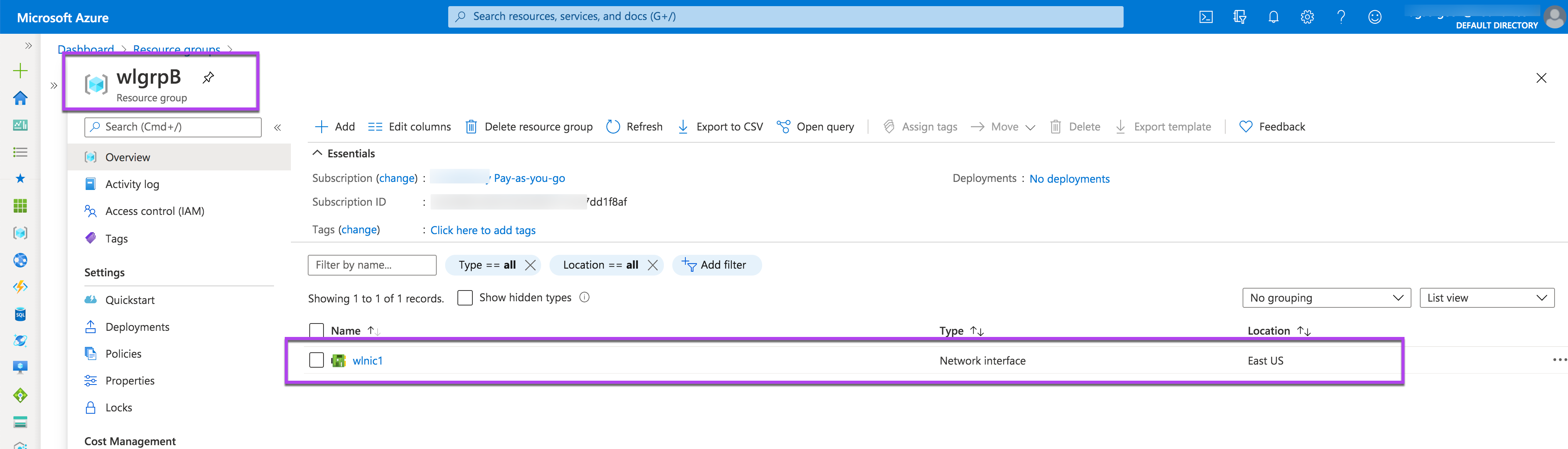
Please do not confuse: you can attach resources with multiple resource groups.
For more information on moving Azure resources, please visit the following URL-
A company has an Azure subscription that contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following resources have been deployed to the subscription.
|
Name |
Resource type |
Resource group |
|
wlnic1 |
Network Interface |
wlgrpA |
|
wlip1 |
Public IP address |
wlgrpA |
|
wlnetwork |
Virtual Network |
wlgrpA |
|
wlstore1 |
Storage account |
wlgrpA |
The network interface is attached to a virtual machine that is located in the wlnetwork virtual network.
If the public IP address is moved to the wlgrpB resource group, would the location of the resource change?
- A. Yes
- B. No
Explanation:
Answer – B
The location of the resource would remain as it is. It’s only the resource group that changes.
Here is the screenshot of wlgrpA before we move wlip1 to resource group wlgrpB.
And here are the Notification about the successful move and the screenshot of wlgrpB after the move.
For more information on moving Azure resources, please visit the following URL-
Your company has an Azure subscription. They are planning to deploy 50 Azure virtual machines that need to be part of an Availability Set. You have to ensure that as many virtual machines are available if the fabric fails or during service periods.
You need to configure the below template for this requirement.
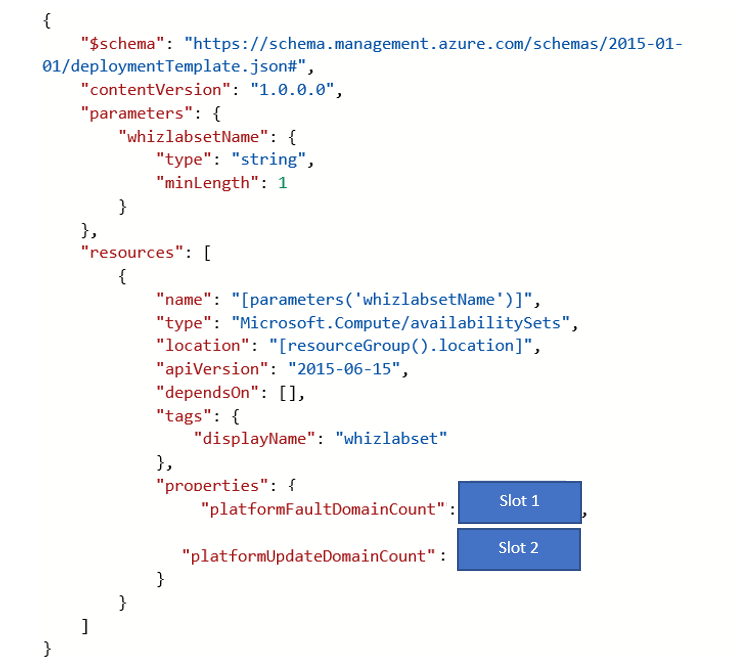
Which of the following would go into Slot 1?
- A. 1
- B. 2
- C. 3
- D. 4
Explanation:
Answer - C
The maximum possible number of fault domains in an availability set is 3. Since we have to ensure that the maximum possible number of virtual machines are available when the fabric fails, we need to choose the value of 3.
The Microsoft documentation mentions the following.
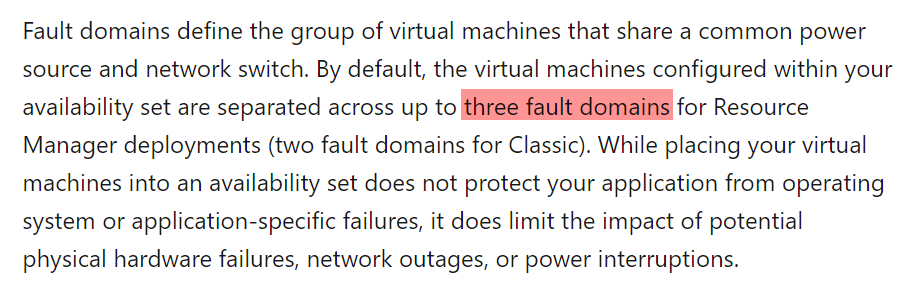
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on availability sets, please visit the following URL-
Your company has an Azure subscription. They are planning to deploy 50 Azure virtual machines that need to be part of an Availability Set. You have to ensure that as many virtual machines are available if the fabric fails or during service periods.
You need to configure the below template for this requirement.
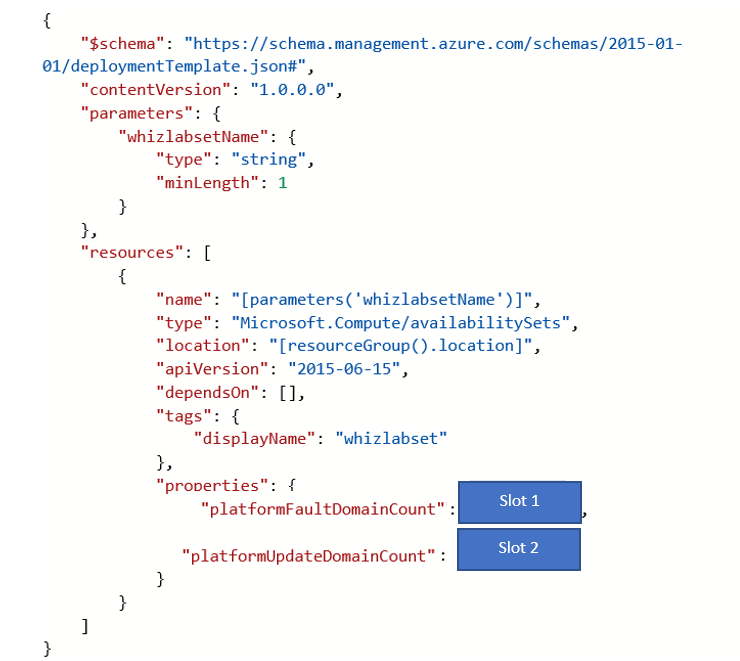
Which of the following would go into Slot 2?
- A. 2
- B. 5
- C. 20
- D. 40
Explanation:
Answer – C
First, we have to ensure that the maximum possible number of virtual machines are available when the fabric fails. We need to choose the value of 20. The maximum number of fault domains possible in an availability set is 3.
The Microsoft documentation mentions the following.
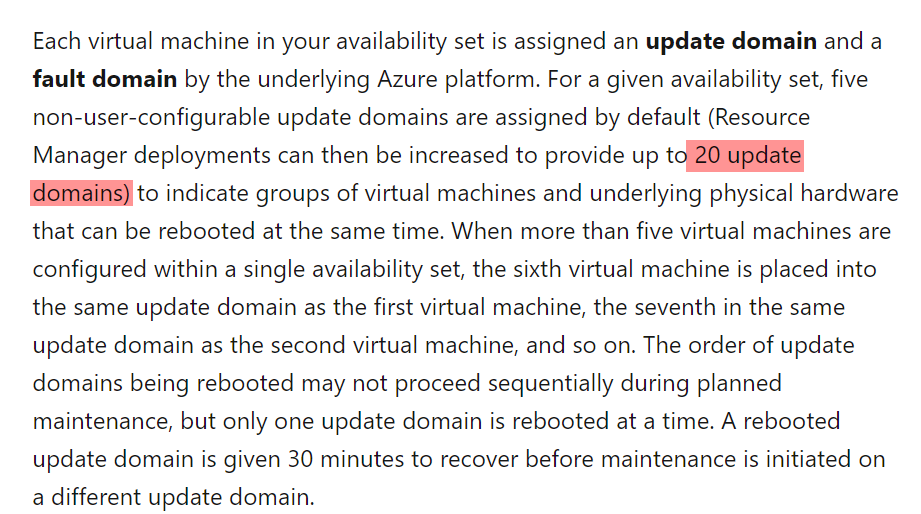 All other options are incorrect.
All other options are incorrect.
For more information on availability sets, please visit the following URL-
A company has two applications, wlappA and wlAppB. Below are the details of each application.
- wlappA – This application is deployed to an Azure Web App. Managed Identity has been enabled for the web app.
- wlappB – This application is deployed to an Azure Container Instance. Managed Identity has been enabled on the container instance.
These applications require access to a storage account. The solution needs to limit the use of secrets. Also, wlappB should only be able to access the storage account for a maximum of 15 days.
Which of the following features needs to be used to allow wlappA to access the storage account?
- A. CORS
- B. Access Keys
- C. Shared Access Signatures
- D. Managed Identity
Explanation:
Answer – D
Managed identities are identities created by ARM (Azure Resource Manager) and assigned to the resource for which it is enabled. The big advantage of managed identity is that its life cycle is tightly coupled with the resource. When a resource is deleted the corresponding Manage Identity is also deleted. This means a security admin will not have to maintain Managed Identity.
Since WlAppA uses Managed Identity, WlAppA can access the Storage Account via IAM. As per requirement, we need to minimize the number of secrets used, so Access keys are not ideal in this scenario.
Option A is incorrect since this is used to enable or disable Cross-Origin Resource sharing.
Option B is incorrect We use this option to have an authorized access to the storage account created, and in this scenario, we are working with managed identities. So no need for access keys for authorized acess.
Option C is incorrect since this is required to provide access to the storage account's resources for a specified period of time.
Option D is correct since we need to minimize the use of secrets. Hence, we can use the Managed Identity to access the Key vault to get the storage account keys' values.
For more information on working with access keys, please visit the following URL:
A company has two applications, wlappA and wlAppB. Below are the details of each application.
- wlappA – This application is deployed to an Azure Web App. Managed Identity has been enabled for the web app.
- wlappB – This application is deployed to an Azure Container Instance. Managed Identity has been enabled on the container instance.
These applications require access to a storage account. The solution needs to limit the use of secrets. Also, wlappB should only be able to access the storage account for a maximum of 15 days.
Which of the following needs to be used to allow wlappB to access the storage account?
- A. CORS
- B. Access Keys
- C. Shared Access Signatures
- D. Managed Identity
Explanation:
Answer – C
Here we need to provide time-bound access. We need to make use of Shared Access Signatures.
The Microsoft documentation mentions the following.
Option A is incorrect since this is used to enable or disable Cross-Origin Resource sharing.
Option B is incorrect since this does not provide time-bound access.
Option D is incorrect since we need to minimize the use of secrets. Hence, we can’t use the Managed Identity to access the Key vault to get the storage account keys' values.
For more information on Shared Access Signatures, please visit the following URL-
Your company needs to deploy an application to a set of three virtual machines. You have to ensure that two virtual machines are always available in the event of a data center failure at any point in time.
You decide to deploy the virtual machines as part of an availability set.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - B
Availability sets can’t protect virtual machines from a data center level failure. Availability zones protect VMs from the data center failure.
You need to distribute your virtual machines across three availability zones.
Here is what Microsoft documentation provides.
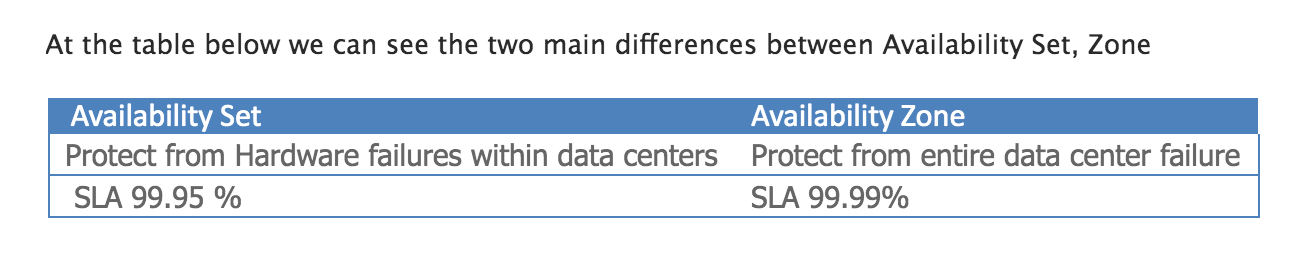
For more information on Availability sets, please visit the following URLs-
Your company needs to deploy an application to a set of three virtual machines. You have to ensure that two virtual machines are always available in the event of a data center failure at any point in time.
You decide to deploy the virtual machines as part of a single availability zone.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
Since an Availability Zone consists of one or more than one datacenters, the answer is No. Because in the case of Availability Zone with only one datacenter, we can't ensure that at any point in time, two virtual machines are always available in the event of a datacenter failure. From the point of best design standards, it's always advisable to have the VMs spread across multiple availability zones.
For more information on Availability Zones, please visit the following URL-
Your company needs to deploy an application to a set of three virtual machines. You have to ensure that two virtual machines are always available in the event of a data center failure at any point in time.
You decide to deploy the virtual machines across three availability zones.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, this is the right approach. The Microsoft documentation mentions the following.
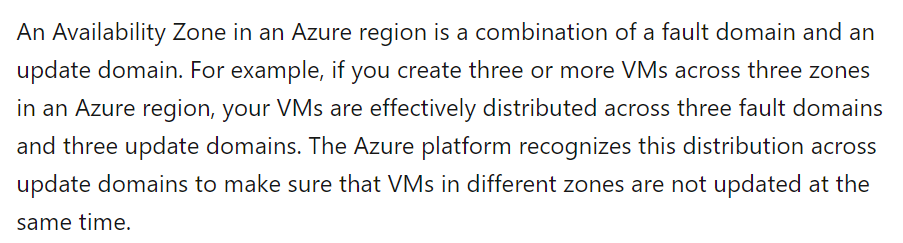
For more information on Availability Zones, please visit the following URL-
Your team needs to deploy an Azure Resource Manager template. This template would be used to deploy 10 Azure Web Apps. The team wants to ensure that the required resources are present in Azure before deploying the template. The implementation needs to minimize costs as much as possible. Which of the following would the team need to deploy as a pre-requisite?
- A. An Azure Application Gateway
- B. An Azure Load Balancer
- C. A single App Service Plan
- D. 10 App Service Plans
Explanation:
Answer – C
For an Azure Web App, you need to have an Azure App Service Plan in place. To minimize costs, you can have a single App Service Plan and link all the Azure Web Apps to that App Service Plan.
The Microsoft documentation mentions the following.
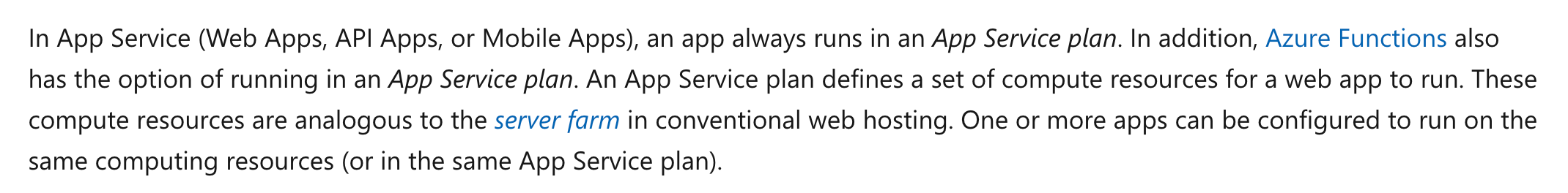
Options A and B are incorrect since you need to have an App Service Plan.
Option D is incorrect since this would be an expensive option.
For more information about App Service Plans, please visit the following URL-
You have an Azure subscription that contains the following resources.
|
Name |
Type |
|
wlbalancer1 |
Load Balancer |
|
wlvm1 |
Virtual Machine |
|
wlvm2 |
Virtual Machine |
The virtual machines run a web site that has the following configuration.
|
Name |
Physical path |
Alias |
|
Root folder |
C:\inetpub\wwwroot\wl |
/ |
|
Temp |
C:\inetpub\wwwroot\Temp |
Temp |
The Load Balancer is configured to route requests across the virtual machines.
A health probe is configured with the below settings.
- Name – wlprobe
- Protocol – HTTP
- Port – 80
- Path - /Temp/wlProbe.htm
- Interval – 5
- Unhealthy threshold – 2
You have to ensure the health probe functions correctly. Which of the following would you implement for this requirement?
- A. Change the unhealthy threshold value on the health probe.
- B. Change the port number value on the health probe to 8080.
- C. On both virtual machines create a file named wlProbe.htm in the C:\inetpub\wwwroot\Temp folder.
- D. On both virtual machines create a file named wlProbe.htm in the C:\inetpub\wwwroot\wl\Temp folder.
Explanation:
Answer – C
We are talking about an HTTP probe that requires a probe on a specified path in this problem. Because the relative path is /Temp, we need to ensure a file in this path on the virtual machines.
The Microsoft documentation mentions the following about HTTP based health probes.
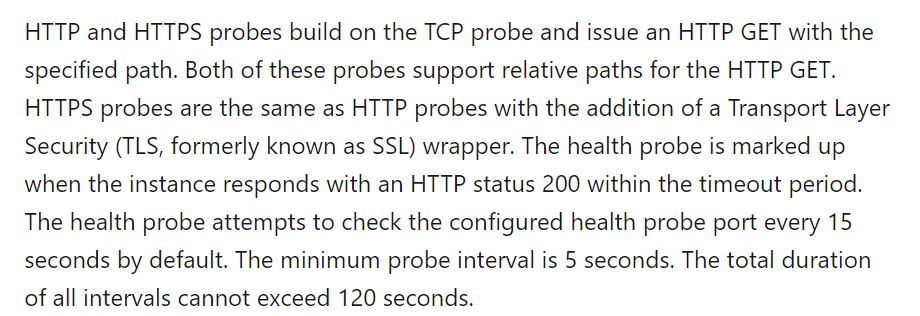
All other options are incorrect.
For more information about health probes, please visit the following URL-
A company has an Azure subscription named staging. The subscription contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following policies have been assigned.
|
Policy Definition Name |
Parameter |
Assigned to |
|
Not allowed resource types |
virtualNetworks |
staging subscription |
|
Allowed resource types |
virtualNetworks |
wlgrpA |
Can you create a virtual network in the resource group wlgrpA?
- A. Yes
- B. No
Explanation:
Answer – B
Since the policy Not allowed resource type is assigned at "Subscription" level, all the resource that belong to it will get impacted. Due to this reason, virtual network cannot be created in wlgrpA resource group.
For more information on Azure policies, please visit the following URL-
Note - for reference please find the screenshot on what Azure says while trying to create a virtual network in wlgrpA.
A company has an Azure subscription named staging. The subscription contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following policies have been assigned.
|
Policy Definition Name |
Parameter |
Assigned to |
|
Not allowed resource types |
virtualNetworks |
staging subscription |
|
Allowed resource types |
virtualNetworks |
wlgrpA |
Can you create a virtual network in the resource group wlgrpB?
- A. Yes
- B. No
Explanation:
Answer – B
A policy is defined at the subscription level with a Deny permission on virtualNetworks. This becomes the permission rule for all resource groups in the subscription.
For more information on Azure policies, please visit the following URL-
A company has an Azure subscription named staging. The subscription contains the following resource groups.
|
Name |
Location |
|
wlgrpA |
East US |
|
wlgrpB |
West US |
The following policies have been assigned.
|
Policy Definition Name |
Parameter |
Assigned to |
|
Not allowed resource types |
virtualNetworks |
staging subscription |
|
Allowed resource types |
virtualNetworks |
wlgrpA |
Can you create a virtual machine in the resource group wlgrpB that doesn't have any other resources?
- A. Yes
- B. No
Explanation:
Answer – B
The virtual machines need to be part of a virtual network. There is a policy definition not to allow virtual networks assigned to Staging Subscription, and since the "parent" is assigned this policy we cannot have a virtual network created, and since VNET is there, the creation of the virtual machine won’t be allowed in any of the resource groups.
For more information about Azure policies, please visit the following URL-
A company has the following virtual machines defined as part of their Azure subscription.
|
Name |
Number of vCPUs |
Location |
State |
|
wlvm1 |
16 |
West US |
Stopped (Deallocated) |
|
wlvm2 |
2 |
West US |
Running |
The subscription has a limit of 20 vCPUs for the West US region.
The company now wants to deploy the following virtual machines.
|
Name |
Number of vCPUs |
Location |
|
wlvm3 |
16 |
West US |
|
wlvm4 |
2 |
West US |
Would the company be able to deploy wlvm3?
- A. Yes
- B. No
Explanation:
Answer – B
Even though wlvm1 is in the Stopped(deallocated) state, this would still count the total number of vCPU's in the region. Hence adding a virtual machine with 16 vCPUs would cross the limit on vCPUs for the region.
The Microsoft documentation mentions the following.

You can easily find the subscription limit of vCPUs for the region using, for example, the following PowerShell command for "West US" region: Get-AzVMUsage -Location "West US".
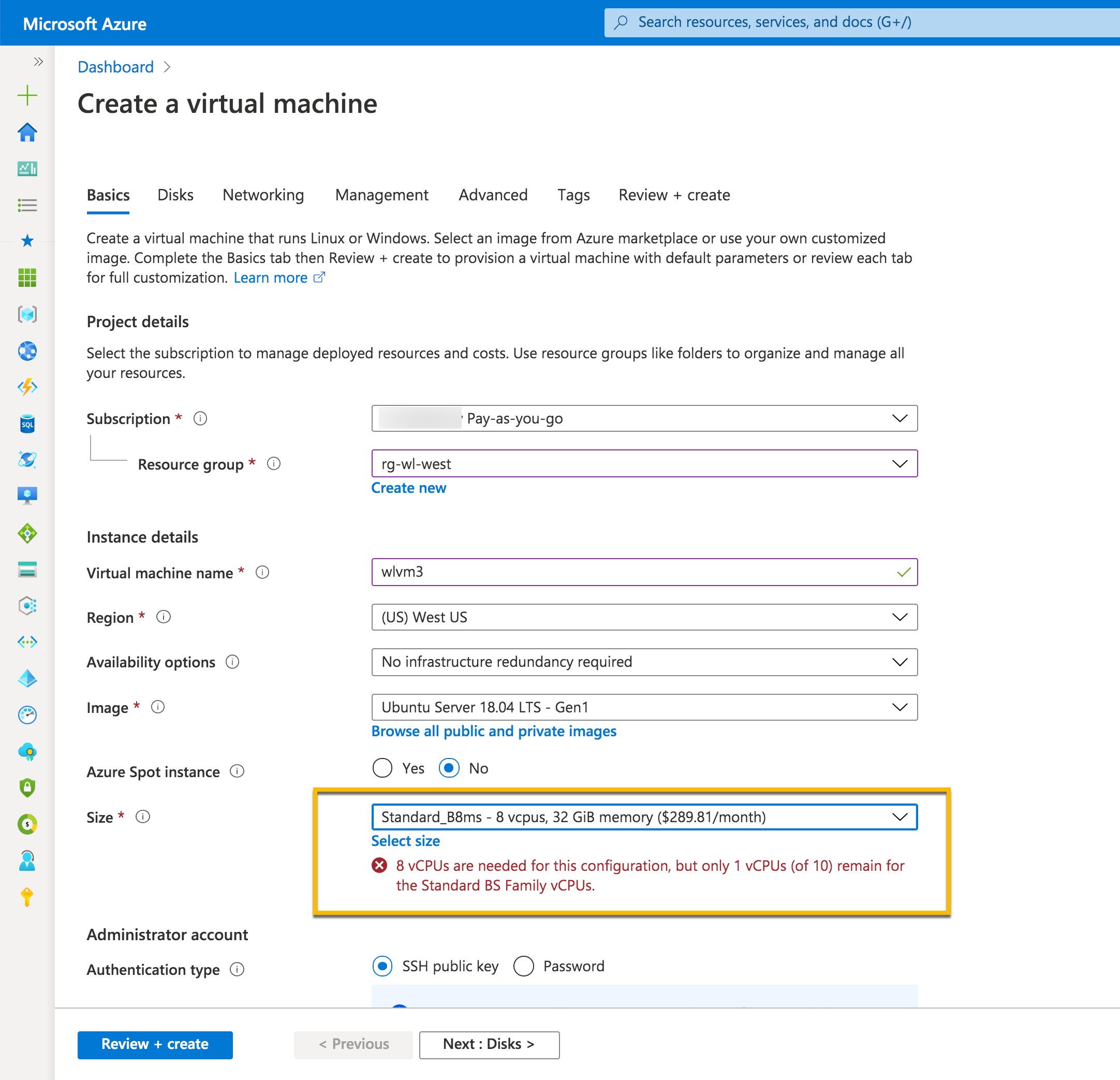
For illustration purposes, we used a subscription with the limit of 10 vCPUs for the West US region. We created two VMs: wlvm1 with 8 vCPUs and wlvm2 with 1 vCPU. We stopped (deallocated) wlvm1.
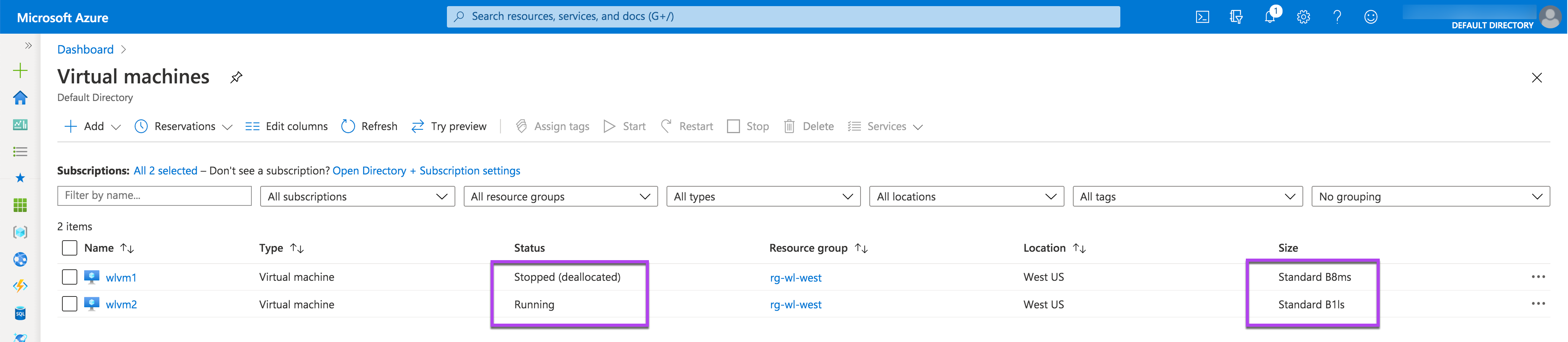
When we tried to create wlvm3 with 8 vCPUs, Azure displayed an error message that we have a limit for 1 vCPU only: this is what left from our subscription limit of 10 vCPUs for the West US region.
For more information on Azure resource limits, please visit the following URLs-
A company has the following virtual machines defined as part of their Azure subscription.
|
Name |
Number of vCPUs |
Location |
State |
|
wlvm1 |
16 |
West US |
Stopped (Deallocated) |
|
wlvm2 |
2 |
West US |
Running |
The subscription has a limit of 20 vCPUs for the West US region.
The company now wants to deploy the following virtual machines.
|
Name |
Number of vCPUs |
Location |
|
wlvm3 |
16 |
West US |
|
wlvm4 |
2 |
West US |
Would the company be able to deploy wlvm4?
- A. Yes
- B. No
Explanation:
Answer – A
Since the total number of vCPUs comes in the limit, one would be able to create a virtual machine of this size.
You can easily find the subscription limit of vCPUs for the region using, for example, the following PowerShell command for "West US" region: Get-AzVMUsage -Location "West US".
For illustration purposes, we used a subscription with the limit of 10 vCPUs for the West US region. We created two VMs: wlvm1 with 8 vCPUs and wlvm2 with 1 vCPU. We stopped (deallocated) wlvm1.

We didn't have any problem creating wlvm4 with 1vCPU within our subscription limit of 10 vCPUs for the West US region.
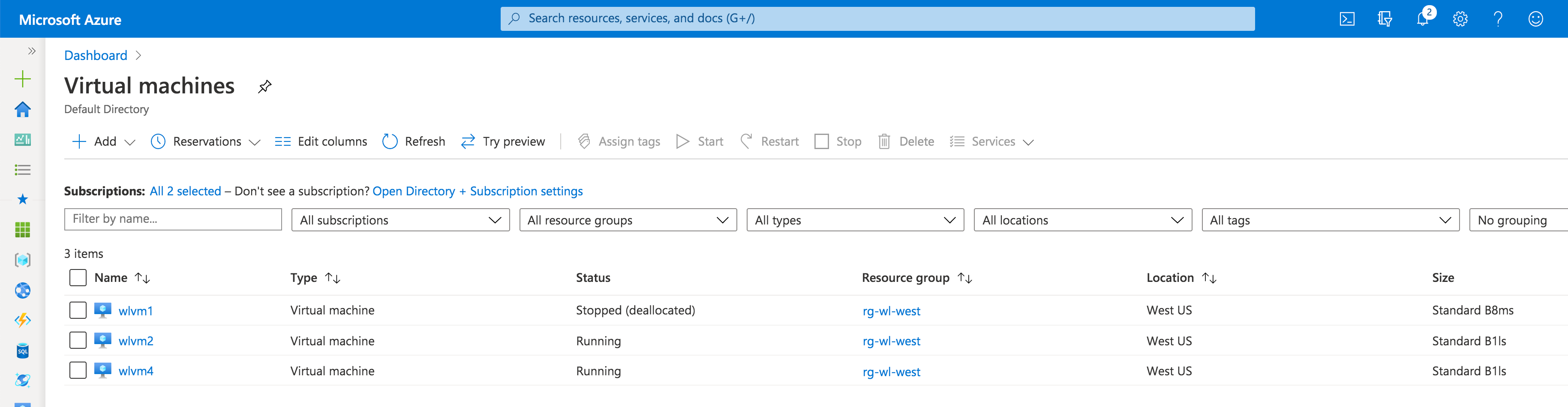
For more information on Azure resource limits, please visit the following URL-
You have an Azure storage account in place. You are planning to enable Azure AD Authentication for the storage account. You want to provide a set of user’s specific permissions to access file shares using Azure AD authentication. Below are the requirements for the users.
- wluserA – Here, the user should be given access to read files shares over SMB
- wluserB – Here, the user should be given access to read, write, delete, and modify NTFS permissions in Azure Storage file shares over SMB.
You need to provide the right permissions, which ensure that the least privileged access is given.
Which of the following RBAC role should be assigned to wluserA?
- A. Storage File Data SMB Share Reader
- B. Storage File Data SMB Share Writer
- C. Storage File Data SMB Share Contributor
- D. Storage File Data SMB Share Elevated Contributor
Explanation:
Answer – A
We can provide the Storage File Data SMB Share Reader RBAC role for this level of access.
The Microsoft documentation mentions the following.
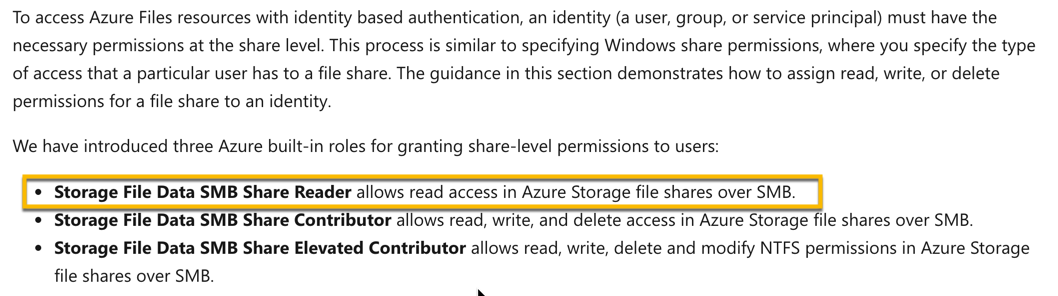
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information about Azure Active Directory authentication for Azure file shares, please visit the following URL-
You have an Azure storage account in place. You are planning to enable Azure AD Authentication for the storage account. You want to provide a set of user’s specific permissions to access file shares using Azure AD authentication. Below are the requirements for the users.
- wluserA – Here, the user should be given access to read files shares over SMB
- wluserB – Here, the user should be given access to read, write, delete, and modify NTFS permissions in Azure Storage file shares over SMB.
You need to provide the right permissions, which ensure that the least privileged access is given.
Which of the following RBAC role should be assigned to wluserB?
- A. Storage File Data SMB Share Reader
- B. Storage File Data SMB Share Writer
- C. Storage File Data SMB Share Contributor
- D. Storage File Data SMB Share Elevated Contributor
Explanation:
Answer – D
We can provide the Storage File Data SMB Share Elevated Contributor RBAC role for this level of access.
The Microsoft documentation mentions the following.
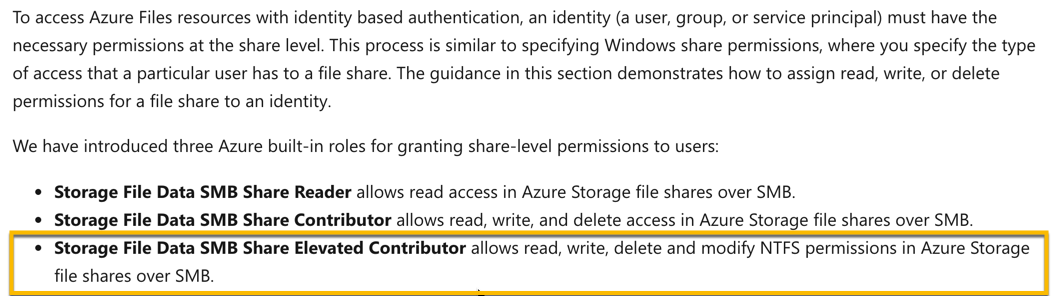
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information about Azure Active Directory authentication for Azure file shares, please visit the following URL-
Which of the following needs to be implemented on the Azure virtual network to deploy the Azure Bastion Host?
- A. Add a new address space.
- B. Add a new subnet.
- C. Enable DDoS protection for the virtual network.
- D. Add a service endpoint.
Explanation:
Answer – B
To create an Azure Bastion host, you need to have the AzureBastionSubnet created as part of the virtual network.
This is mentioned in the Microsoft documentation.


All other options are incorrect.
Reference: Tutorial: Deploy Bastion using specified settings: Azure portal | Microsoft Learn
Which of the following should be set for the following requirement?
“Users who join their devices should use an additional authentication method during the process of joining devices.”
- A. Option 1
- B. Option 2
- C. Option 3
- D. Option 4
Explanation:
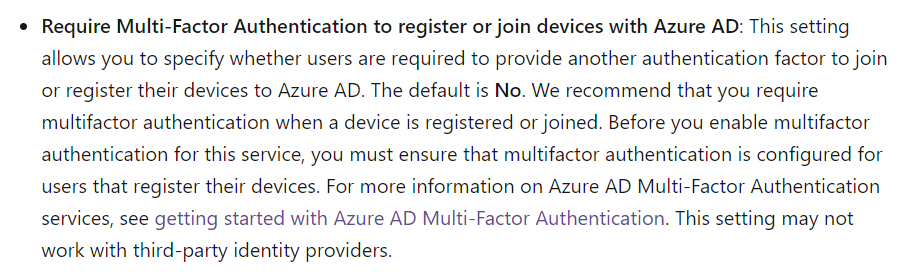
Correct Answer – D
For this, we need to set the option for Require Multi-Factor Auth to join devices.
This is mentioned in the Microsoft documentation.
All other options are incorrect.
For more information about device management, please visit the following URL-
What is the minimum number of policies required for taking the backup of windows virtual machines hosting the web servers?
- A. 1
- B. 2
- C. 3
- D. 4
Explanation:
Answer – A
The minimum number of backup policies required is "1" i.e., Option A reason using one single policy we can have a backup of 100 VMs and in our scenario, we have 2 VMs with a web application. Coming to the database, we do not need to define any policy.
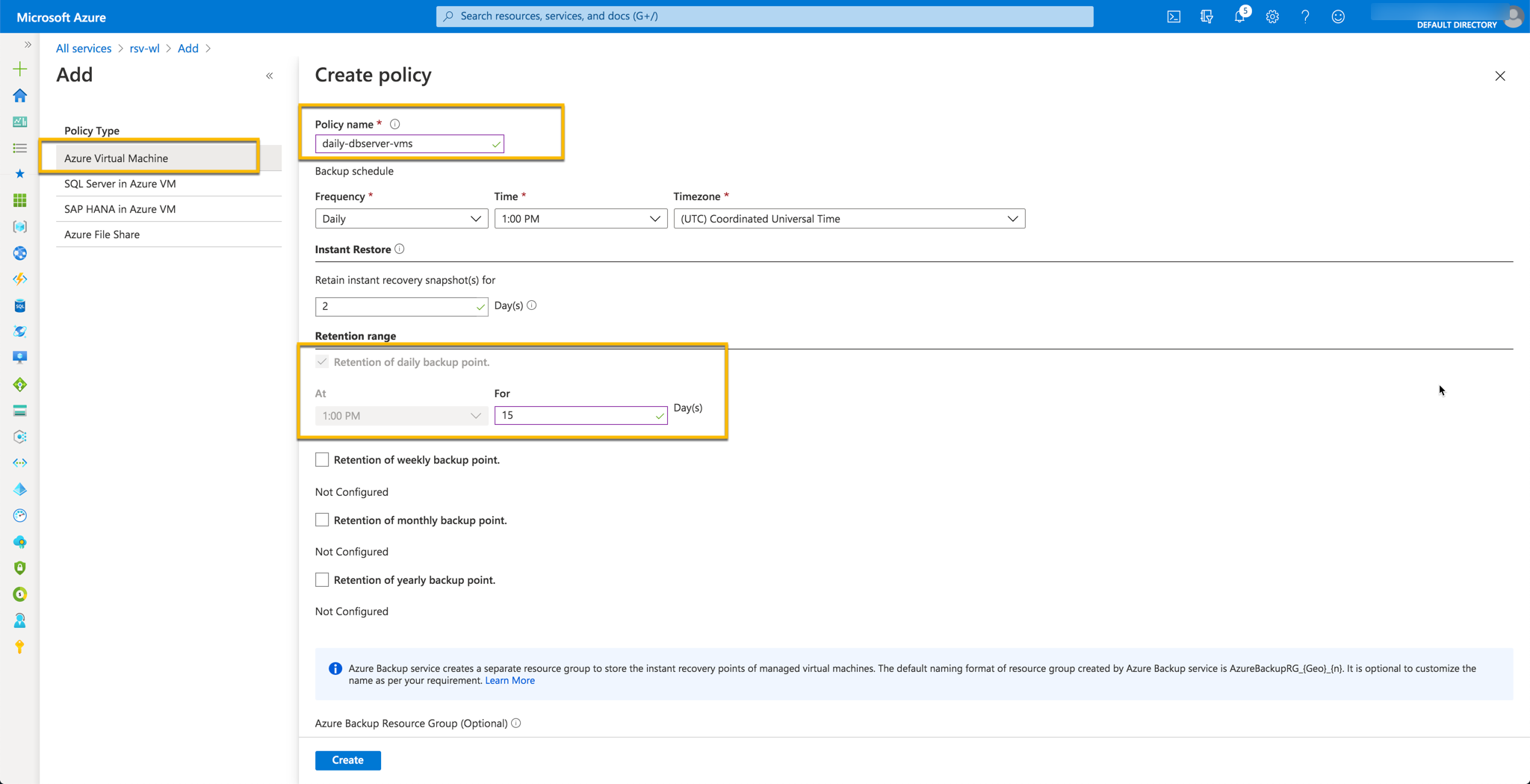
For more information on Azure backup for virtual machines, please visit the following URL-
Can you send the security events of the virtual machines to the Log Analytics workspace?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, you can. Even though the virtual machines and the Log Analytics workspace are in separate locations, you can still connect the virtual machines to the workspace.
For more information on collecting data into a Log Analytics workspace, please visit the following URL-
You need to troubleshoot network security group rules for a virtual machine.
What Azure Monitor Insight for Networks component should you use for an integrated view of the NSG configuration status?
- A. Connectivity
- B. Network health and metrics
- C. Traffic
- D. Diagnostics Toolkit
- E. Availability
Explanation:
Correct Answer: C
Azure Monitor Insights for Networks brings several diagnostics and monitoring tools under one roof. It includes the following components:
- Network health and metrics — provides the integrated view of the networking resources' health, metrics, and alerts. Users can filter resources by subscriptions, resource group, and type.
- Connectivity — provides insights into the Connection Monitor tests. Test Information is divided into two categories: Sources and Destinations. Users can filter resources by subscriptions, resource group, source and destination types, and reachability criteria.
- Traffic — provides information about all NSGs and their Flow logs and Traffic Analytics configurations.
There is an additional set of the tools — Diagnostics Toolkit. It helps to troubleshoot the networks. The toolkit includes the following services: Capture packets on virtual machines, Troubleshoot VPN, Troubleshoot connectivity, Identify next hops, Diagnose traffic filtering issues.
The Traffic tab focuses only on network security groups (NSG). There are two tools to troubleshoot the NSGs: Flow logs and Traffic Analytics. If you select the Networks item (Number 2) under the Insights section of the Monitor blade, the portal opens the Monitor Networks screen (Number 1). Then you can click on the Traffic tab (Number 3). This tab presents information about NSGs. You can click on the panel button (Number 5), and the portal opens the table with the NGSs' details on the bottom of the screen (Number 6). The table provides information about the configuration status of the Flow logs (Number 7) and Traffic Analytics (Number 8) for each NSG. You can filter the table’s entries using the predefined checkboxes (Number 4).
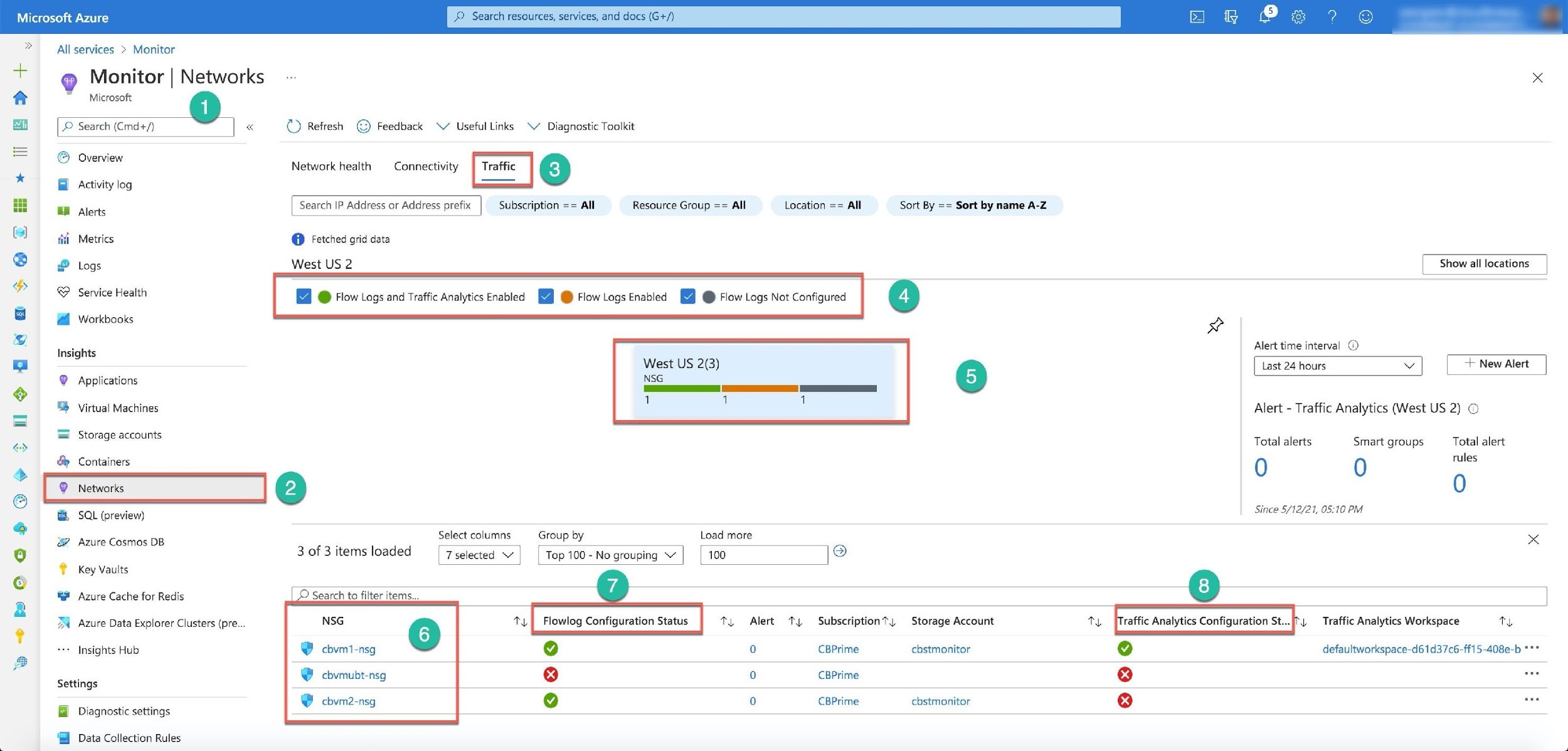
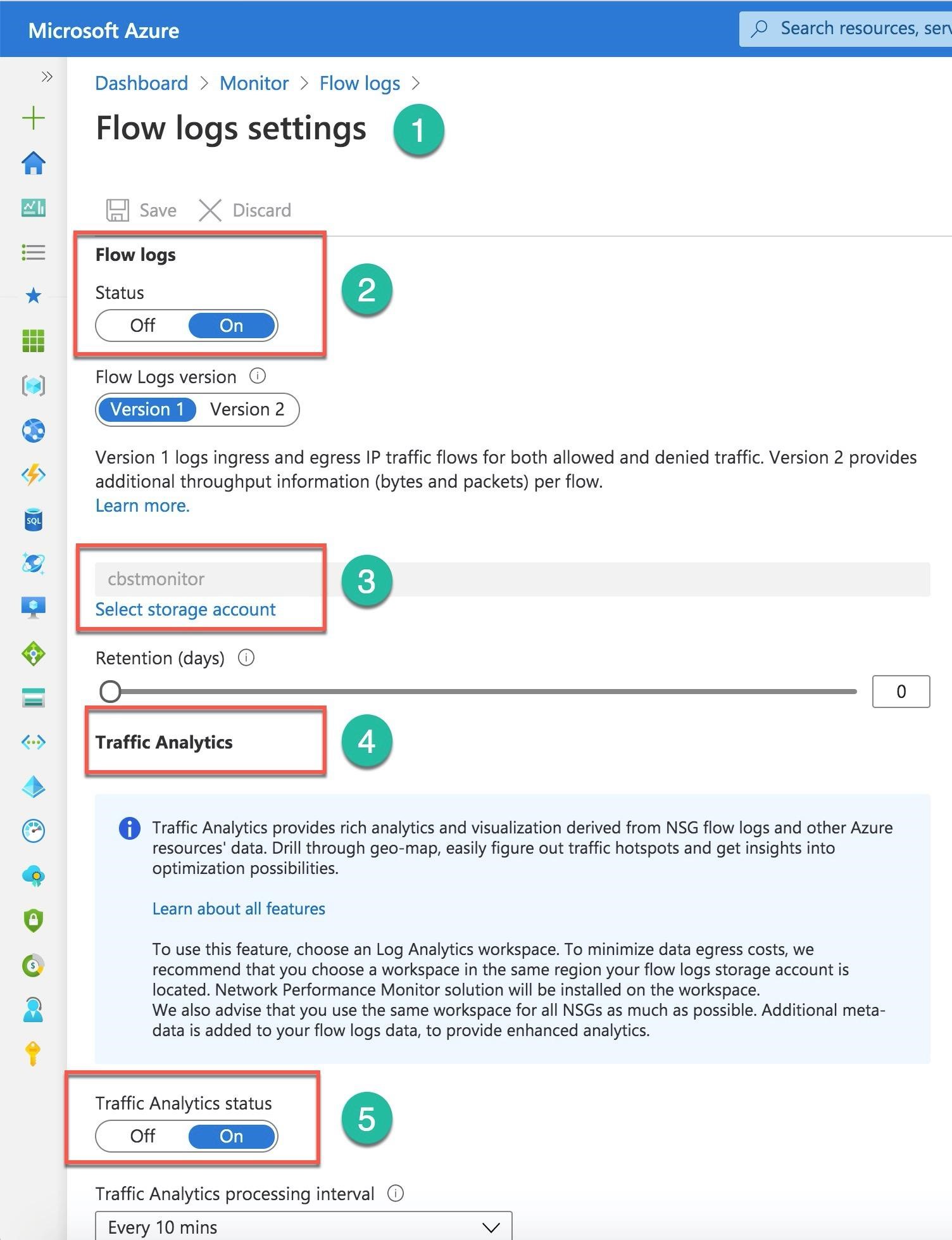
To enable the logs and analytics, you click on the signs in one of the columns: the Flowlog Configuration Status or the Traffic Analytics Configuration status. The portal opens a new screen for Flow logs Settings (Number 1). You can enable the logs (Number 2), select the log's version, and provide a storage account for the logs (Number 3) with the number of days for the blog retention. The same screen provides options for Traffic Analytics as well (Number 4). You can enable this service (Number 5), set the processing interval for Every hour or Every 10 minutes, and select the Log Analytics workspace.
All other options are incorrect.
For more information about the Azure Monitor Insights for Networks and Traffic component, please visit the below URLs:
- https://docs.microsoft.com/en-us/azure/azure-monitor/insights/network-insights-overview#traffic
- https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-overview
- https://docs.microsoft.com/en-us/azure/network-watcher/traffic-analytics
- https://channel9.msdn.com/Shows/Azure-Friday/Get-a-unified-network-monitoring-experience-with-Network-Insights

