





| No. | Domain | Total Question | Correct | Incorrect | Unattempted | Marked for Review |
|---|---|---|---|---|---|---|
| 1 | Manage Azure identities and governance | 17 | 0 | 0 | 17 | 0 |
| 2 | Implement and manage storage | 14 | 0 | 0 | 14 | 0 |
| 3 | Deploy and manage Azure compute resources | 9 | 0 | 0 | 9 | 0 |
| 4 | Configure and manage virtual networking | 13 | 0 | 0 | 13 | 0 |
| 5 | Monitor and back up Azure resources | 2 | 0 | 0 | 2 | 0 |
| Total | All Domains | 55 | 0 | 0 | 55 | 0 |
A team member has created a point-to-site VPN connection between a computer named "WorkstationA" and an Azure Virtual Network. Another point-to-site VPN connection needs to be made between the same Azure Virtual Network and a computer named "WorkstationB." The VPN client package was generated and installed on "WorkstationB." You need to ensure that you can create a successful point-to-site VPN connection.
You decide to export the "Workstation A" client certificate and install it on "Workstation B."
Would this solution fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, this is one of the requirements. This is also mentioned in the Microsoft documentation.
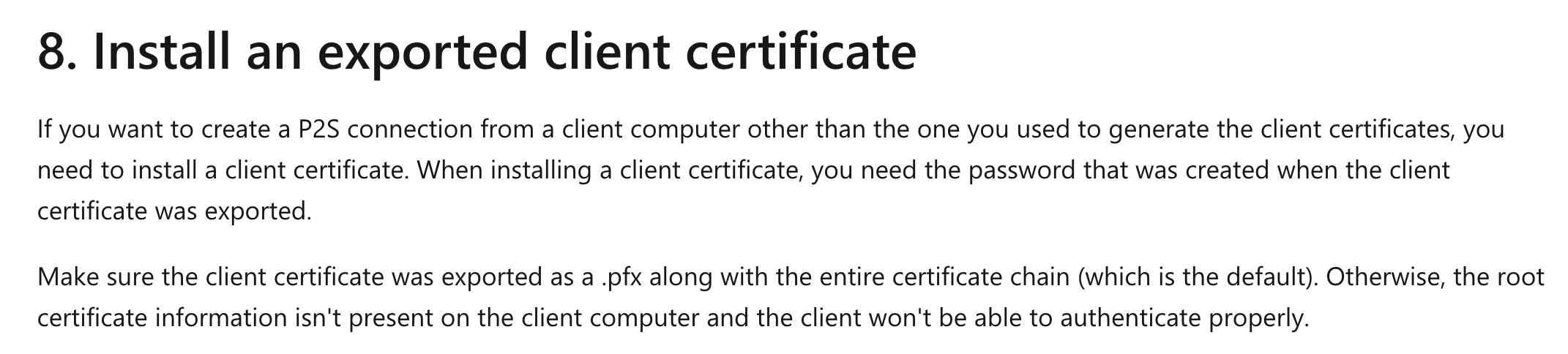
For more information on creating point-to-site VPN connections, please visit the below URL-
You have a storage account named whizlabstore. You have created a file share named demo using the file service. You need to ensure that users can connect to the file share from their home computers. Which of the following port should be open to provide the connectivity?
- A. 80
- B. 443
- C. 445
- D. 3389
Explanation:
Answer – C
To access files from home computers, users have to use SMB protocol that expects port 445 to be open.
This is clearly given in the Microsoft documentation.
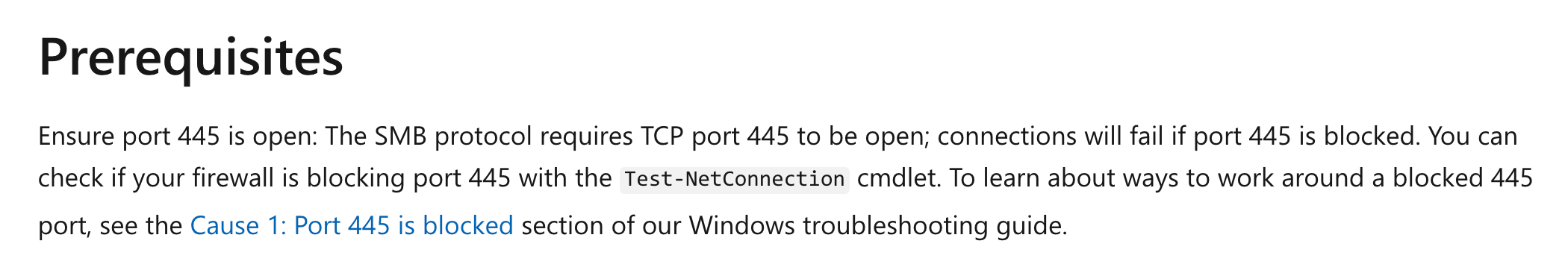
For more information on using file shares in Azure, please visit the below URL-
A company has created a storage account in their Azure subscription. The name of the storage account is whizlabstore. They have also created a file share named demo. They need to access the files in the file share via a UNC path.
You need to fill in the following blocks to ensure that the right UNC path is provided.
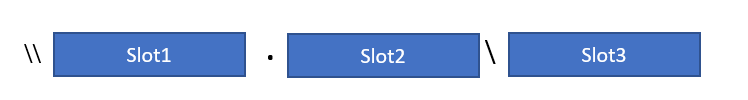
Which of the following needs to go into Slot1?
- A. blob
- B. blob.core.windows.net
- C. portal.azure.com
- D. file
- E. file.core.windows.net
- F. whizlabstore
- G. demo
Explanation:
Answer – F
To work with UNC path format, you have to mount the Azure file share with File Explorer. The UNC path format is:
\\.file.core.windows.net\
or in our case:
\\whizlabstore.file.core.windows.net\demo
For more information on using Aure file share service, please visit the below URLs-
https://docs.microsoft.com/en-us/azure/storage/files/storage-how-to-use-files-windows
https://docs.microsoft.com/en-us/windows/win32/fileio/naming-a-file?redirectedfrom=MSDN
A company has created a storage account in their Azure subscription. The name of the storage account is whizlabstore. They have also created a file share named demo. They need to access the files in the file share via a UNC path.
You need to fill in the following blocks to ensure that the right UNC path is provided.
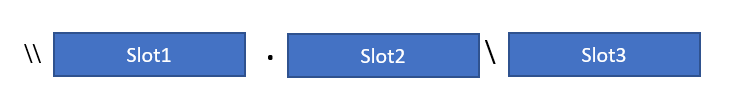
Which of the following needs to go into Slot2?
- A. blob
- B. blob.core.windows.net
- C. portal.azure.com
- D. file
- E. file.core.windows.net
- F. whizlabstore
- G. demo
Explanation:
Answer – E
To work with UNC path format, you have to mount the Azure file share with File Explorer. The UNC path format is:
\\.file.core.windows.net\
or in our case:
\\whizlabstore.file.core.windows.net\demo
For more information on using Aure file share service, please visit the below URLs-
A company has created a storage account in their Azure subscription. The name of the storage account is whizlabstore. They have also created a file share named demo. They need to access the files in the file share via a UNC path.
You need to fill in the following blocks to ensure that the right UNC path is provided.
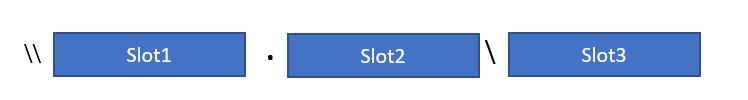
Which of the following needs to go into Slot3?
- A. blob
- B. blob.core.windows.net
- C. portal.azure.com
- D. file
- E. file.core.windows.net
- F. whizlabstore
- G. demo
Explanation:
Answer – G
UNC stand for Universal naming convention. UNC is used for Microsoft Windows for accessing shared network folder .and printer. Generic naming convention for UNC is given below:
\\host-name\share-name\file path
To work with UNC path format, you have to mount the Azure file share with File Explorer. The UNC path format is:
\\.file.core.windows.net\
or in our case:
\\whizlabstore.file.core.windows.net\demo
From the above is it clear that G is the correct answer all other answers are wrong.
For more information on using Azure file share service, please visit the below URLs-
Would Virtual Machines launched in the whizlab-client virtual network automatically get registered in the private domain of private.whizlabs.com if auto registration is enabled?
- A. Yes
- B. No
Explanation:
Answer – A
So below is the representation of the network based on the details given in the question.
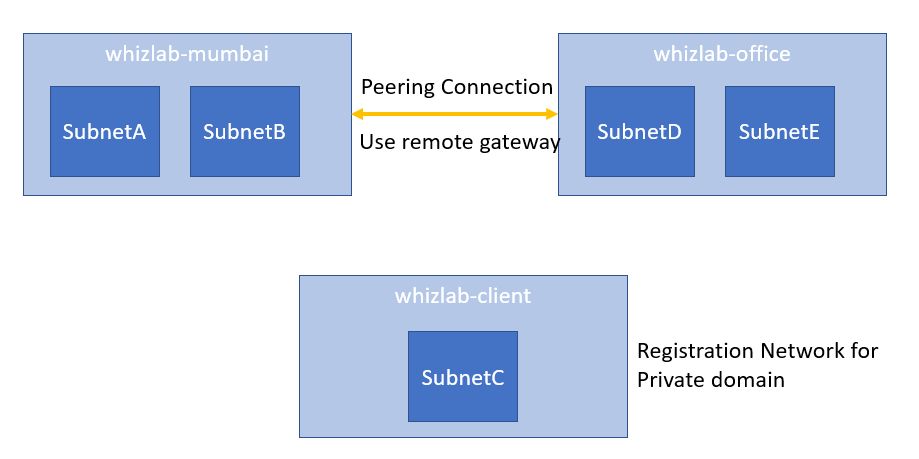
Since the whizlab-client is registered with the private hosted zone, automatic registration of VM’s is possible.
This is also given in the Microsoft documentation.

For more information on private DNS zones, please visit the below URL-
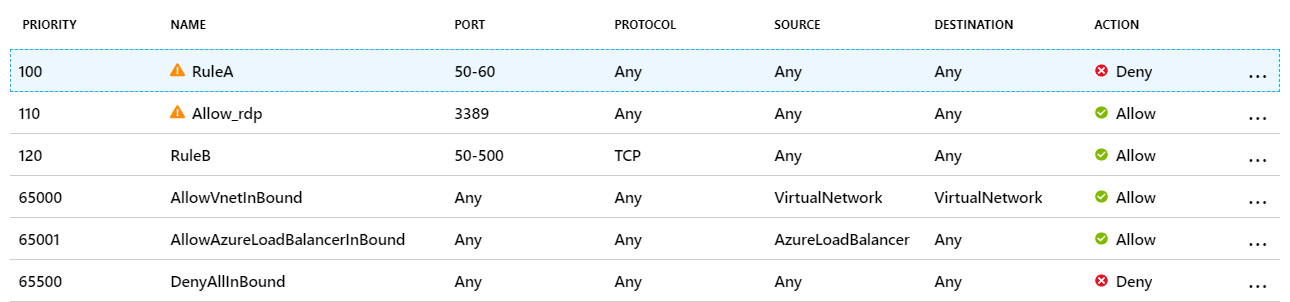
A company has set up a Virtual Machine in Azure. A web server listening on port 80 and a DNS server has been installed on the Virtual machine. A network security group is attached to the network interface for the virtual machine. The rules for the NSG are given below.
Inbound Rules
Outbound Rules
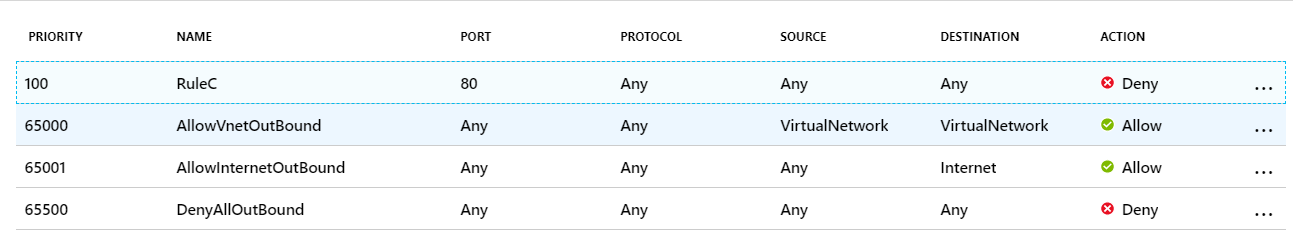
If RuleB is deleted/omitted, please select the service through which Internet users connect to the virtual machine.
- A. Through the web server
- B. Through the DNS server
- C. both Web and DNS servers
- D. Through RDP
- E. Through RDP, Web, and DNS servers
Explanation:
Answer – D
If RuleB is deleted, users won’t be able to access port 80 and the web server.
There is a Deny rule of RuleA for ports 50-60. Since DNS listens on port 53, you will not be able to access the DNS server. But you will still be able to connect to the virtual machine using Remote Desktop Protocol (RDP) under the Allow_rdp rule.
Because of this logic, all other options are incorrect.
For more information on network security, please visit the below URL-
Your company has set up a storage account in Azure, as shown below.
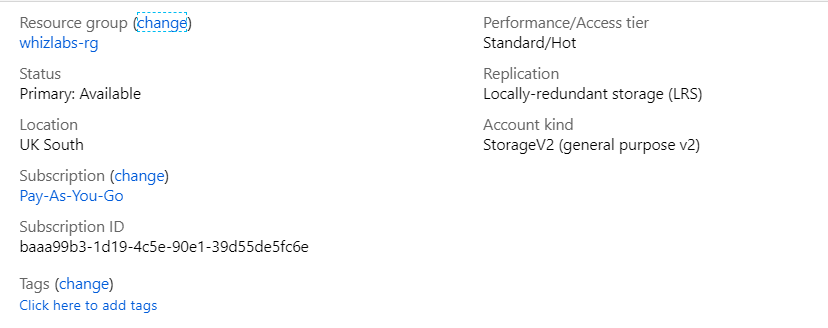
The company needs to allow only connections to the storage account from an IP address range of 51.107.2.0 to 51.107.2.255. From which of the following section of the storage account would you modify to fulfill this requirement?
- A. Networking
- B. Advanced security
- C. Soft Delete
- D. Lifecycle Management
Explanation:
Answer – A
This can be done from the Networking, as shown below.
Ensure to click on “Selected networks” and then enter the IP address range.
Since this is clear from the implementation, all other options are incorrect.
For more information on the Firewall and virtual network feature, please visit the below URL-
https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security?tabs=azure-portal
Your company has set up a storage account in Azure, as shown below.
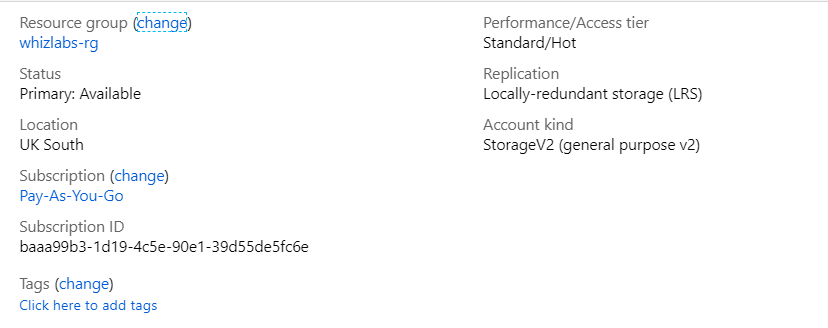
There is a requirement to retain any blob data that might accidentally be deleted. The deleted data needs to be retained for 14 days. From which of the following section of the storage account would you modify to fulfill this requirement?
- A. Firewall and virtual networks
- B. Advanced security
- C. Soft Delete
- D. Lifecycle Management
Explanation:
Answer – C
This can be done from the soft delete option from the storage account at any time by using the Azure portal, PowerShell, or Azure CLI.
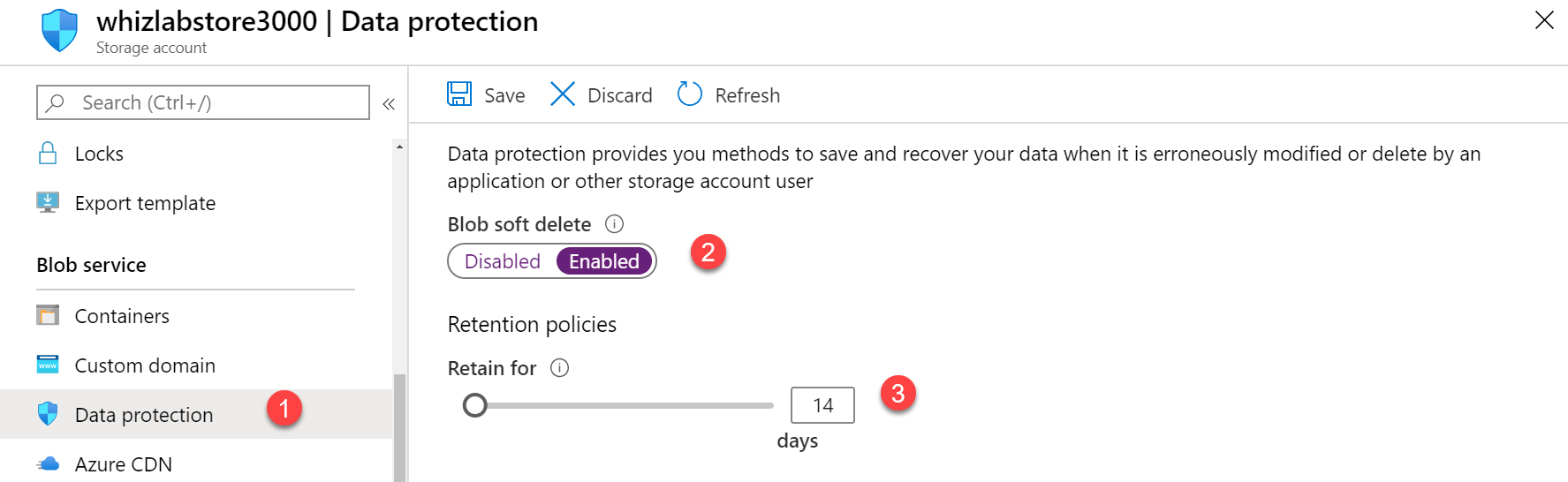
Blob soft delete protects an individual blob, snapshot, or version from accidental deletes or overwrites by maintaining the deleted data in the system for a specified period of time. During the retention period, you can restore a soft-deleted object to its state at the time it was deleted.

Since this is clear from the implementation, all other options are incorrect.
Reference: Enable soft delete for blobs - Azure Storage | Microsoft Learn
A company wants to deploy a virtual machine using a Resource Manager template. The template needs to be submitted via Azure CLI commands. The template is stored in a file named storage.json.
You need to complete the below CLI command.
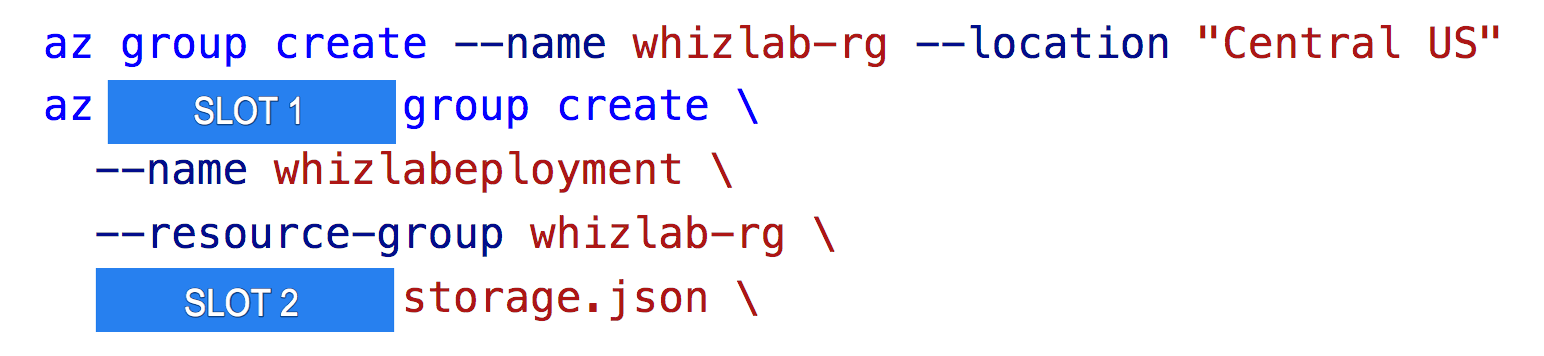
Which of the following would go into SLOT 1?
- A. template
- B. deployment
- C. resource
- D. vm
Explanation:
Answer - B
SLOT 1 covers the word "deployment".
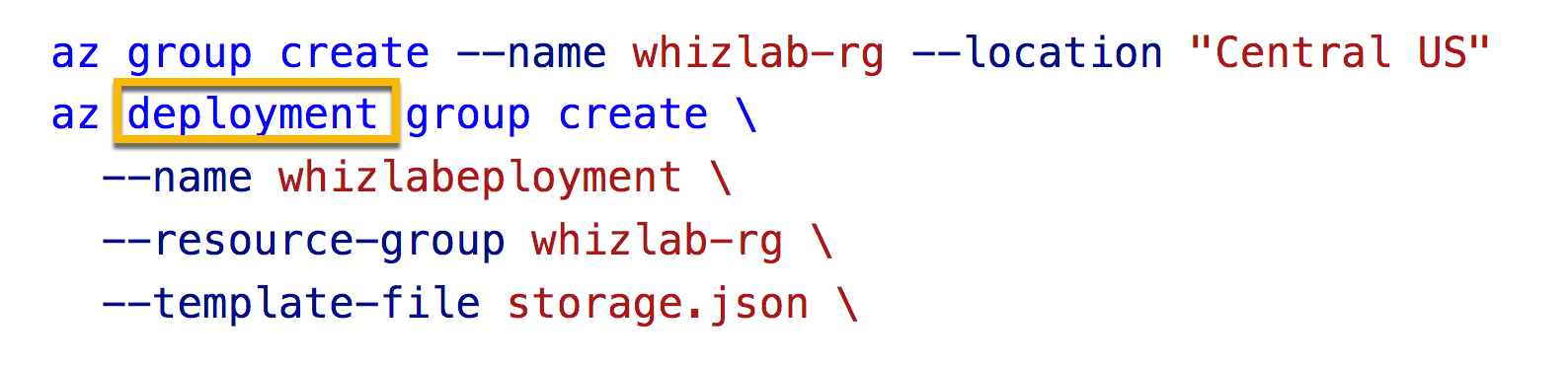
All other options are incorrect.
For more information on deploying templates via the CLI, please visit the below URL-
A company wants to deploy a virtual machine using a Resource Manager template. The template needs to be submitted via Azure CLI commands. The template is stored in a file named storage.json.
You need to complete the below CLI command.

Which of the following would go into SLOT 2?
- A. --template
- B. --template-uri
- C. --template-file
- D. --template-resource
Explanation:
Answer - C
SLOT 2 covers "--template-file" option.
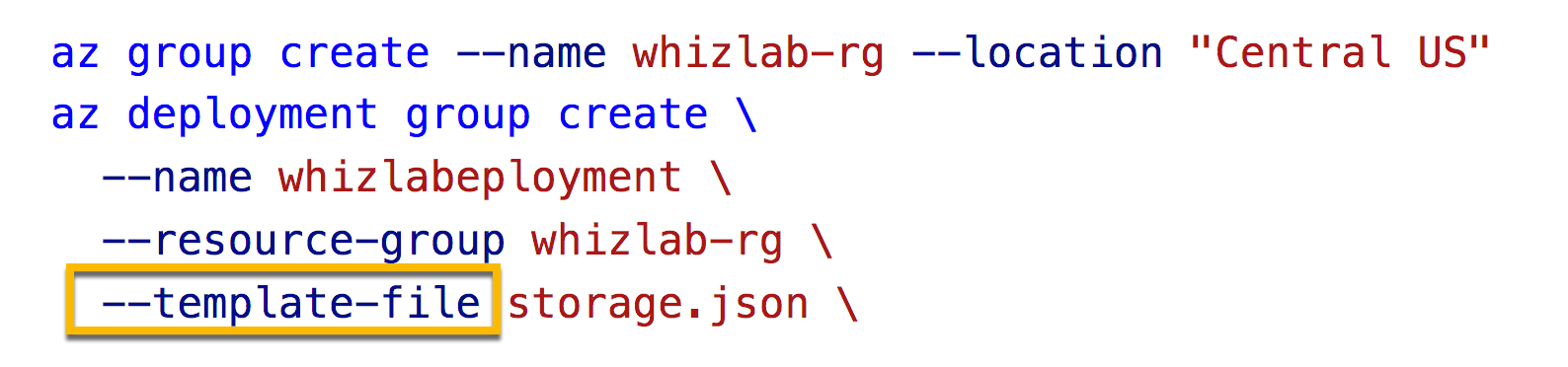
All other options are incorrect.
For more information on deploying templates via the CLI, please visit the below URL-
A company has set up an Azure subscription and a tenant. They want to ensure that only Virtual Machines of a particular SKU size can be launched in their Azure account.
They decide to implement Role-Based access control.
Does this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer — B
Role-based access control can be used to restrict access to resources. RBAC does not put any governance, regarding type of resources to be created. If you need to limit the resource creation, like provision VM's only of a particular SKU's, you need to implement Azure policies.
You can use allowed virtual machine policy in this scenario:
- Allowed Virtual Machine SKUs (Deny): Specifies a set of virtual machine SKUs that you can deploy as parameter to this policy. Any VM SKU which is not in the parameter list, cannot be created as per this policy. Users will get a message “VM SKU “is not allowed by the policy -- Allowed Virtual Machine SKUs.
For more information on policy and role-based access control, please refer to following list.
Policy -- Overview of Azure Policy - Azure Policy | Microsoft Docs
RBAC -- https://docs.microsoft.com/en-us/azure/role-based-access-control/overview
A company has set up an Azure subscription and a tenant. They want to ensure that only Virtual Machines of a particular SKU size can be launched in their Azure account.
They decide to implement Azure locks.
Does this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - B
Azure locks are used to prevent users from accidentally deleting or modifying critical resources. If you need to limit the resource creation, like provision VM only of a particular SKU, you need to implement Azure policies.
For more information on Azure locks, please visit the below URL-
A company has set up an Azure subscription and a tenant. They want to ensure that only Virtual Machines of a particular SKU size can be launched in their Azure account.
They decide to implement Azure policies.
Does this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - A
Yes, this can be done with Azure policies. There is also already an in-built policy which can implement this policy as shown below.
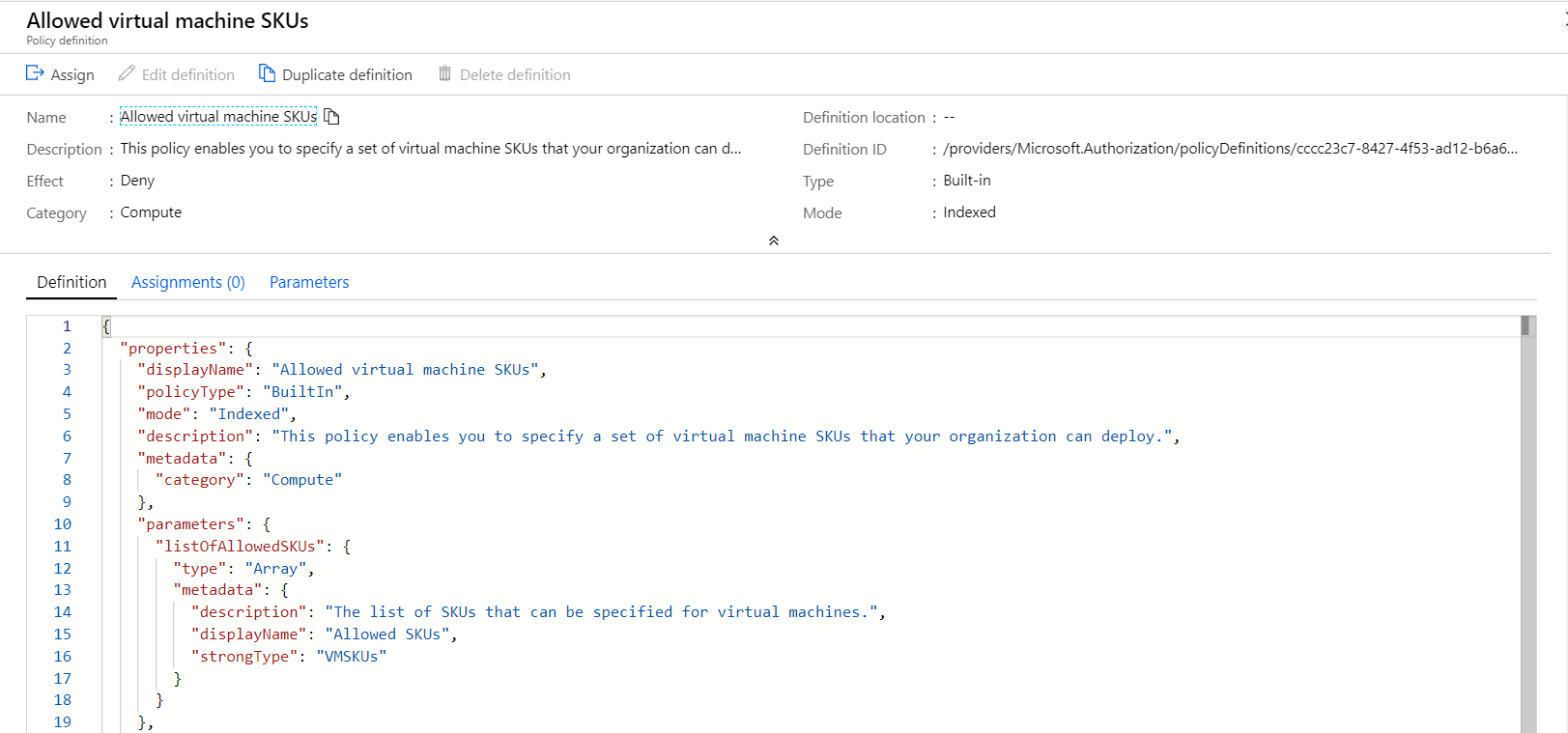
For more information on an example on this, please visit the below URL-
A company plans to use Azure Network watcher to perform the following tasks.
- Find out if a network security rule prevents a network packet from reaching a virtual machine hosted in an Azure virtual network.
- Find out if there is outbound connectivity between an Azure virtual machine and an external host.
Which of the following Network watcher feature would you use for the following requirement?
"Find out if a network security rule is preventing a network packet from reaching a virtual machine hosted in an Azure virtual network."
- A. IP Flow Verify
- B. Next Hop
- C. Packet Capture
- D. Traffic Analysis
Explanation:
Answer – A
This can be done with the IP Flow Verify feature. The Microsoft documentation mentions the following.
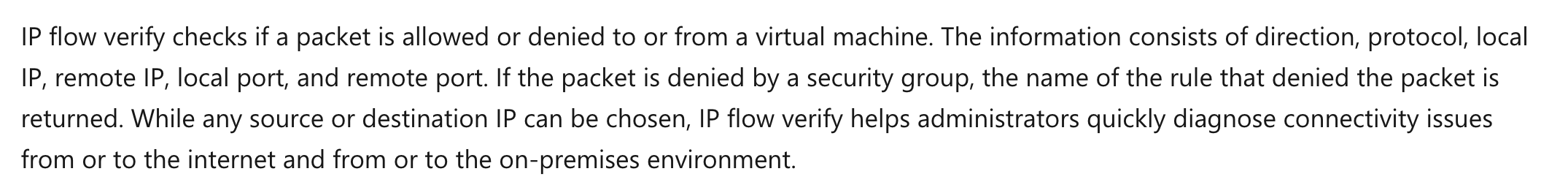
Option B is incorrect since this feature is used to get the next hop type and IP address of a specific VM packet.
Option C is incorrect since this feature is used for deep-dive network packet capture.
Option D is incorrect since this feature is a cloud-based solution that provides visibility into user and application activity in cloud networks.
For more information on the IP Flow Verify feature, please visit the below URL-
A company plans to use Azure Network watcher to perform the following tasks.
- Find out if a network security rule prevents a network packet from reaching a virtual machine hosted in an Azure virtual network.
- Find out if there is outbound connectivity between an Azure virtual machine and an external host.
Which of the following network watcher feature would you use for the following requirement?
"Find out if there is outbound connectivity between an Azure virtual machine and an external host."
- A. IP Flow Verify
- B. Next Hop
- C. Connection Monitor
- D. Traffic Analytics
Explanation:
Answer – C
This can be done with the Connection Monitor feature. The Microsoft documentation mentions the following.
Option A is incorrect since this feature is used to verify traffic flow based on security group rules.
Option B is incorrect since this feature is used to get the next hop type and IP address of a specific VM packet.
Option D is incorrect since this feature is a cloud-based solution that provides visibility into user and application activity in cloud networks.
For more information on the network watcher tool, please visit the below URL-
A company is planning to deploy an application to a set of Virtual Machines in an Azure network. The company needs to have an SLA of 99.99% for the application hosted on the Virtual machines. Which of the following should be implemented to guarantee an SLA of 99.99% on the infrastructure level?
- A. Make the virtual machines part of an availability set.
- B. Deploy the virtual machines across availability zones.
- C. Assign a standard public IP address to the virtual machines.
- D. Deploy single virtual machines across multiple regions.
Explanation:
Answer – B
You can achieve 99.99% SLA on your virtual machines' infrastructure level by deploying them across availability zones.
The Microsoft documentation mentions the following.

Option A is incorrect since availability sets can only guarantee an SLA of 99.95%.
Option C is incorrect since this will not help ensure 99.99% availability for the architecture.
Option D is incorrect since this is normally used for disaster recovery purposes.
For more information on availability zones, please visit the below URL-
Your company wants to provision an Azure storage account. The storage account needs to meet the following requirements.
- Should be able to support hot, cool, and archive blob tiers.
- Should be able to provide fault tolerance if a disaster hits the Azure region, which has the storage account.
- Should minimize on costs.
You need to complete the below command to create the storage account.

Which of the following would go into Slot1?
- A. FileStorage
- B. Storage
- C. StorageV2
- D. Table
- E. BlockBlobStorage
Explanation:
Answer – C
The task requires to support the Hot, Cool, and Archive tiers. There is only one option from our list of options that can provide this: StorageV2 or General Purpose v2 Storage Account. With this storage account type, we will have the complete functionality of the BLOB service.
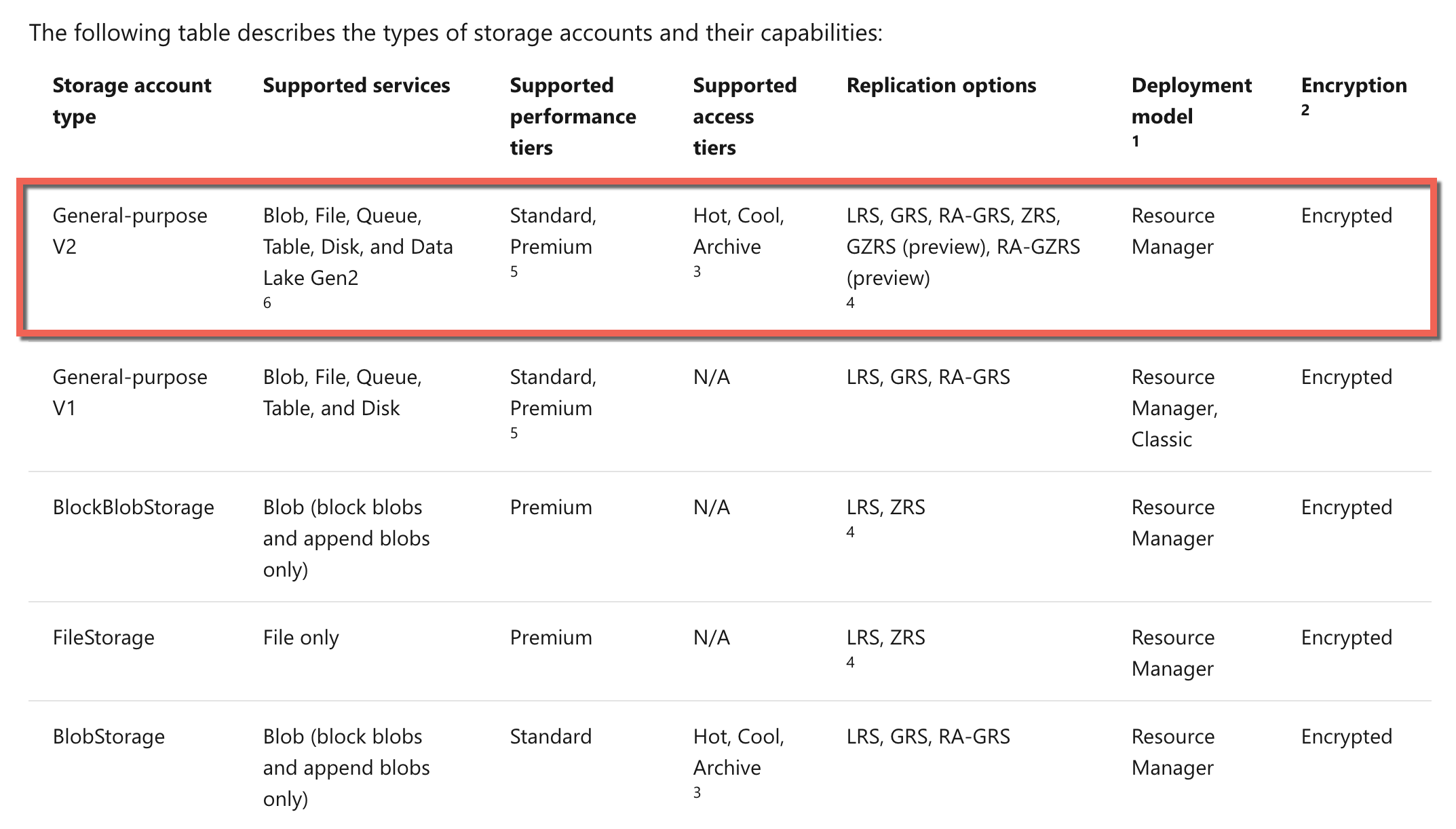
Option A is incorrect since it does not support the access tiers.
Option B is incorrect since it does not support the access tiers.
Option D is incorrect since this is a service and not a storage account kind.
Option E is incorrect since it does not support the access tiers.
For more information on storage accounts, please visit the below URL-
Your company wants to provision an Azure storage account. The storage account needs to meet the following requirements.
- Should be able to support hot, cool, and archive blob tiers.
- Should be able to provide fault tolerance if a disaster hits the Azure region, which has the storage account.
- Should minimize on costs.
You need to complete the below command to create the storage account.

Which of the following would go into Slot2?
- A. Standard_GRS
- B. Standard_LRS
- C. Standard_RAGRS
- D. Premium_LRS
Explanation:
Answer – A
Standard_GRS, which is geo-redundant storage would ensure that data is available in a secondary region if the primary region goes down.
The Microsoft documentation mentions the following.
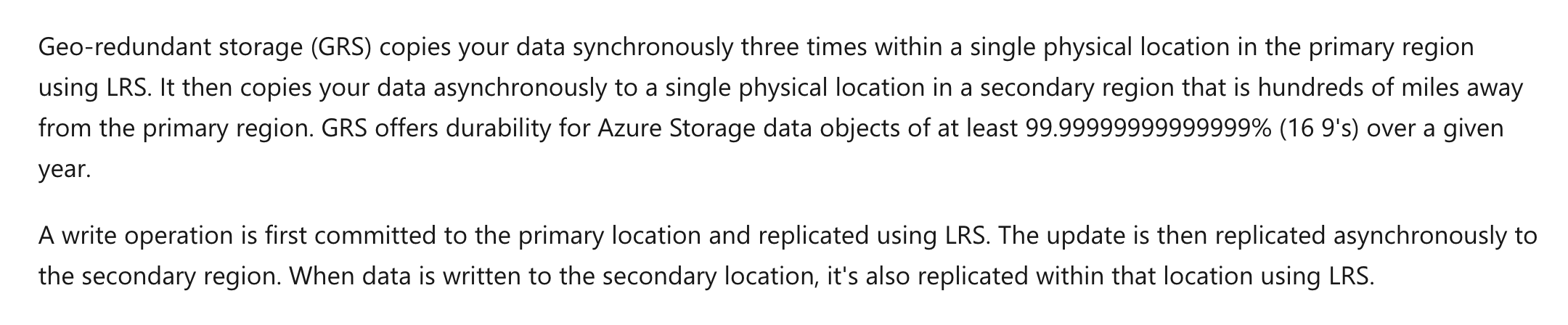
Options B and D are incorrect since these don’t guarantee that data will be available if a region goes down.
Option C is incorrect since the costs would be more than Standard_GRS.
For more information on geo-redundant storage, please visit the below URL-
Currently, in your production environment, containerized applications are running on the Azure Kubernetes Service cluster (AKS cluster). Managed disks, for persistent storage, are being used. Currently, managed disk backup is being done via automation scripts. The scripts are hard to maintain. You're working as an Azure administrator, and are expected to suggest a backup solution for managing disk, with the following requirements:
- It should support snapshot backup lifecycle which is policy-driven and provide fast backup and recovery
- It should have a very light admin overhead.
- The cost of the overall solution is low
Which of the following solutions will you select?
- A. Azure recovery service vault
- B. Azure Backup vault
- C. Azure site recovery
- D. Azure Backup Center
Explanation:
Correct Answers: B and D
- Option B is correct because a backup vault can be used for managing Azure disk snapshot life cycle management, as explained later.
- Option D is correct because the backup center is the best option for creating the backup vault
- Option A is incorrect because the recovery service, vault, does not support, disk snapshot life cycle management.
- Option C is incorrect because Azure site recovery is used for creating disaster recovery sites.
Azure backup vault supports manage disk snapshot backup lifecycle, which is policy-driven and provides fast backup and recovery from the snapshot of managed disk.
The backup process of the backup vault does not cause any performance issues on the virtual machine. It has virtually no administrative overhead and low cost. We can easily create a backup vault from the backup center.
Backup Center provides a single unified management experience in Azure for enterprises to govern, monitor, operate and analyse backups at scale.
The following figure shows how a backup vault can be created from the backup center
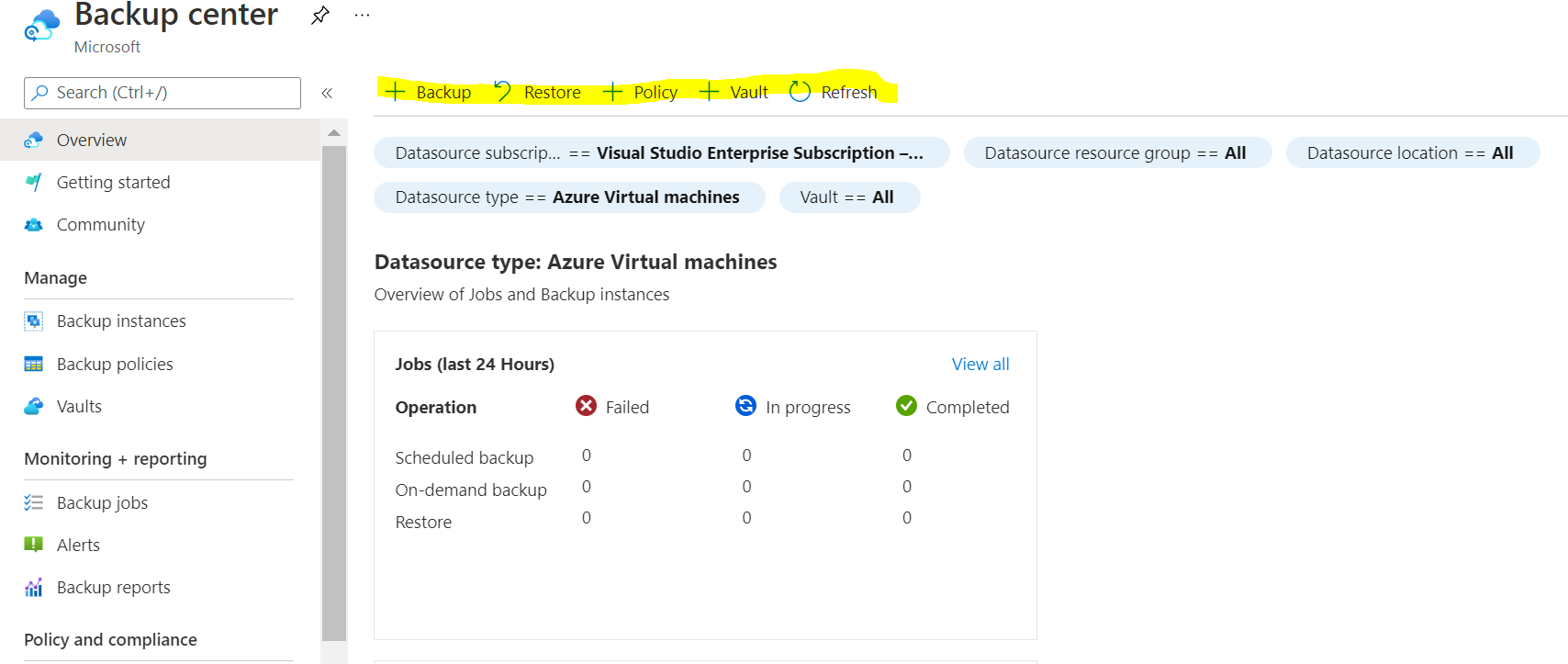
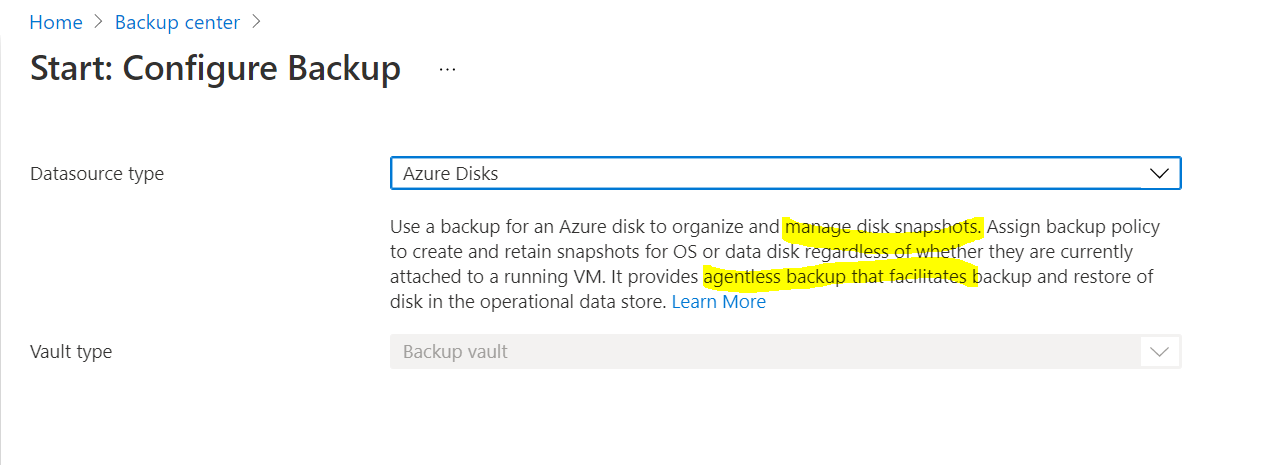
For more details, please refer to the following Azure documentation link
A team has set up Log Analytics for a virtual machine named demovm. They are running the following query in the Log Analytics Workspace.
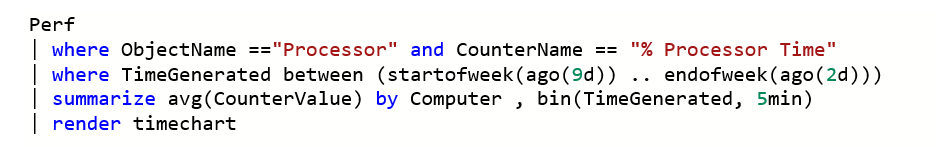
In which of the below format will the data be displayed?
- A. table that has 2 columns
- B. table that has 3 columns
- C. graph that has the Computer values on the Y axis
- D. graph that has the avg(CounterValue) values on the Y axis
Explanation:
Answer – D
If you try to run the query in Log Analytics, you will see the below output. It consists of a graph that has the Average of the Counter value on the Y-axis.
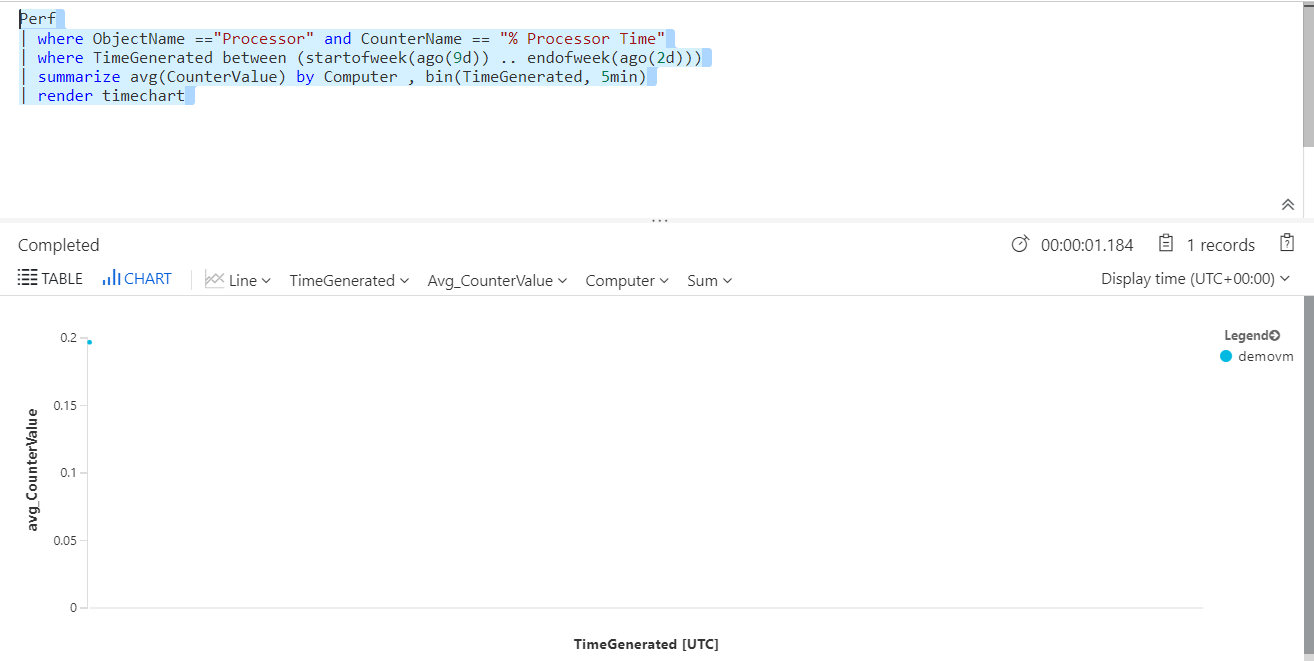
Since this is clear from the implementation, all other options are incorrect.
For more information on performing log queries, please visit the below URL-
A company has set up an Azure Virtual Machine. A team member is trying to connect to the Virtual machine but is not able to do so. Below is the snippet of the Networking section of the Virtual Machine.
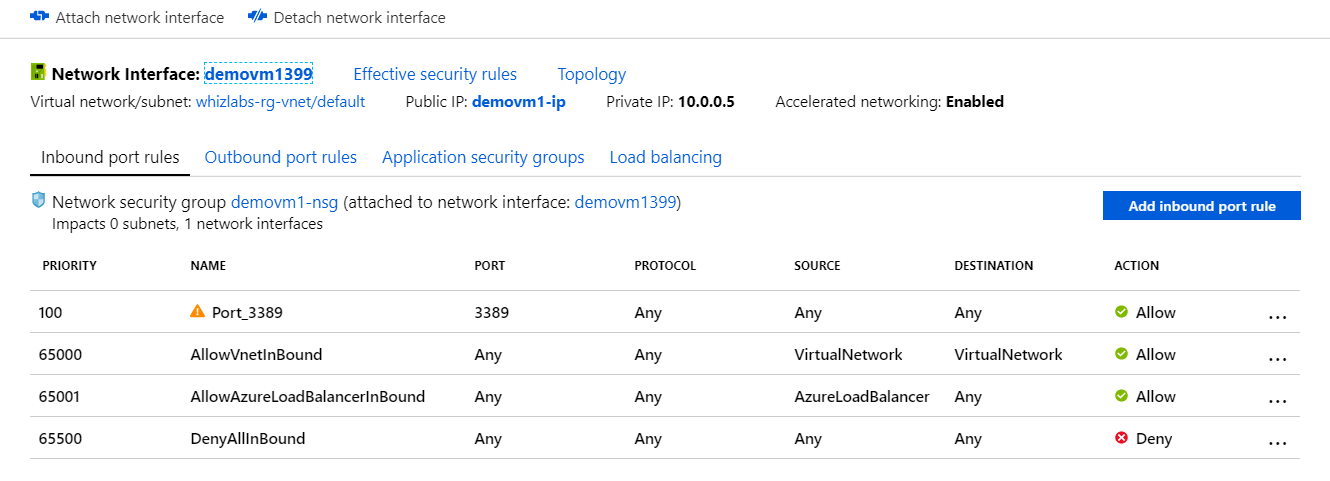
Which of the following needs to be done to ensure that the team member can connect to the Virtual Machine?
- A. Delete the Rule “Port_3389”.
- B. Add a rule to the Outbound port rules to allow traffic on port 3389.
- C. Delete the Rule “DenyAllInBound”.
- D. Start the Virtual Machine.
Explanation:
Answer – D
Here the issue is that no public IP address has been assigned to the Virtual Machine. This is because the Virtual Machine is in a stopped state. So, you would need to start the Virtual machine. You will get a Public IP address and then connect to the Virtual Machine.
Option A is incorrect since this would stop the RDP connectivity.
Option B is incorrect since this is an Inbound connectivity issue.
Option C is incorrect since you can’t delete the default rules.
For more information on IP address types, please visit the below URL-
Your company currently has a Site-to-Site connection with an Azure Virtual Private network. The VPN device allocated on the on-premise side will undergo a change in its public IP address. You have to ensure the Site-to-Site VPN connection continues to work after the change. Which of the following step would you need to carry out after the change in the public IP address on the on-premise VPN device, ensuring minimum connection downtime?
- A. Start the VPN connection.
- B. Stop the VPN connection.
- C. Modify the local gateway IP address.
- D. Modify the VPN gateway address.
Explanation:
Correct Option: C
If the VPN device that you want to connect to has changed its public IP address, you need to modify the local network gateway to reflect that change
This is also given in the Microsoft documentation.

Since this is clearly mentioned in the Microsoft documentation, all other options are incorrect.
For more information on creating site-to-site VPN connections, please go ahead and visit the below URL-
A company has an application deployed across a set of virtual machines. Users connect to the application either using point-to-site VPN or site-to-site VPN connections. You need to ensure that connections to the application are spread across all of the virtual machines. Which of the following could you set up for this requirement? Choose 2 answers from the options given below.
- A. A Public Load Balancer
- B. An Internal Load Balancer
- C. A Traffic Manager Profile
- D. An Azure Content Delivery Network
- E. An Azure Application Gateway
Explanation:
Answer – B and E
Since we need to distribute traffic across the virtual machines, we can use either the Load Balancer or Application Gateway service.
The Microsoft documentation mentions the following on these services.

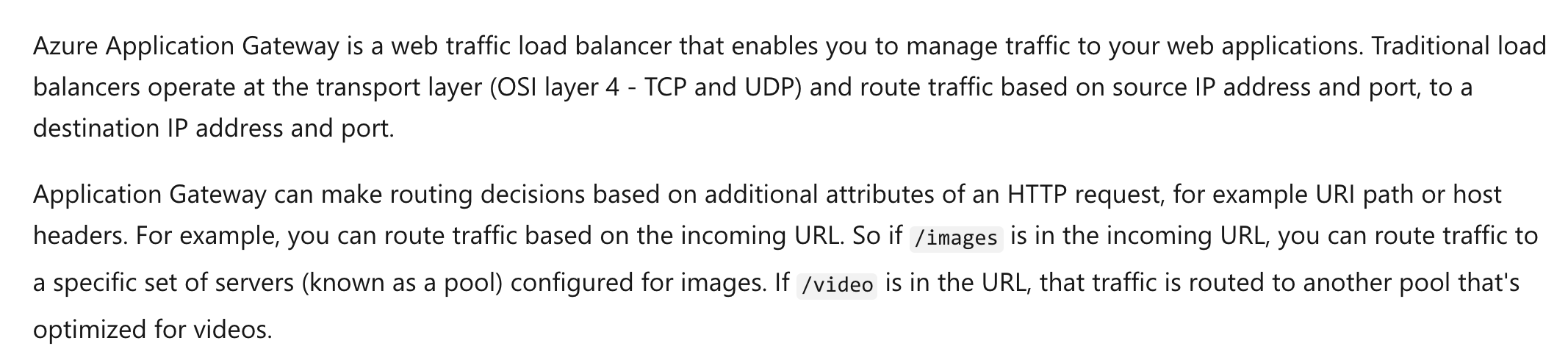
All of the other options are incorrect since the users access the Azure virtual machines via the private IP addresses. This is because the users are connecting via VPN’s. So we need to use internal load balancing solutions.
For more information on the load balancer and the application gateway, please visit the below URL-
A company has set up an Azure subscription. They have provisioned a storage account and are currently using the BLOB service. They want to assign permissions to 3 user groups.
- GroupA – This group should have the ability to manage the storage account.
- GroupB – This group should be able to manage containers within a storage account.
- GroupC – This group should be given full access to Azure Storage blob containers and data, including assigning POSIX access control.
You need to assign the relevant Role-Based Access Control, ensuring the privilege of least access.
Which of the following would you assign to GroupA?
- A. Owner
- B. Contributor
- C. Storage Account Contributor
- D. Storage Blob Data Contributor
- E. Storage Blob Data Owner
Explanation:
Answer – C
This can be accomplished by the Storage Account Contributor.
The Microsoft documentation mentions the following.
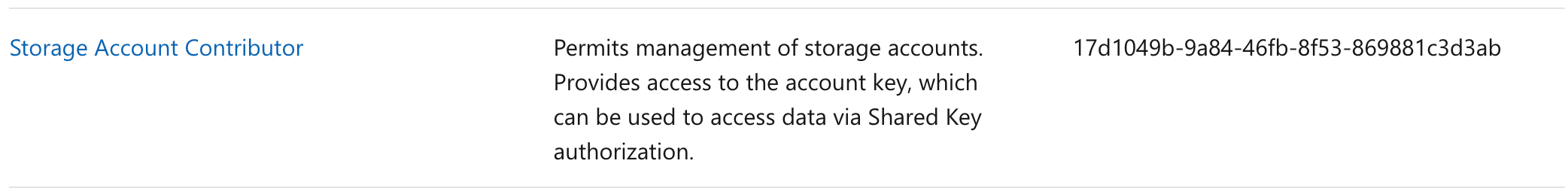
Options A and B are incorrect since these would provide more permissions than required.
Options D and E are incorrect since these roles don’t have the required permissions.
For more information on built-in roles, please visit the below URL-
A company has set up an Azure subscription. They have provisioned a storage account and are currently using the BLOB service. They want to assign permissions to 3 user groups.
- GroupA – This group should have the ability to manage the storage account.
- GroupB – This group should be able to manage containers within a storage account.
- GroupC – This group should be given full access to Azure Storage blob containers and data, including assigning POSIX access control.
You need to assign the relevant Role-Based Access Control, ensuring the privilege of least access.
Which of the following would you assign to GroupB?
- A. Owner
- B. Contributor
- C. Storage Account Contributor
- D. Storage Blob Data Contributor
- E. Storage Blob Data Owner
Explanation:
Answer – D
This can be accomplished with the Storage Blob Data Contributor.
The Microsoft documentation mentions the following.
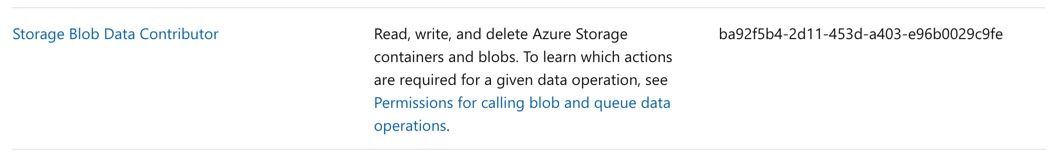
Options A and B are incorrect since these would provide more permissions than required.
Options C and E are incorrect since these roles don’t have the required permissions.
For more information on built-in roles, please visit the below URL-
A company has set up an Azure subscription. They have provisioned a storage account and are currently using the BLOB service. They want to assign permissions to 3 user groups.
- GroupA – This group should have the ability to manage the storage account.
- GroupB – This group should be able to manage containers within a storage account.
- GroupC – This group should be given full access to Azure Storage blob containers and data, including assigning POSIX access control.
You need to assign the relevant Role-Based Access Control, ensuring the privilege of least access.
Which of the following would you assign to GroupC?
- A. Owner
- B. Contributor
- C. Storage Account Contributor
- D. Storage Blob Data Contributor
- E. Storage Blob Data Owner
Explanation:
Answer – E
This can be accomplished with the Storage Blob Data Owner. The Microsoft documentation mentions the following.
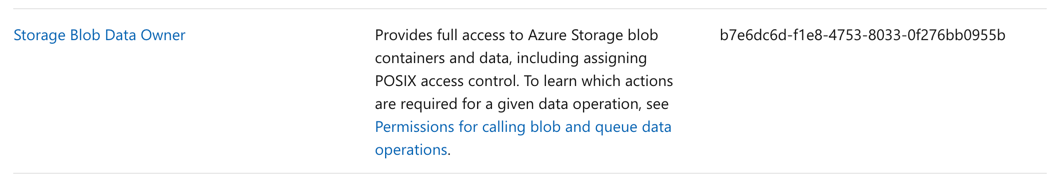
Options A and B are incorrect since these would provide more permissions than required.
Options C and D are incorrect since these roles don’t have the required permissions.
For more information on built-in roles, please visit the below URL-
A company is planning to use the Azure Import/Export service to move data out of its Azure Storage account. Which of the following service could be used when defining the Azure Export job?
- A. BLOB storage
- B. File storage
- C. Queue storage
- D. Table storage
Explanation:
Answer – A
Only the BLOB service is supported by the Export job feature. This is also given in the Microsoft documentation.
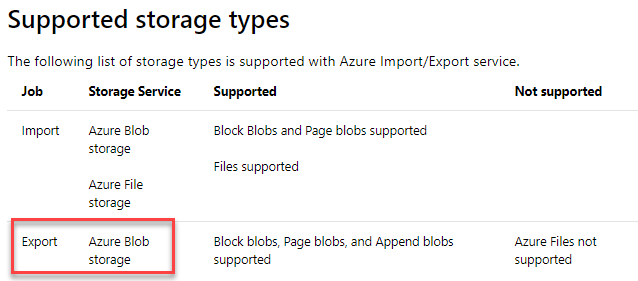
Since this is clearly mentioned, all other options are incorrect.
For more information on Azure import/export requirements, please visit the below URL-
As an IT admin, you have to develop scripts that need to add data disks to an existing virtual machine. Below is the incomplete script.

Which of the following would go into Slot1?
- A. New-AzDisk
- B. New-AzDiskConfig
- C. Add-AzVMDataDisk
- D. Set-AzDisk
Explanation:
Answer – B
An example of this is given in the Microsoft documentation.
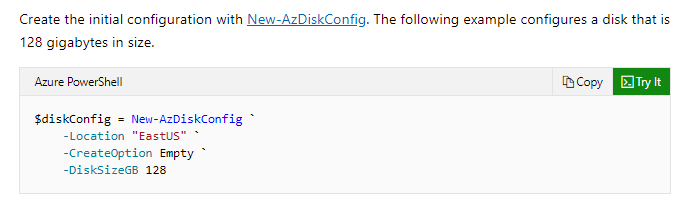
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on managing data disk, please visit the below URL-
As an IT admin, you have to develop scripts that need to add data disks to an existing virtual machine. Below is the incomplete script.

Which of the following would go into Slot2?
- A. New-AzDisk
- B. New-AzDiskConfig
- C. Add-AzVMDataDisk
- D. Set-AzDisk
Explanation:
Answer - A
An example of this is given in the Microsoft documentation.
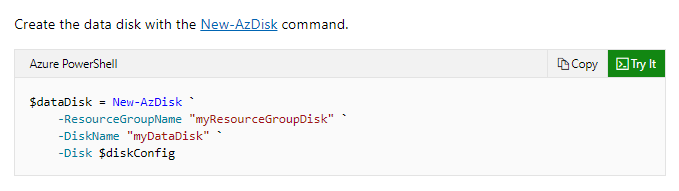
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on managing data disk, please visit the below URL-
As an IT admin, you have to develop scripts that need to be used to add data disks to an existing virtual machine. Below is the incomplete script.

Which of the following would go into Slot3?
- A. Set-AzVM
- B. UpdateAzVM
- C. Get-AzVM
- D. New-AzVM
Explanation:
Answer – C
An example of this is given in the Microsoft documentation.
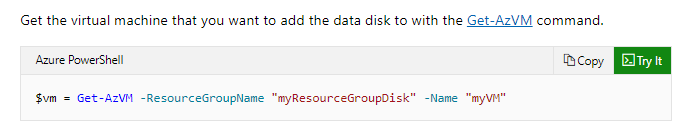
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on managing data disk, please visit the below URL-
As an IT admin, you have to develop scripts that need to be used to add data disks to an existing virtual machine. Below is the incomplete script.

Which of the following would go into Slot4?
- A. New-AzDisk
- B. New-AzDiskConfig
- C. Add-AzVMDataDisk
- D. Set-AzDisk
Explanation:
Answer - C
An example of this is given in the Microsoft documentation.
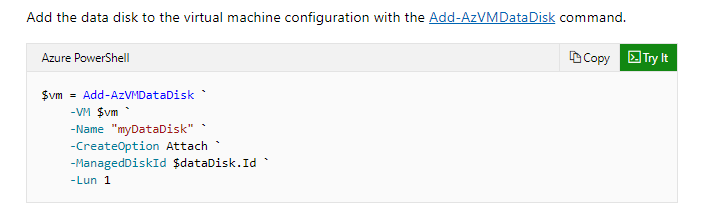
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on managing data disk, please visit the below URL-
As an IT admin, you have to develop scripts that need to be used to add data disks to an existing virtual machine. Below is the incomplete script.

Which of the following would go into Slot5?
- A. Set-AzVM
- B. Update-AzVM
- C. Get-AzVM
- D. New-AzVM
Explanation:
Answer – B
An example of this is given in the Microsoft documentation.
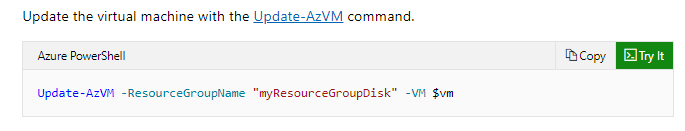
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on managing data disk, please visit the below URL-
You have an Azure virtual machine based on the Windows Server 2016 image. You implement Azure backup for the virtual machine. You want to restore the virtual machine by using the Replace existing option.
You need to go ahead and replace the virtual machine using the Azure Backup option. You have started the backup operation but it failed and is showing an error message: VM is not in a state to allow backups.
Which of the following should be done to solve this problem?
- A. Create a custom image.
- B. Stop the virtual machine.
- C. Allocate a new disk.
- D. Enable encryption on the disk.
Explanation:
Correct Answer – B
The backup operation failed because the VM is in Failed state. For a successful backup, the VM state should be Running, Stopped, or Stopped (deallocated).

Reference:
Troubleshoot backup errors with Azure VMs - Azure Backup | Microsoft Learn
You have an Azure subscription named whizlabstaging. Under the subscription, you create a resource group named whizlabs-rg.
Then you create an Azure policy based on the “Not allowed resources types” definition. Here you define the parameters as Microsoft.Network.virtual networks as the not allowed resource type. You assign this policy to the Tenant Root Group and a Virtual Network does not already exist in this subscription.
Would you be able to create a virtual machine in the whizlabs-rg resource group?
- A. Yes
- B. No
Explanation:
Answer — B
Azure policy is applied to the Tenant Root Group. It means that it would be applied to all subscriptions and all resource groups within the subscription. A VM can be created only inside a network. If you need to create a virtual machine, you must have permission to create virtual network resources, required for VM provisioning.
This policy “not allowed resources type" includes Microsoft.Network in its parameter list. So the policy will not allow the creation of any network resources.
So, B is the correct answer.
For more information on creating Azure Policies, please visit the below URL:
A company currently has the following networks defined in Azure.
|
Name |
Address space |
|
whizlab-vnet1 |
10.1.0.0/16 |
|
whizlab-vnet2 |
10.2.0.0/16 |
|
whizlab-vnet3 |
10.3.0.0/16 |
All virtual networks are hosting virtual machines with varying workloads. A virtual machine named whizlab-detect hosted in whizlab-vnet2. This virtual machine will have an intrusion detection software installed on it. All traffic on all virtual networks must be routed via this virtual machine.
You need to complete the required steps for implementing this requirement.
You are going to create the virtual network peering connection for all of the virtual networks. Which of the following is important to set for the virtual network peering connection?
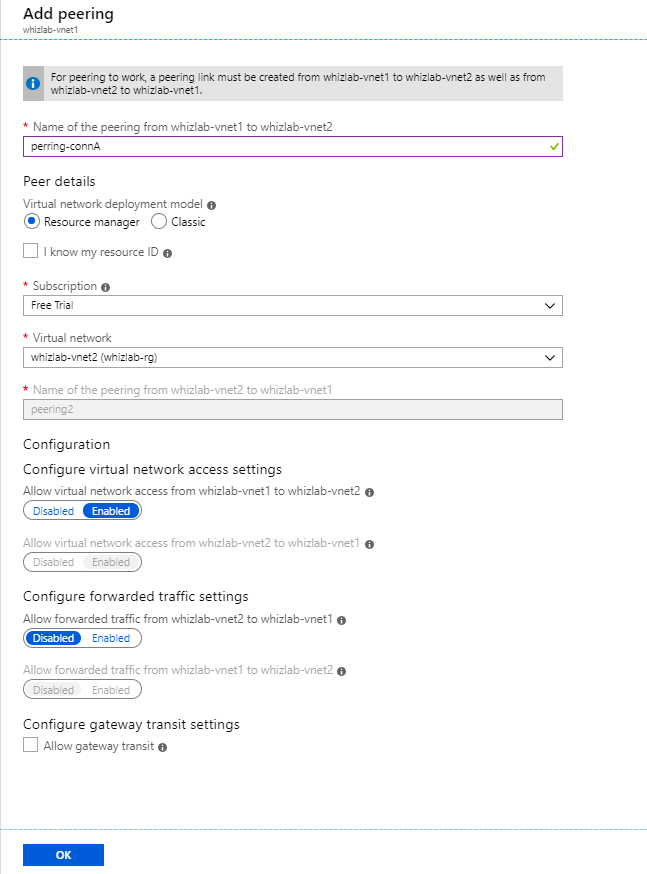
- A. Set the virtual network deployment model as Classic.
- B. Set the virtual network access settings as Disabled.
- C. Set the forwarded traffic settings as Enabled.
- D. Enable “Allow gateway transit”.
Explanation:
Answer – C
To ensure that traffic can be forwarded across networks, you need to enable forwarded traffic settings.
This is like the Hub and spoke model given in the Microsoft documentation wherein you need to enable forwarded traffic.
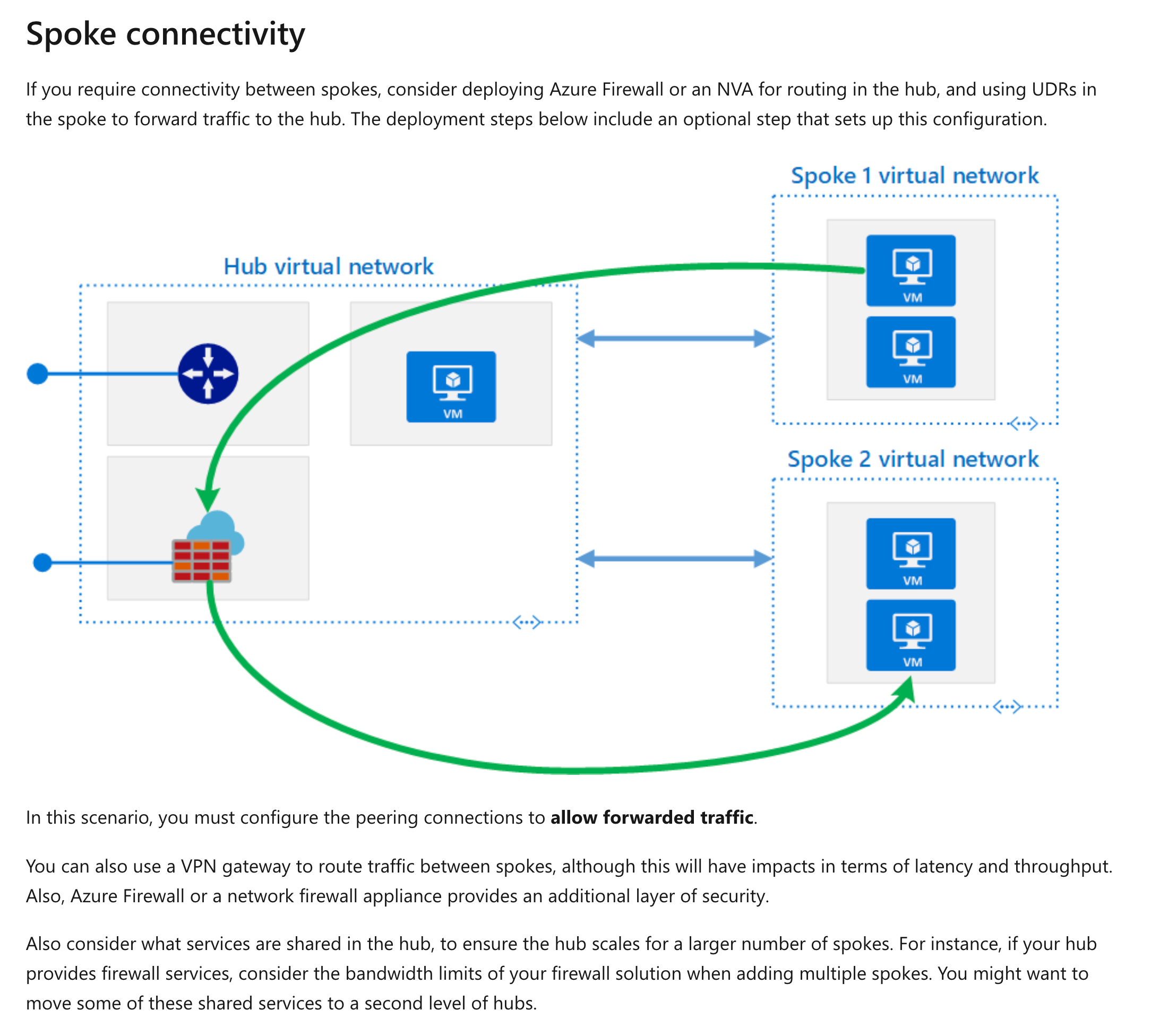
Option A is incorrect since this is used when you have a classic deployment of a virtual network.
Option B is incorrect since the traffic should be enabled.
Option D is incorrect since this is when you want traffic to flow to an on-premise setup.
For more information on the hub-spoke setup, please visit the below URL-
A company currently has the following networks defined in Azure.
|
Name |
Address space |
|
whizlab-vnet1 |
10.1.0.0/16 |
|
whizlab-vnet2 |
10.2.0.0/16 |
|
whizlab-vnet3 |
10.3.0.0/16 |
All virtual networks are hosting virtual machines with varying workloads. A virtual machine named whizlab-detect hosted in whizlab-vnet2. This virtual machine will have an intrusion detection software installed on it. All traffic on all virtual networks must be routed via this virtual machine.
You need to complete the required steps for implementing this requirement.
Which of the following would you need to create additional to ensure that traffic is sent via the virtual machine hosting the intrusion software?
- A. A new route table
- B. Add an address space
- C. Add DNS servers
- D. Add a service endpoint
Explanation:
Answer – A
In order to ensure that traffic is routed via the intrusion-based device, you need to set up a route table and add the route table to the subnets in the other virtual networks.
The diagram of the hub and spoke model also includes the use of a User-defined route (UDR), which is nothing but a custom route table.
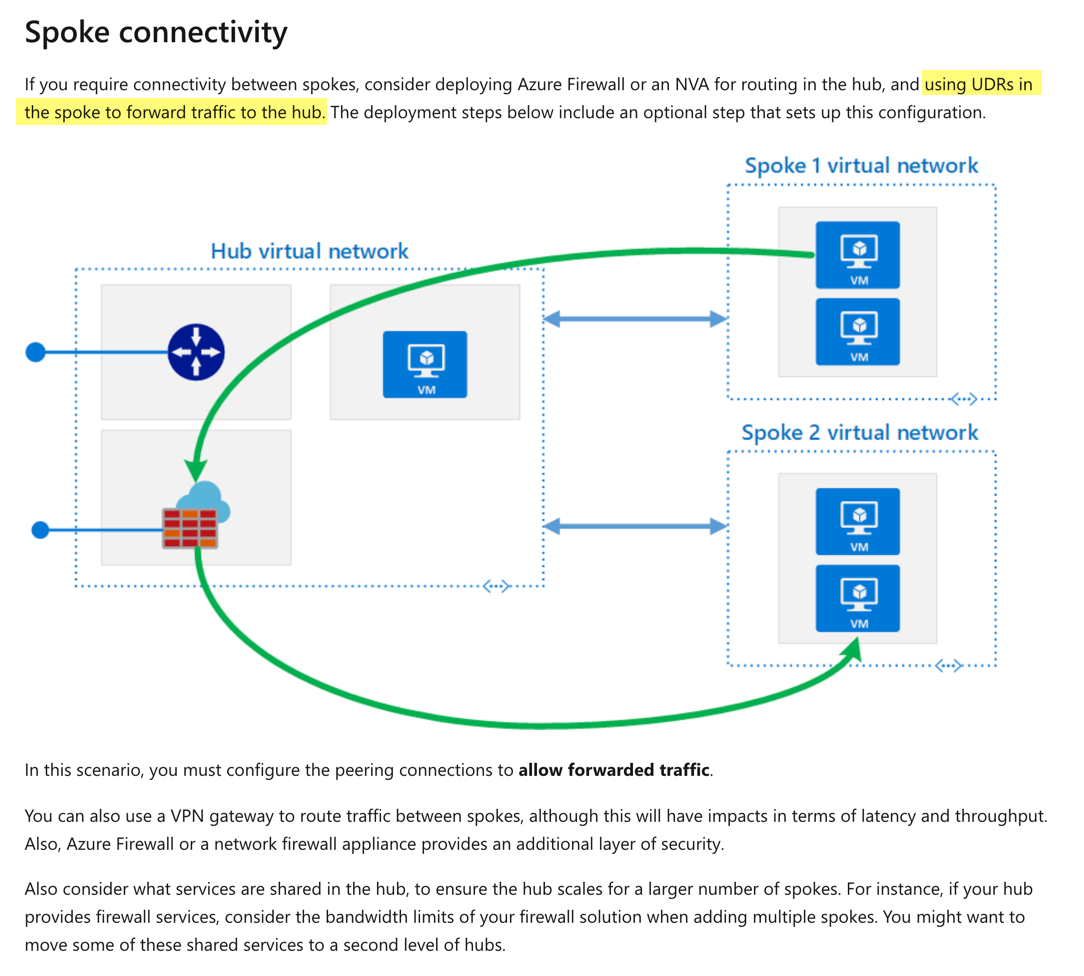
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on working with route tables, please visit the below URLs-
A company currently has the following networks defined in Azure.
|
Name |
Address space |
|
whizlab-vnet1 |
10.1.0.0/16 |
|
whizlab-vnet2 |
10.2.0.0/16 |
|
whizlab-vnet3 |
10.3.0.0/16 |
All virtual networks are hosting virtual machines with varying workloads. A virtual machine named whizlab-detect hosted in whizlab-vnet2. This virtual machine will have an intrusion detection software installed on it. All traffic on all virtual networks must be routed via this virtual machine.
You need to complete the required steps for implementing this requirement.
Which of the following needs to be enabled on the virtual machine whizlab-detect?
- A. Enable IP forwarding.
- B. Enable the identity for the virtual machine.
- C. Add an extension to the virtual machine.
- D. Change the size of the virtual machine.
Explanation:
Answer - A
In order to ensure traffic can be forwarded, you need to enable IP forwarding. An example of this is given in the Microsoft documentation.
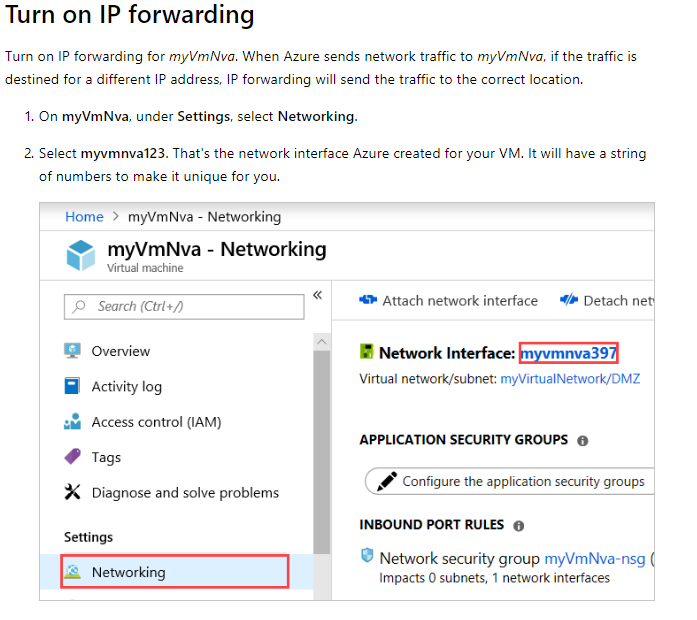
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on working with route tables, please visit the below URL-
A company is planning to use Azure for the various services they offer. They want to ensure that they can bill each department for the resources they consume. They decide to use Azure policies to separate the bills department wise.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
Azure policies are used from a governance perspective and can’t be used to create bills department wise.
For more information on Azure policies, please visit the below URL-
A company is planning to use Azure for the various services they offer. They want to ensure that they can bill each department for the resources they consume. They decide to use Azure resource tags to separate the bills department wise.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, you can use resource tags to organize your Azure resources and also apply billing techniques department wise. The Microsoft documentation mentions the following.
For more information on tagging resources, please visit the below URLs-
A company is planning to use Azure for the various services they offer. They want to ensure that they can bill each department for the resources they consume. They decide to use Azure role-based access control to separate the bills department wise.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
This is used to control access to resources and can’t be used for billing purposes.
For more information on Role-based access control, please visit the below URL-
A company has the following resources deployed to their Azure subscription.
|
Name |
Type |
Resource Group |
|
whizlab-vnet1 |
Virtual Network |
whizlabs-rg |
|
whizlab-vnet2 |
Virtual Network |
whizlabs-rg |
| whizlabvm | Virtual machine |
whizlabs-rg |
The virtual machine whizlabvm is currently in the running state.
The company now assigns the below Azure policy.
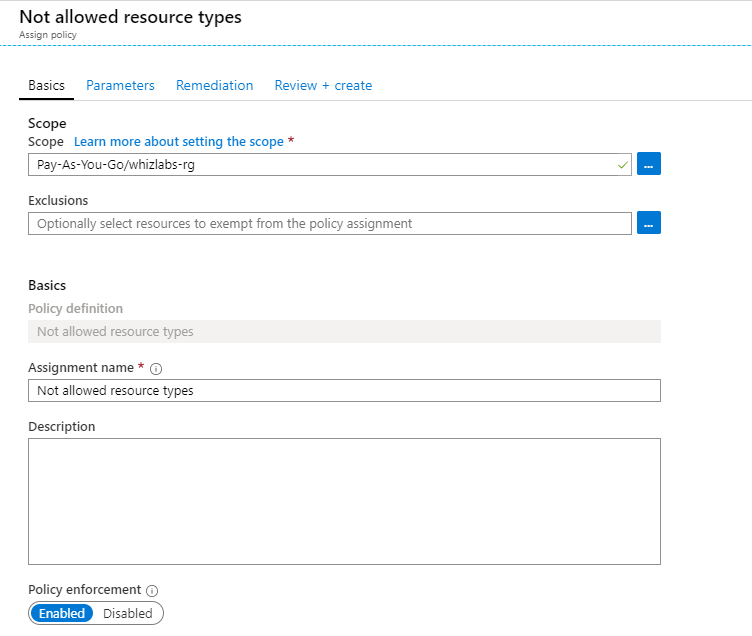
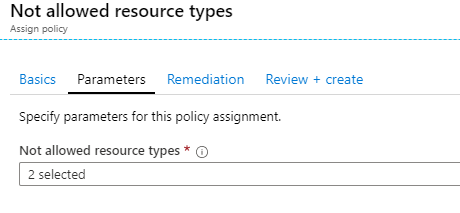
The Not Allowed resources types are
- Microsoft.Network/virtualNetworks
- Microsoft/Compute/virtualMachines
Would an administrator be able to move the virtual machine to another resource group?
- A. Yes
- B. No
Explanation:
Answer – A
The Not allowed resource types policy is only applied to the resource group whizlabs-rg. You can move the virtual machine to another resource group.
For more information on Azure policies, please visit the below URL-
A company has the following resources deployed to their Azure subscription.
|
Name |
Type |
Resource Group |
|
whizlab-vnet1 |
Virtual Network |
whizlabs-rg |
|
whizlab-vnet2 |
Virtual Network |
whizlabs-rg |
| whizlabvm | Virtual machine |
whizlabs-rg |
The virtual machine whizlabvm is currently in a running state.
The company now assigns the below Azure policy.
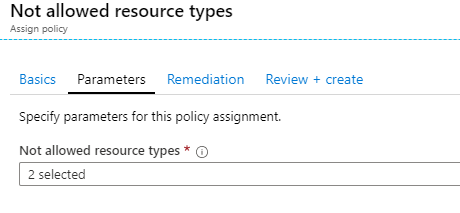
The Not Allowed resources types are
- Microsoft.Network/virtualNetworks
- Microsoft/Compute/virtualMachines
Would the state of the virtual machine change to deallocated?
- A. Yes
- B. No
Explanation:
Correct Answer – B
Azure policies would only highlight the compliance of existing resources and enforce the policy restrictions on new resources.
Here, the virtual machine whizlabvm is currently in a running state, and the company assigns the "Not allowed resource types Azure policy"
Not allowed resource types (Deny): Prevents a list of resource types from being deployed.
Hence the state of the virtual machine would remain as it is.
For more information on Azure policies, please visit the below URL-
A company has the following resources deployed to their Azure subscription.
|
Name |
Type |
Resource Group |
|
whizlab-vnet1 |
Virtual Network |
whizlabs-rg |
|
whizlab-vnet2 |
Virtual Network |
whizlabs-rg |
| whizlabvm | Virtual machine |
whizlabs-rg |
The virtual machine whizlabvm is currently running.
The company now assigns the below Azure policy.


The Not Allowed resources types are
- Microsoft.Network/virtualNetworks
- Microsoft/Compute/virtualMachines
Would an administrator be able to modify the address space of whizlab-vnet2?
- A. Yes
- B. No
Explanation:
Answer – B
Since there is a policy, "Not allowed resource types" policy in place that does not allow any actions on virtual networks, you cannot change the virtual networks."Not allowed resource types" means, it's built-in policy enables you to specify the resource types that your organization cannot deploy. Restricts which resource types can be deployed in your environment.You can modify the existing address space, but you cannot add an additional address space.
Not allowed resource types (Deny): Prevents a list of resource types from being deployed. So, you cannot do any updates or modifications to the resource with this policy.
After defining Not Allowed resource type policy on the Resource Group, it effects all the resources that are within it and also the new ones being added.
So, in this case, when you try to change the existing address space of Virtual Network2 error is displayed.
Below tested scenario is for your reference and we suggest you, please try this scenario at your end to get more idea.
For more information on Azure policies, please visit the below URL-
A team is currently storing all of their objects in an Azure storage account. They are using the Azure Blob service. They want to create a lifecycle management rule that would do the following.
- Change the objects' tier level to the cool tier if they have not been modified in the past 30 days.
- Archive an object if they have not been modified in the past 90 days.
The Lifecycle rule would be applied to a container called demo and a folder within the container called data.
You have to complete the following JSON snippet for the Lifecycle rule.
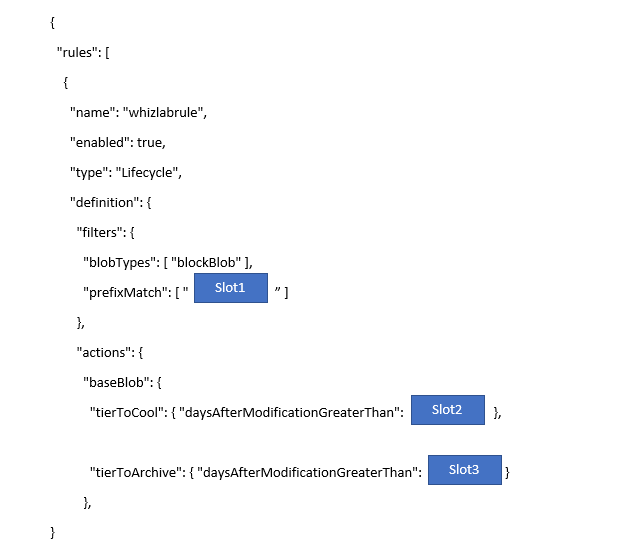
Which of the following would go into Slot1?
- A. demo
- B. data
- C. data/demo
- D. demo/data
Explanation:
Answer – D
The format of the prefixMatch is container/folder: demo/data.
An example of this is given in the Microsoft documentation.
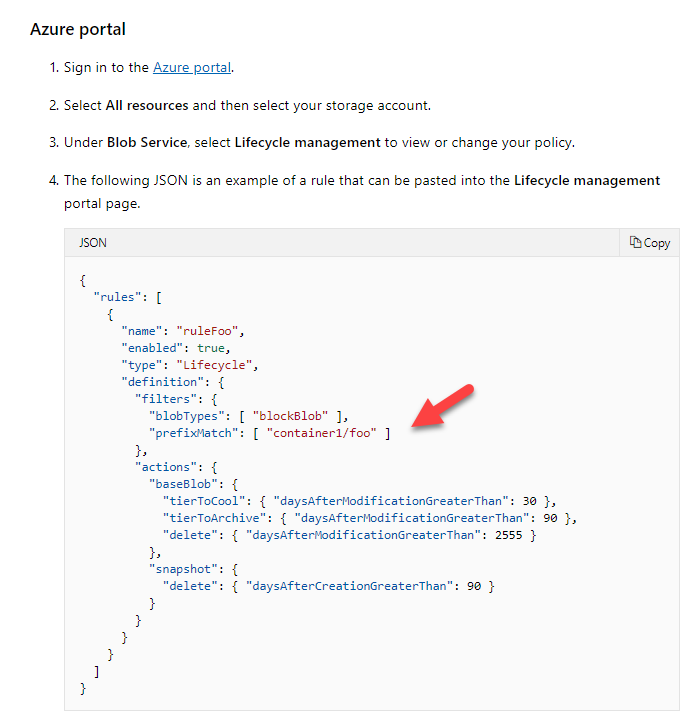
Since this is clearly mentioned in the Microsoft documentation, all other options are invalid.
For more information on lifecycle management rules, please visit the below URL-
A team is currently storing all of their objects in an Azure storage account. They are using the Azure Blob service. They want to create a lifecycle management rule that would do the following.
- Change the objects' tier level to the cool tier if they have not been modified in the past 30 days.
- Archive an object if they have not been modified in the past 90 days.
The Lifecycle rule would be applied to a container called demo and a folder within the container called data.
You have to complete the following JSON snippet for the Lifecycle rule.

Which of the following would go into Slot2?
- A. 15
- B. 30
- C. 90
- D. 120
Explanation:
Answer – B
Since the question states that we need to move the objects to the cool tier after 30 days, this should be the value for tierToCool.
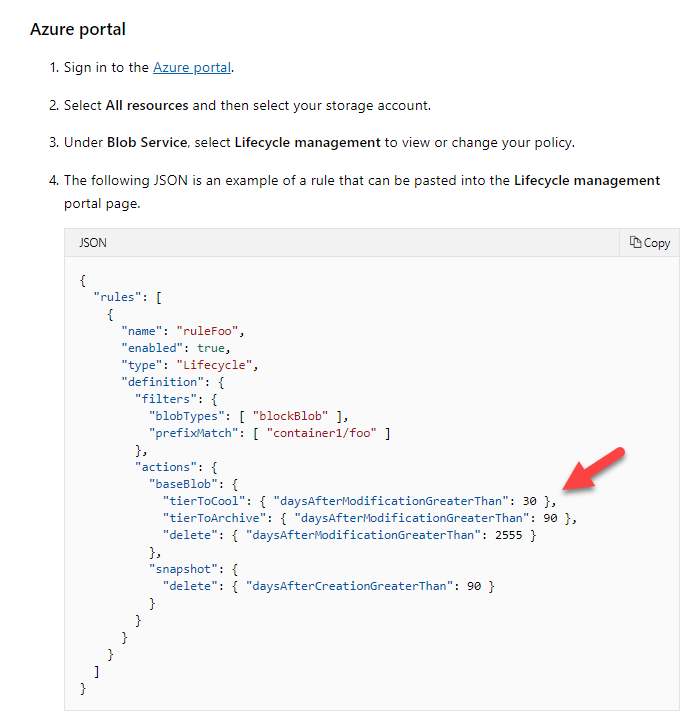
An example of this is given in the Microsoft documentation.
Since this is clearly mentioned in the Microsoft documentation, all other options are invalid.
For more information on lifecycle management rules, please visit the below URL-
A team is currently storing all of their objects in an Azure storage account. They are using the Azure Blob service. They want to create a lifecycle management rule that would do the following.
- Change the objects' tier level to the cool tier if they have not been modified in the past 30 days.
- Archive an object if they have not been modified in the past 90 days.
The Lifecycle rule would be applied to a container called demo and a folder within the container called data.
You have to complete the following JSON snippet for the Lifecycle rule.

Which of the following would go into Slot3?
- A. 15
- B. 30
- C. 90
- D. 120
Explanation:
Answer – C
Since the question states that we need to move the objects to the archive tier after 90 days, this should be the value for tierToArchive.
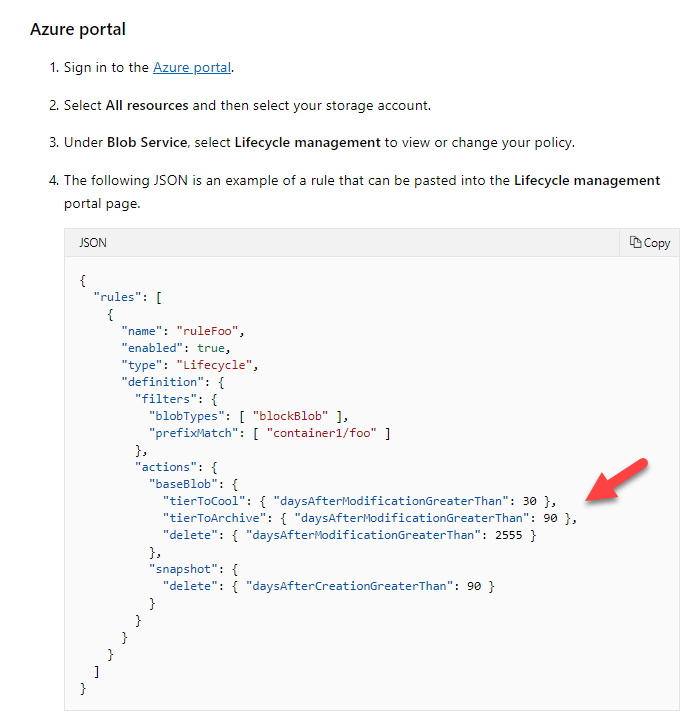
Since this is clearly mentioned in the Microsoft documentation, all other options are invalid.
For more information on lifecycle management rules, please visit the below URL-
A team is currently making use of an Azure storage account as shown below
A file named audio.log has been uploaded to a container called demo.
Which of the following is a valid URL that could be used to access the file?
- A. https://whizlabstore/demo/audio.log
- B. https://whizlabstore.blob.core.windows.net/audio.log
- C. https://whizlabstore.blob.core.windows.net/demo/audio.log
- D. https://whizlabstore/audio.log
Explanation:
Answer – C
The URL of the accessing an object must be https://<storageAccountName>.blob.core.windows.net /<containerName>/<objectName>:
https://whizlabstore.blob.core.windows.net/demo/audio.log
The Microsoft documentation mentions the following on the format of the URL for blob objects.
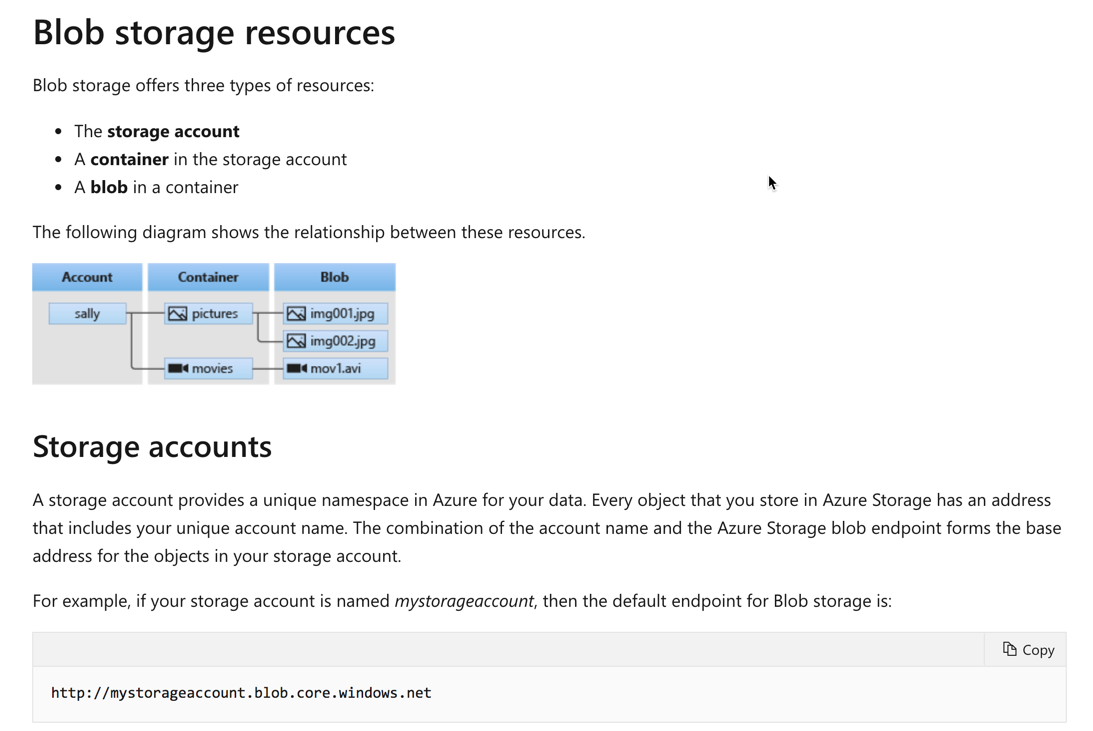
Since this is clearly mentioned in the Microsoft documentation, all other options are invalid.
For more information on the blob service, please visit the below URL
A team is currently making use of an Azure storage account, as shown below.

A file named audio.log has been uploaded to a container called demo.
You need to allow users to download the object. The access should be granted for a day only. You need to provide a secure way to access the object. Which of the following would you implement for this purpose?
- A. Provide access Keys.
- B. Mark public access on the container.
- C. Generate a shared access signature.
- D. Mark public access on the object.
Explanation:
Answer – C
The secure way to implement this is to generate a shared access signature. The Microsoft documentation mentions the following.

All of the other ways are incorrect since they don’t provide secure access to the storage account object.
For more information on Shared access signatures, please visit the below URL-
A company currently has a set of Azure virtual machines. They want to ensure that their IT administrative team gets alert when any of the virtual machines are shut down.
They decide to create alerts based on Activity Logs in Azure Monitor.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
The Activity Log service provides insights for all resource activities within your subscription. An example of events recorded is shown below.
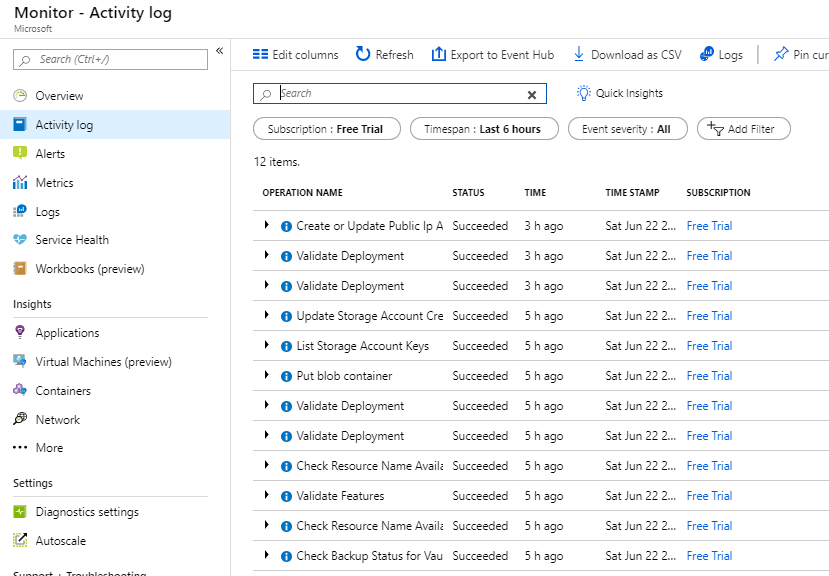
You can create alerts based on the Activity logs.
For more information on Azure activity logs, please visit the below URLs-
A company currently has a set of Azure virtual machines. They want to ensure that their IT administrative team gets alert when any of the virtual machines are shut down.
They decide to create alerts in the Azure Advisor service.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The Azure Advisor service is used as a recommendation engine and can’t be used to record virtual machines' activities.
For more information on Azure Advisor, please visit the below URL-
A company currently has a set of Azure virtual machines. They want to ensure that their IT administrative team gets alert when any virtual machines are shut down.
They decide to create alerts in the Service Health service.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The Service Health service is used to inform users of the health of Azure-based services.
For more information on Azure Service Health, please visit the below URL-
You need to provision the Azure storage account. You need to complete the below Azure CLI script for this.
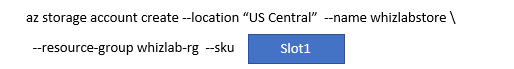
Which of the following would go into Slot1?
- A. Standard_GRS
- B. Standard_LRS
- C. Standard_RAGRS
- D. Standard_ZRS
Explanation:
Answer- B
We need to keep costs minimized. There is no mention in the question on Fault tolerance and disaster recovery. We can opt for Local Redundant storage.
Since this is the most cost-effective approach, all other options are incorrect.
For more information on Data Redundancy, please visit the below URL-
You need to configure a VPN connection for whizlabs-net2. Which of the following would you need to configure in the virtual network?
- A. An additional address space
- B. A gateway subnet
- C. A peering connection
- D. An express route connection
Explanation:
Answer – B
For the Virtual network, you need to have a gateway subnet.
The Microsoft documentation mentions the following.
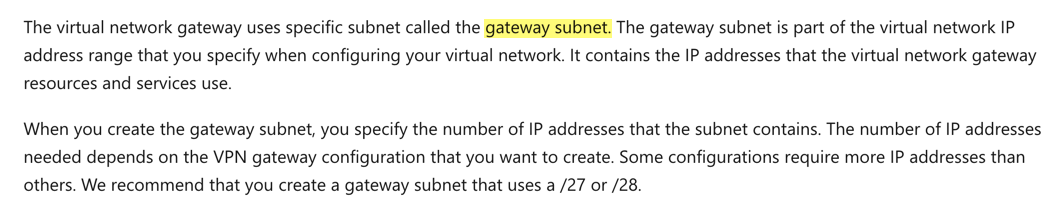
Since this is clearly mentioned in the documentation, all other options are incorrect.
For more information on Site-to-Site VPN connections, please visit the below URL-
You have to ensure that users can communicate with the virtual machine whizlabapi on port number 80. You decide to create an Outbound rule in the Network Security Group associated with the virtual machine's network interface.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
You need to add an Inbound security rule and not an Outbound Security rule.
For more information on network security, please visit the below URL-

