





| No. | Domain | Total Question | Correct | Incorrect | Unattempted | Marked for Review |
|---|---|---|---|---|---|---|
| 1 | Manage Azure identities and governance | 10 | 0 | 0 | 10 | 0 |
| 2 | Implement and manage storage | 9 | 0 | 0 | 9 | 0 |
| 3 | Deploy and manage Azure compute resources | 10 | 0 | 0 | 10 | 0 |
| 4 | Configure and manage virtual networking | 25 | 0 | 0 | 25 | 0 |
| 5 | Monitor and back up Azure resources | 1 | 0 | 0 | 1 | 0 |
| Total | All Domains | 55 | 0 | 0 | 55 | 0 |
You have been requested to move the initial set of documents to Azure. The total size of the documents is 500MB. Which of the following is the ideal implementation step that should be followed to fulfill this requirement?
- A. Generate a shared access signature (SAS). Map a drive and then copy the files by using File Explorer.
- B. Use the Azure Import/Export service.
- C. Generate an access key. Map a drive, and then copy the files by using File Explorer.
- D. Use Azure Storage Explorer to copy the files.
Explanation:
Answer – D
As per the case study, you have the following requirements.
- Move the existing documents to Azure Blob storage using the Internet.
You can easily copy files using the Azure Storage Explorer.
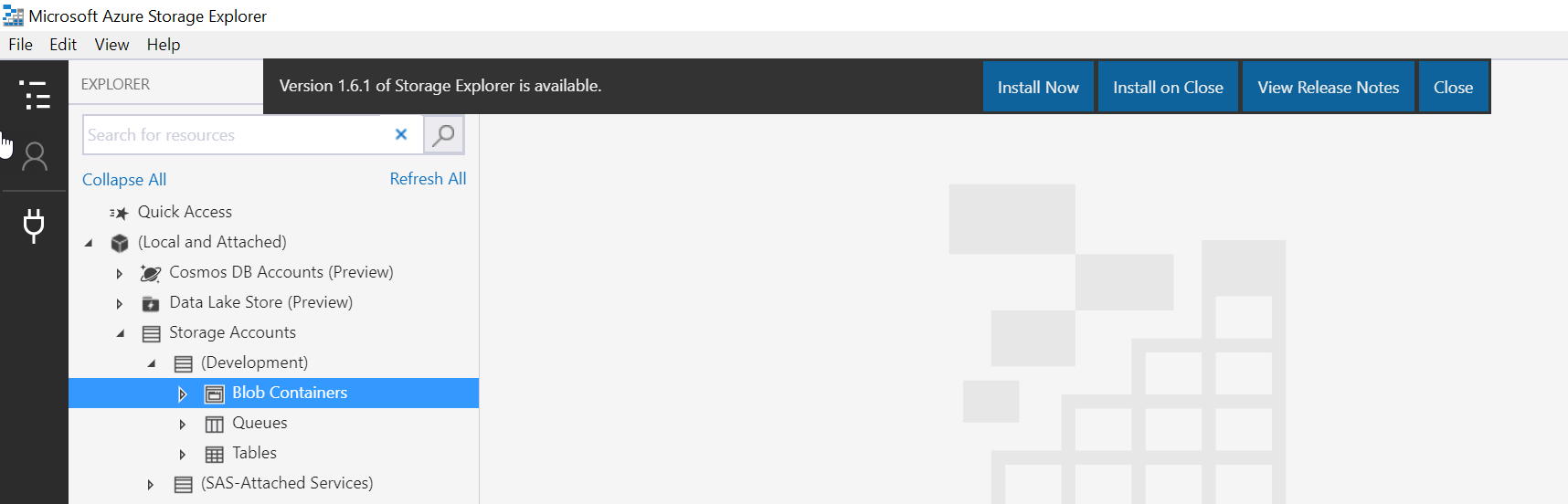
Options A and C are incorrect because this is used for File storage and not BLOB storage.
Option B is incorrect since this is normally used as a one-time transfer of a large amount of data to Azure.
For more information on the Azure Storage Explorer, please refer to the below URL-
The application whizlabs-app is a critical application. Hence you need to ensure that a backup solution is in place for the application. Which of the following would you need to create first?
- A. A recovery plan
- B. An Azure Backup Server
- C. A backup policy
- D. A Recovery Services vault
Explanation:
Answer – D
To back up any Azure resource, the first thing you need to do is create a Recovery Services vault. Your vault must be in the same region as your VM.
The below snapshot from the Microsoft documentation addressing the Recovery Services vault location.

Since the documentation clearly mentions this, all other options are invalid.
For more information on preparing your VM’s for backup, please refer to the below URL-
You are working on the network design for hosting the different tiers for the whizlabs-app application. How many virtual networks would you recommend hosting the Virtual Machines for the application?
- A. 1
- B. 2
- C. 3
- D. 4
Explanation:
Answer – A
Since there is no requirement to have multiple virtual networks, one network would suffice for this requirement.
For more information on Azure virtual networks, please go to the below URL-
You are working on the network design for hosting the different tiers for the whizlabs-app application. How many subnets would you recommend hosting the Virtual Machines for the application?
- A. 1
- B. 2
- C. 3
- D. 4
Explanation:
Answer – C
There are 3 layers as part of the case study
- A SQL database
- A web front end
- A processing middle tier
It would be preferential to have a separate subnet for each layer. An example diagram of an architecture separation for VM workloads is given in the Microsoft documentation.
For more information on the network overview for Virtual Machines, please go to the below URL-
You need to ensure that users can join devices to Azure AD. These users must be members of the pilot Azure AD group. Which two settings do you need to modify to implement these requirements? The case requirement is that the user should be a member of a pilot group and all pilot group members should be able to join the devices.
- A. Users may join devices to Azure AD.
- B. Additional local administrators on Azure AD joined devices.
- C. Users may register their devices with Azure AD.
- D. Require Multi-Factor Auth to join devices.
Explanation:
Answers – A and D
In the Case study, there are two requirements to join devices.
• There should be a pilot group so that the testing of devices joining Azure AD can be carried out.
• When users joined their own devices to Azure AD, they need to use a phone verification method to verify their identity.
To fulfill the first requirement, we need to modify "Users may join devices to Azure AD" and select a pilot Azure AD group created earlier.
For the second requirement, we need to modify the "Require Multi-Factor Auth to join devices" settings and select a phone verification method.
The Microsoft documentation mentions the following to support this.
- Users may register their devices with Azure AD - You need to configure this setting to allow Windows 10 personal, iOS, Android, and macOS devices to be registered with Azure AD. If you select None, devices are not allowed to register with Azure AD. Enrollment with Microsoft Intune or Mobile Device Management (MDM) for Office 365 requires registration. If you have configured either of these services, ALL is selected and NONE is not available.
- Require Multi-Factor Auth to join devices - You can choose whether users must provide an additional authentication factor to join their device to Azure AD. The default is No. We recommend requiring multi-factor authentication when registering a device. Before you enable multi-factor authentication for this service, you must ensure that multi-factor authentication is configured to register their devices. For more information on different Azure multi-factor authentication services, see getting started with Azure multi-factor authentication.
Option B is incorrect since this is used for users granted local administrator rights on a device.
Option C is incorrect since this setting is to allow devices to be registered with Azure AD.
Reference: For more information on device settings, please go to the below URL
Manage devices in Azure AD using the Azure portal - Microsoft Entra | Microsoft Docs
You are planning the move of whizlabs-app to Azure. You create a network security group (NSG). You need to recommend a solution to provide users with access to whizlabs-app. What should you recommend?
- A. Create an outgoing security rule for port 443 from the Internet. Associate the Network Security Group to all the subnets.
- B. Create an incoming security rule for port 443 from the Internet. Associate the Network Security Group to all the subnets.
- C. Create an incoming security rule for port 443 from the Internet. Associate the Network Security Group to the subnet that contains the web servers.
- D. Create an outgoing security rule for port 443 from the Internet. Associate the Network Security Group to the subnet that contains the web servers.
Explanation:
Answer – C
If you have a Network Security group, change the Incoming rules to allow port 443. This is so that users from the Internet can access to the web server on the secure port 443.
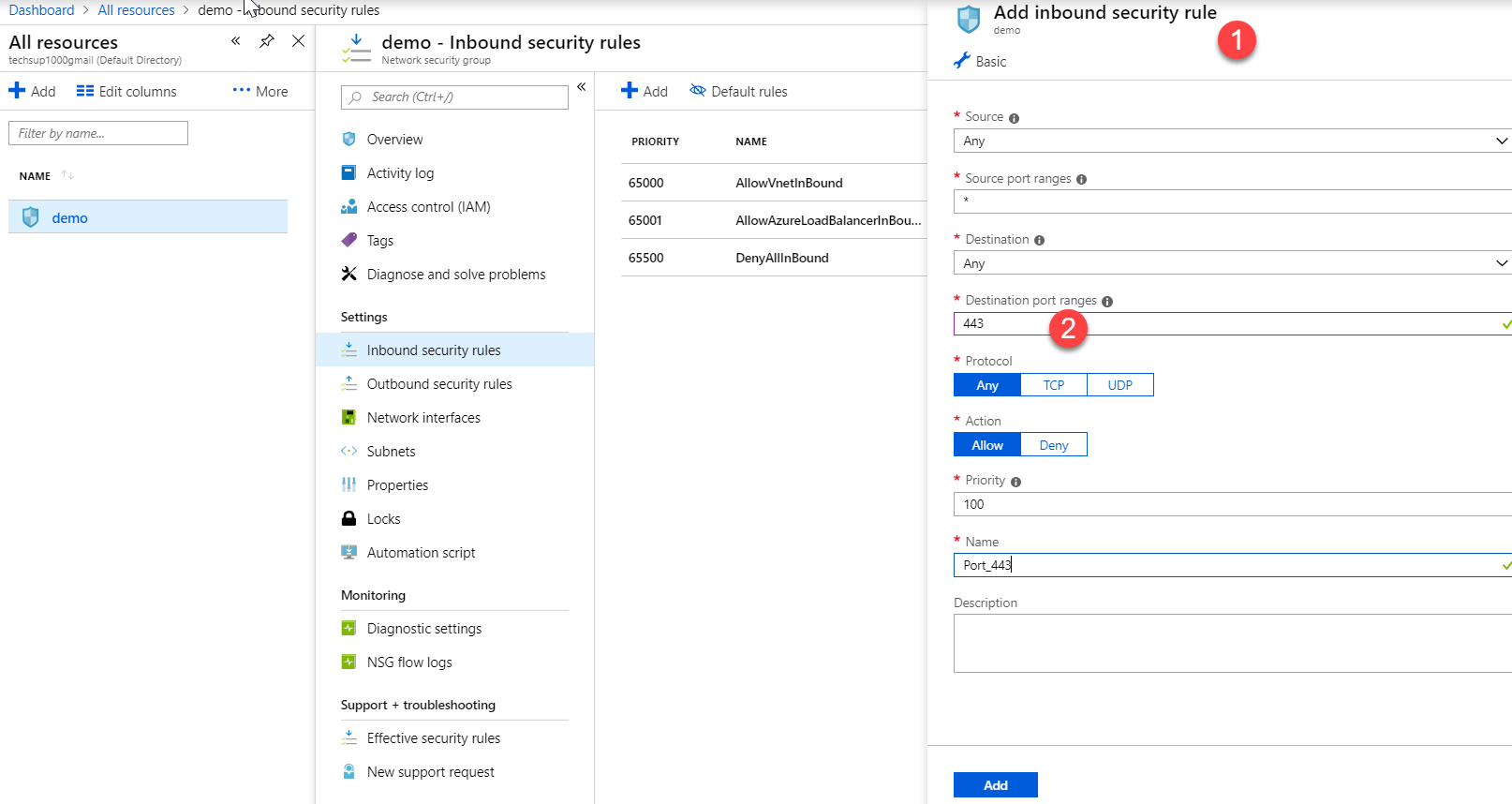
Options A and D are incorrect since users need to connect to the web server. That means the incoming rule needs to be modified and not the outgoing rules.
Option B is incorrect since associating the Network Security Group with Multiple subnets will affect all the other application tiers.
For more information on Network Security Groups, please go to the below URL-
Your company has an Azure subscription, and an on-premises file server named demoserver. You need to synchronize files with the demoserver and Azure using Azure File Sync Service.
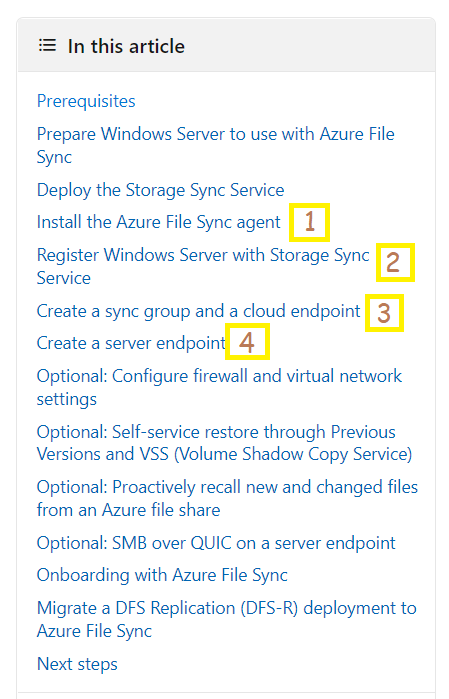
Which of the following actions would you perform to deploy the Azure File Sync?
- Correct Answer
- 1.
Install the Azure File Sync agent on the demoserver
- 2.
Register demoserver
- 3.
Create a sync group and a cloud endpoint
- 4.
Add a server endpoint
Explanation:
Correct Answers(Ascending Order):
|
1 |
Install the Azure File Sync agent on the demoserver. |
|
2 |
Register demoserver. |
|
3 |
Create a sync group and a cloud endpoint. |
|
4 |
Add a server endpoint. |
Reference:
Your company has an Azure subscription that is used by multiple departments in your company. The subscription contains 5 resource groups. Each department uses resources in several resource groups. Your supervisor has requested to send a report that details the costs for each department. Which of the following actions would you need to perform for this purpose? Choose 3 answers from the options given below.
- A. Assign a tag to each resource group.
- B. Use the Resource costs blade of each resource group.
- C. Download the usage report.
- D. Assign a tag to each resource.
- E. From the Costs Analysis blade, filter the view by tag.
Explanation:
Answer – C, D, and E
The benefit of tagging and billing is given in the Microsoft documentation.
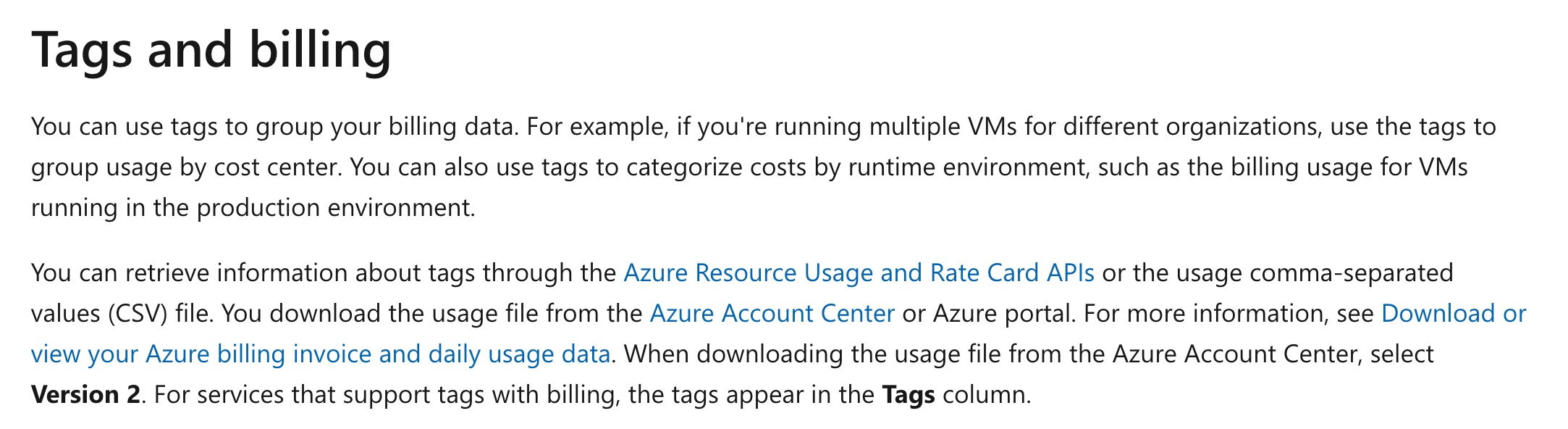
Option A is incorrect since here, the resources are used across various departments and are not constrained via resource groups.
Option B is incorrect since the costing on a tag basis needs to be seen from Cost Analysis.
For more information on using tags, please visit the below URL-
You have an Azure Active Directory (Azure AD) tenant that has the initial domain name.
You have a domain name of whizlabs.com registered at a third-party registrar. You need to ensure that you can create Azure AD users that have names containing a suffix of @whizlabs.com.
Which of the following would need to be implemented to fulfill this requirement? Choose 3 answers from the options given below.
- A. Configure the company branding.
- B. Add an Azure AD tenant.
- C. Verify the domain.
- D. Create an Azure DNS Zone.
- E. Add a custom domain name.
- F. Add a record to the public whizlabs.com DNS zone.
Explanation:
Answer - C, E, and F
If you want to add a custom domain to Azure AD, first you need to add a domain name to the Azure AD. Then update DNS information at the domain registrar service. And finally, verify that you do own this domain name.
The Microsoft documentation gives the list of steps to add a custom domain.
Since this is clearly given in the documentation, all other options are incorrect.
For more information on adding custom domains, please go to the below URL-
A company currently has an Azure account and subscription. They are planning to make their application available 99.99% of the time using Virtual Machines and a Load balancer. Which of the following would need to be in place? You have to minimize costs associated with the solution. Choose 2 answers from the options given below.
- A. Create a Basic Load balancer.
- B. Create a Standard Load balancer.
- C. Add 2 Virtual Machines to the backend pool.
- D. Add a Virtual Machine to the backend pool.
Explanation:
Answer – B and C
To solve this problem you need to use a Standard Load balancer with two virtual machines as a backend pool.
This is clearly mentioned in the Microsoft documentation.
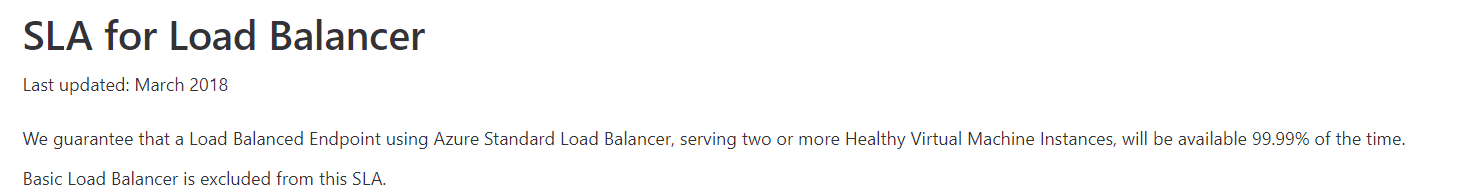
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on the SLA for the Load balancer, please go to the below URL-
A company has set up an external load balancer that load balances traffic on port 80 and 443 across 3 virtual machines. You have to ensure that all traffic is directed towards a VM named demovm. How would you achieve this?
- A. By creating a new public load balancer for demovm
- B. By creating a new internal load balancer for demovm
- C. By creating an inbound NAT rule
- D. By creating a new IP configuration
Explanation:
Answer – C
An example of this is given in the Microsoft documentation.
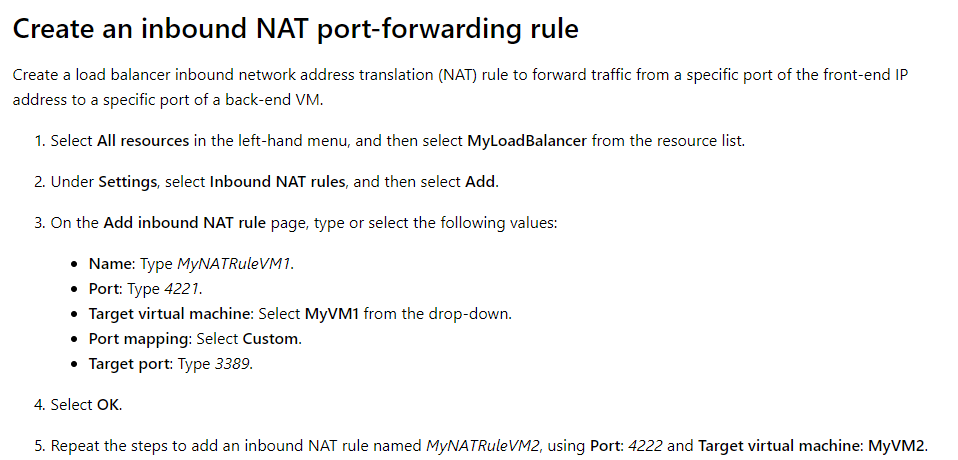
Options A and B are incorrect since we don’t need to recreate an entire load balancer just for this scenario.
Option D is incorrect since this is used to attach a front-end IP to the load balancer.
For more information on port forwarding for the load balancer, please go to the below URL-
A company has set up a Load balancer that load balances traffic on ports 80 and 443 across 3 virtual machines. You have to ensure that users are assigned the same web server for the duration of their session. Which of the following would you configure for this requirement?
- A. Floating IP
- B. Health Probe
- C. Session Persistence
- D. TCP Reset
Explanation:
Answer – C
The Microsoft documentation mentions Session Persistence or Source IP affinity mode, as mentioned below.
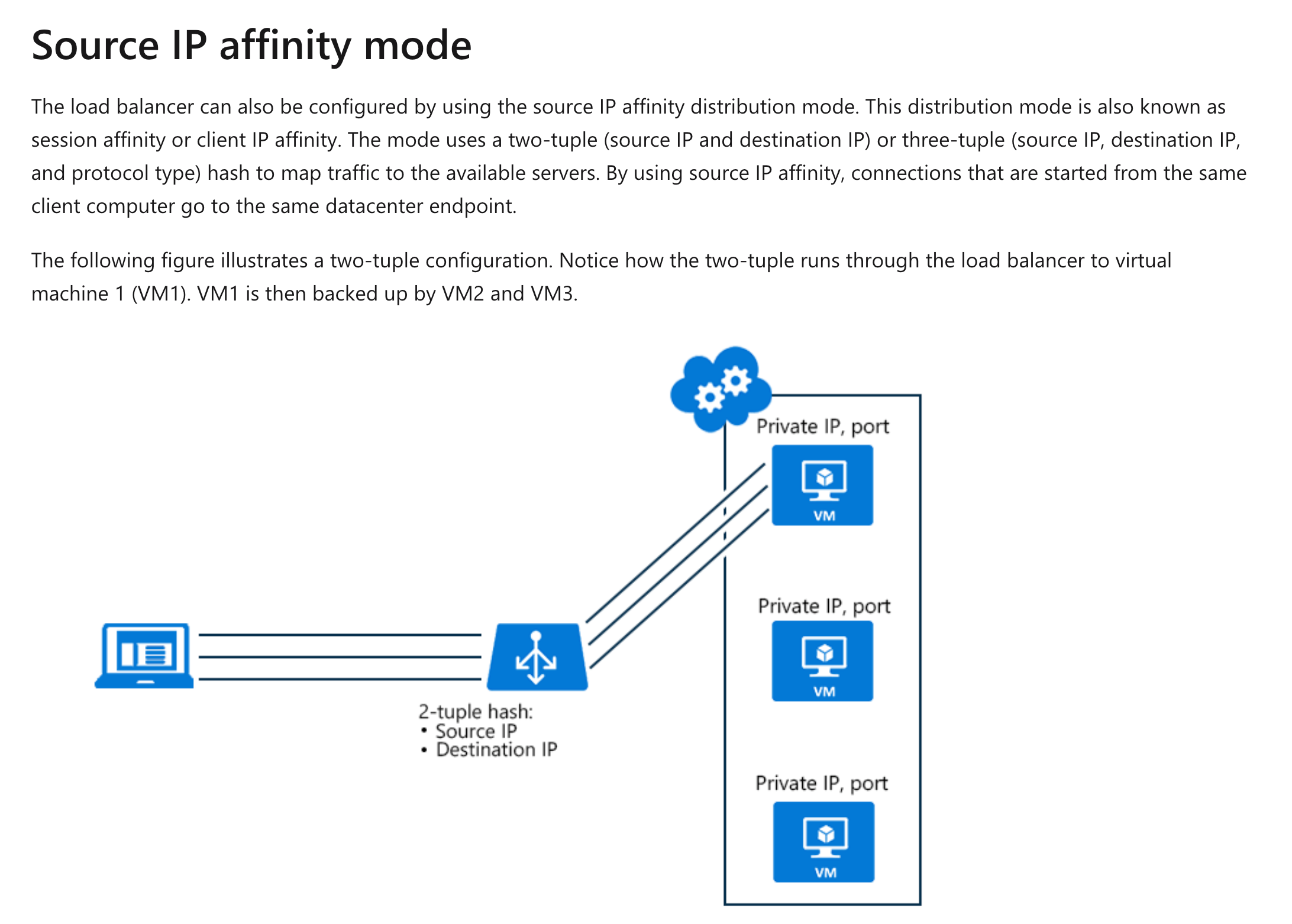
Option A is incorrect since this is used when you have multiple front-end IPs.
Option B is incorrect since this is used to check the health of the back-end VM’s.
Option D is incorrect since this is used for an idle timeout.
For more information on load balancer distribution mode, please go to the below URL-
A company has started using Azure and set up a subscription. They want to see the costs being incurred for each type of resource. Which of the following can help you get these details?
- A. Go to your Azure AD directory and go to Cost Analysis.
- B. Go to your Subscription and go to Cost Analysis.
- C. Go to your Azure AD directory and go to Licences.
- D. Go to your Subscription and go to Resource Groups.
Explanation:
Answer - B
If you go to your subscription, look at the Cost Analysis, you can see a breakdown of each resource's costs.
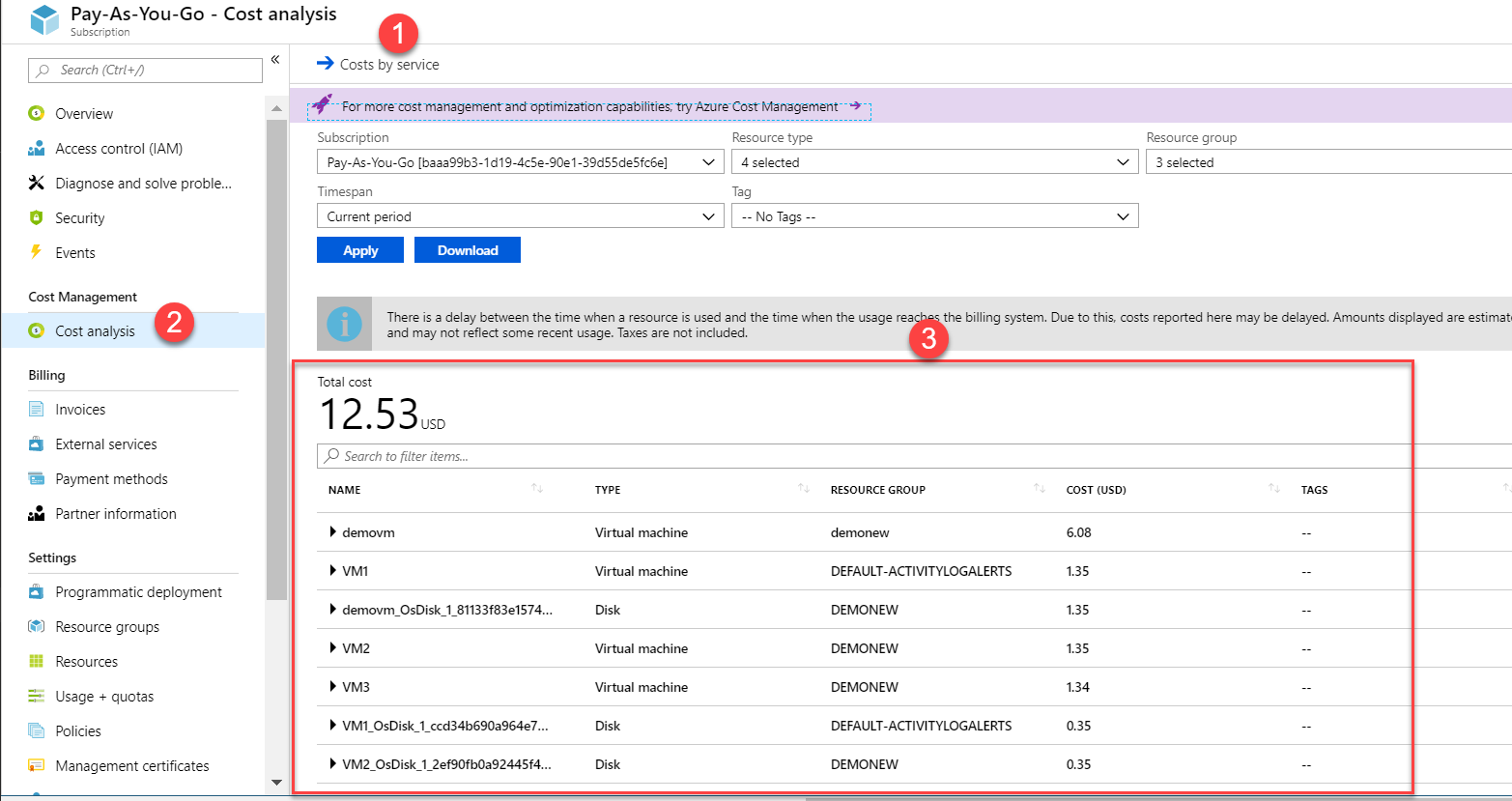
The Cost Analysis section for the subscription allows you to see all the costs. Hence all other options are incorrect.
For more information on cost analysis, please visit the below URL-
Your company currently has a Virtual Network defined in Azure. The Virtual Network has a default subnet that contains 2 Virtual machines named demovm and demovm1. There is a requirement to inspect all network traffic between the Virtual Machines for a duration of 3 hours.
You propose a solution to create a Data Collector Set.
Does this solution fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The right solution is to use Network Watcher.
A Data Collector Set is used to collect data for Performance counters.
For more information on Data Collector sets, please visit the below URL-
Your company currently has a Virtual Network defined in Azure. The Virtual Network has a default subnet that contains 2 Virtual machines named demovm and demovm1. There is a requirement to inspect all network traffic between the Virtual Machines for a duration of 3 hours.
You propose a solution to run Packet Capture on Azure Network watcher.
Does this solution fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - A
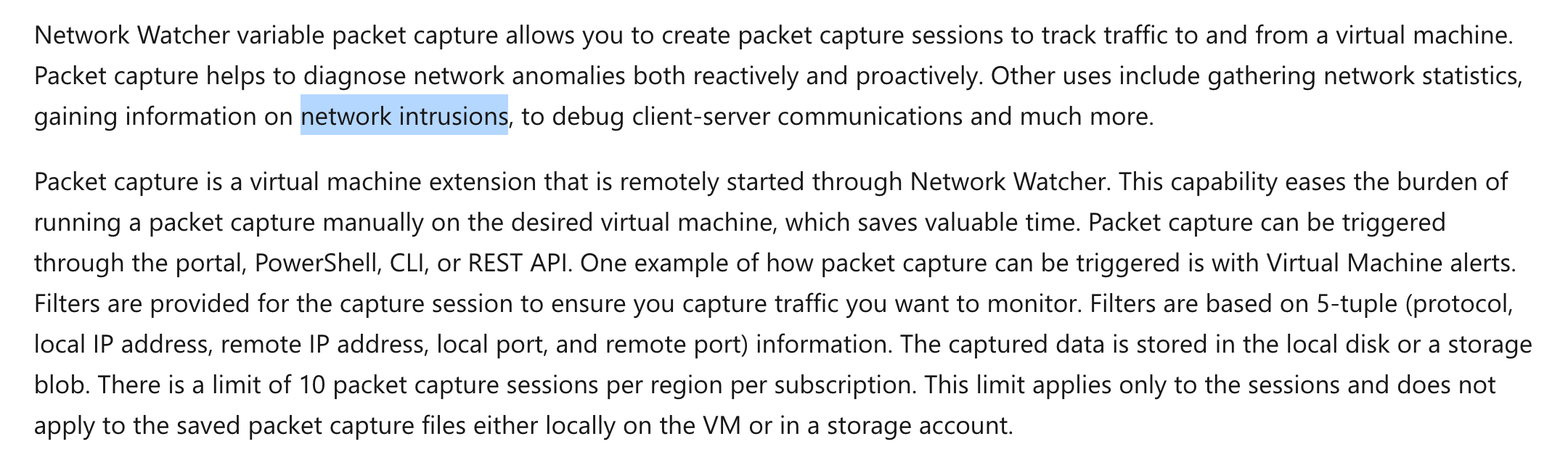
The Microsoft documentation mentions the following.
"Network Watcher variable packet capture allows you to create packet capture sessions to track traffic to and from a virtual machine. Packet capture helps to diagnose network anomalies both reactively and proactively. Other uses include gathering network statistics, gaining information on network intrusions, to debug client-server communications and much more."
For more information on Network watcher, please go ahead and visit the below URL-
Your company currently has a Virtual Network defined in Azure. The Virtual Network has a default subnet that contains 2 Virtual machines named demovm and demovm1. There is a requirement to inspect all network traffic between the Virtual Machines for a duration of 3 hours.
You propose a solution to create a metric chart for Network In and Network Out.
Does this solution fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
The creation of the metric Chart for Network Monitoring will reveal the number of packets coming into and out of the Virtual machine. But it will not do detailed packet inspection.
For more information on monitoring Virtual Machine, please go ahead and visit the below URL-
You are the Azure administrator for a company. You have to create a custom role based on the Virtual Machine Contributor role. You have to complete the following PowerShell script.
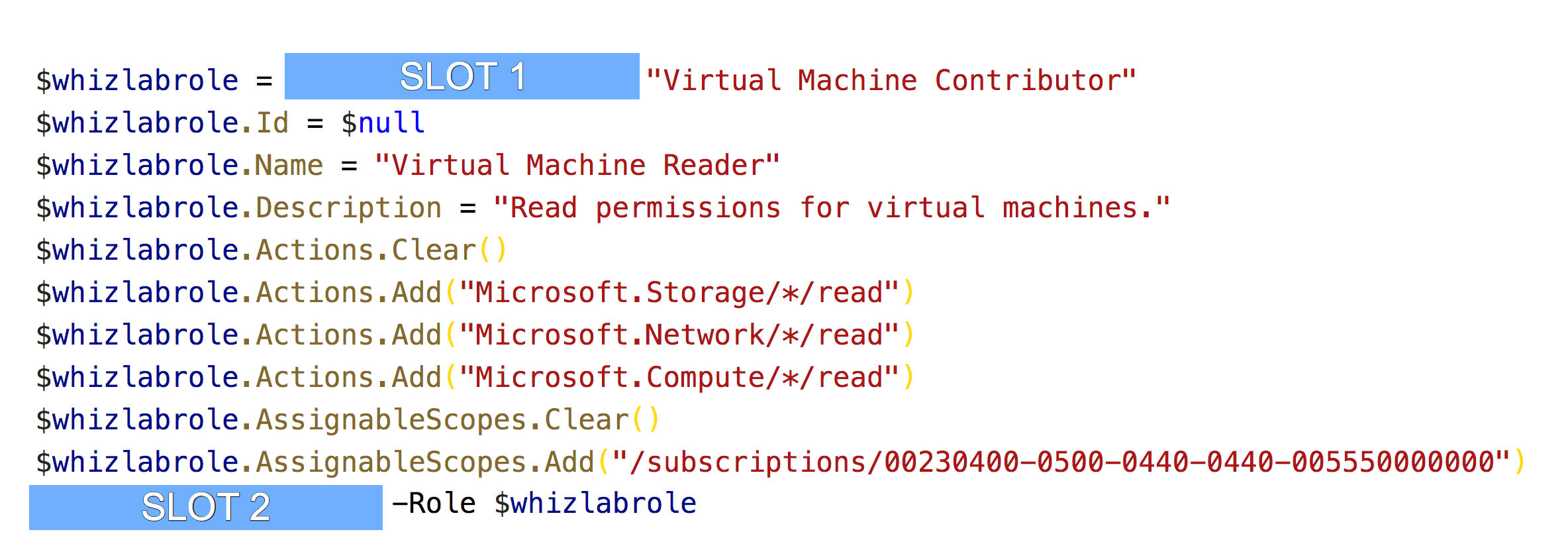
Which of the following would come in SLOT 1?
- A. Get-AzRoleDefinition
- B. New-AzRoleDefinition
- C. Set-AzRoleDefinition
- D. Create-AzRoleDefinition
Explanation:
Answer – A
First, we need to get the role definition.
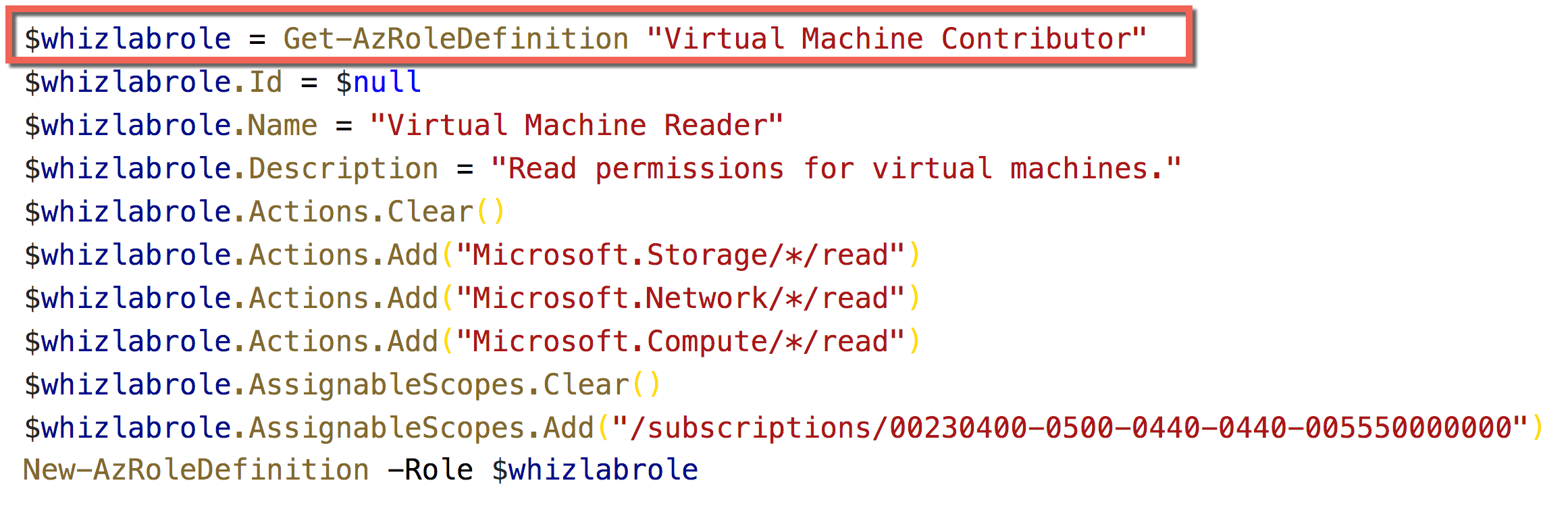
All other options are incorrect.
For more information on creating a custom role, please visit the below URL-
You are the Azure administrator for a company. You have to create a custom role based on the Virtual Machine Contributor role. You have to complete the following PowerShell script.

Which of the following would come in SLOT 2?
- A. Get-AzRoleDefinition
- B. New-AzRoleDefinition
- C. Set-AzRoleDefinition
- D. Create-AzRoleDefinition
Explanation:
Answer – B
After we created a new role definition for "Virtual Machine Reader" based on "Virtual Machine Contributor", we can commit a new role definition.
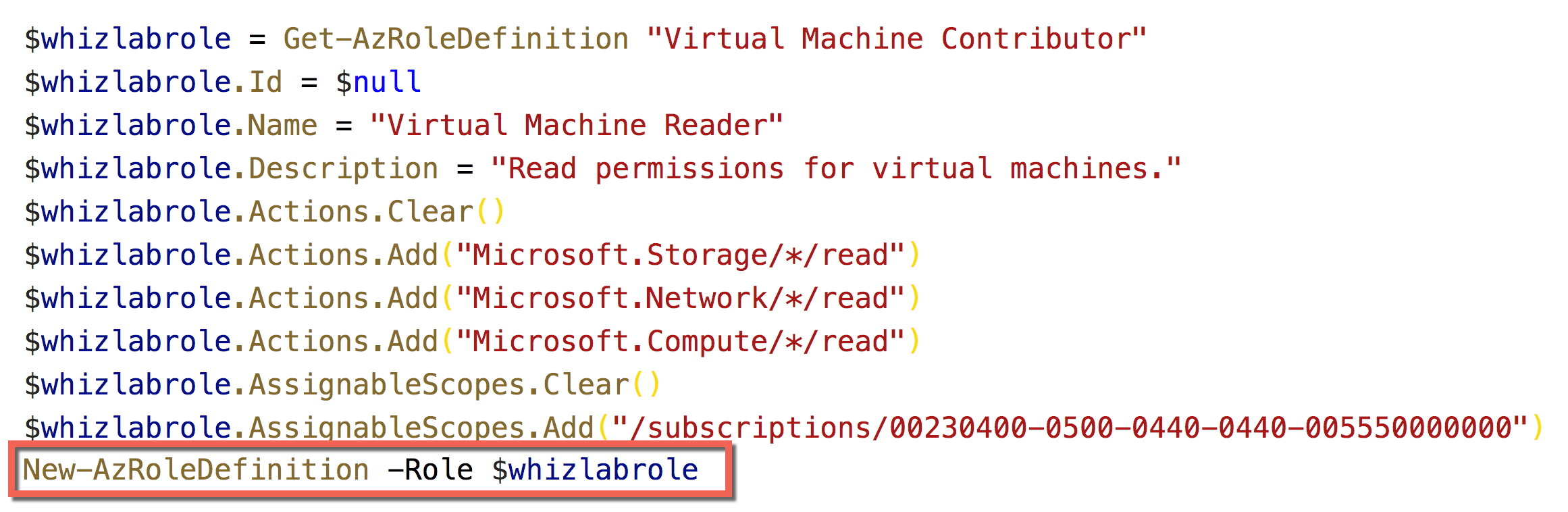
All other options are incorrect.
For more information on creating a custom role, please visit the below URL-
A company has just set up an Azure account and subscription. There is a requirement to ensure that IT administrators can only spin up virtual machines of a particular SKU size. Which of the following can help achieve this?
- A. Create an RBAC role and assign it to the relevant resource group.
- B. Create an Azure policy and assign it to the subscription.
- C. Assign the appropriate AD role to the IT administrators’ group.
- D. Assign the appropriate subscription policy to the IT administrators’ group.
Explanation:
Answer – B
Azure policies are used for governance purposes. The Microsoft documentation mentions the following.

Option A is incorrect since policies are used to control permissions at the resource property level.
Option C is incorrect since Azure AD roles are specifically meant to control access to Azure AD.
Option D is incorrect since there is no concept of subscription policies.
For more information on this example, one can go to the following URLs-
A company has the following set of Virtual Machines defined in the Azure account.
| Name | Region |
| whizlabs-vm1 | East US |
| whizlabs-vm2 | Central US |
The company wants to move whizlabs-vm1 to another subscription. Which of the following can be implemented to fulfill this requirement?
- A. Move the Virtual Machine to the Central US region first.
- B. You cannot move the Virtual Machine across subscriptions. You would need to delete and recreate the VM in the new subscription.
- C. Use the Move-AzResource powershell command to move the Virtual Machine.
- D. Use the Move-VMResource powershell command to move the Virtual Machine.
Explanation:
Correct Answer – C
You can move Azure resources across subscriptions using the Move-AzResource PowerShell command. There are just some restrictions when moving Virtual Machines.
Below is the command provided in the Microsoft documentation.
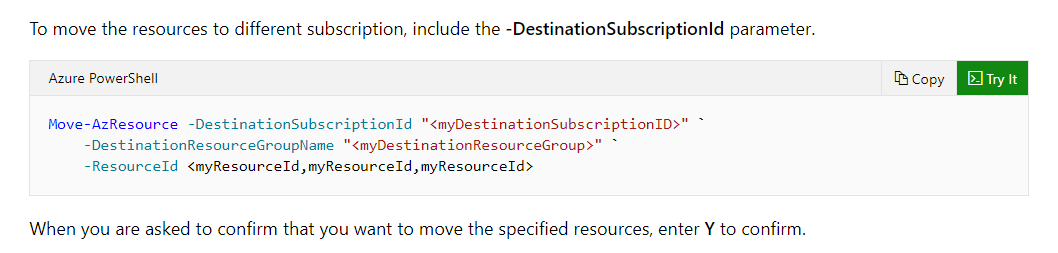
Option A is incorrect since you don’t need to move the Virtual machine to any specific region before moving it to the destination.
Option B is incorrect since you can move resources across subscriptions.
Option D is incorrect since the right command is Move-AzResource.
For more information on moving virtual machines, one can go to the following link-
A team has a Virtual Machine defined in Azure. The Networking details are given below.
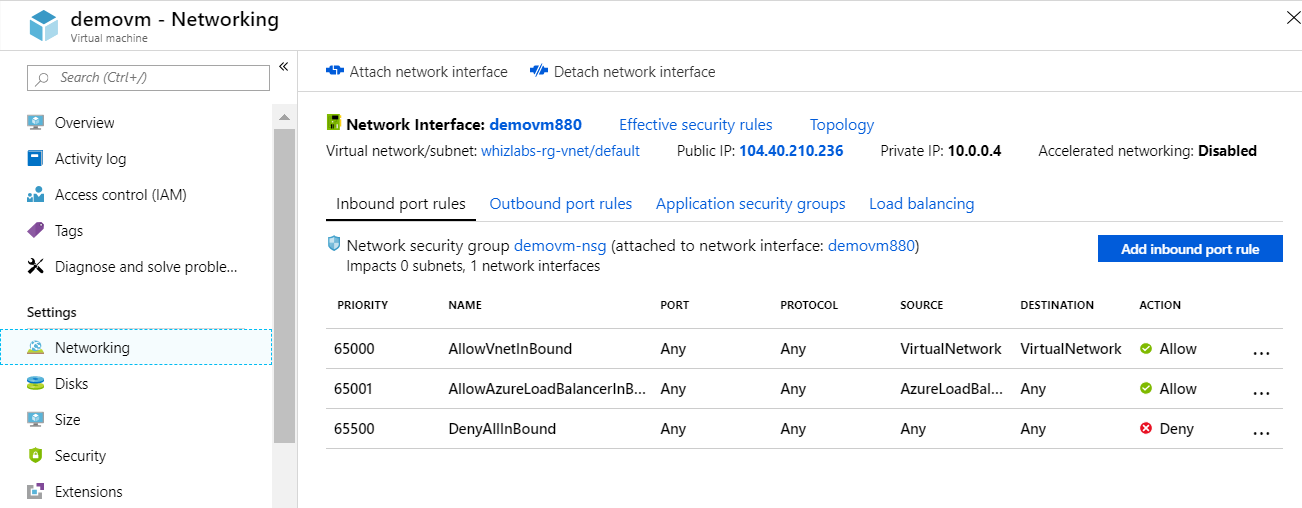
A new network interface named secondary has been created. The Network interface needs to be added to the Virtual machine. What must be done first to ensure that the network interface can be attached to the Virtual Machine?
- A. The machine needs to be stopped first.
- B. The primary network interface needs to be removed
- C. The Network security group rules needs to be removed from the network interface
- D. The public IP needs to be deallocated from the primary network interface
Explanation:
Answer – A
In order to add a network interface to a virtual machine, the machine needs to be stopped first. The Microsoft documentation also mentions this.
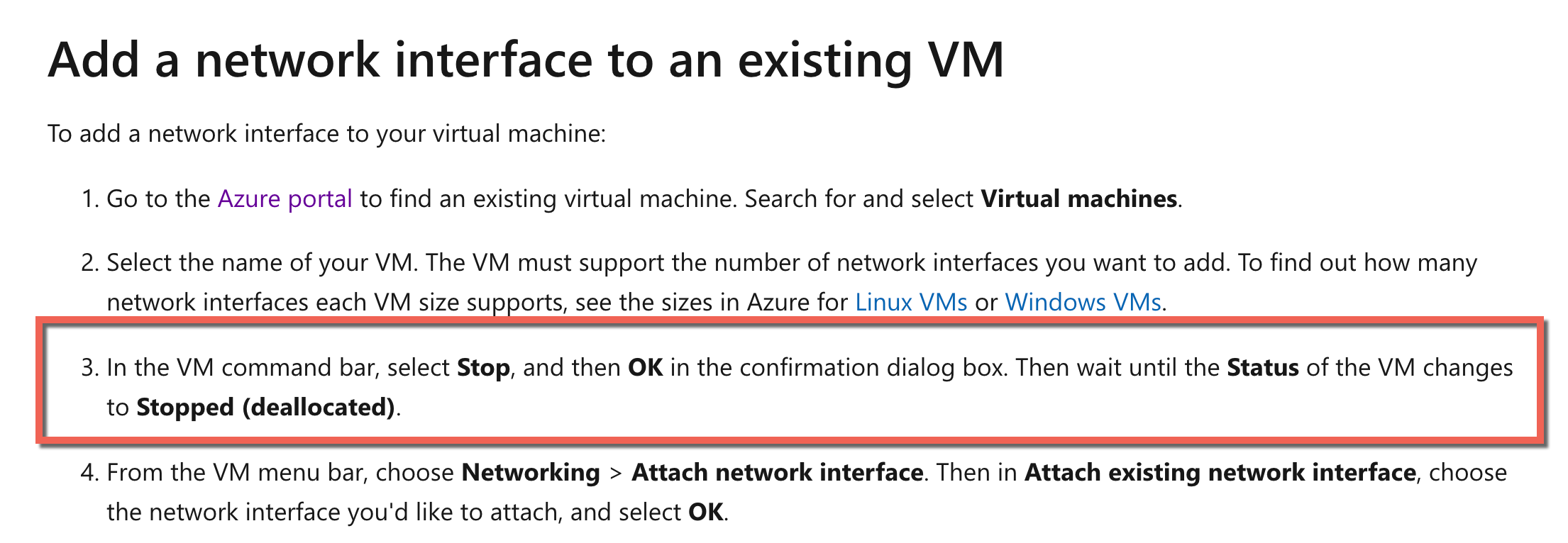
Since the right option is given in the Microsoft documentation, all other options are invalid.
For more information on adding a network interface, one can go to the following link-
A company has the following virtual networks defined in Azure.
|
Name |
Address space |
|
whizlabs-network1 |
10.1.0.0/16 |
|
whizlabs-network2 |
10.2.0.0/16 |
The following virtual machines have been defined as well.
|
Name |
Network |
|
whizlabsvm1 |
whizlabs-network1 |
|
whizlabsvm2 |
whizlabs-network2 |
The necessary peering connections have been created between whizlabs-network1 and whizlabs-network2. The firewalls on the virtual machines have been modified to allow ICMP traffic. But traffic does not seem to flow between the virtual machines when the ping request is made.
Which of the following can be used to diagnose the issue?
- A. Application Insights
- B. IP Flow Verify
- C. Azure Advisor
- D. Microsoft Defender for Cloud
Explanation:
Answer – B
The issue could be due to the security groups. You can diagnose the issue using IP Flow Verify.
The Microsoft documentation mentions the following.
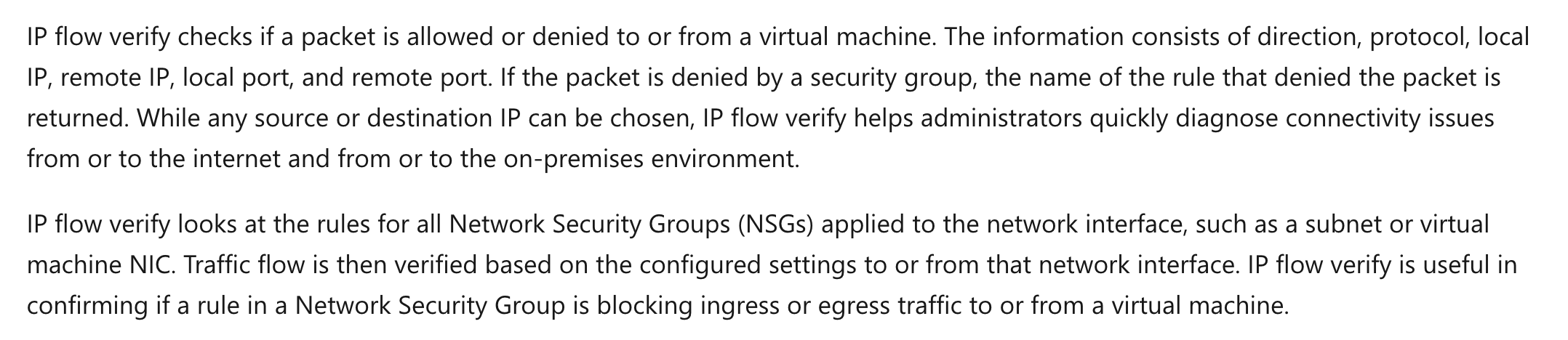
Option A is incorrect since this is normally used from an application diagnostics perspective.
Option C is incorrect since this is used to provide recommendations on various types of Azure resources.
Option D is incorrect since this is used mainly from a security aspect in Azure.
For more information on IP Flow Verify, one can go to the following link-
A company has the following virtual networks defined in Azure.
|
Name |
Address space |
|
whizlabs-network1 |
10.1.0.0/16 |
|
whizlabs-network2 |
10.2.0.0/16 |
The following virtual machines have been defined as well.
|
Name |
Network |
|
whizlabsvm1 |
whizlabs-network1 |
|
whizlabsvm2 |
whizlabs-network2 |
The necessary peering connections have been created between whizlabs-network1 and whizlabs-network2. The firewalls on the virtual machines have been modified to allow ICMP traffic. But traffic does not seem to flow between the virtual machines when the ping request is made.
The security department wanted to check on any network intrusions into the virtual networks. Which of the following tool could be used for this purpose?
- A. IP Flow Verify
- B. Packet Capture
- C. Azure connection monitor
- D. Application Insights
Explanation:
Answer - B
The Microsoft documentation mentions the following.
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on packet capture, one can go to the following link-
Your company has an Azure account and subscription. The subscription contains a virtual machine named demovm.
In your office, you have Windows 10 PC named Computer1 that is connected to the Internet. You add a network interface to the demovm, as shown in the exhibit below.
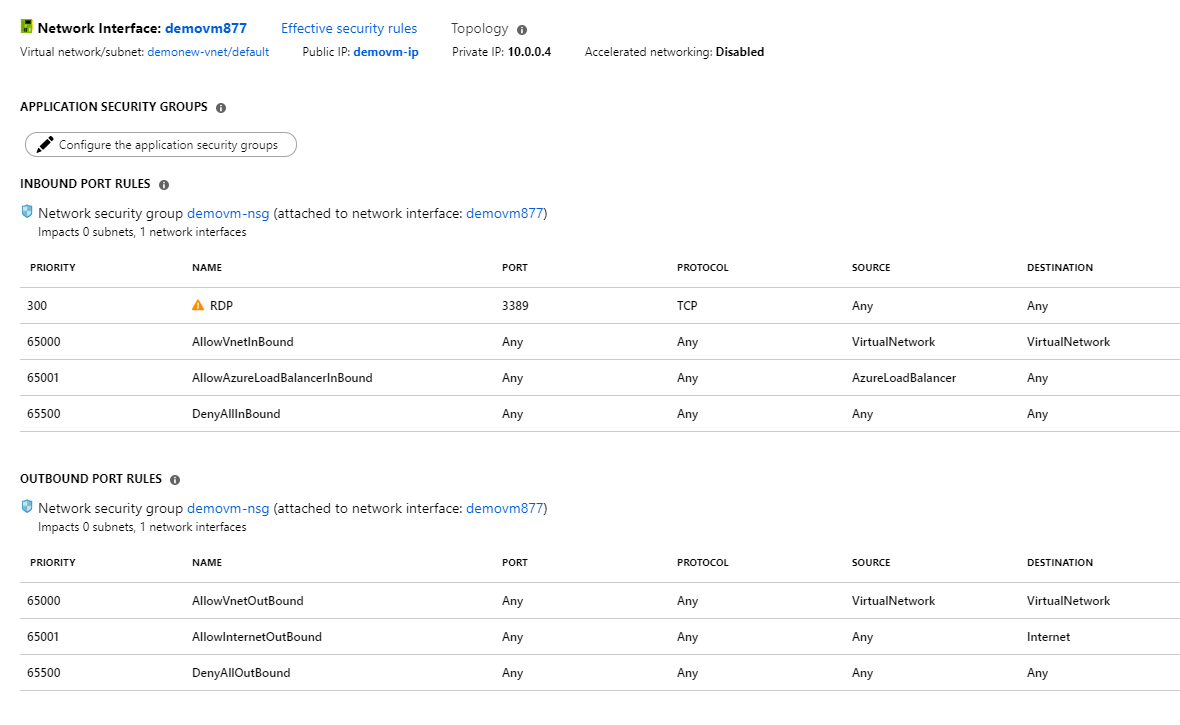
You are trying to connect to demovm from Computer1 using Remote Desktop, but the connection fails. You need to establish a Remote Desktop connection to demovm.
What should you do first?
- A. Start demovm.
- B. Attach a network interface.
- C. Delete the DenyAllOutBound outbound port rule.
- D. Delete the DenyAllInBound inbound port rule.
Explanation:
Answer – A
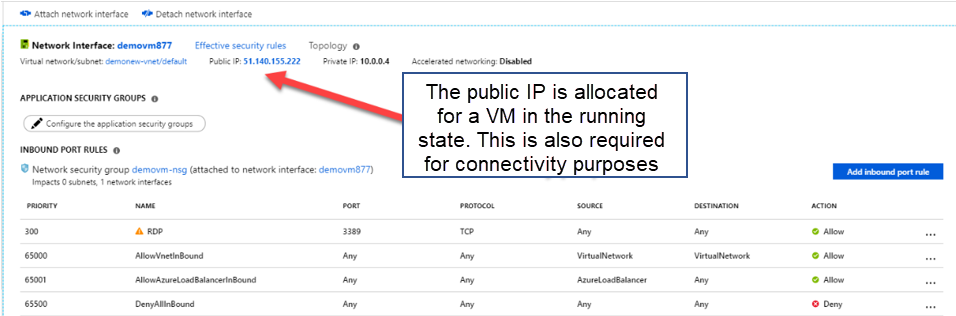
Here the main issue is that demovm is not started and doesn't have allocated an IP address. When you start demovm, you will get a public IP address, which will be assigned to the Network Interface.
The Network security groups are fine for allowing RDP access.
Option B is incorrect because adding a new interface will not solve the connectivity issue.
Options C and D are incorrect since you cannot delete the built-in network security group rules.
For more information on Network security groups, please go to the below URL-
Your company has an Azure account and subscription. The subscription contains a virtual machine named demovm.
In your office, you have Windows 10 PC named Computer1 that is connected to the Internet.
You add a network interface to demovm as shown in the exhibit below.
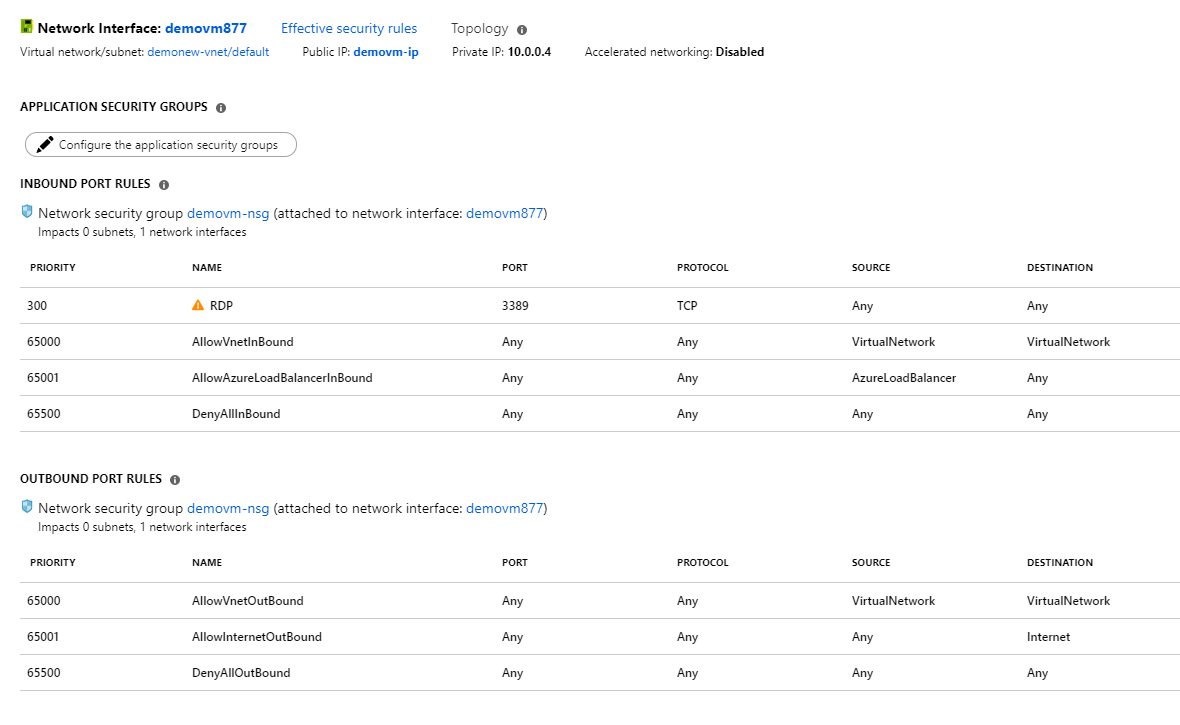
From Computer1 you want to access a web service running on port 80 after demovm is started.
Which of the following must be done for this to work?
- A. Attach a network interface.
- B. Add an incoming network security group rule for allowing traffic on port 80
- C. Add an outgoing network security group rule for allowing traffic on port 80
- D. Delete the DenyAllOutBound outbound port rule.
- E. Delete the DenyAllInBound inbound port rule.
Explanation:
Answer – B
Here you need to add an incoming rule to allow traffic on port 80
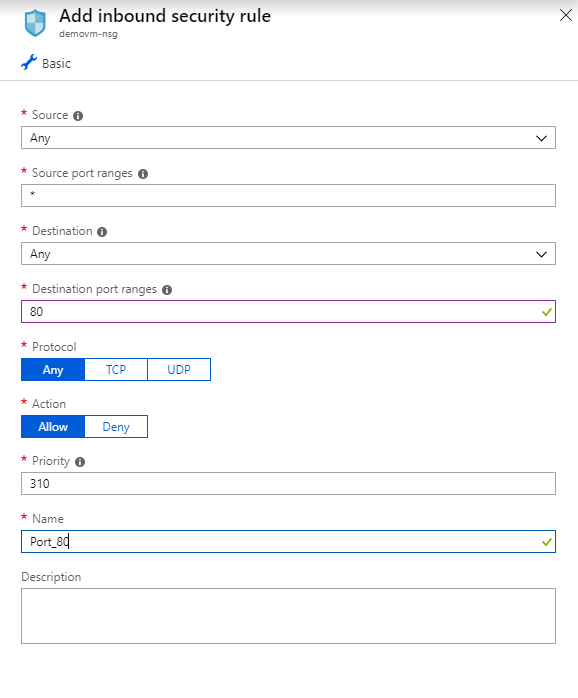
Option A is incorrect since this needs to be done for the currently attached network interface.
Option C is incorrect since the incoming traffic needs to be allowed.
Options D and E are incorrect since you cannot delete the built-in network security group rules.
For more information on Network security groups, please go to the below URL
Your company has an Azure account and subscription. The subscription contains the resources in the following table.
|
Name |
Type |
|
whizlabs-sc |
Storage container |
|
whizlabs-rg |
Resource Group |
|
documents |
BLOB container |
|
demo |
File share |
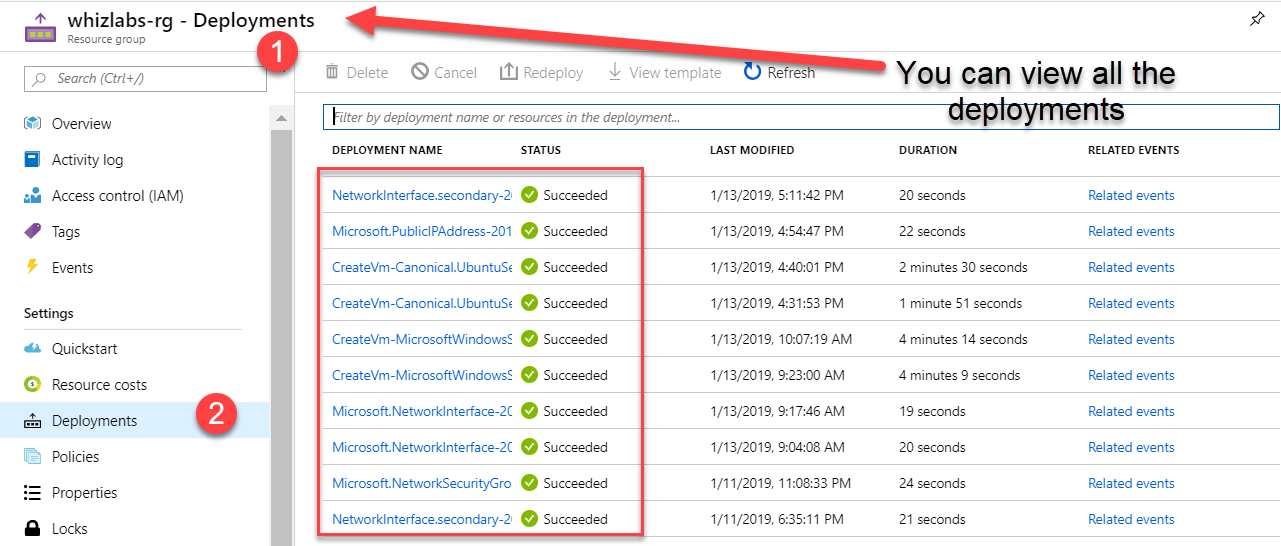
Your IT administrator has deployed a virtual machine called demovm and a storage account called whizlabstore by using a single Azure Resource Manager template. You want to do a review of the template that was used for the deployment. Which of the following resource blade could be used to view the template that was used for the deployment?
- A. whizlabs-rg
- B. demovm
- C. whizlabs-sc
- D. whizlabstore
Explanation:
Answer – A
If you go to the Resource Group blade, you can see the resource group's deployments. An example is shown below.
And if you open any deployment, you can see the template used for the deployment.
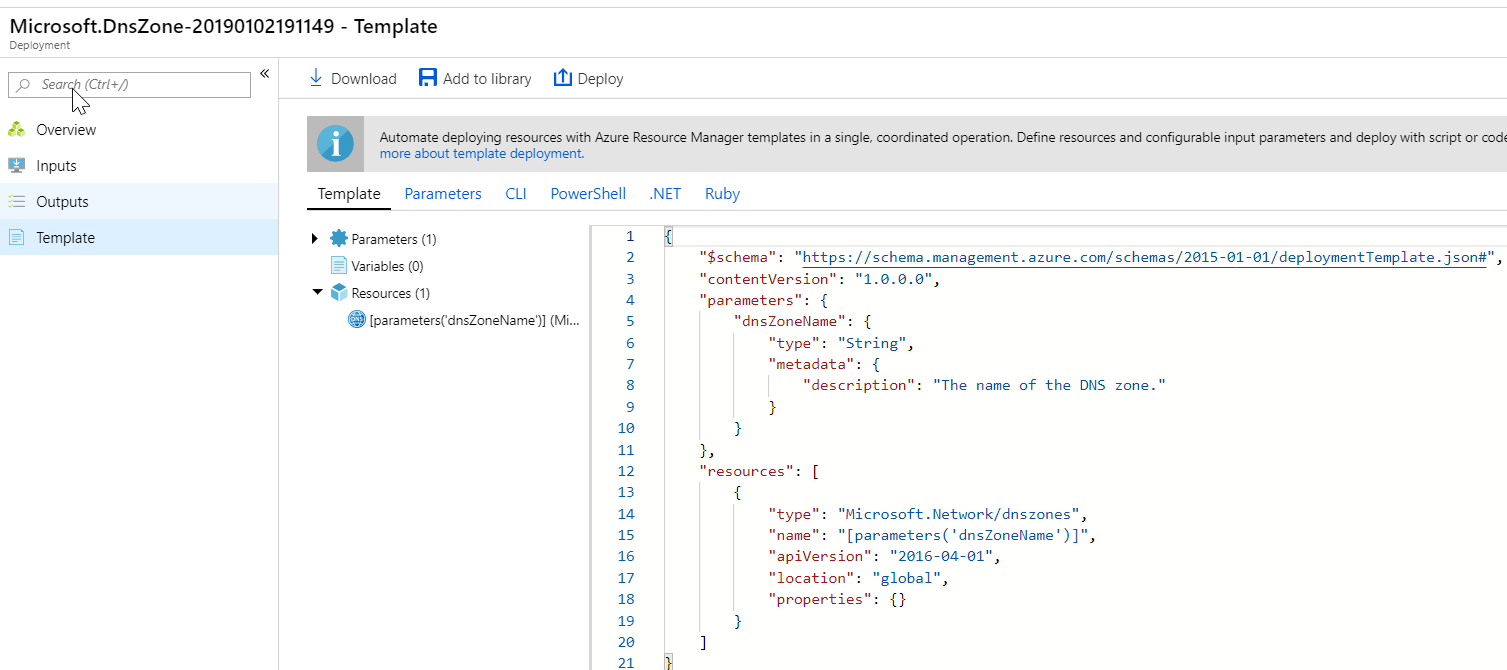
The other options are incorrect because these will not give the overall template deployment for multiple resources.
For more information on resource template deployments, please visit the below URL-
Your company has an Azure subscription. In the subscription, you create an Azure file share named share1. You also create a shared access signature (SAS) named SASdemo, as shown in the following exhibit.
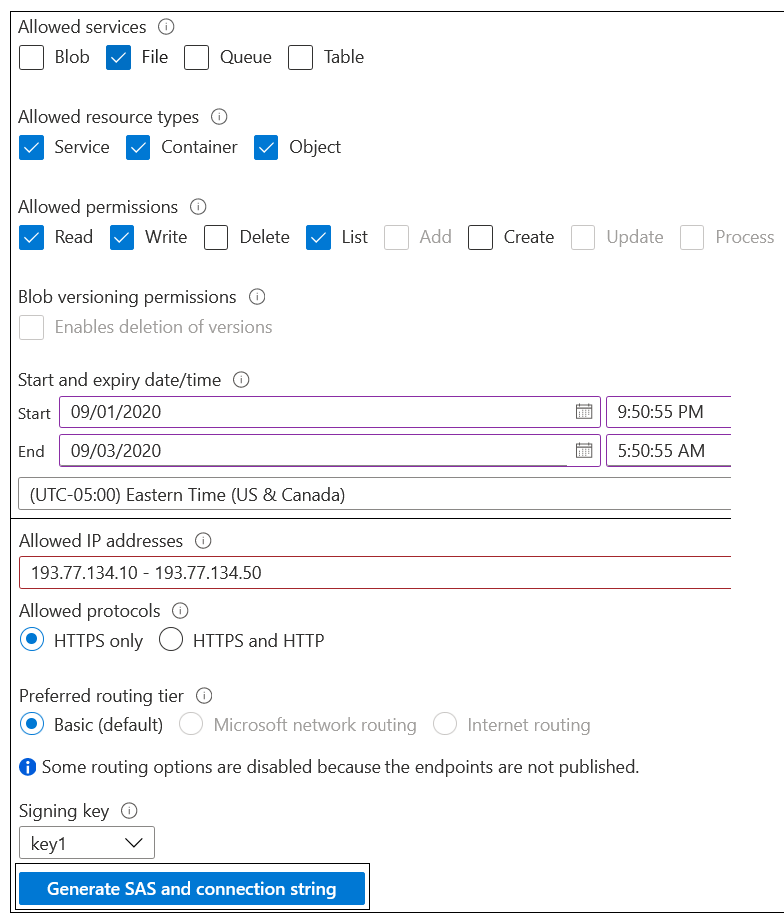
If you run Microsoft Azure Storage Explorer on a computer that has an IP address of 193.77.134.1 and you use SASdemo to connect to the storage account, then you
- A. will be prompted for the credentials.
- B. will have no access.
- C. will have read, write and list access.
- D. will have read-only access.
Explanation:
Answer – B
Since the IP address is not in the valid IP address range defined by the SAS, you will be denied access.
You will get the below error in Azure Storage Explorer.
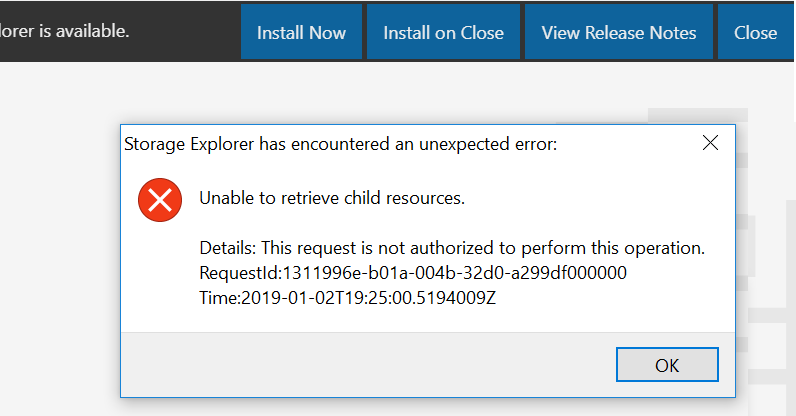
All other options are incorrect.
For more information on Shared access signatures, please go to the below URL-
Your company has an Azure subscription. In the subscription, you create an Azure file share named share1. You also create a shared access signature (SAS) named SASdemo, as shown in the following exhibit.
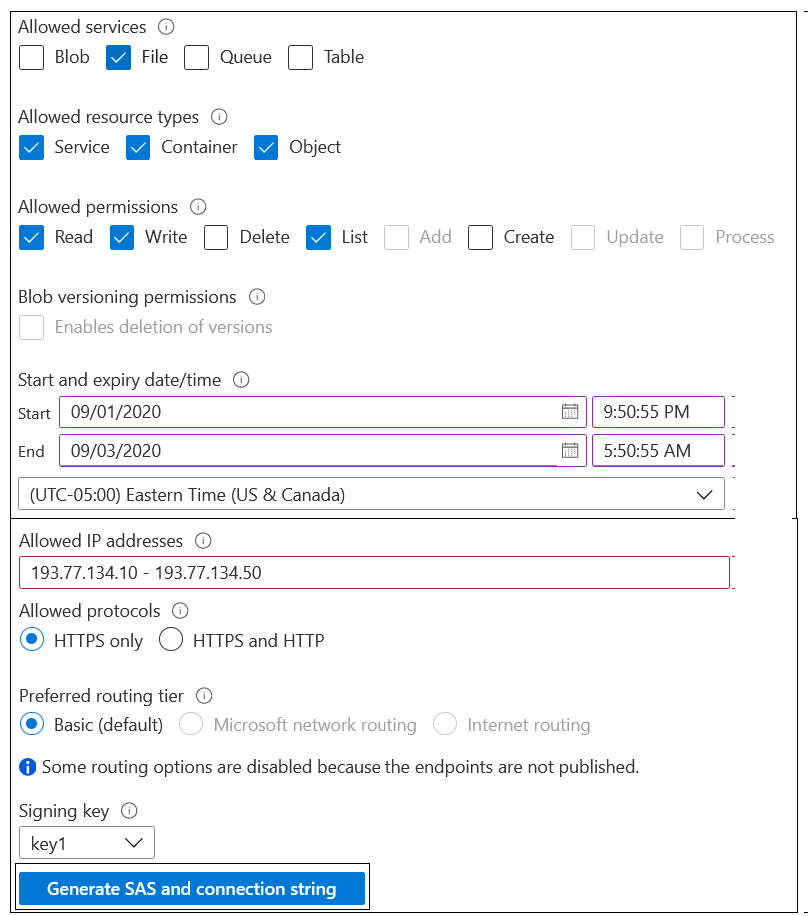
If you use the "net use" command on a computer that has an IP address of 193.77.134.50 and then use SASdemo to connect to share1, then you
- A. will be prompted for the credentials
- B. will have no access
- C. will have read,write and list access
- D. will have read-only access
Explanation:
Answer — B
"net use" command is a Command Prompt command that's used to connect to, remove, and configure connections to shared resources, like mapped drives and network printers."
As per the question, we need to use the "net use" command on a computer that has an IP address of 193.77.134.50 and then use SASdemo to connect to share1.
- The net use command is used to connect to file shares(SMB protocol), and SMB is not supported with SAS.
- Storage account key: To mount an Azure file share, you will need the primary (or secondary) storage key. SAS keys are not currently supported for mounting.
It is clear that B is the correct answer and the rest all other options are incorrect
References:
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network interfaces that you require?
- A. 5
- B. 10
- C. 15
- D. 20
Explanation:
Answer – A
The network interface for a Virtual Machine can have both a private and public IP address.
So, by this measure, we only need to define 5 network interface cards, one for each virtual machine.
It is clear that A is the correct answer and all the other options are incorrect.
For more information on the virtual network interfaces in Azure, please visit the below URL-
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network security groups that you require?
- A. 1
- B. 2
- C. 5
- D. 10
Explanation:
Answer – A
A network security group can have multiple network interfaces assigned to it, as shown in the below diagram.
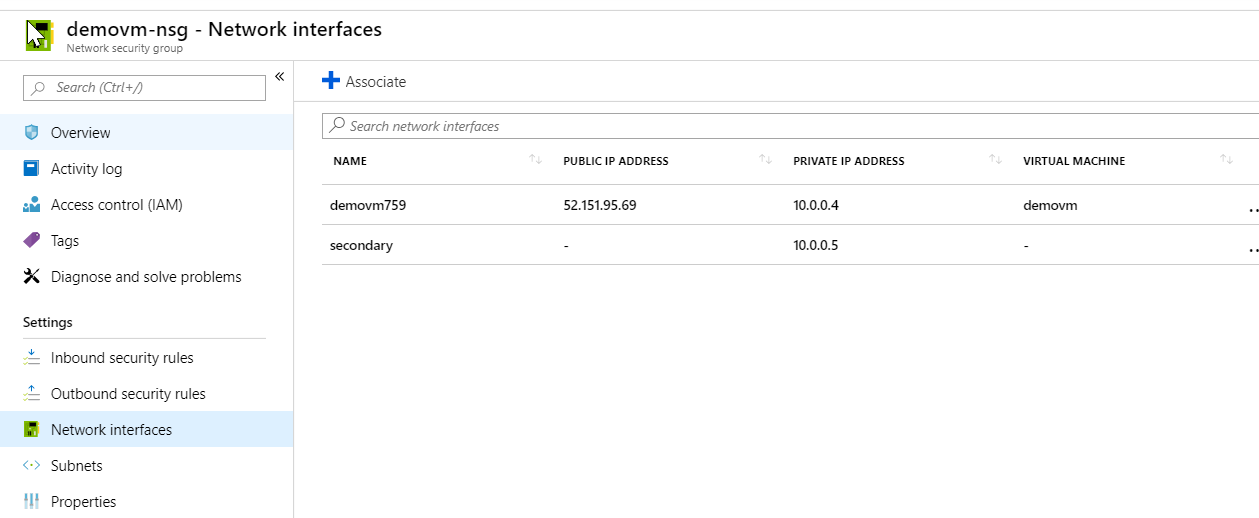
The question clearly states that the virtual machines all require the same inbound and outbound security rules. Hence we should use just the same network security group for all network interfaces.
For more information on network security groups, please visit the below URL-
You have a virtual network named VNET2 that has the configuration shown in the following exhibit.
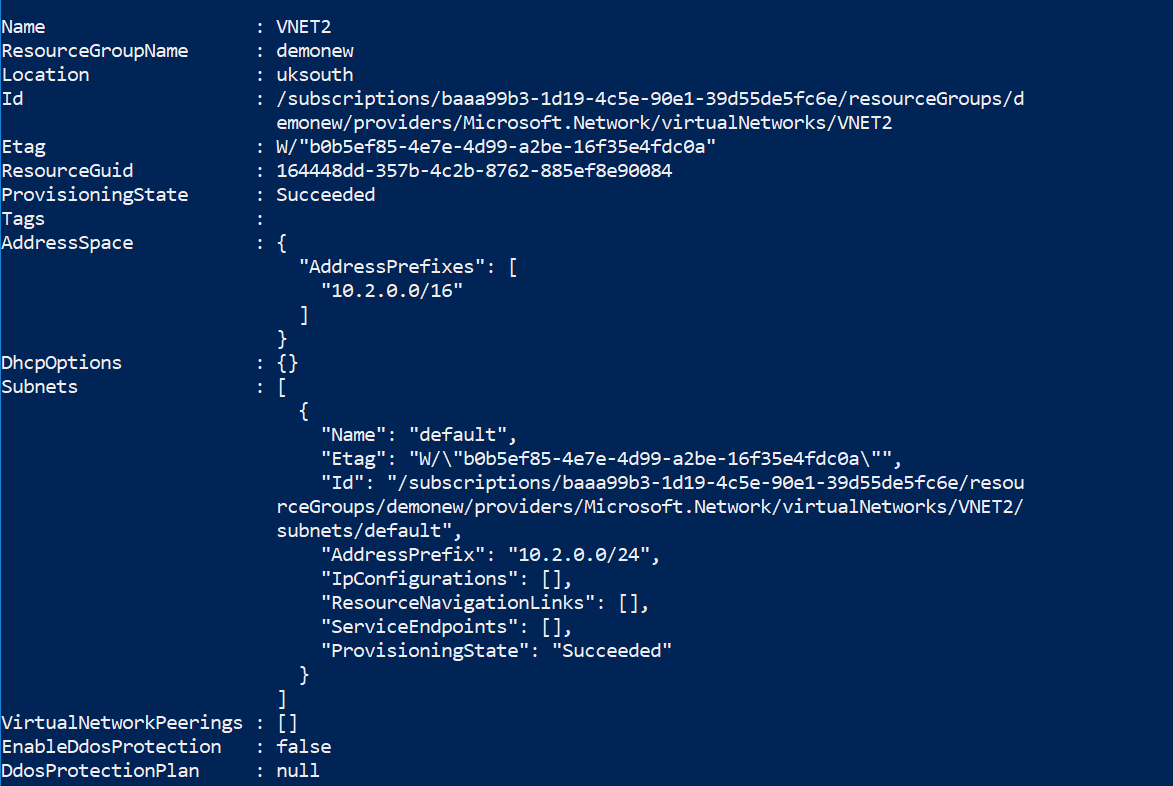
What should you do first before a virtual machine on VNET2 can receive an IP address from 192.168.1.0/24?
- A. Add a network interface.
- B. Add a subnet.
- C. Add an address space.
- D. Delete a subnet.
- E. Delete an address space.
Explanation:
Answer – C
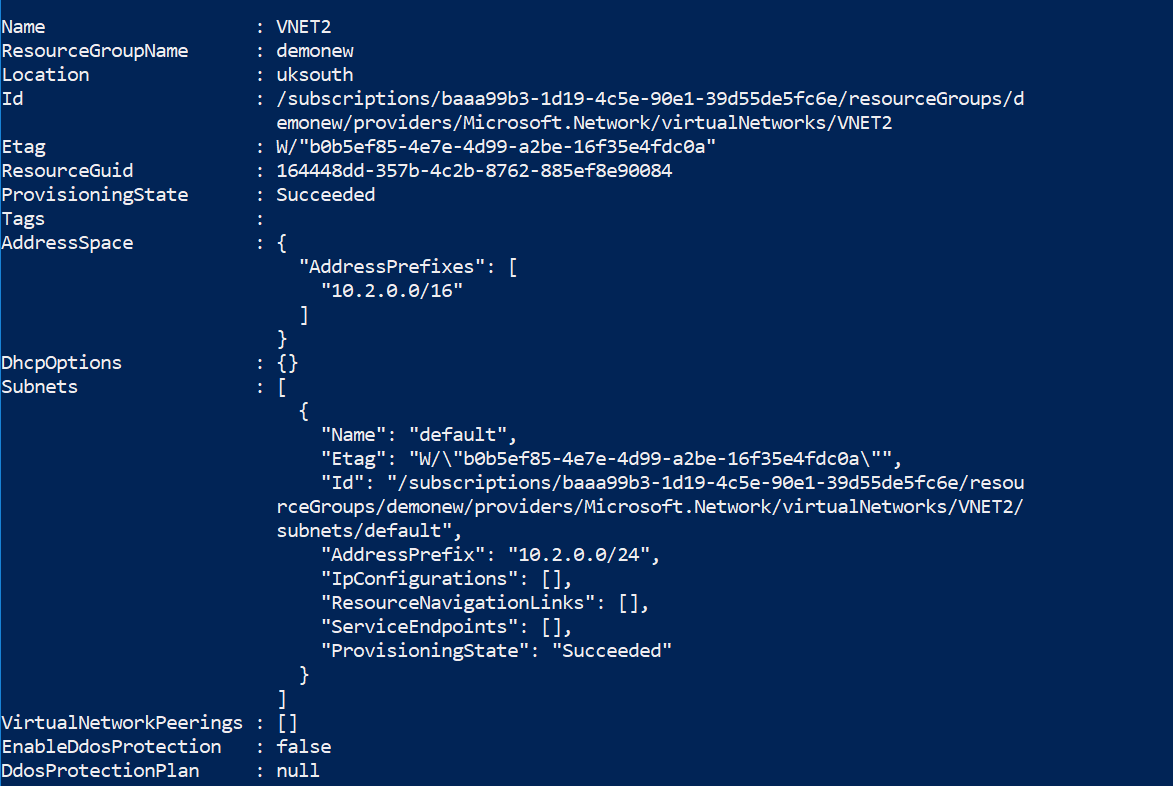
The Virtual Network has no address space relative to 192.168.1.0/24 as per the PowerShell output given in the Exhibit.
Hence first, you need to add an address space, as shown below.
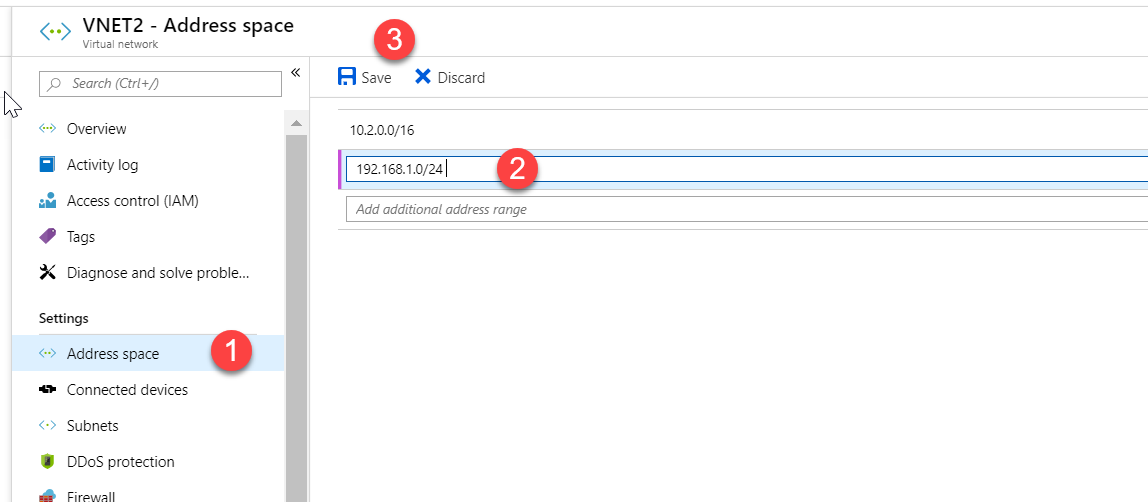
After you save the address space, create a new subnet with the address space, and ensure that the VM is put in the new subnet.
Option A is incorrect since the network interface can only receive an address from 10.2.0.0/24 as per the PowerShell output given in the Exhibit.
Option B is incorrect since you need to add the address space 192.168.1.0/24 before adding the subnet.
Options D and E are incorrect since you need to add the address space and subnet and not delete the address space and subnet.
For more information on Virtual Networks, please go to the below URL-
You have a virtual network named VNET2 that has the configuration shown in the following exhibit.
What should you do first before a virtual machine on VNET2 can receive an IP address from 10.2.1.0/24?
- A. Add a network interface.
- B. Add a subnet.
- C. Add an address space.
- D. Delete a subnet.
- E. Delete an address space.
Explanation:
Answer – B
First, you need to add a new subnet, as shown below.
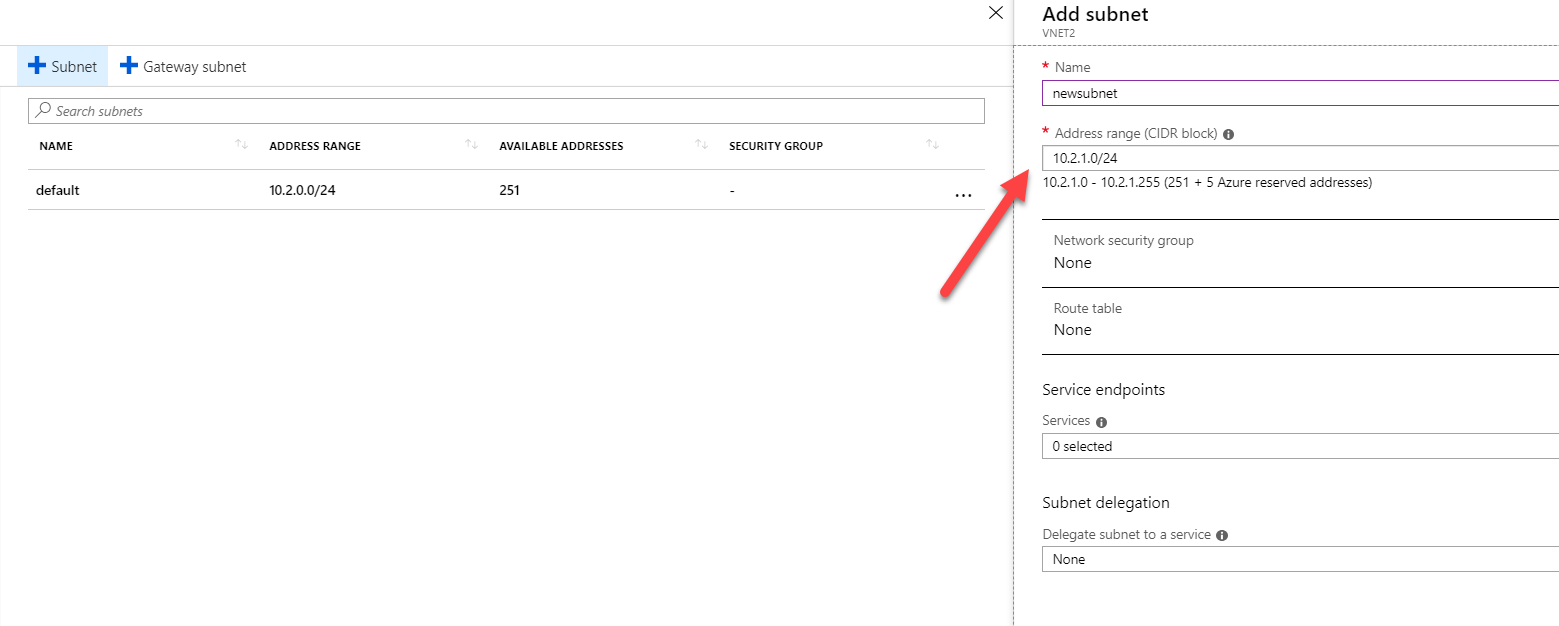
You can then add the new VM as part of the new subnet so that it receives the address from the 10.2.1.0/24 address space.
Option A is incorrect since the network interface can only receive an address from 10.2.0.0/24 as per the PowerShell output given in the Exhibit.
Option C is incorrect since we already have the required address space.
Options D and E are incorrect since you need to add the subnet and not delete the address space and subnet.
For more information on Virtual Networks, please go to the below URL-
You create a new version of your web app. But you still need to finalize the app testing and verification before deploying the latest version to production.
Please select the most effective tool for checking your app and deployment to production.
- A. Create a test App Service app, deploy a new version, test and then copy to production
- B. Create a test VM, deploy a new version, test, zip a new version project, and deploy to production
- C. Create a test deployment slot for your web app, deploy a new version, test and swap the slots
- D. Create a test Docker container with a new version, deploy it to a new App Service, test it and switch the old App Service production to a new one.
- E. Create a test environment on the OneDrive, test and sync content of your new version with App Service
Explanation:
Correct Answer: C
You can deploy your web application to the App Service in a manual or automatic way. App Service provides the Deployment center (Number 1) for continuous deployment from different code management sources: GitHub, Bitbucket, and Local Git (Number 2). You also can use the cloud drives, like OneDrive and Dropbox, to sync a ready-to-deploy code with your application in production or any other environment. For the manual deployment, you can use zip or war compressed files, Visual Studio, FTP, etc. But you still need to test and verify your app before production deployment.
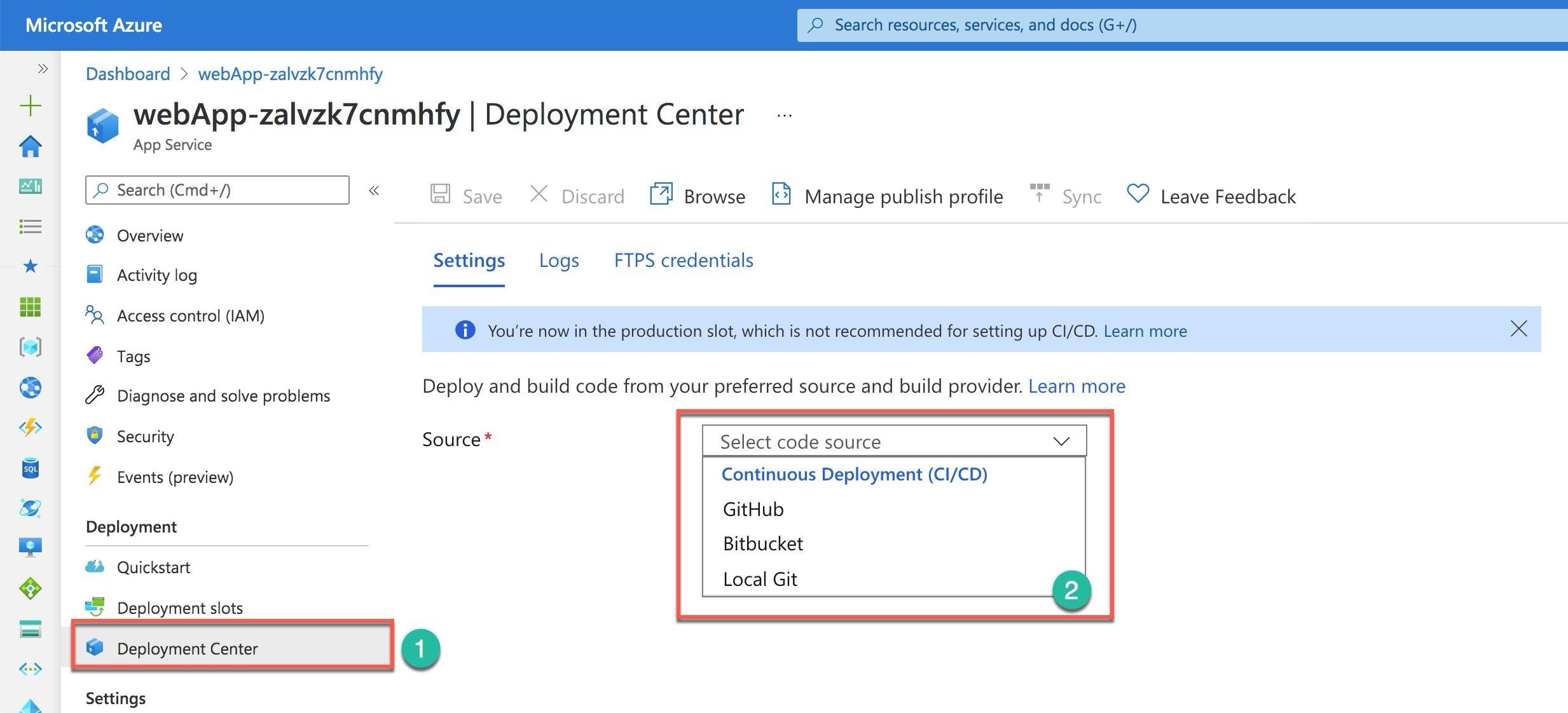
Azure App Service provides a special functionality to help you with testing, a new version verification, and seamless deployment to production. This functionality is the deployment slots. By default, every App Service app has one production slot. If you deploy an application to a Standard and above plan, you would have at least 5 deployment slots to publish or deploy your new code before a release. The deployment slot is another App service app. It has its own URL different from the main (production) application address.
You can select the Deployment slots item (Number 1) under the Deployment section. On the Deployment slots screen, select the Add Slot (Number 2), and the portal opens a new panel to the right to input information about your new slot. You need to provide the new slot’s name (Number 3). Azure will automatically create a web address for your new App service app. And then, you can push the Add button. After the new slot is created, you can deploy your new version to this slot. When you are ready to release, you can swap the slots by pushing the Swap button (Number 4).
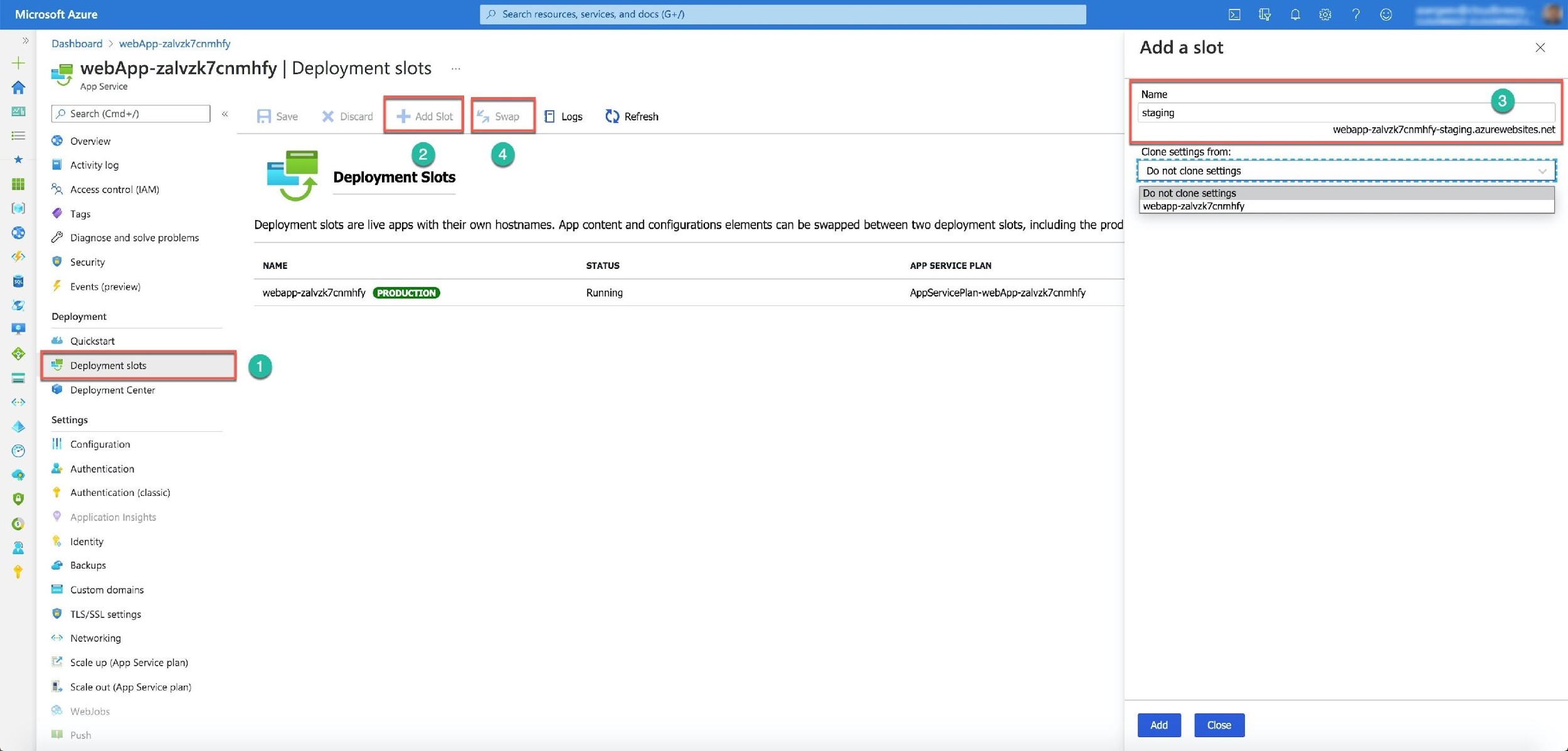
Your new slot will become a production slot, and users can start using the new version of your application. If something happens with the release and you need to roll back to the previous version, you can use the same Swap button to make the old production application the current one.
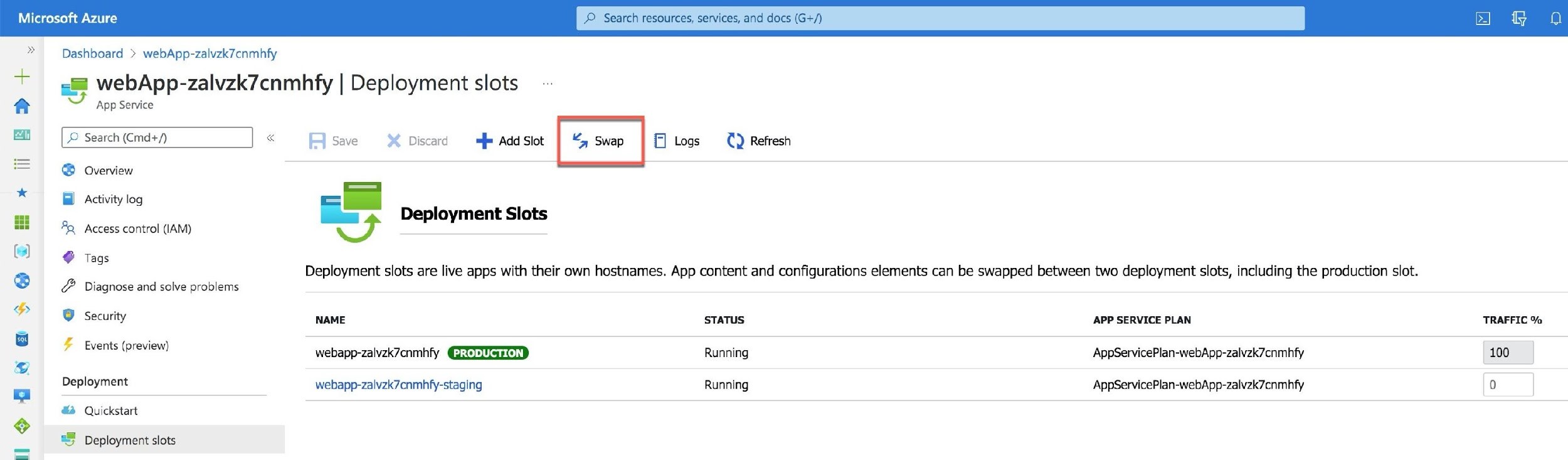
All other options are incorrect.
For more information about App Service app deployment slots, please visit the below URLs:
- https://docs.microsoft.com/en-us/learn/modules/stage-deploy-app-service-deployment-slots/2-create-deployment-slots
- https://docs.microsoft.com/en-us/azure/app-service/deploy-staging-slots
- https://docs.microsoft.com/en-us/learn/modules/host-a-web-app-with-azure-app-service/6-deploying-code-to-app-service
A company needs to create a storage account that must follow the requirements below.
- Users should be able to add files such as images and videos.
- Ability to store archive data.
- File shares need to be in place, which can be accessed across several VM’s.
- The data needs to be available even if a region goes down.
- The solution needs to be cost-effective.
Which of the following type of storage account would you create for this purpose?
- A. BlockBlob Storage
- B. General Purpose(v1)
- C. General Purpose(v2)
- D. Table storage
Explanation:
Answer – C
The below snapshot from the Microsoft documentation shows the different types of storage accounts.
Option B is incorrect since General Purpose V1 is not available anymore.
As we can see that only General Purpose v2 supports all of the requirements. Hence all other options are incorrect.
For more information on storage accounts, please visit the below URL-
A company needs to create a storage account that must follow the requirements below.
- Users should be able to add files such as images and videos.
- Ability to store archive data.
- File shares need to be in place, which can be accessed across several VM’s.
- The data needs to be available even if a region goes down.
- The solution needs to be cost-effective.
What is the type of replication they need to implement for the storage account?
- A. Locally redundant storage (LRS)
- B. Zone-redundant storage (ZRS)
- C. Geo-redundant storage (GRS)
- D. Read-access geo-redundant storage (RA-GRS)
Explanation:
Answer – C
The Microsoft documentation mentions the following.
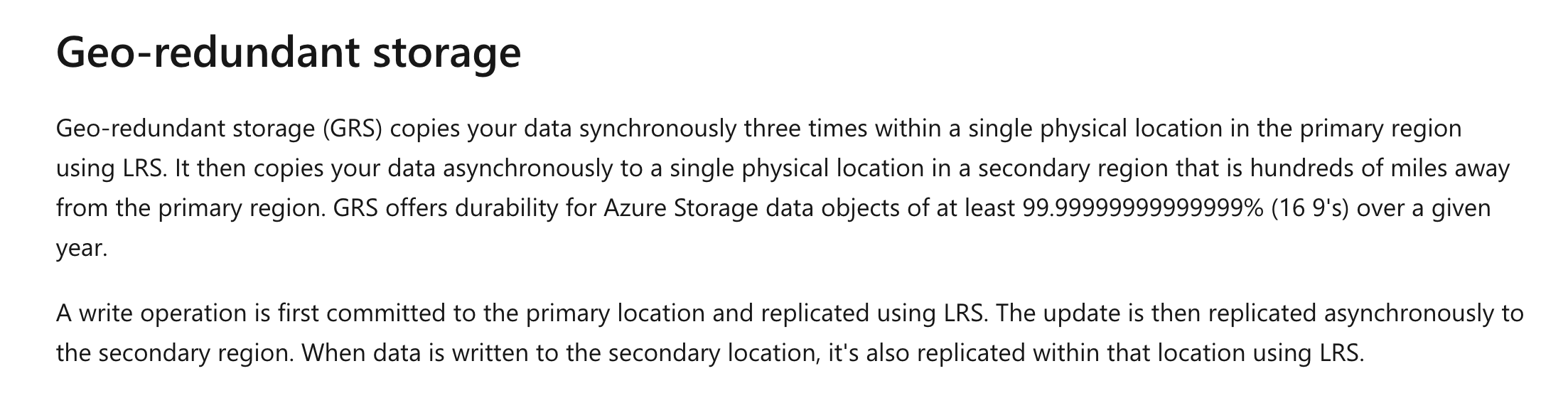
Options A and B are incorrect since these replication strategies don’t replicate the data across regions.
Option D is incorrect because additional read access to data in another region is not mentioned and we also have to keep the cost to a minimum.
For more information on storage redundancy, please visit the below URL-
You need to deploy two Azure virtual machines named VM1 and VM2 based on the Windows server 2016. The deployment must meet the following requirements.
- Provide a Service Level Agreement (SLA) of 99.95 percent availability.
- Use managed disks.
You propose a solution to create a scale set for the requirement.
Would the solution meet the goal?
- A. Yes
- B. No
Explanation:
Answer — B
Virtual Machine Scale Sets is a free service, therefore, it does not have a financially backed SLA itself. However, if the Virtual Machine Scale Sets include Virtual Machines in at least 2 Fault Domains, the availability of the underlying Virtual Machines SLA for two or more instances applies:
Since in the question, creating scale set with fault domain/availability zone is not mentioned.
It is clear that B is the correct answer.
However, we can create an HA machine with Scale set as explain below:
While, creating virtual machines, with scale set spreading algorithm, decide how VM's will be allocated to different fault domain.
Max Spreading -- VM are across as many fault domains as possible
Fix Spreading -- VM are across fault domain as per the user selection, unless user select fix spread with 1 fault domain, the VM's will meet the SLA requirements of the virtual machine.
For details, please see the following link
You need to deploy two Azure virtual machines named VM1 and VM2 based on the Windows server 2016 image. The deployment must meet the following requirements.
- Provide a Service Level Agreement (SLA) of 99.95 percent availability.
- Use managed disks.
You propose a solution to create an availability set for the requirement.
Would the solution meet the goal?
- A. Yes
- B. No
Explanation:
Answer – A
The Microsoft documentation mentions the following.

For more information on availability sets, please visit the below URL-
You need to deploy two Azure virtual machines named VM1 and VM2 based on the Windows server 2016. The deployment must meet the following requirements.
- Provide a Service Level Agreement (SLA) of 99.95 percent availability.
- Use managed disks.
You propose a solution to create a Traffic Manager for the requirement.
Would the solution meet the goal?
- A. Yes
- B. No
Explanation:
Answer – B
Azure Traffic Manager is used for traffic distribution based on DNS queries. For achieving high availability, you need to use Availability sets.
For more information on Azure Traffic Manager, please visit the below URL-
Your company has an Azure account and an Azure subscription. They have created a Virtual Network named whizlabs-net. The following users have been setup.
|
User |
Role |
|
whizlabs-usr1 |
Owner |
|
whizlabs-usr2 |
Security admin |
|
whizlabs-usr3 |
Network Contributor |
Which of the following users would be able to add a subnet to the Virtual Network?
- A. whizlabs-usr1 only
- B. whizlabs-usr2 only
- C. whizlabs-usr3 only
- D. whizlabs-usr1 and whizlabs-usr2 only
- E. whizlabs-usr1 and whizlabs-usr3 only
- F. whizlabs-usr2 and whizlabs-usr3 only
- G. whizlabs-usr1, whizlabs-usr2 and whizlabs-usr3
Explanation:
Answer — E
Azure always allocates the owner role to the user, who creates a new subscription. The owner role can perform any operation, on azure resources, including allocation/modification of the privileges of other users. A contributor can do everything, which the owner can do, except, any operation related to users privileges. Network contributor is a specialization of contributor role, and it can do every operation related to the network.
Option A is not the best option as both user1 and user3 can perform network operation
Option B is incorrect because user2 can perform operations related to security, not related to networking
Option C is not the best answer(Same reason as option A)
Option D is incorrect as user2 can not perform any network operation.
Option F is incorrect due to the same reason as option D.
Option G is incorrect as it is just a distractor.
From the above, it is clear that only user1(owner) and user3(network contributor) can add resources to a network. Hence, E is the correct answer, while all other answers are wrong.
Please see the following link for the network contribution role:
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles#network-contributor
For more information on the built-in roles, please go to the below URLs:
Your company has an Azure account and an Azure subscription. They have created a Virtual Network named whizlabs-net. The following users have been setup.
|
User |
Role |
|
whizlabs-usr1 |
Owner |
|
whizlabs-usr2 |
Security admin |
|
whizlabs-usr3 |
Network Contributor |
Which of the following users can add the Reader role access for a user to the Virtual Network?
- A. whizlabs-usr1 only
- B. whizlabs-usr2 only
- C. whizlabs-usr3 only
- D. whizlabs-usr1 and whizlabs-usr2 only
- E. whizlabs-usr1 and whizlabs-usr3 only
- F. whizlabs-usr2 and whizlabs-usr3 only
- G. whizlabs-usr1, whizlabs-usr2 and whizlabs-usr3
Explanation:
Answer – A
The Network Contributor does not have access to assign roles. And if you look at the Security admin role, it only has the privilege to work with Security Center.

For more information on the built-in roles, please go to the below URLs-
You work as an Azure Administrator for a company. You need to create a role based on the following requirements.
- View all the resources in the Azure subscription.
- Issue support requests to Microsoft.
- Use the principle of least privilege.
You have to complete the below JSON role definition.
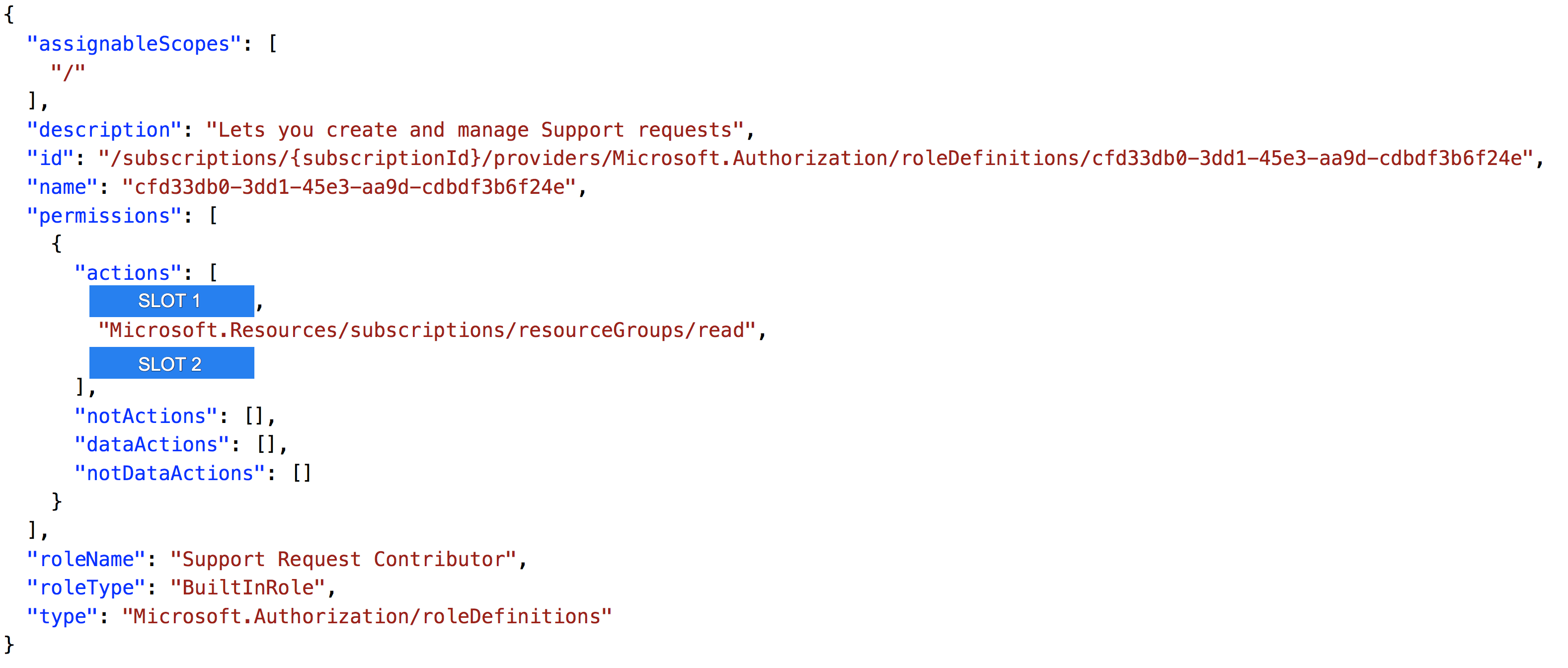
Which of the following would go into SLOT 1?
- A. "Microsoft.Authorization/*/*"
- B. "Microsoft.Authorization/*/read"
- C. " Microsoft.Authorization/read/*"
- D. “Microsoft.Authorization/*”
Explanation:
Answer - B
If you look at the Microsoft documentation for the role definition, you can see that the correct action is "Microsoft.Authorization/*/read".
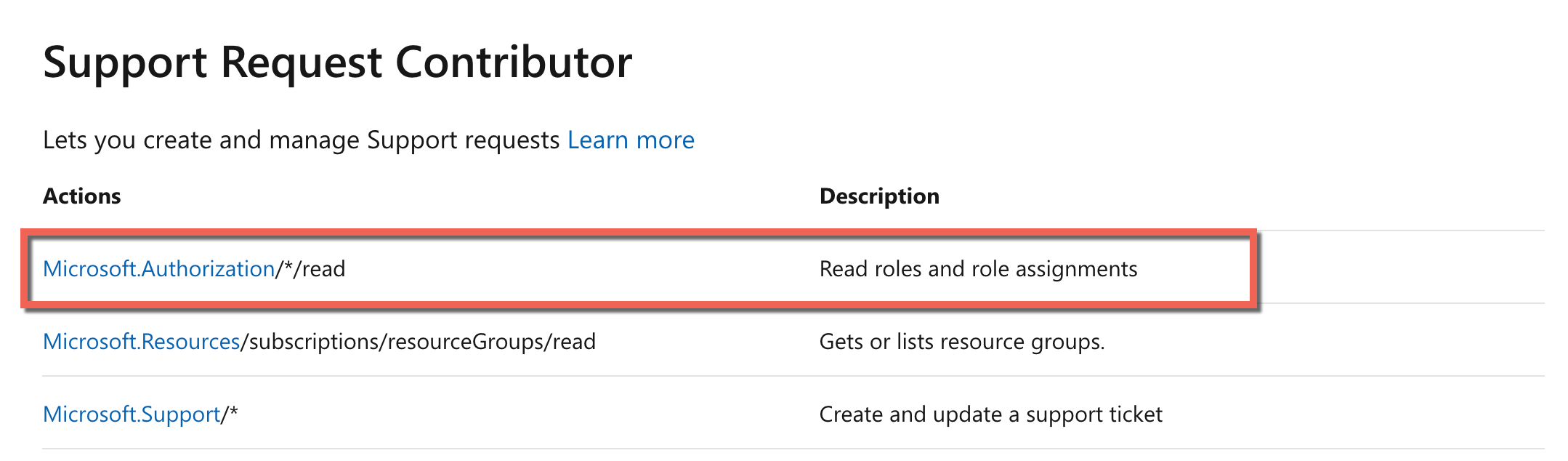
For more information on the built-in roles, please go to the below URL-
You work as an Azure Administrator for a company. You need to create a role based on the following requirements.
- View all the resources in the Azure subscription.
- Issue support requests to Microsoft.
- Use the principle of least privilege.
You have to complete the below JSON role definition.

Which of the following would go into SLOT 2?
- A. "*/*"
- B. "*/Microsoft.Support"
- C. "Microsoft.Support/*"
- D. “Microsoft.Support”
Explanation:
Answer – C
If you look at the Microsoft documentation for the role definition, you can see that the correct action is “Microsoft.Support/*”.
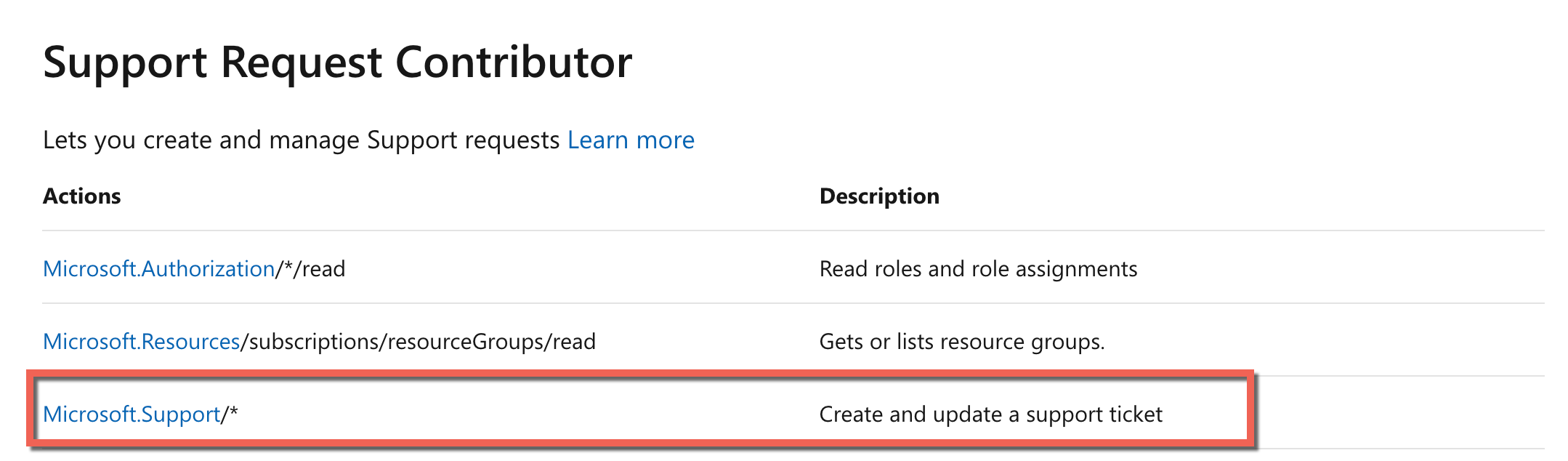
For more information on the built-in roles, please go to the below URL-
You have the Azure virtual networks shown in the following table.
|
Name |
Address space |
Subnet |
Resource Group-Region |
|
VNet1 |
10.11.0.0/16 |
10.11.0.0/17 |
West US |
|
VNet2 |
10.11.0.0/17 |
10.11.0.0/25 |
West US |
|
VNet3 |
10.10.0.0/22 |
10.10.0.0/24 |
East US |
|
VNet4 |
192.168.16.0/22 |
192.168.16.0/24 |
North Europe |
To which virtual networks can you establish a peering connection from VNet1?
- A. VNet2 and VNet3 only
- B. VNet2 only
- C. VNet3 and VNet4 only
- D. VNet2, VNet3, and VNet4
Explanation:
Answer – C
Since VNet2 has an overlapping CIDR block peering with VNet1 is not possible. Hence peering is possible from VNet1 to VNet3 and VNet1 to VNet4. Below is the error that we get while configuring VNet2.
For more information on Virtual Network peering, please visit the below URL-
Your company has an Azure account and a subscription. The subscription contains the virtual networks in the following table.
|
Name |
Address Space |
Subnet name |
Subnet address range |
|
VNet1 |
10.1.0.0/16 |
Subnet1 |
10.1.1.0/24 |
|
VNet2 |
10.10.0.0/16 |
Subnet2 |
10.10.1.0/24 |
|
VNet3 |
172.16.0.0/16 |
Subnet3 |
172.16.1.0/24 |
The subscription also contains the virtual machines in the following table.
|
Name |
Network |
Subnet |
IP address |
|
VM1 |
VNet1 |
Subnet1 |
10.1.1.4 |
|
VM2 |
VNet2 |
Subnet2 |
10.10.1.4 |
|
VM3 |
VNet3 |
Subnet3 |
172.16.1.4 |
The firewalls on all the virtual machines are configured to allow all ICMP traffic.
You add the peerings in the following table.
|
Virtual Network |
Peering Network |
|
VNet1 |
VNet3 |
|
VNet2 |
VNet3 |
|
VNet3 |
VNet1 |
For each of the following statements, select Yes if the statement is true.
Can VM1 ping to VM3?
- A. Yes
- B. No
Explanation:
Answer – A
VM1 can ping VM3 because peering between vnet1 and vnet3 has been established.
Peering is always bidirectional and ping also requires bidirectional connectivity.
It is clear that A is the correct answer.
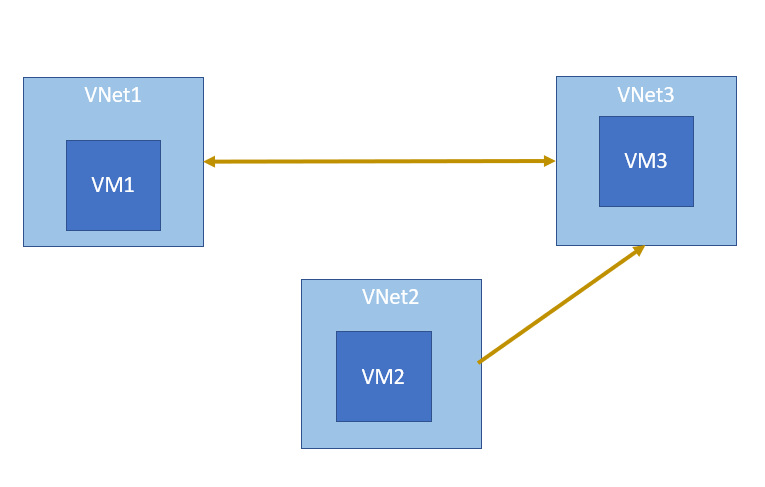
For more information on VNET peering, please visit the below URL-
Your company has an Azure account and a subscription. The subscription contains the virtual networks in the following table.
|
Name |
Address Space |
Subnet name |
Subnet address range |
|
VNet1 |
10.1.0.0/16 |
Subnet1 |
10.1.1.0/24 |
|
VNet2 |
10.10.0.0/16 |
Subnet2 |
10.10.1.0/24 |
|
VNet3 |
172.16.0.0/16 |
Subnet3 |
172.16.1.0/24 |
The subscription also contains the virtual machines in the following table.
|
Name |
Network |
Subnet |
IP address |
|
VM1 |
VNet1 |
Subnet1 |
10.1.1.4 |
|
VM2 |
VNet2 |
Subnet2 |
10.10.1.4 |
|
VM3 |
VNet3 |
Subnet3 |
172.16.1.4 |
The firewalls on all the virtual machines are configured to allow all ICMP traffic.
You add the peerings in the following table.
|
Virtual Network |
Peering Network |
|
VNet1 |
VNet3 |
|
VNet2 |
VNet3 |
|
VNet3 |
VNet1 |
For each of the following statements, select Yes if the statement is true.
Does VNet2(VM2) peer with VNet3(VM3)?
- A. Yes
- B. No
Explanation:
In this question, we are asked to decide whether the statement “Has VNet2(VM) peered with VNet3(VM3)” is true or not.
Answer — B (No)
Peering is always bidirectional. Peering in VNet2(VM2) and VNet3(VM3) is shown as unidirectional.
The main learning from this question is that the peering connection has two states - Initiated state ( as shown between VNet2 and VNet3 and the connected state. (as shown between VNet1 and VNet3. When the peering connection is in a connected state, it becomes bidirectional.
A bidirectional link must be created in order to establish a successful connection
Hence B is the correct answer 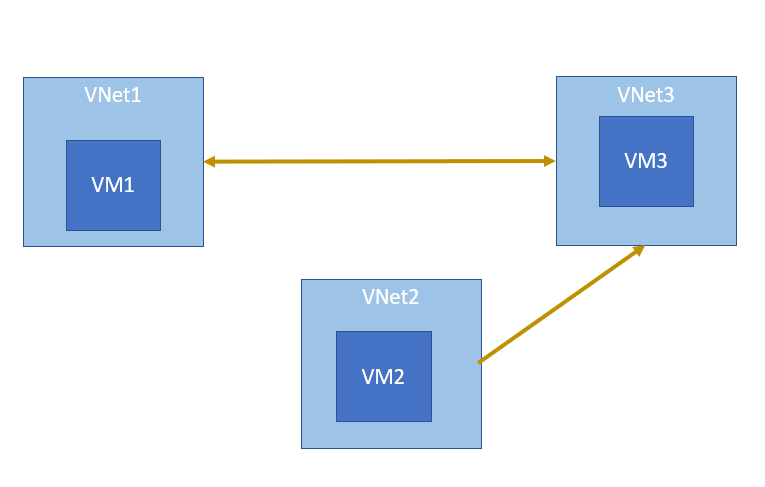
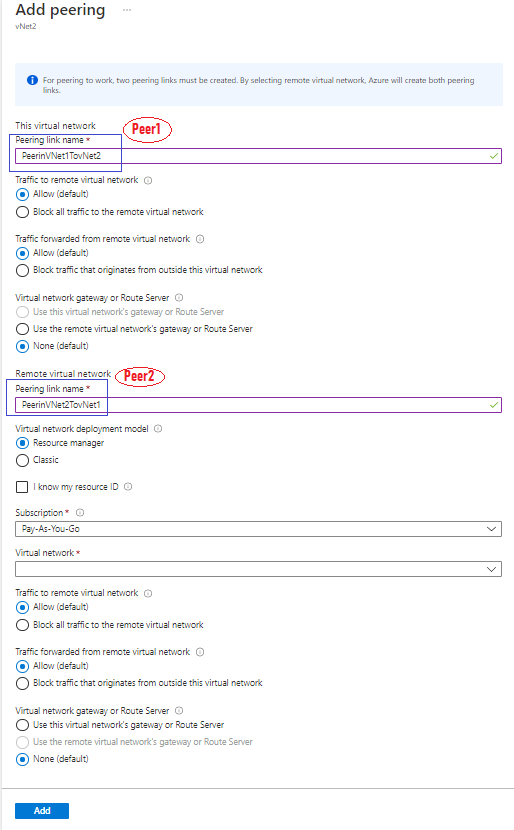
For better understanding create peering with PowerShell/CLI.
In the Azure portal, both peering have been created in a single UI.
For more information on VNET peering, please visit the below URL-
Your company has an Azure account and a subscription. The subscription contains the virtual networks in the following table.
|
Name |
Address Space |
Subnet name |
Subnet address range |
|
VNet1 |
10.1.0.0/16 |
Subnet1 |
10.1.1.0/24 |
|
VNet2 |
10.10.0.0/16 |
Subnet2 |
10.10.1.0/24 |
|
VNet3 |
172.16.0.0/16 |
Subnet3 |
172.16.1.0/24 |
The subscription also contains the virtual machines in the following table.
|
Name |
Network |
Subnet |
IP address |
|
VM1 |
VNet1 |
Subnet1 |
10.1.1.4 |
|
VM2 |
VNet2 |
Subnet2 |
10.10.1.4 |
|
VM3 |
VNet3 |
Subnet3 |
172.16.1.4 |
The firewalls on all the virtual machines are configured to allow all ICMP traffic.
You add the peerings in the following table.
|
Virtual Network |
Peering Network |
|
VNet1 |
VNet3 |
|
VNet2 |
VNet3 |
|
VNet3 |
VNet1 |
For each of the following statements, select Yes if the statement is true.
Has VM2 peered with VM1?
- A. Yes
- B. No
Explanation:
Answer — B
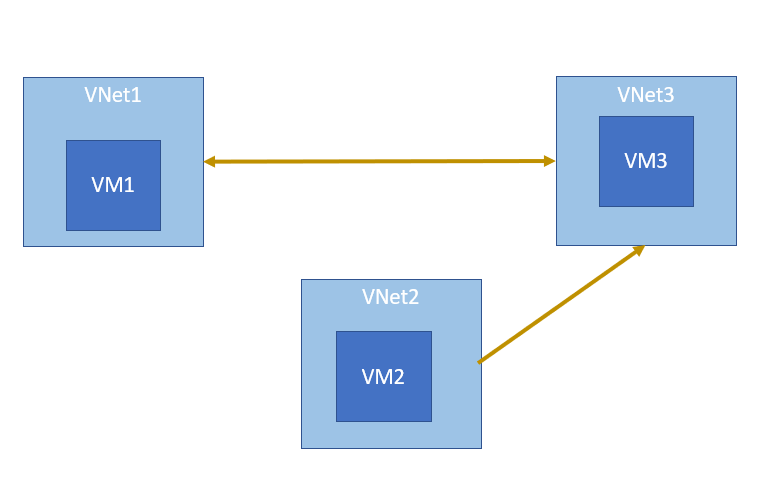
The following diagram represents peering establish between vnets. Diagram shows no peering between Vnet1 and Vnet2.
Ping require bidirectional connectivity. It is clear that VM1 and VM 2 can not ping each other.
In view of above, B is the correct answer and all other answers are wrong.
For more information on VNET peering, please visit the below URL-
A company has the following storage accounts in place as part of its Azure subscription.
|
Name |
Storage Account Type |
|
whizlabstore1 |
General Purpose V1 |
|
whizlabstore2 |
General Purpose V2 |
|
Whizlabstore3 |
Blob Storage |
Which of the following storage account/accounts could be used to store objects as part of the Archive tier?
- A. whizlabstore1 only
- B. whizlabstore2 only
- C. whizlabstore3 only
- D. whizlabstore1 and whizlabstore2 only
- E. whizlabstore1 and whizlabstore3 only
- F. whizlabstore2 and whizlabstore3 only
- G. All storage accounts
Explanation:
Answer - F
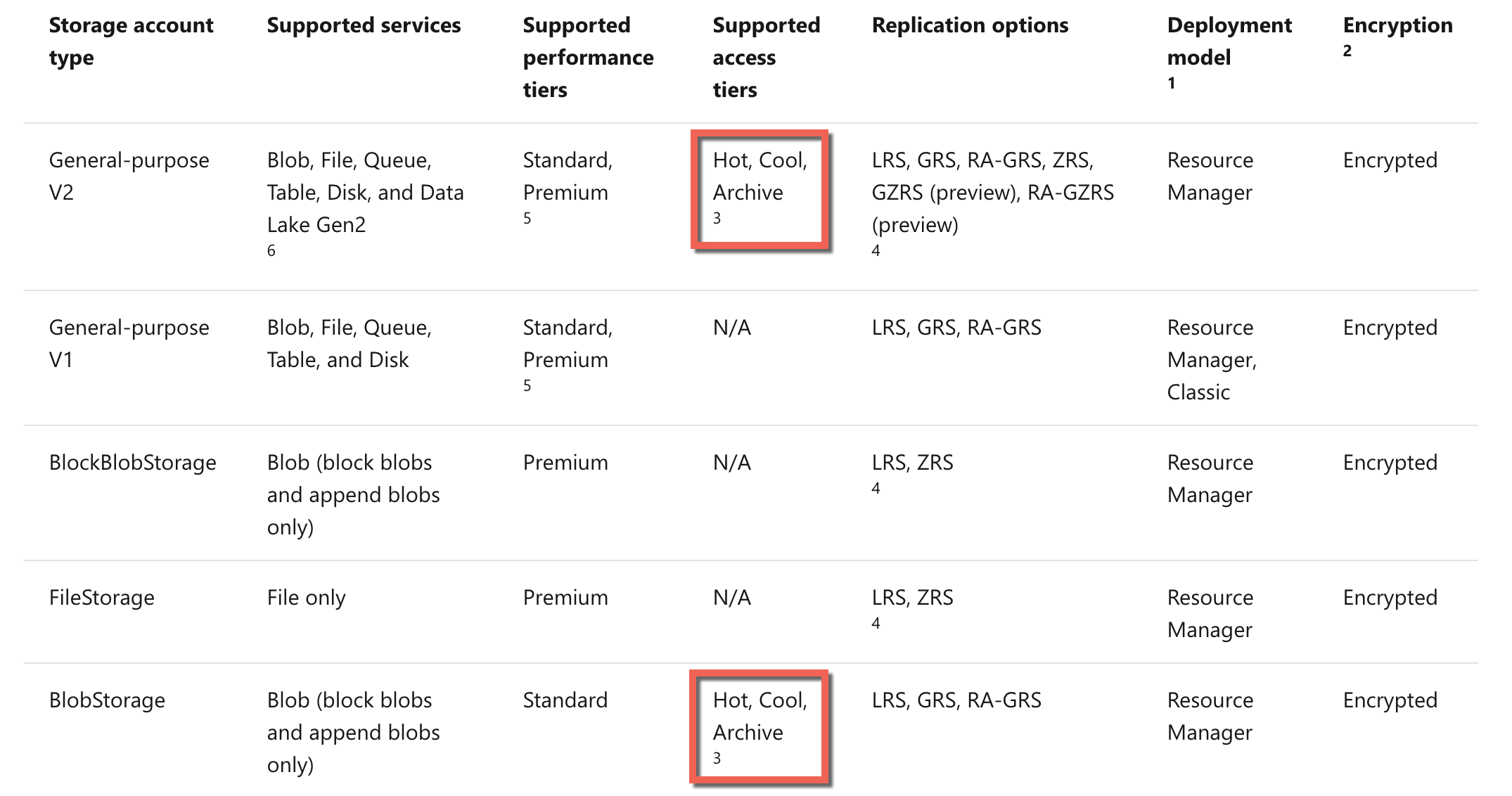
As per the Microsoft documentation given below, only the General Purpose V2 and Blob storage account types support the Archive access tier.
As a result, all other options are incorrect.
For more information on storage accounts, one can go to the following link-
A company needs to deploy the following architecture to Azure.
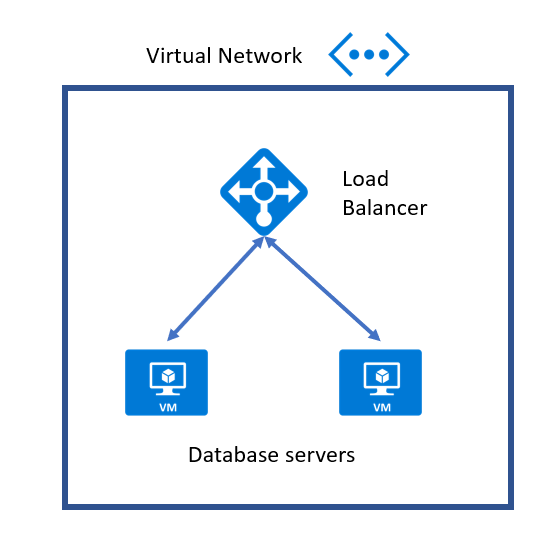
The architecture would consist of a load balancer that should only accept requests via private IP addresses. It should not flow via the internet. The load balancer would direct requests to database servers hosted on Virtual machines.
Which of the following load balancer type should be implemented for this architecture?
- A. Public Load balancer
- B. Multi-port balancer
- C. Internal Load balancer
- D. External Load balancer
Explanation:
Answer – C
Since we don’t want requests to flow via the Internet, we should create an internal load balancer. The Microsoft documentation mentions the following.
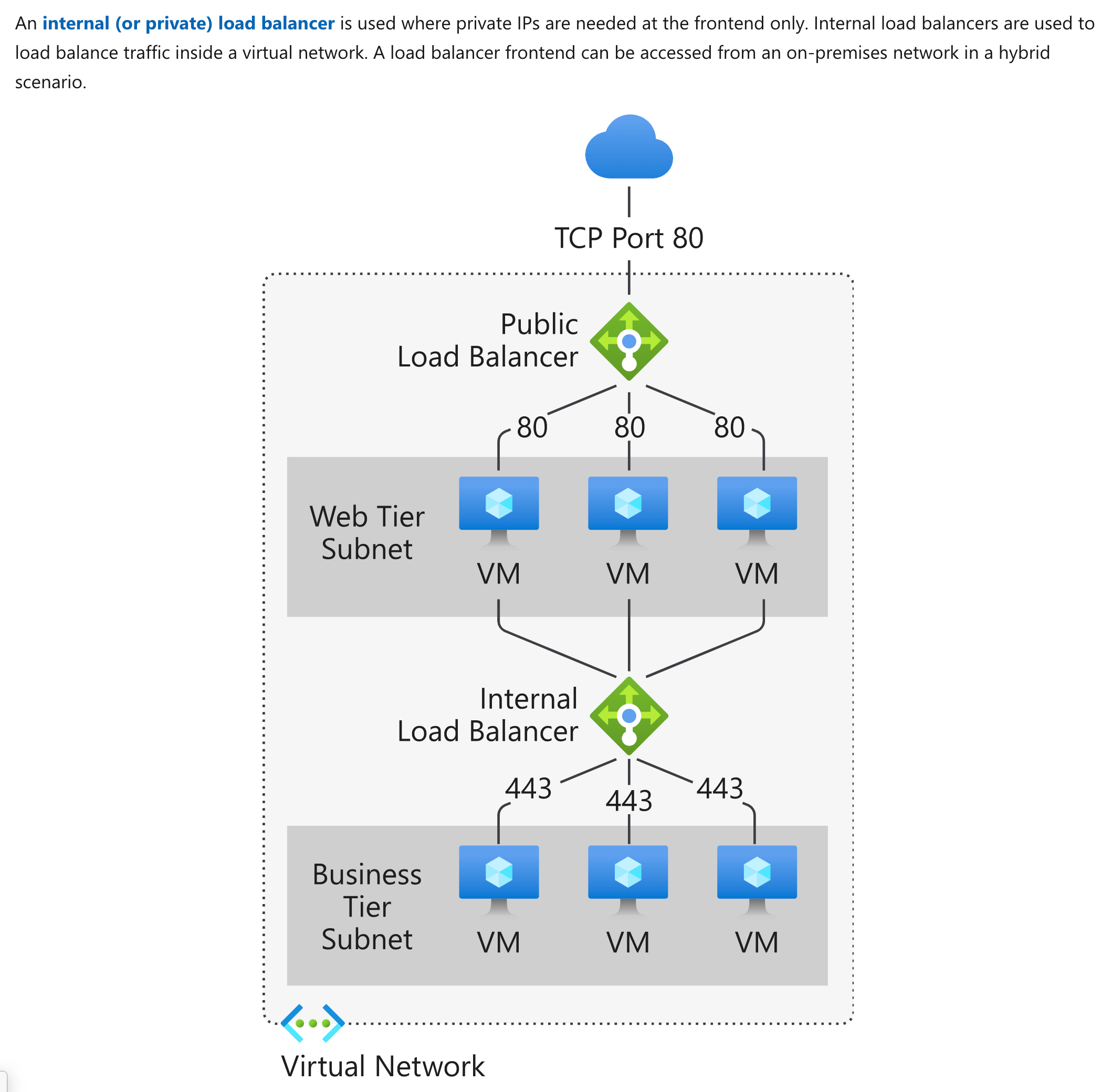
Option A is incorrect since this is created when requests need to flow via the Internet.
Options B and D are incorrect terms when it comes to the load balancer.
For more information on the Azure Load balancer, one can go to the following link-
Which of the following should be used to guarantee SLA of at least 99.5% for the availability of the Virtual Machines? Choose 2 answers from the options given below.
- A. Azure Managed Disks
- B. Azure Network Interfaces
- C. Azure Availability sets
- D. Azure scale sets
Explanation:
Answer – A and C
Managed Disks and Availability Sets can guarantee at least 99.5% of the Virtual Machines availability.
The Microsoft documentation mentions the following.
- For any Single Instance Virtual Machine using Standard SSD Managed Disks for Operating System Disk and Data Disks, we guarantee you will have Virtual Machine Connectivity of at least 99.5%.
- For all Virtual Machines with two or more instances deployed in the same Availability Set or the same Dedicated Host Group, we guarantee you will have Virtual Machine Connectivity to at least one instance 99.95% of the time.
Option B is incorrect. Having multiple network interfaces can be used to recover applications on virtual machines since you can move network interfaces across virtual machines. But then here to ensure that you are guaranteed an SLA of 99.5% uptime, you should use Azure Managed Disks and/or Azure Availability Sets.
Option D is incorrect since this can be used to scale your application and can be used for high availability.
For more information on managing availability for Virtual Machines, one can go to the below URLs-
Which of the following storage account type should be used for Azure storage?
- A. Blob storage
- B. General Purpose v1
- C. General Purpose v2
- D. Table storage
Explanation:
Answer – C
Option C is correct: The question has the key requirement, “Storage replication needs to be in place to ensure that data is available even in the case of a data center failure”. This means that you need to use Zone redundant replication, which is available in General Purpose v2. Standard storage account type for blobs, file shares, queues, and tables. Recommended for most scenarios using Azure Storage.
Option A is incorrect: Azure Blob storage is Microsoft's object storage solution for the cloud. Blob storage is optimized for storing massive amounts of unstructured data.
Option B is incorrect: General-purpose v1 is a legacy storage account type. These account types aren’t recommended by Microsoft. It may not have the latest features or the lowest per-gigabyte pricing.
Option D is incorrect: Azure Table storage is a service that stores structured NoSQL data in the cloud, providing a key/attribute store with a schemaless design.
Types of storage accounts
Azure Storage offers several types of storage accounts. Each type supports different features and has its own pricing model.
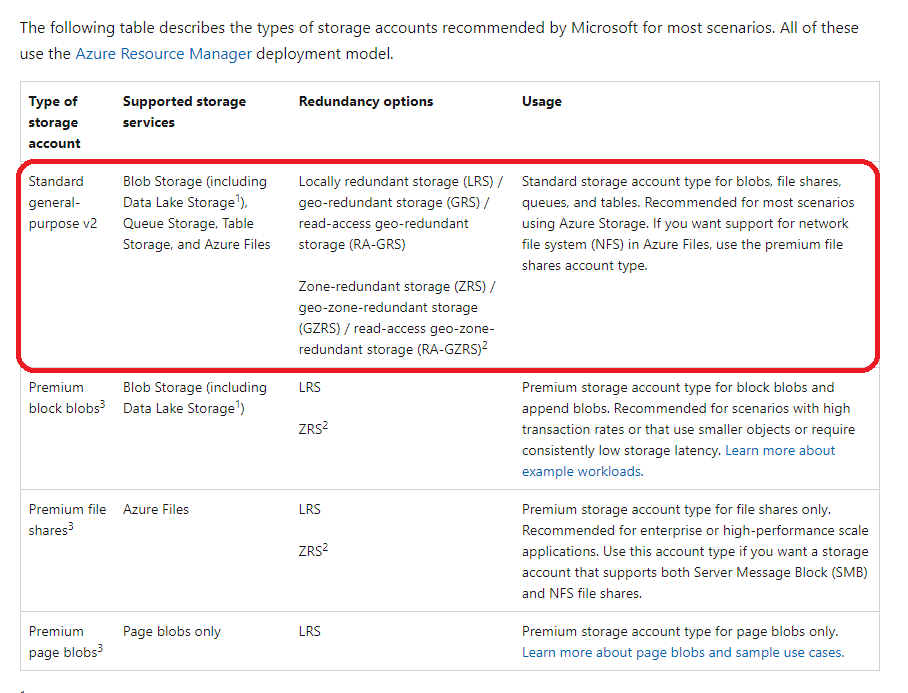
For more information on storage accounts, one can go to the below URL-
How many availability sets would you create for the deployment of the web and database virtual machines onto Azure?
- A. 1
- B. 2
- C. 4
- D. 10
Explanation:
Answer – B
You should ideally create availability sets based on the number of tiers you have for your application.
All other options are invalid.
For more information on availability sets, one can go to the below URL-
When adding custom domain names, which of the following record needs to be added to your custom domain registrar?
- A. A record
- B. NS record
- C. TXT record
- D. PTR record
Explanation:
Answer – C
When you add a custom domain name in Azure AD, below is an example of what you would need to add to your domain registrar to complete the registration of the custom domain.
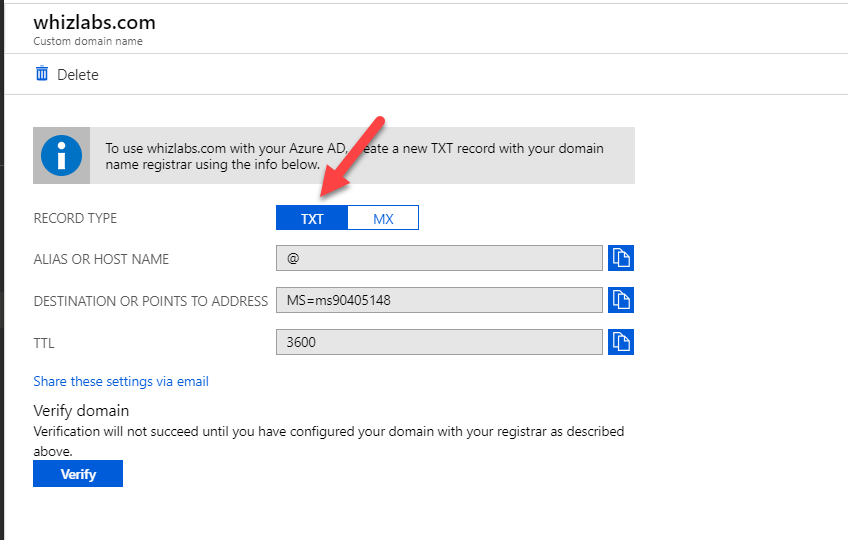
Since this is clearly shown, all other options are invalid.
For more information on custom domain names in Azure, one can go to the below URL-
Which of the following rule would you apply to the Network Security Group for the Network interface attached to the Web server?
- A. An inbound rule allowing traffic on port 80
- B. An inbound rule allowing traffic on port 443
- C. An outbound rule allowing traffic on port 80
- D. An outbound rule allowing traffic on port 443
Explanation:
Answer – B
Since the users will connect via HTTPS, that means that port 443 should be open. And we need to add an Inbound security rule. An example is shown below.
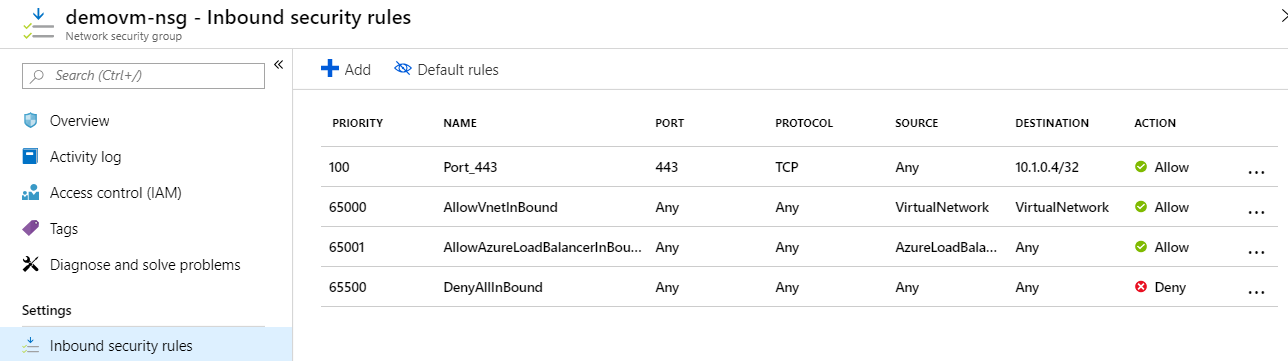
Option A is incorrect since this is the port for HTTP traffic.
Options C and D are incorrect since you need to modify the Inbound security rule.
For more information on security groups, one can go to the below URL-
A team member has created a point-to-site VPN connection between a computer named “WorkstationA” and an Azure Virtual Network. Another point-to-site VPN connection needs to be created between the same Azure Virtual Network and a computer named “WorkstationB”. The VPN client package was generated and installed on “WorkstationB”. You need to ensure that you can create a successful point-to-site VPN connection.
You decide to export the “WorkstationA” client certificate in the form of .pfx file and install it on "Workstation B".
Would this solution fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
To have a successful point-to-site VPN connection, you need to install the exported client certificate to "WorkstationB".
For more information on point-to-site VPN, please visit the below URL-
You provide custom Azure services for your customers. They need to access the services from their own virtual networks in a secure manner avoiding any internet connections. What are the four components that you and your customers need to set up to utilize Azure custom services?
- Correct Answers
Azure Load Balancer
Standard Load Balancer is secure by default and part of your virtual network. The virtual network is a private and isolated network
Private Link Service
Your service that is running behind Azure Standard Load Balancer can be enabled for Private Link access so that consumers to your service can access it privately from their own VNets
Private Link
Now you don't access the Azure resource using a public IP address. Instead, you use a private IP address that Azure assigns to the resource from the address space of your subnet
Private Endpoint
A private endpoint is a network interface that uses a private IP address from your virtual network. This network interface connects you privately and securely to a service that's powered by Azure Private Link
Explanation:
Correct answers:
|
Service Name |
Answer / Definition Area |
|
Azure Load Balancer |
Standard Load Balancer is secure by default and part of your virtual network. The virtual network is a private and isolated network. |
|
Private Link Service |
Your service that is running behind Azure Standard Load Balancer can be enabled for Private Link access so that consumers to your service can access it privately from their own VNets |
|
Private Link |
Now you don't access the Azure resource using a public IP address. Instead, you use a private IP address that Azure assigns to the resource from the address space of your subnet. |
|
Private Endpoint |
A private endpoint is a network interface that uses a private IP address from your virtual network. This network interface connects you privately and securely to a service that's powered by Azure Private Link. |
Azure Private Link helps users connect the Azure resources to their virtual networks without using the internet and public IPs. Instead of the internet, the customers use the Microsoft Azure backbone network. Instead of using public IP addresses for resource access, the resources are using the private IP addresses that Azure assigns to them using their virtual network’s subnets in the private link services.
For customers utilizing your Azure services from their virtual networks, you need to create an Azure Private Link. This link connects the Private Endpoint that customers add to their virtual network and the Private Link Service that you add to connect to your services running behind the Standard Azure Load Balancer.
For more information about Azure Load Balancer, Private Endpoint, Private Link, and Private Link Service, please visit the below URLs:
- https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-overview#securebydefault
- https://docs.microsoft.com/en-us/learn/modules/introduction-azure-private-link/3-how-azure-private-link-works
- https://docs.microsoft.com/en-us/azure/private-link/private-link-service-overview
- https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-overview




