





| No. | Domain | Total Question | Correct | Incorrect | Unattempted | Marked for Review |
|---|---|---|---|---|---|---|
| 1 | Manage Azure identities and governance | 12 | 0 | 0 | 12 | 0 |
| 2 | Implement and manage storage | 4 | 0 | 0 | 4 | 0 |
| 3 | Deploy and manage Azure compute resources | 18 | 0 | 0 | 18 | 0 |
| 4 | Configure and manage virtual networking | 15 | 0 | 0 | 15 | 0 |
| 5 | Monitor and back up Azure resources | 6 | 0 | 0 | 6 | 0 |
| Total | All Domains | 55 | 0 | 0 | 55 | 0 |
Company WhizLabs has 2 Azure subscriptions named “Staging” and “Production”.
The “Staging” subscription has the following resource groups.
|
Name |
Region |
Lock type |
|
rg-staging-1 |
West Europe |
None |
|
rg-staging-2 |
West Europe |
Read Only |
The company has deployed a web application app-whizlabsweb with the ASP-whizlabsrg1-ba8c App Service plan to the rg-staging-1 resource group.
The “Production” subscription has the following resource groups.
|
Name |
Region |
Lock type |
|
rg-production-3 |
East Asia |
Delete |
|
rg-production-4 |
Central US |
None |
Would you be able to move app-whizlabsweb to the rg-staging-2 resource group?
- A. Yes
- B. No
Explanation:
Answer – B
Since rg-staging-2 has Read Only lock defined. Read lock means that user can not make any changes/updates in the resource group. Read lock is same as applying reader role on the Resource group. Reader role allow only */Read operation, excluding move operation.
Hence B is the correct answer. For details please, see the following link.
Azure built-in roles - Azure RBAC | Microsoft Docs
Lock resources to prevent changes - Azure Resource Manager | Microsoft Docs
Company WhizLabs has 2 Azure subscriptions named “Staging” and “Production”.
The “Staging” subscription has the following resource groups.
|
Name |
Region |
Lock type |
|
rg-staging-1 |
West Europe |
None |
|
rg-staging-2 |
West Europe |
Read-only |
The company has deployed a storage account stwhizlabs to the rg-staging-1 resource group.
The “Production” subscription has the following resource groups.
|
Name |
Region |
Lock type |
|
rg-production-3 |
East Asia |
Delete |
|
rg-production-4 |
Central US |
None |
Would you be able to move stwhizlabs resource to the rg-production-3 resource group?
- A. Yes
- B. No
Explanation:
Correct Answer — A
We can move resources from one resource group to another, and in this case the source resource group does not have any lock defined and receiving resource group has got delete lock, which stops from deleting of resources. Below is the further explanation of what delete lock does.
Delete lock on a resource group means that any resource which is contained by a resource group cannot be deleted. The idea behind delete lock is to avoid any resource deletion even by mistake. A resource group can be deleted by a user by mistake, in case, there is no lock on the resource group. A malicious user can also delete a group, without delete lock. This can cause serious problem in production system, and may even impact the end user.
Delete lock puts no other restrictions. Resources can always be added to a resource group with delete lock.
From this explanation it is clear that A (yes) is the correct answer, all other answers are wrong.
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/move-resource-group-and-subscription
Note - below screenshots are added for reference purposes.
Company WhizLabs has 2 Azure subscriptions named “Staging” and “Production.”
The “Staging” subscription has the following resource groups.
|
Name |
Region |
Lock type |
| rg-staging-1 |
West Europe |
None |
| rg-staging-2 |
West Europe |
Read-only |
The company has deployed a web application (app-whizlabsweb) within the App Service plan (ASP-whizlabsrg1-ba8c) to the resource group (rg-staging-1).
The “Production” subscription has the following resource groups.
|
Name |
Region |
Lock type |
|
rg-production-3 |
East Asia |
Delete |
|
rg-production-4 |
Central US |
None |
Also, the company provisioned a web application (app-prod-web) in the resource group (rg-production-4).
Would you be able to move App Service resources from rg-staging-1 to the rg-production-4 resource group?
- A. Yes
- B. No
Explanation:
Answer — B
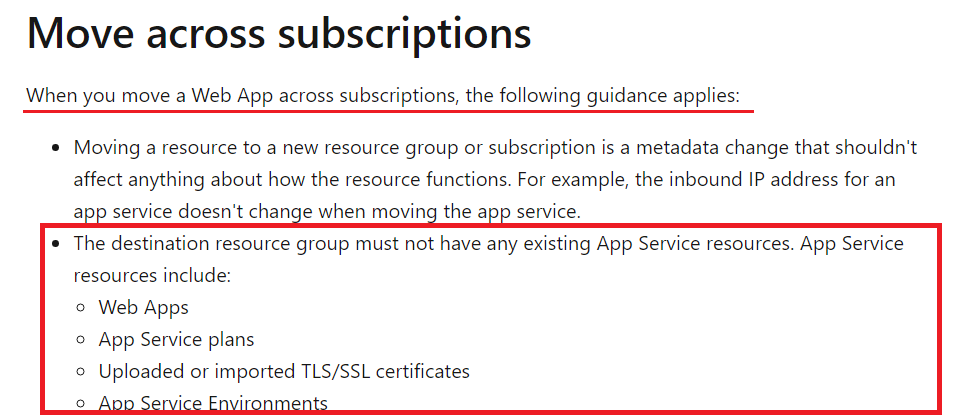
Moving a resource from one Resource Group results in metadata changes, and it does not have any effect on resources. Both rg-staging-1 & rg-production-4 do not have any locks. But, we still cannot move App Service resources from resource group"rg-staging-1" to the target resource group "rg-production-4" because it already contains web resources.
The destination resource group must not have any existing App Service resources. App Service resources include Web Apps, App Service plans, etc.
Here, rg-staging-1 --> has web application (app-whizlabsweb) with the App Service plan (ASP-whizlabsrg1-ba8c), and the target resource group (rg-production-4) ---> has a web application (app-prod-web).
As per Microsoft Documentation, Web resources in the destination group violate the rules for moving App Service resources from one subscription to another.
It is clear that B is the correct answer and A is the wrong answer.
For more details, please see the following:
For more information on resource locks, please visit the following URL-
A company has an Azure subscription named whizlabstaging. They also have a resource group named whizlabs-rg. The resource group has an internal load balancer named “whizlab-internal” and a public load balancer named “whizlab-public”. They want to give a user named “whizlabusr” permissions to configure both load balancers. The solution must follow the principle of least privilege.
Which role would you assign to the user to allow the addition of a backend pool to the load balancer “whizlab-internal”?
- A. Contributor role on whizlab-internal
- B. Network Contributor role on whizlab-internal
- C. Network Contributor role on whizlabs-rg
- D. Owner role on whizlab-internal
Explanation:
Answer – C
To provide the ability to add the backend pool, "whizlabusr" must have the read access to the details of the virtual machine and the virtual network. For this reason, the user should be assigned a Network Contributor role within the resource group. In this role, "whizlabusr" will have the read access to the VM and full access to the group's network resources.
The other options are all invalid since they would only provide access to the load balancer resource itself. They will not provide access to the other resources such as the virtual machines that needed to be added to the back-end pool.
For more information on Role-based access control, please visit the following URL-
A company has an Azure subscription named whizlabstaging. They also have a resource group named whizlabs-rg. The resource group has an internal load balancer named “whizlab-internal” and a public load balancer named “whizlab-public”. They want to give a user named “whizlabusr” permissions to configure both load balancers. The solution must follow the principle of least privilege.
Which role would you assign to the user to allow a health probe to the load balancer “whizlab-public”?
- A. Contributor role on whizlab-internal
- B. Network Contributor role on whizlab-internal
- C. Network Contributor role on whizlabs-rg
- D. Owner role on whizlab-internal
Explanation:
Correct Answer – C
An Azure public load balancer is a load balancer that has been assigned a public IP and can be accessed from the internet. While a private or internal load balance has a private IP and cannot be accessed from outside the vnet.
Options A & D are incorrect because there provide a lot more access than required
Option B is incorrect because it does not provide access to a public load balancer
Option C is correct because it will provide access to both public and private load balancers at whizlabs-rg resource group level. It also follows the principle of the least privileges.
For more information on Role-based access control, please visit the following URL:
Your company has an Azure AD tenant named whizlabs.com.
The following users are defined in the tenant.
|
Name |
Role |
|
whizlabusr1 |
Cloud device administrator |
|
whizlabusr2 |
User administrator |
The tenant also consists of the following Windows 10 devices.
|
Name |
Join type |
|
whizlabvm1 |
Azure AD registered |
|
whizlabvm2 |
Azure AD joined |
The tenant also has the following groups defined.
|
Name |
Join Type |
Owner |
|
whizlabgrp1 |
Assigned |
whizlabusr1 |
|
whizlabgrp2 |
Dynamic Device |
whizlabusr2 |
Would the user whizlabusr1 be able to add the device whizlabvm2 to the group whizlabgrp1?
- A. Yes
- B. No
Explanation:
Answer – A
Since whizlabusr1 user has the role of Cloud Device Administrator and is a Group Owner, the user would be able to add registered or joined devices to the group.
The Microsoft documentation provides the following information about Cloud Device Administrator.

For more information about the Cloud Device Administrator role and on working with group administrators, please visit the following URL-
Your company has an Azure AD tenant named whizlabs.com.
The following users are defined in the tenant.
|
Name |
Role |
|
whizlabusr1 |
Cloud device administrator |
|
whizlabusr2 |
User administrator |
The tenant also consists of the following Windows 10 devices.
|
Name |
Join type |
|
whizlabvm1 |
Azure AD registered |
|
whizlabvm2 |
Azure AD joined |
The tenant also has the following groups defined.
|
Name |
Join Type |
Owner |
|
whizlabgrp1 |
Assigned |
whizlabusr1 |
|
whizlabgrp2 |
Dynamic Device |
whizlabusr2 |
Would the user whizlabusr2 be able to add the device whizlabvm1 to the group whizlabgrp1?
- A. Yes
- B. No
Explanation:
Answer – A
Since whizlabusr2 holds the role of "User Administrator" he/she can update the membership of any assigned group, regardless of whether they are owner of the group or not because of the role associated with. He/She can add users, devices, to any assigned group in Azure AD.
Reference:
Your company has an Azure AD tenant named whizlabs.com.
The following users are defined in the tenant.
|
Name |
Role |
|
whizlabusr1 |
Cloud device administrator |
|
whizlabusr2 |
User administrator |
The tenant also consists of the following Windows 10 devices.
|
Name |
Join type |
|
whizlabvm1 |
Azure AD registered |
|
whizlabvm2 |
Azure AD joined |
The tenant also has the following groups defined.
|
Name |
Join Type |
Owner |
|
whizlabgrp1 |
Assigned |
whizlabusr1 |
|
whizlabgrp2 |
Dynamic Device |
whizlabusr2 |
Would the user whizlabusr2 be able to add the device whizlabvm2 to the group whizlabgrp2?
- A. Yes
- B. No
Explanation:
Answer – B
Since the group is Dynamic in nature, you won’t be able to add users or devices to a group manually. Device whizlabvm2 shall be governed by Rules and automatically removed or added dynamically.
Reference: How to manage groups - Azure Active Directory - Microsoft Entra | Microsoft Learn
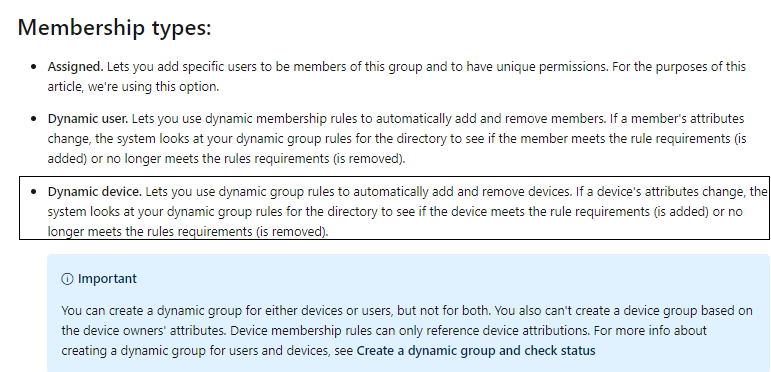
The device WhizlabVM2 is already "Azure AD joined". Hence WhizlabVM2 will be governed by AD rule
For example, you have a Dynamic Group, as defined below.
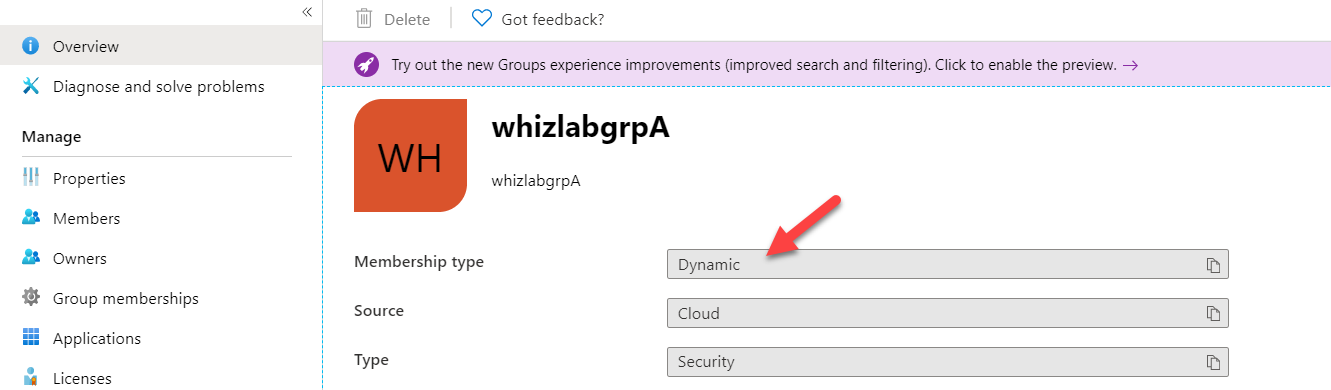
The ability to Add members will be greyed out.
For more information on creating Dynamic groups, please visit the following URL-
A company has deployed the following Azure Load Balancer resources to their Azure subscription
|
Name |
SKU |
|
whizlabload1 |
Basic |
|
whizlabload2 |
Standard |
Each load balancer would have to load balance requests across three virtual machines.
You want to ensure that whizlabload1 can load balance requests across the three virtual machines.
Which of the following has to be implemented?
- A. Ensure the virtual machines are created in the different regions.
- B. Ensure the virtual machines are created in the same resource group.
- C. Ensure the virtual machines are created in the same virtual network.
- D. Ensure the virtual machines are created in the same availability set or virtual machine scale set.
Explanation:
Answer – D
You look at the comparison between the Standard and the Basic Load Balancer in the Microsoft documentation. It clearly mentions that the virtual machines need to be part of an availability set or a virtual machine scale set.
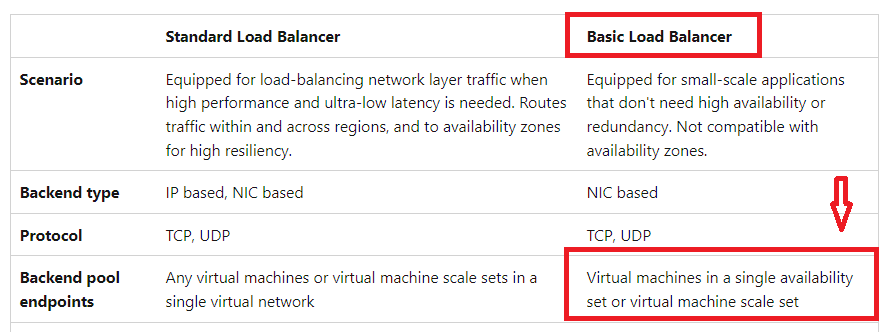
Since this is clearly mentioned in the documentation, all other options are incorrect.
For more information on the Azure Load Balancer, please visit the following URL-
- What is Azure Load Balancer? - Azure Load Balancer | Microsoft Learn
- Azure Load Balancer SKUs | Microsoft Learn
A company has deployed the following Azure Load Balancer resources to their Azure subscription.
|
Name |
SKU |
|
whizlabload1 |
Basic |
|
whizlabload2 |
Standard |
Each load balancer would have to load balance requests across three virtual machines.
You want to ensure that whizlabload2 can load balance requests across the three virtual machines.
Which of the following has to be implemented?
- A. Ensure the virtual machines are running the same operating system.
- B. Ensure the virtual machines are created in the same resource group.
- C. Ensure the virtual machines are created in the same virtual network.
- D. Ensure the virtual machines are created in the same availability set or virtual machine scale set.
Explanation:
Answer – C
You look at the comparison between the Standard and the Basic Load Balancer in the Microsoft documentation. It clearly mentions that the virtual machines need to be part of a single virtual network.
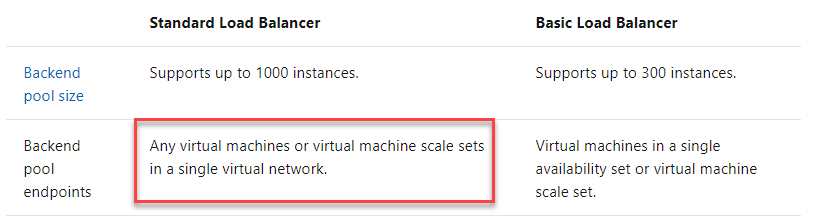
Since this is clearly mentioned in the documentation, all other options are incorrect.
For more information on the Azure Load Balancer, please visit the following URL-
A company is planning to deploy a set of virtual machines across the different system tiers, as mentioned below.
|
Tier |
Accessible from the Internet |
Number of virtual machines |
|
Web servers |
Yes |
5 |
|
Business Logic |
No |
50 |
|
Microsoft SQL Database servers |
No |
5 |
The following requirements need to be met.
- Incoming requests to the Business Logic tier from the web servers need to be spread equally across the virtual machines.
- All web servers need to be protected from SQL injection attacks.
Which of the following would you implement for the below requirement?
“Incoming requests to the Business Logic tier from the web servers need to be spread equally across the virtual machines.”
- A. An application gateway that uses the Standard tier
- B. An application gateway that uses the WAF tier
- C. A network security group
- D. An Internal Load Balancer
- E. A Public Load Balancer
Explanation:
Answer – D
3 tier architecture shown below will help us to answer question number 11 and 12 .
In Question 11, the Business Logic Tier has the requirement of NOT being accessible from the Internet. Hence, we should spin up an Internal Load Balancer with privat IP.
Hence the correct answer is D and all other answer and All other answers are wrong. Please see the diagram below for better clearance.
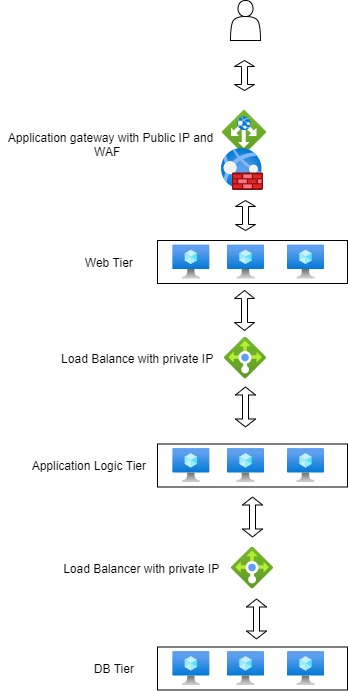
For more information on the Azure Load Balancer, please visit the following URL-
A company is planning to deploy a set of virtual machines across the different system tiers as mentioned below.
|
Tier |
Accessible from the Internet |
Number of virtual machines |
|
Web servers |
Yes |
5 |
|
Business Logic |
No |
50 |
|
Microsoft SQL Database servers |
No |
5 |
The company intends to meet the following requirements:
- Incoming requests to the Business Logic tier from the web servers need to be spread equally across the virtual machines.
- All web servers need to be protected from SQL injection attacks.
Which of the following solution would you implement for the below requirement?
“All web servers need to be protected from SQL injection attacks.”
- A. An application gateway that uses the Standard tier
- B. An application gateway with WAF
- C. A network security group
- D. An Internal Load Balancer
- E. A Public Load Balancer
Explanation:
Answer - B
To protect the web servers against SQL injection attacks, one can use the Web Application Firewall feature, as shown in the solution diagram below. Application gateway has the option to provide a WAF firewall. It is clear that B is the correct answer and all other answers are wrong.

The Microsoft documentation mentions the following.
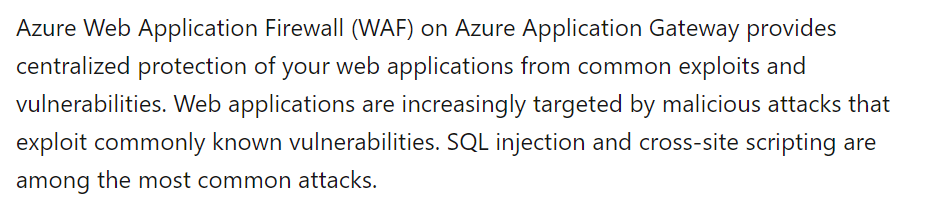
Since this is clearly mentioned in the documentation, all other options are incorrect.
For more information on the Web Application Firewall, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.

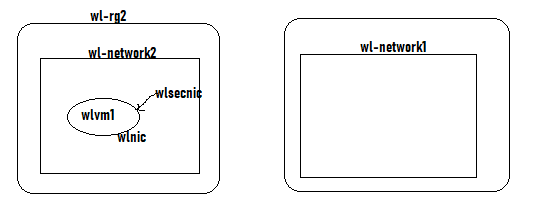
The virtual machine wlvm1 is part of a virtual network named wl-network2. The virtual machine has a network interface named wlnic attached to it. You need to create a new network interface named wlsecnic and later attached it to the virtual machine.
You decide to create wlsecnic in the wl-rg2 resource group and the West US region.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
In order to attach a network interface to a virtual machine, it must be created in the same region as the virtual machine. It also is a part of the same virtual network hosting the virtual machine.
Hence here, the requirements for ensuring the network interface can be attached to the virtual machine are met.
Below is an excerpt from the Microsoft documentation on the creation of a network interface.
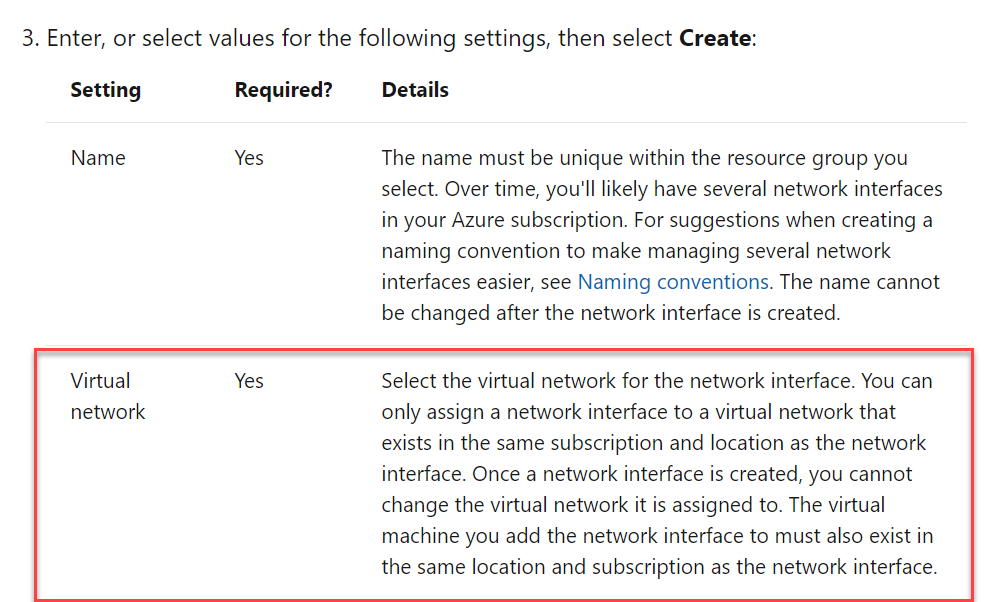
For more information on network interfaces, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.

The virtual machine wlvm1 is part of a virtual network named wl-network2. The virtual machine has a network interface named wlnic attached to it. You need to create a new network interface named wlsecnic and later attach it to the virtual machine.
You decide to create wlsecnic in the wl-rg1 resource group and the West US region.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Requirement: Can we create a resource in a resource group, when the region for the resource and resource group are different
Answer: A — Yes
First, we need to understand the difference between data and metadata. Metadata is not the actual data, but additional useful information about the data. A resource group contains metadata regarding azure resources, not the actual resources. A resource group contains the list of resources and some additional useful information like the region in which resources exist., components of each resource, etc… In view of this, a resource group and actual resources contained by the resource group can be in a different regions. The basic constraint here is that a VM and all its components should be in the same network and in the same region.
In the given scenario, we are asked to create a new network interface wlsecnic and attached it to wlvm1, which resides in wl-network2. Since all these resources are in the West US region, it is possible to do so although wl-rg2 is a separate region (West Europe)
Here it should be noted that it is a good practice to create a resource group and its resources, in the same region. Sometimes, data residency and compliance requirements will also force us to create both in the same region.
A company has the following resources defined as part of its Azure subscription.

The virtual machine wlvm1 is part of a virtual network named wl-network2. The virtual machine has a network interface named wlnic attached to it. You need to create a new network interface named wlsenic and later attach it to the virtual machine.
You decide to create wlsenic in the wl-rg2 resource group and in Central US region.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
In order to attach a network interface to a virtual machine, it must be created in the same region as the virtual machine. It also is a part of the same virtual network hosting the virtual machine.
Here the virtual machine is in the West US region and the network interface is being created in the Central US region.
For more information on network interfaces, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Location |
Resource group |
|
whizlab-rg1 |
Resource group |
West US |
Not applicable |
|
whizlab-rg2 |
Resource group |
West US |
Not applicable |
|
whizlabvault1 |
Recovery Services vault |
Central US |
whizlab-rg1 |
|
whizlabvault2 |
Recovery Services vault |
West US |
whizlab-rg2 |
|
whizlabvm1 |
Virtual machine |
Central US |
whizlab-rg2 |
|
whizlabstore1 |
Storage account |
West US |
whizlab-rg1 |
|
whizlabdb |
Azure SQL database |
East US |
whizlab-rg2 |
A blob container named “whizlabdata” and a file share named “whizlabfiledata” are created in the storage account whizlabstore1.
Which of the following resources can be backed up with the help of the recovery services vault whizlabvault1?
- A. whizlabvm1 only
- B. whizlabvm1 and whizlabfiledata only
- C. whizlabvm1 and whizlabdb only
- D. whizlabvm1, whizlabstore1 and whizlabdb.
- E. whizlabvm1, whizlabdata, whizlabfiledata and whizlabdb
Explanation:
Answer – A
Here the recovery services vault (whizlabvault1) is located in the Central US region. This means that only resources in this region can be backed up in the recovery services vault. And for this, we have only the virtual machine located in this region.

Since this is the only approach for backing up data in the recovery services vault, all other options are incorrect.
For more information on the recovery services vault, please visit the following URLs-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Location |
Resource group |
|
whizlab-rg1 |
Resource group |
West US |
Not applicable |
|
whizlab-rg2 |
Resource group |
West US |
Not applicable |
|
whizlabvault1 |
Recovery Services vault |
Central US |
whizlab-rg1 |
|
whizlabvault2 |
Recovery Services vault |
West US |
whizlab-rg2 |
|
whizlabvm1 |
Virtual machine |
Central US |
whizlab-rg2 |
|
whizlabstore1 |
Storage account |
West US |
whizlab-rg1 |
|
whizlabdb |
Azure SQL database |
East US |
whizlab-rg2 |
A blob container named “whizlabdata” and a file share named “whizlabfiledata” are created in the storage account whizlabstore1 .
Which of the following resources can be backed up with the help of the recovery services vault whizlabvault2?
- A. whizlabstore1 only
- B. whizlabfiledata only
- C. whizlabvm1 and whizlabfiledata only
- D. whizlabdata and whizlabfiledata only
- E. whizlabstore1 and whizlabdb only
Explanation:
Answer — B
In Azure recovery service vault (RSV), we can backup only those resources, which are in same region as of RSV region. In the current scenario the RSV (whizlabvault2) region is west us. Storage account whizlabstore1 is also in the same region. Whizlabstore1 have two resource — A blob container named “whizlabdata” and a file share named “whizlabfiledata”. Azure blob data cannot be backup in RSV (it requires a backup vault). In RSV, However, azure file share can be backup. There are no other resources in the same region other than these two.
It is clear that B is the correct answer and all other answers are wrong.
A company has an Azure AD directory that contains the following users.
|
Name |
Role |
|
whizlabusr1 |
None |
|
whizlabusr2 |
Global administrator |
|
whizlabusr3 |
Cloud device administrator |
|
whizlabusr4 |
Intune administrator |
The Azure AD Tenant has the following device settings.
- Users can join devices to Azure AD.
- Additional local administrators on Azure AD joined devices is set to None.
The user whizlabusr1 goes ahead and joins a Windows 10 computer to the Azure AD tenant.
You need to identify those users that would be added to the local Administrators group on the computer.
- A. whizlabusr1 only
- B. whizlabusr2 only
- C. whizlabusr1, whizlabusr2 and whizlabusr3 only
- D. whizlabusr1 and whizlabusr2 only
- E. whizlabusr1, whizlabusr2, whizlabusr3 and whizlabusr4
Explanation:
Correct Answer – D
When a device is joined to Azure AD, the user who joins the computer to the domain is added as the local administrator. Also, the Global Administrator will be added as an administrator to the system.
Hence D is the correct answer and all other answers are wrong.
This is also mentioned in the Microsoft documentation.
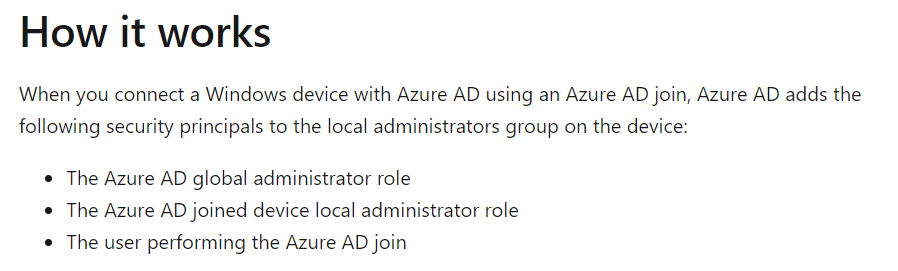
For more information on managing the local administrators in the Azure AD join process, please visit the following URL-
You need to increase the number of CPU cores and memory for running Azure Container Instance.
What steps do you take to carry out this task?
- A. Stop the ACI
- B. Redeploy ARM ACI deployment template
- C. In Azure portal, select the Scale up for ACI container
- D. Update Dockerfile
- E. Delete the ACI
Explanation:
Correct Answers: B and E
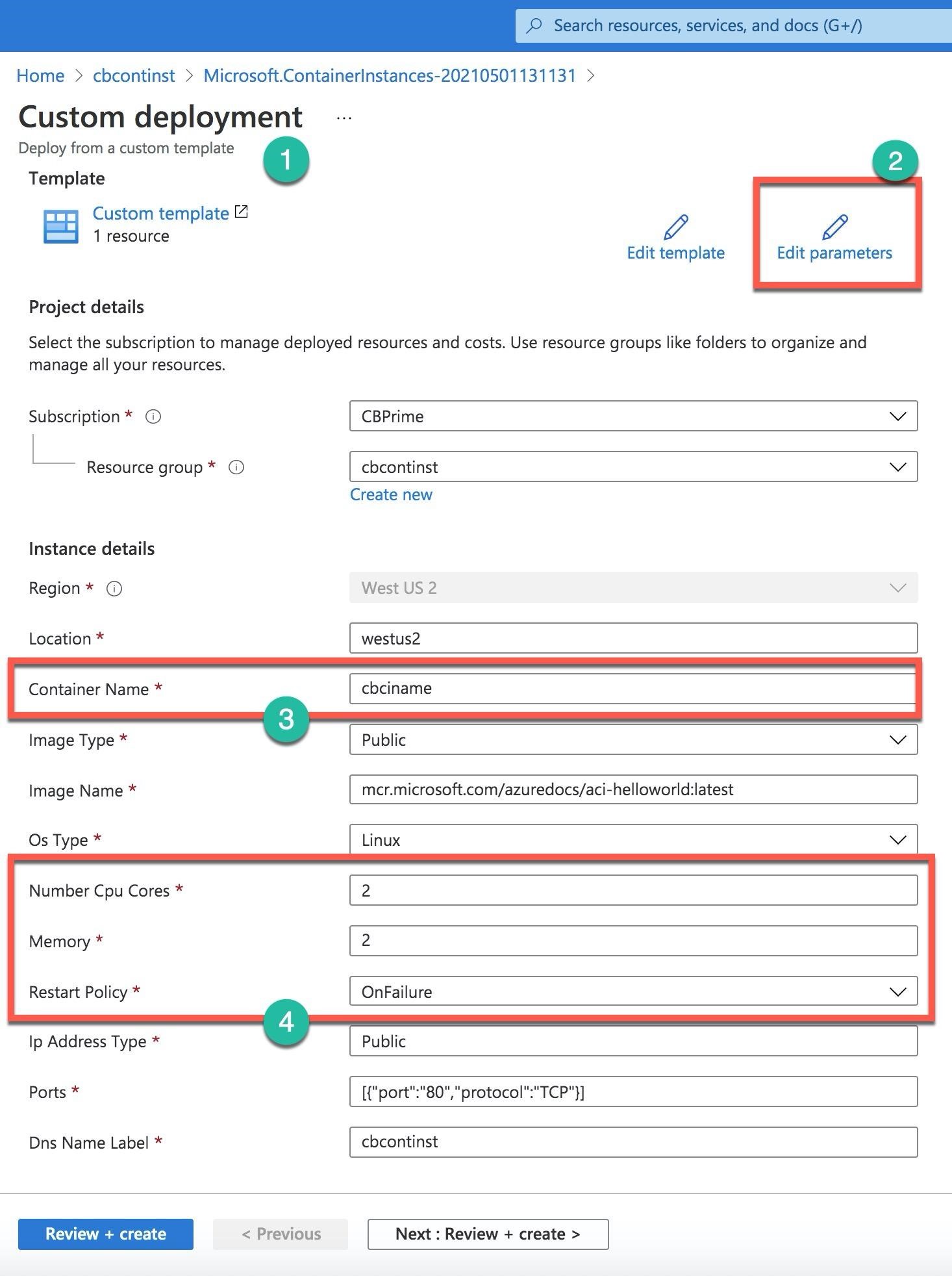
Unfortunately, Azure does not allow to scale Azure Container Instances. You need to delete the current ACI and create a new instance with the new resource requirements. The most convenient way is to reuse and run the ARM template from the previous ACI deployment. You can find the template under the Deployments section on the ACI’s resource group blade. When you select the deployment template and click on the Redeploy button on the top bar, the Azure portal opens the Custom deployment screen (Number 1). Here you click on the “Edit Parameters (Number 2) and can change the number of CPU cores, memory, restart policy, etc. (Number 4). If you have not deleted the previous ACI and keep the same name for the new instance (Number 3), you will get a deployment failed error when you click on the Create button after a review.
The error status message is the following.
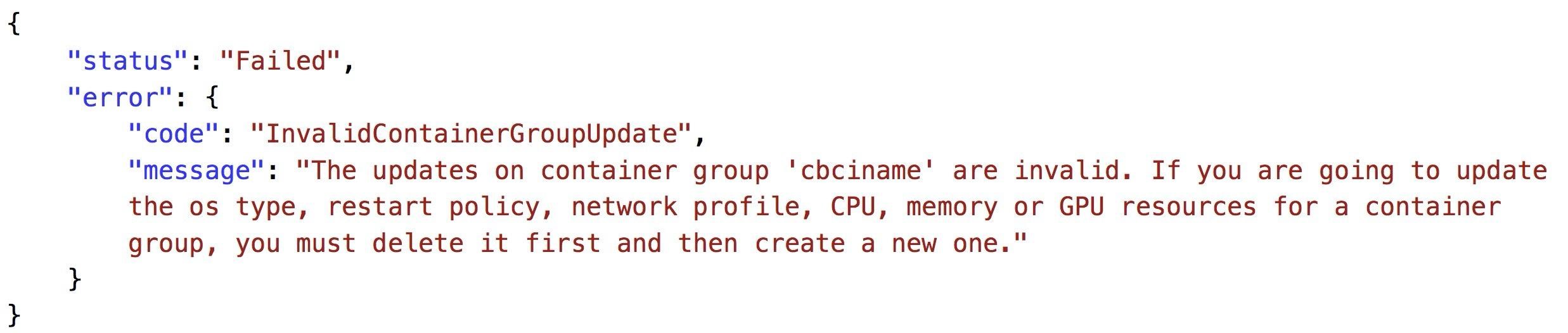
Therefore, you must delete the old ACI or change the name of the new ACI.
All other options are incorrect.
For more information about creating and updating the ACI using the ARM templates, please visit the below URLs:
You create an ACI multi-container group.
Please select all correct statements about the ACI group.
- A. ACI group is similar to the AKS node
- B. Containers in the ACI group share the same resources
- C. You can add new containers to the already running ACI group
- D. You can select different VM size for each container in a group
- E. ACI group can include the init containers
- F. You can create multi-container ACI groups on Linux only
Explanation:
Correct Answers: B, E and F
You can create the groups of the ACI containers. These ACI groups are similar to AKS pods. The group is a collection of containers that runs or schedules on the same host machine. It shares the host’s resources, local network, and storage volumes. You can deploy the multi-container group only on Linux using ARM templates, YAML scripts, or Docker Compose.
- Option B is correct because the containers in the ACI group share the same resources of the host machine. The containers share not only the same resources but also local network and storage volumes.
- Option E is correct because the ACI group can include the init containers. This container type prepares the run of your application. They set up accounts, databases, or running scripts. Only after the init containers finish their jobs the application containers start.
- Option F is correct because currently, you can create multi-container ACI groups on Linux only.
- Option A is incorrect because the ACI group is similar to the AKS pods but not to the AKS nodes.
- Option C is incorrect because you need to delete the old ACI group and create a new one with additional containers. Usually, you can deploy a multi-container group using ARM templates or YAML scripts. The Docker Compose can also be used.
- Option D is incorrect because the ACI multi-container group shares the same host machine, and you cannot dedicate any VMs to a particular container.
For more information about Azure Container Instance groups, please visit the below URLs:
You create an AKS cluster and need to attach the data volume accessible from the multiple pods simultaneously.
What type of storage should you use?
- A. Azure Standard Disks
- B. Azure Table
- C. Azure Files
- D. Azure Premium Disks
- E. Azure Blob
Explanation:
Correct Answer: C
Azure provides two types of storage for AKS: Azure Disks and Azure Files. If you need to have persistent storage for a pod, you should use the Azure Disks. For accessibility to the data from the multiple pods simultaneously, you need to use shared Azure Files.
Both Azure Disks and Azure Files come in Premium and Standard Options. The Premium option uses the high-performance SSDs, and the Standard — regular HDDs. You can provision both storage types as Static or Dynamic volumes.
Data volumes using Azure Files are mounted as SMB 3.0 shared drives.
When you define an application deployment manifest (deployment.yaml), you provide the storage type and additional information for storage access, like a storage secret (created based on Azure storage account and storage key), share name, and type of access (Number 1).
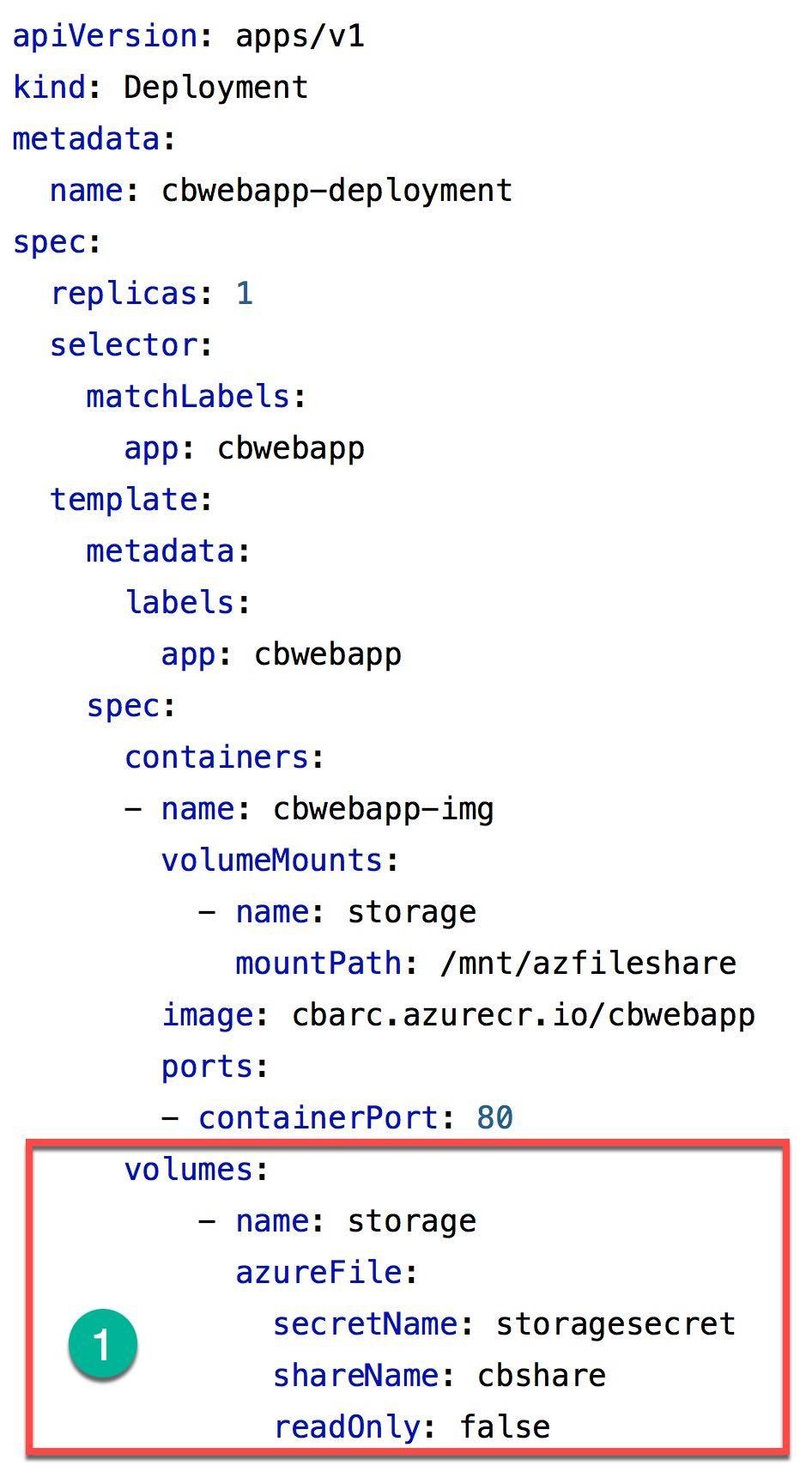
All other options are incorrect.
For more information about Azure storage options for AKS nodes and pods, please visit the below URL:
- https://docs.microsoft.com/en-us/azure/aks/concepts-storage
- https://docs.microsoft.com/en-us/azure/aks/operator-best-practices-storage
- https://docs.microsoft.com/en-us/azure/aks/azure-files-volume#create-an-azure-file-share
- https://docs.microsoft.com/en-us/learn/modules/aks-deploy-container-app/5-exercise-deploy-app
A company has an Azure subscription. They want to transfer around 6 TB of data to the subscription. They plan to use the Azure Import/Export service. Which of the following can they use as the destination for the imported data?
- A. Azure Data Lake Storage
- B. Azure SQL Database
- C. Azure File Sync Storage
- D. Azure Blob storage
Explanation:
Answer – D
When transferring a large amount of data to an Azure storage account, you can transfer data to Azure blob storage or Azure file storage.
The Microsoft documentation mentions the following.
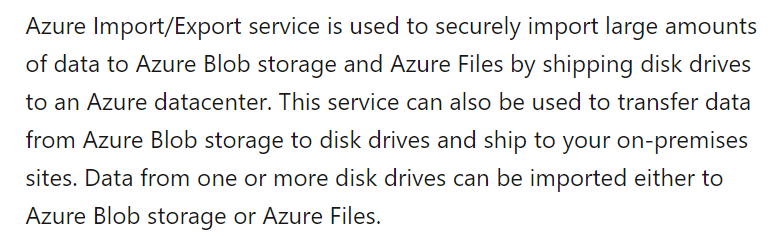
Since this is clear from the Microsoft documentation, all other options are incorrect.
For more information on the Import-Export service, please visit the following URL-
A company has an Azure AD tenant. They have users that are also synced with their on-premise environment. The domain contains the following users.
|
Name |
Role |
|
whizlabadmin1 |
Security administrator |
|
whizlabadmin2 |
Billing administrator |
|
whizlabusr |
Reports reader |
The administrator has enabled self-service password reset (SSPR) for all users.
The administrator has enabled the following SSPR settings.
- Number of methods required to reset – 2
- Methods available to users – Mobile phone and Security questions
- Number of questions to register – 3
- Number of questions to reset – 3
The following security questions are chosen.
- In what city was your first job?
- What was the name of the first school you attended?
- What was your first job?
Would whizlabadmin1 be required to answer the security question “In what city was your first job?” to reset their password?
- A. Yes
- B. No
Explanation:
Answer – B
For administrators, the password reset policy is different, wherein they are not asked for security questions.
The Microsoft documentation mentions the following.
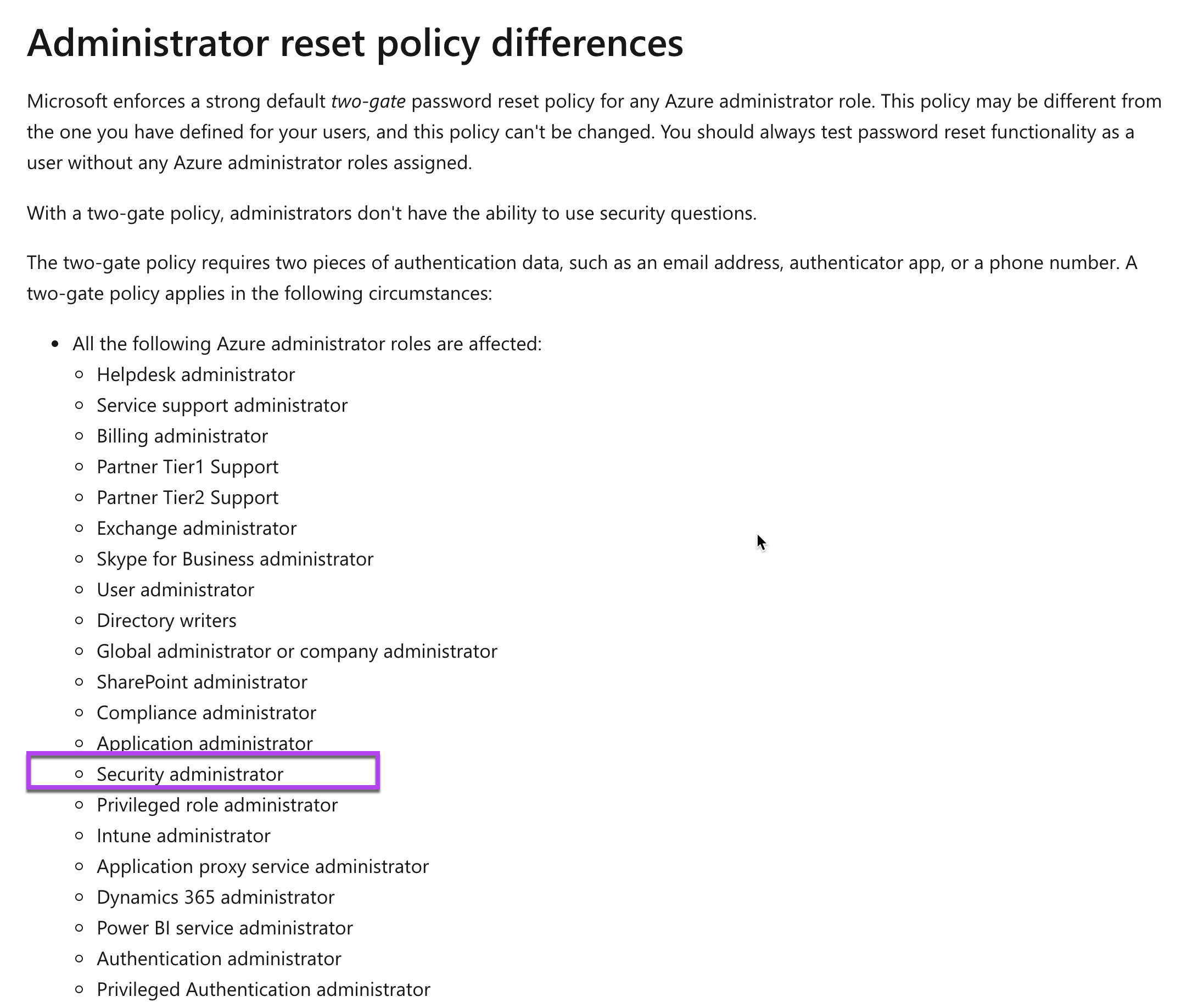
For more information on the password reset policy for administrators, please visit the following URL-
A company has an Azure AD tenant. They have users that are also synced with their on-premise environment. The domain contains the following users.
|
Name |
Role |
|
whizlabadmin1 |
Security administrator |
|
whizlabadmin2 |
Billing administrator |
|
whizlabusr |
Reports reader |
The administrator has enabled self-service password reset (SSPR) for all users.
The administrator has enabled the following SSPR settings.
- Number of methods required to reset – 2
- Methods available to users – Mobile phone and Security questions
- Number of questions to register – 3
- Number of questions to reset – 3
The following security questions are chosen.
- In what city was your first job?
- What was the name of the first school you attended?
- What was your first job?
Would whizlabadmin2 be required to answer the security question “What was the name of the first school you attended?” to reset their password?
- A. Yes
- B. No
Explanation:
Answer - B
For administrators, the password reset policy is different, wherein they are not asked for security questions.
The Microsoft documentation mentions the following.
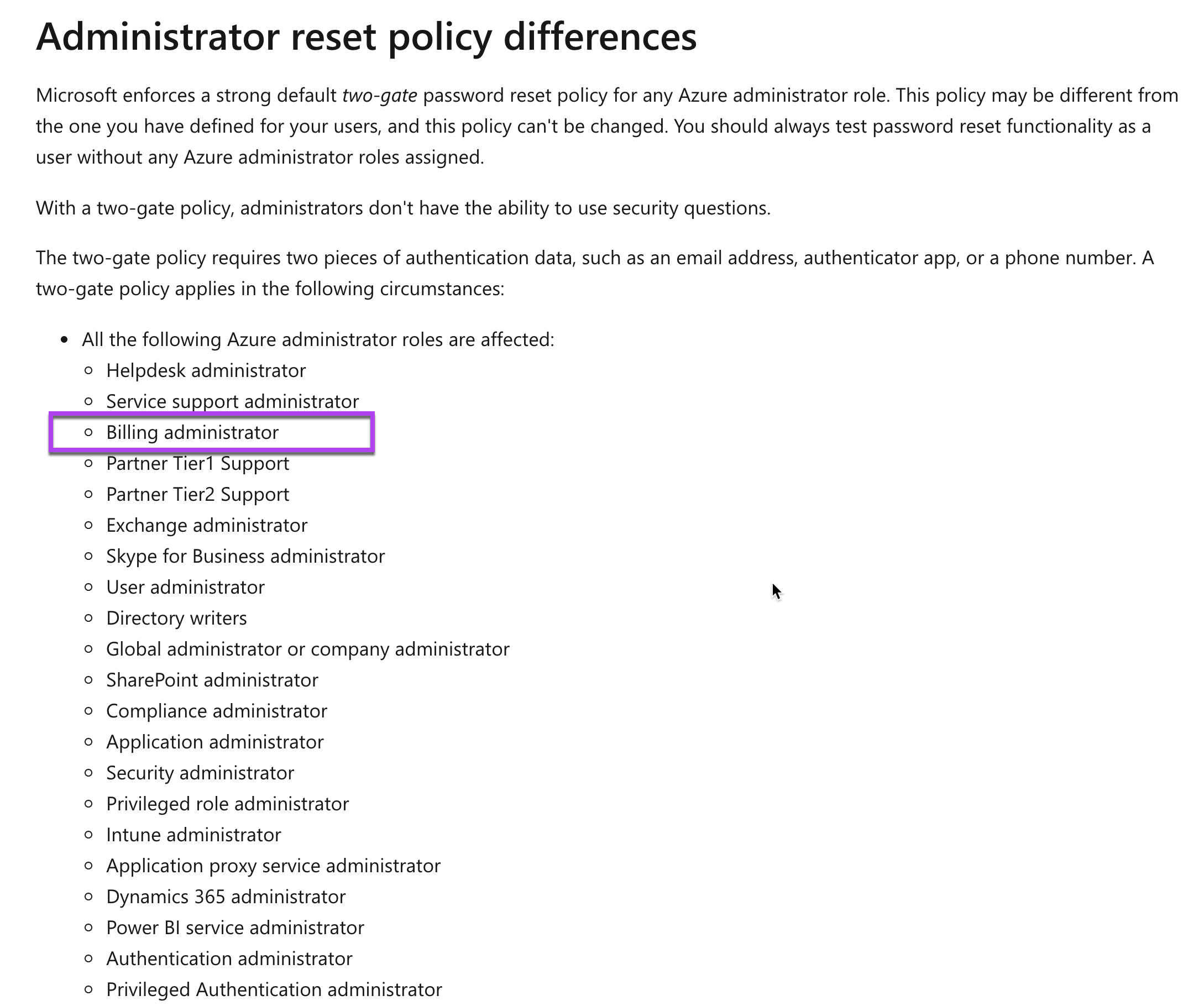
For more information on the password reset policy for administrators, please visit the following URL-
A company has an Azure AD tenant. They have users that are also synced with their on-premise environment. The domain contains the following users.
|
Name |
Role |
|
whizlabadmin1 |
Security administrator |
|
whizlabadmin2 |
Billing administrator |
|
whizlabusr |
Reports reader |
The administrator has enabled self-service password reset (SSPR) for all users.
The administrator has enabled the following SSPR settings.
- Number of methods required to reset – 2
- Methods available to users – Mobile phone and Security questions
- Number of questions to register – 3
- Number of questions to reset – 3
The following security questions are chosen.
- In what city was your first job?
- What was the name of the first school you attended?
- What was your favorite sport in high school?
Would whizlabusr be required to answer the security question “In what city was your first job?” to reset their password?
- A. Yes
- B. No
Explanation:
Correct Answer – A
Since SSPR has been enabled for all users. The user would need to answer the security-related question to reset their password.
For more information on how password reset works, please visit the following URL-
Please select all true statements that apply to the use of Azure Disk Encryption (ADE) for Azure VM disk protection.
- Correct Answer
ADE encrypted VM must be backed up to the Recovery Service Vault
ADE uses BitLocker for Windows VM-controlled disks
ADE is integrated with Azure Key Vault
ADE uses DM-Crypt for Linux-based VMs
Explanation:
Correct Answers:
|
ADE encrypted VM must be backed up to the Recovery Service Vault. |
|
ADE uses BitLocker for Windows VM-controlled disks. |
|
ADE is integrated with Azure Key Vault. |
|
ADE uses DM-Crypt for Linux-based VMs. |
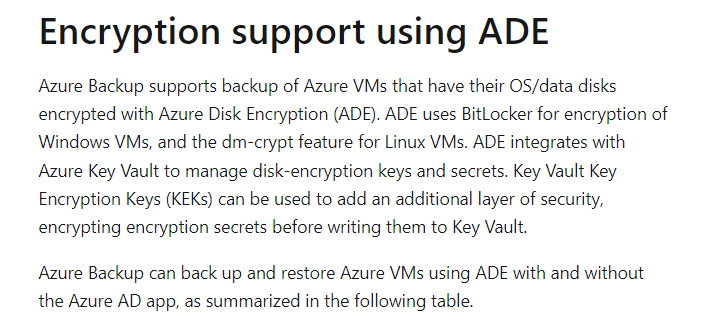
- Azure Backup supports the backup of Azure VMs that have their OS/data disks encrypted with Azure Disk Encryption (ADE).
- Azure Disk Encryption for Windows virtual machines (VMs) uses the BitLocker feature of Windows to provide full disk encryption of the OS disk and data disk.
- Azure Disk Encryption requires an Azure Key Vault to control and manage disk encryption keys and secrets. Your key vault and VMs must reside in the same Azure region and subscription
- Azure Disk Encryption uses the DM-Crypt feature of Linux to provide volume encryption for the OS and data disks of Azure virtual machines (VMs)k encryption keys and secrets.
References:
- Back up and restore encrypted Azure VMs - Azure Backup | Microsoft Docs
- Azure Disk Encryption scenarios on Windows VMs - Azure Virtual Machines | Microsoft Docs
- Enable Azure Disk Encryption for Windows VMs - Azure Virtual Machines | Microsoft Docs
- Enable Azure Disk Encryption for Linux VMs - Azure Virtual Machines | Microsoft Docs
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Region |
|
whizlabs-rg1 |
Resource group |
West US |
|
whizlabs-rg2 |
Resource group |
East Asia |
|
whizlabstore1 |
Storage Account |
West US |
|
whizlabstore2 |
Storage Account |
East Asia |
|
whizlabvm1 |
Virtual Machine |
West US |
|
whizlabnetwork1 |
Virtual Network |
West US |
|
whizlabnetwork2 |
Virtual Network |
East Asia |
Currently, the whizlabvm1 virtual machine resides in the whizlabnetwork1 virtual network.
You need to ensure that the virtual machine resides in the whizlabnetwork2 virtual network.
You decide to create a new network interface and then add the network interface to the whizlabvm1 virtual machine.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
In order to add the virtual machine to the virtual network, the virtual machine needs to be in the same region as the virtual network, which is not the case over here.
The virtual machine is in the West US region and the whizlabnetwork2 virtual network is in the East Asia region.
For more information on virtual networks and virtual machines, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Region |
|
whizlabs-rg1 |
Resource group |
West US |
|
whizlabs-rg2 |
Resource group |
East Asia |
|
whizlabstore1 |
Storage Account |
West US |
|
whizlabstore2 |
Storage Account |
East Asia |
|
whizlabvm1 |
Virtual Machine |
West US |
|
whizlabnetwork1 |
Virtual Network |
West US |
|
whizlabnetwork2 |
Virtual Network |
East Asia |
Currently, the whizlabvm1 virtual machine resides in the whizlabnetwork1 virtual network.
You need to ensure that whizlabvm1 virtual machine resides in the whizlabnetwork2 virtual network.
You decide to delete the whizlabvm1 virtual machine and then recreate the virtual machine in whizlabnetwork2. You also create a new network interface for the virtual machine.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, this is the right approach. You will have to delete the virtual machine and then create the virtual machine in the East Asia region.
For more information on virtual networks and virtual machines, please visit the following URL-
A company has the following resources defined as part of its Azure subscription.
|
Name |
Type |
Region |
|
whizlabs-rg1 |
Resource group |
West US |
|
whizlabs-rg2 |
Resource group |
East Asia |
|
whizlabstore1 |
Storage Account |
West US |
|
whizlabstore2 |
Storage Account |
East Asia |
|
whizlabvm1 |
Virtual Machine |
West US |
|
whizlabnetwork1 |
Virtual Network |
West US |
|
whizlabnetwork2 |
Virtual Network |
East Asia |
Currently, the whizlabvm1 virtual machine resides in the whizlabnetwork1 virtual network.
You need to ensure that the virtual machine resides in the whizlabnetwork2 virtual network.
You decide to turn off the whizlabvm1 virtual machine and then add a new network interface to the virtual machine.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
In order to add the virtual machine to the virtual network, the virtual machine needs to be in the same region as the virtual network, which is not the case over here.
The virtual machine is in the West US region and the whizlabnetwork2 virtual network is in the East Asia region.
For more information on virtual networks and virtual machines, please visit the following URL-
Your company has the following resources deployed to Azure.
|
Name |
IP address |
Connected to |
|
whizlabvm1 |
10.1.0.4 |
whizlabnetwork1/Subnet1 |
|
whizlabvm2 |
10.1.10.4 |
whizlabnetwork1/Subnet2 |
|
whizlabvm3 |
172.16.0.4 |
whizlabnetwork2/SubnetA |
|
whizlabvm4 |
10.2.0.8 |
whizlabnetwork3/SubnetB |
You install a DNS service on the virtual machine whizlabvm1.
The DNS server settings are then configured for each virtual network, as shown below.
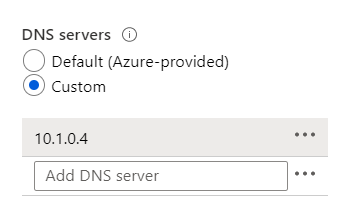
You have to ensure that all virtual machines can resolve DNS names by using the DNS service on the virtual machine whizlabvm1. Which of the following would you implement for this requirement?
- A. Add service endpoints for the virtual network whizlabnetwork2 and whizlabnetwork3.
- B. Add a service endpoint for the virtual network whizlabnetwork1.
- C. Configure a conditional forwarder for the whizlabvm1 virtual machine.
- D. Configure virtual network peering connections between all virtual networks.
Explanation:
Answer – D
Since the networks are isolated from each other, you still need to ensure that the machines can communicate across the virtual networks. And this can be accomplished with the help of the virtual network peering connections.
Options A and B are incorrect since service endpoints should be used when you want to connect virtual networks securely to other Azure-based services.
Option C is incorrect since this should be used when you want to forward DNS requests to the Azure DNS servers.
For more information on virtual network peering connections, please visit the following URL-
Your company has the following resources defined in Azure.
|
Name |
Type |
Resource Group |
Location |
|
whizlabvault2090 |
Recovery services vault |
whizlabs-rg |
East US |
|
whizlabvm1 |
Virtual Machine |
whizlabs-rg |
East US |
|
whizlabvm2 |
Virtual Machine |
whizlabs-rg |
West US |
All of the virtual machines run Windows Server 2016.
On the virtual machine whizlabvm1, you go ahead and back up a folder named whizlabdata as per the following schedule.
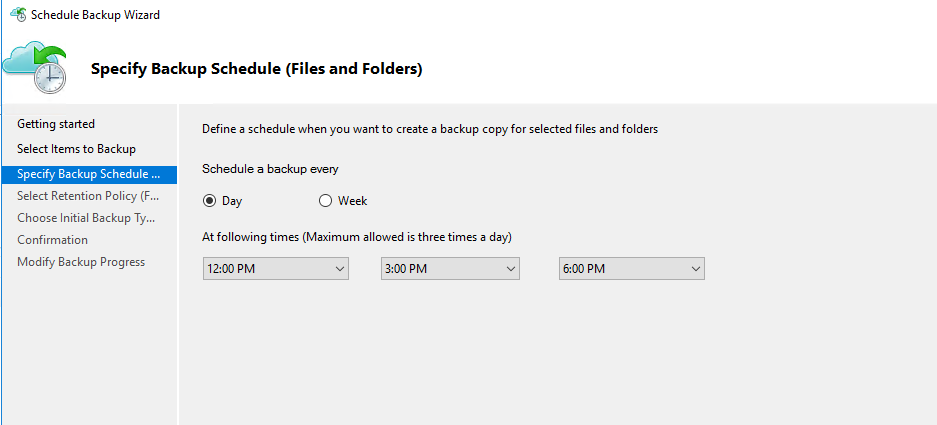
After the backup is in place, you want to restore the backup to the virtual machine whizlabvm2.
Which of the following must you implement for this requirement?
- A. On the virtual machine whizlabvm1, install the Windows Server Backup feature.
- B. On the virtual machine whizlabvm2, install the Windows Server Backup feature.
- C. On the virtual machine whizlabvm1, install the Microsoft Azure Recovery Services Agent.
- D. On the virtual machine whizlabvm2, install the Microsoft Azure Recovery Services Agent.
Explanation:
Answer – D
You want to restore the folder on another virtual machine. You should install the Microsoft Azure Recovery Services Agent on the destination virtual machine.
Options A and B are incorrect since we want to restore the files using the Microsoft Azure Recovery Services Agent.
Option C is incorrect. We already have the MARS agent running on this machine to take the backup.
For more information on using the backup agent on Windows machines, please visit the following URL-
Your company has an Azure virtual machine that runs Windows Server 2016. You have to create an alert in Azure whenever two error events are logged to the System log on the virtual machine within an hour.
You decide to create a Log Analytics workspace and configure the data settings. You then set up the virtual machine as a data source. You then create an alert in Azure Monitor and specify the Log Analytics as the source.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
You can actually create alerts in Azure Monitor based on the events recorded in the Log Analytics workspace.
The Microsoft documentation also has a tutorial on this.
For more information on the tutorial itself, please visit the following URL-
Your company has an Azure virtual machine that runs Windows Server 2016. You have to create an alert in Azure whenever two error events are logged to the System log on the virtual machine within an hour.
You decide to create an Event subscription on the virtual machine. You then create an alert in Azure Monitor and ensure to specify the virtual machine as the source.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
You actually have to record the events in a Log Analytics workspace. And then configure alerts in Azure monitor based on the Azure Log Analytics workspace.
For more information on a tutorial on how this can be achieved, please visit the following URL-
Your company has an Azure virtual machine that runs Windows Server 2016. You have to create an alert in Azure whenever two error events are logged to the System log on the virtual machine within an hour.
You decide to create Notifications on the virtual machine. You then create an alert in Azure Monitor and ensure to specify the virtual machine as the source.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
You actually have to record the events in a Log Analytics workspace. And then configure alerts in Azure monitor based on the Azure Log Analytics workspace.
For more information on a tutorial on how this can be achieved, please visit the following URL-
You create an AKS cbkubecluster cluster. Here is a snapshot from the Networking section of the Kubernetes service overview.
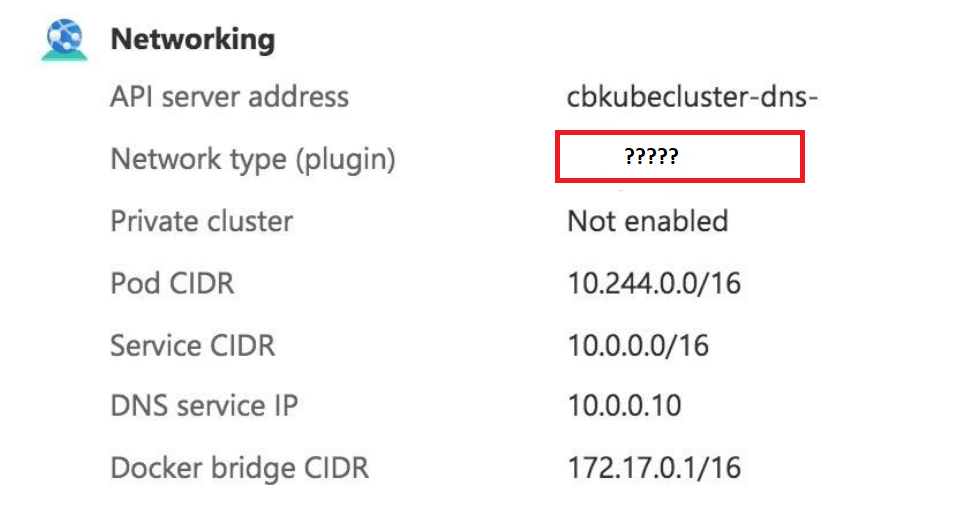
You need to select the type of network model to use for the AKS cluster. Please select the correct network model from the options below to fulfill the question requirement
- A. VPN Gateway
- B. Kubenet
- C. Express Route
- D. Azure CNI
- E. VNet Peering
Explanation:
Correct Answer: B
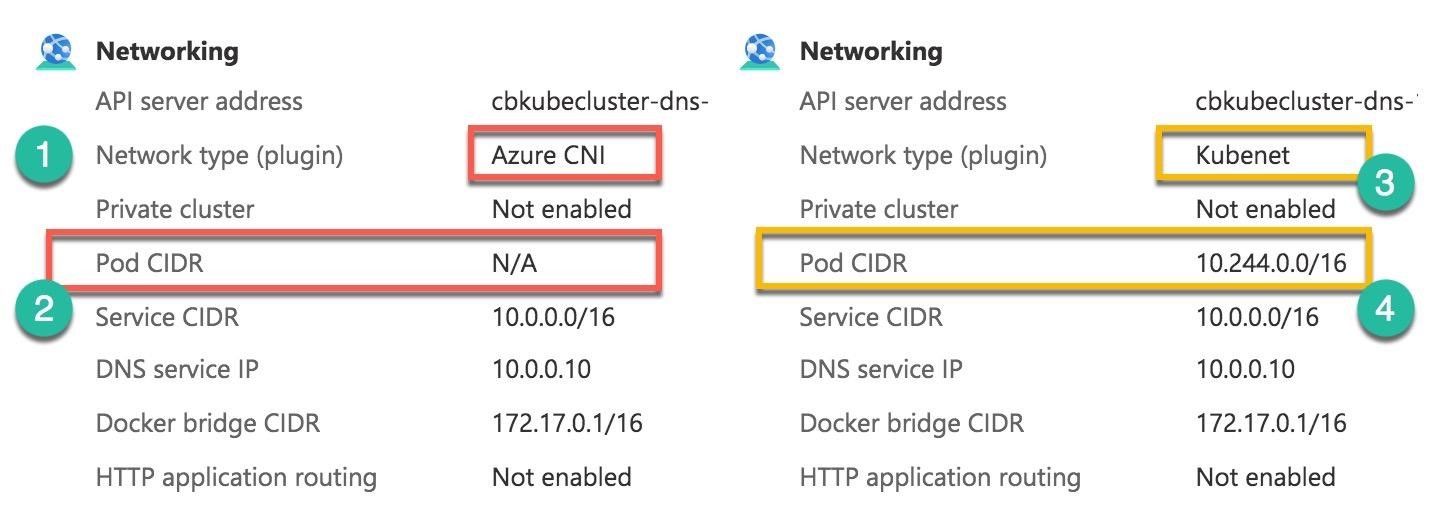
When you create an AKS cluster, you have two choices of the network models for Azure virtual networking: Kubenet and Azure Container Networking Interface (CNI). The main difference between the two models is in providing IP addresses to the pods. The Kubenet (Number 3) is the basic networking model that receives the IP addresses for the nodes from the Azure Vnet subnet, but the pods are served with logically different IP address space: Pod CIDR (Number 4). The pods cannot communicate directly with each other. They have to use Network Address Translation (NAT) to reach any resources on the VNet. In the Azure CNI (Number 1), the pods directly receive IP addresses from the subnet pool. Therefore, there is no value for the Pod CIDR (Number 2). For CNI, you need to plan your address space beforehand to avoid running out of the subnet addresses if you have many pods.
The Kubenet creates an internal Kubernetes virtual network. The Pod CIDR assigns the /24 address space for each node in the cluster. The first node has an internal space of 10.244.0.0/24, then — 10.244.1.0/24 for the next node, and so on (Number 1). And the routing table connects the pods with the Vnet (Number 2 and 3).
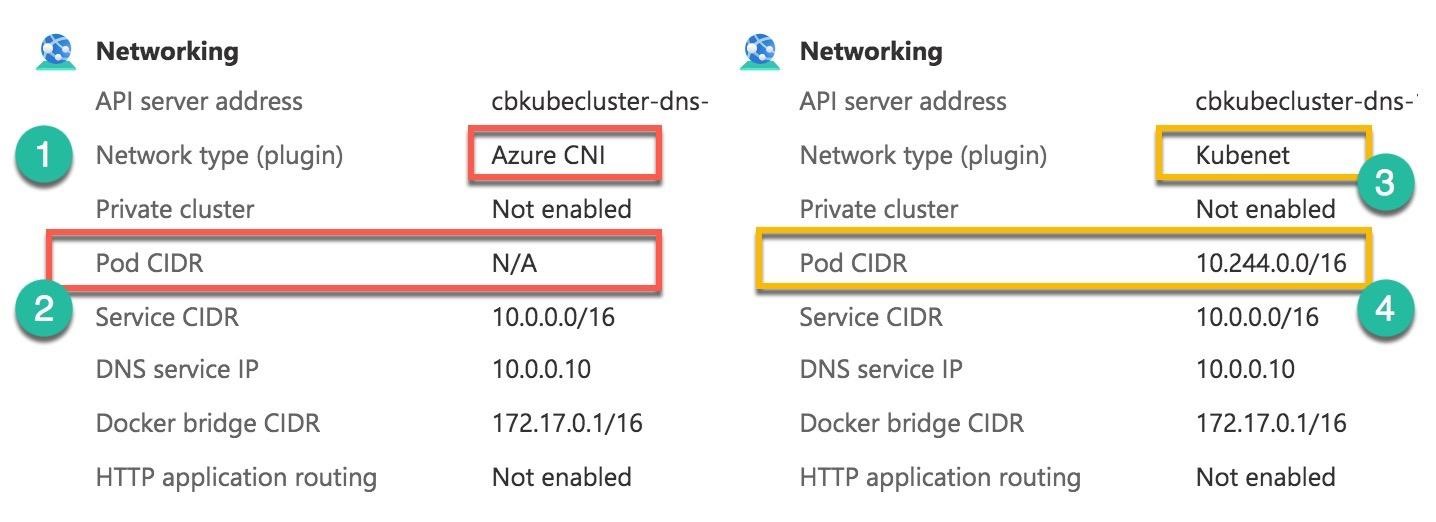
The pods IP addresses for the first node will start from 10.244.0.1 and for the second node — from 10.244.1.1, etc.
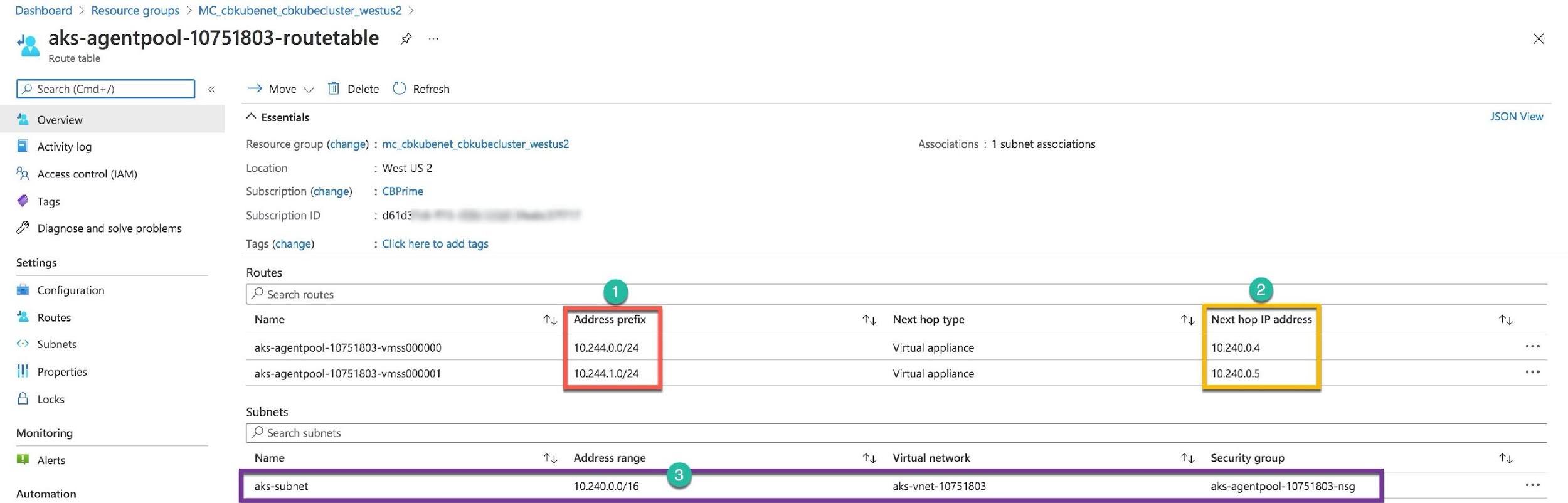
All other options are incorrect.
For more information about AKS networking, please visit the below URLs:
You create an App Service plan B1 for your web app. You want Azure to be able to add up to 10 VM instances to run your app automatically during the highest traffic on your site.
What are two configuration options you should implement to achieve your goal in the most cost-effective way?
- A. Scale up based on a schedule
- B. Scale out the service plan to S1
- C. Scale out based on a metric
- D. Scale up the service plan to P1
- E. Scale out based on a schedule
- F. Scale up the service plan to S1
- G. Scale up based on a metric
- H. Scale out the service plan to P1
Explanation:
Correct Answers: C and F
Suppose you want Azure to add resources for your web app automatically. First, you need to evaluate your App Service plan and then configure the conditions for the app scaling. The automatic process of adding the VM resources is called autoscaling.
The App Service plan provides the VM configuration (CPU, memory, disk space), custom domains, certificates, autoscaling, etc. You can change the plan tier if you need more memory or CPU or a number of additional VM instances to run your app. Changing the App Service plan and scaling the resources mentioned above is called Scale up.
When you need to add more VM instances to run your app based on the metric or schedule, this scaling is called Scale out.
The shared compute tier (Free and Basic tiers) of the App Service plan does not provide the autoscaling functionality. You can scale your app resources manually up to 3 VM instances, if they are available, only in the Basic (B1, B2, and B3) tier. The Free tier does not have this ability. Starting from the Standard tier (S1, S2, S3) and up, the App Service plans provide the autoscaling functionality with up to 30 VM instances in the Premium (P1, P2, P3) tier. The Scale up to S1 tier provides the autoscale functionality with up to 10 VM instances.
After changing the plan from B1 to S1 tier, you will see the autoscale option (Number 2) in the Scale out (App Service plan) section (Number 1). You select the Scale mode based on a metric (Number 3) and Add a rule (Number 4). The portal opens the new section to the right — Scale rule (Number 5). You can use this screen to create your scaling rule based on the metric, like “CPU Percentage,” define the trigger threshold, like CPU load above 70% for 10 minutes, (Number 7), and the Action, like add a new VM instance if the above conditions are met (Number 8).
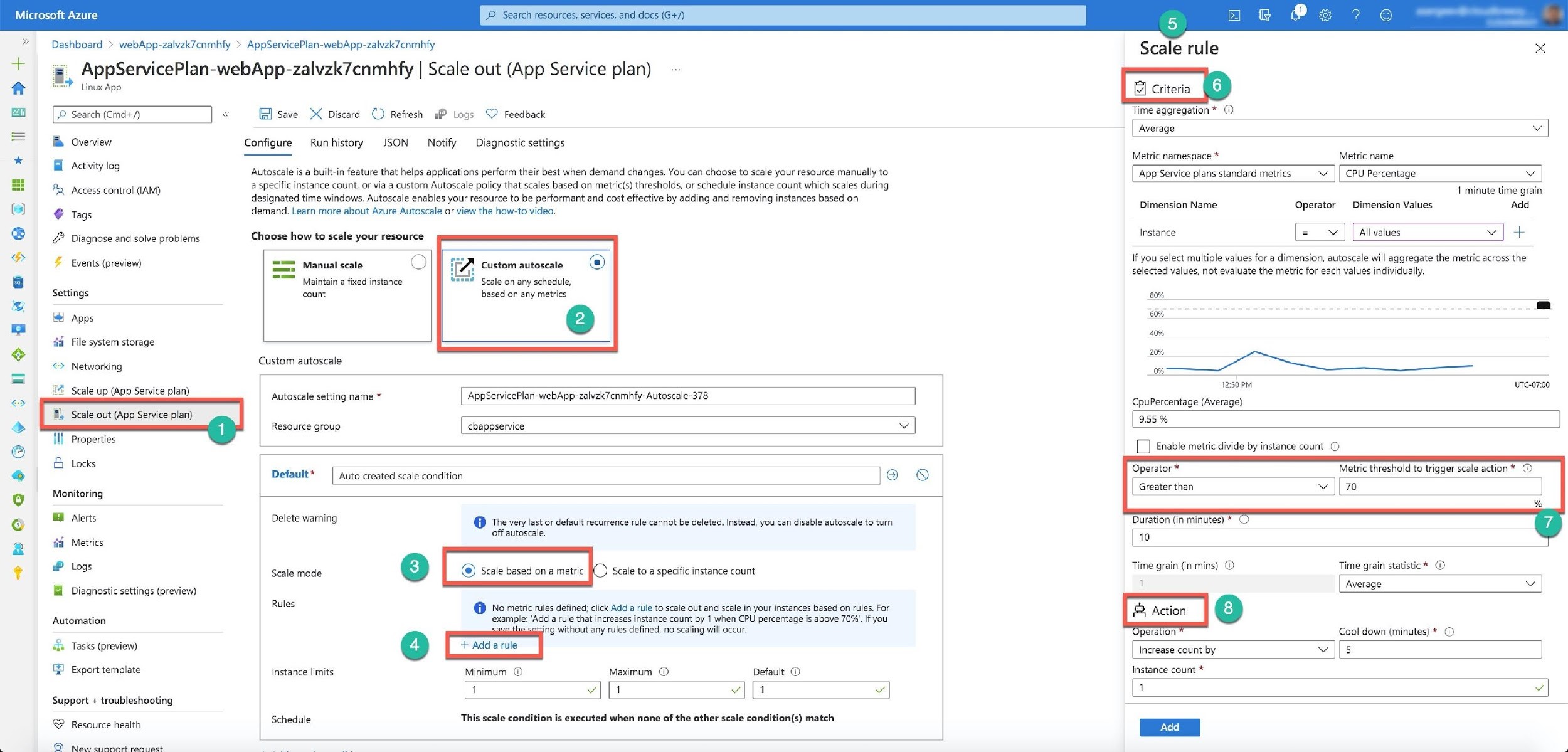
All other options are incorrect.
For more information about scaling settings in App Service Plan, please visit the below URLs:
- https://docs.microsoft.com/en-us/azure/azure-monitor/autoscale/autoscale-get-started
- https://docs.microsoft.com/en-us/azure/app-service/manage-scale-up
- https://docs.microsoft.com/en-us/azure/app-service/overview-hosting-plans
- https://docs.microsoft.com/en-us/learn/modules/app-service-scale-up-scale-out/2-scale-a-web-app-manually
You want to protect your web app using Azure AD authentication and limit access to the app only to the users in your organization.
Please select three steps that you need to take.
- A. Configure Conditional Access
- B. Register an app in Azure AD
- C. Set App Service authentication settings
- D. Create Azure AD Service principal
- E. Select an Identity Provider
Explanation:
Correct Answers: B, C and E
After you create your web app, you can use two options on the App service blade under the Settings section: Authentication or Authentication (classic). If you decide to use the Authentication (classic), the Azure portal will ask you to convert to the current Identity Provider Authentication that Authentication provides.
When you open the Authentication, you need to choose an Identity provider for your web app authentication. There are several options to select from: Microsoft (including Azure AD identities), Facebook, Google, and Twitter. For the Azure AD identities, choose Microsoft (Number 1).
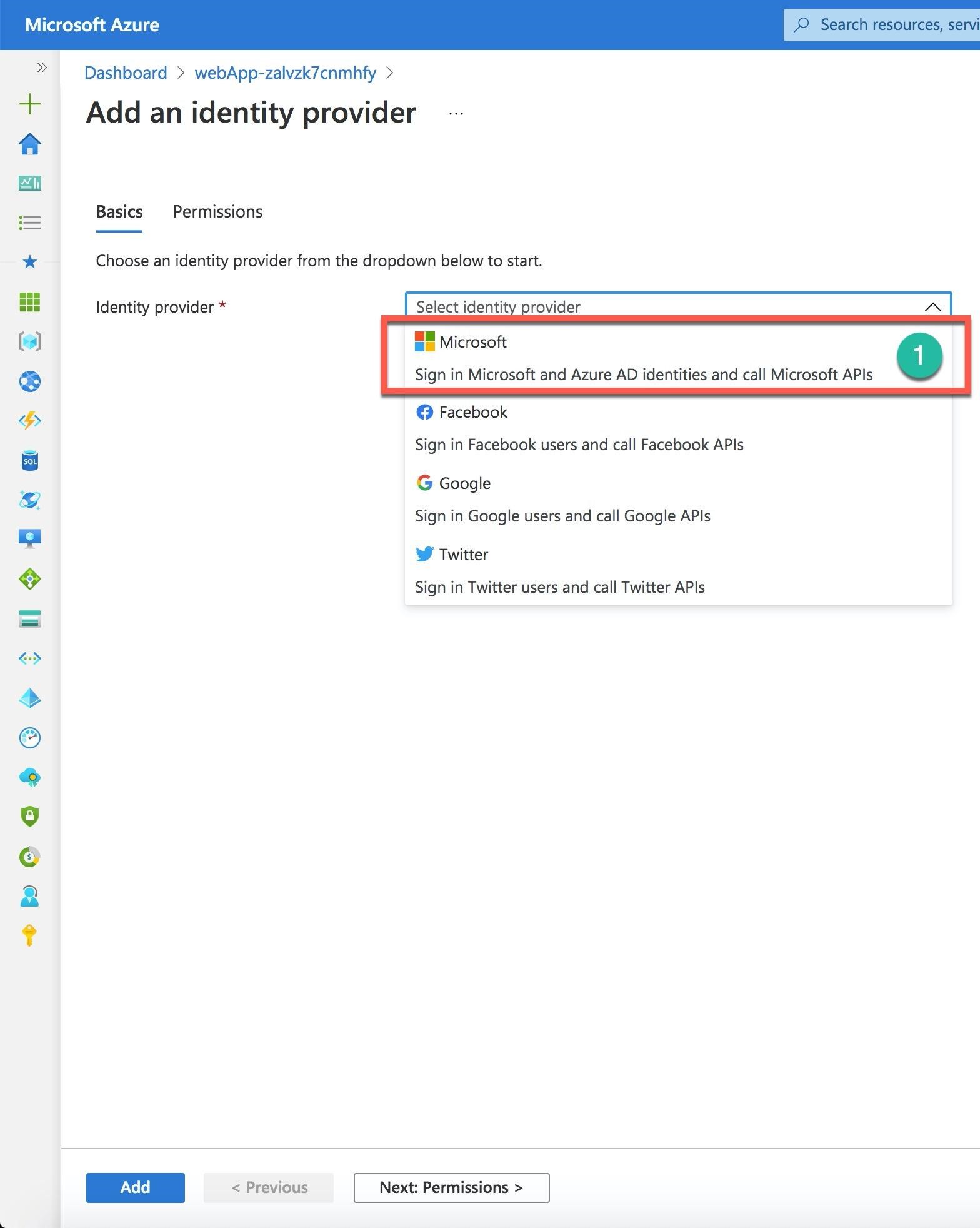
After you select Microsoft as the identity provider (Number 1), the new screen asks you to register your app within the Azure AD (Number 2) and define the App Service authentication settings to require authentication (Number 3).
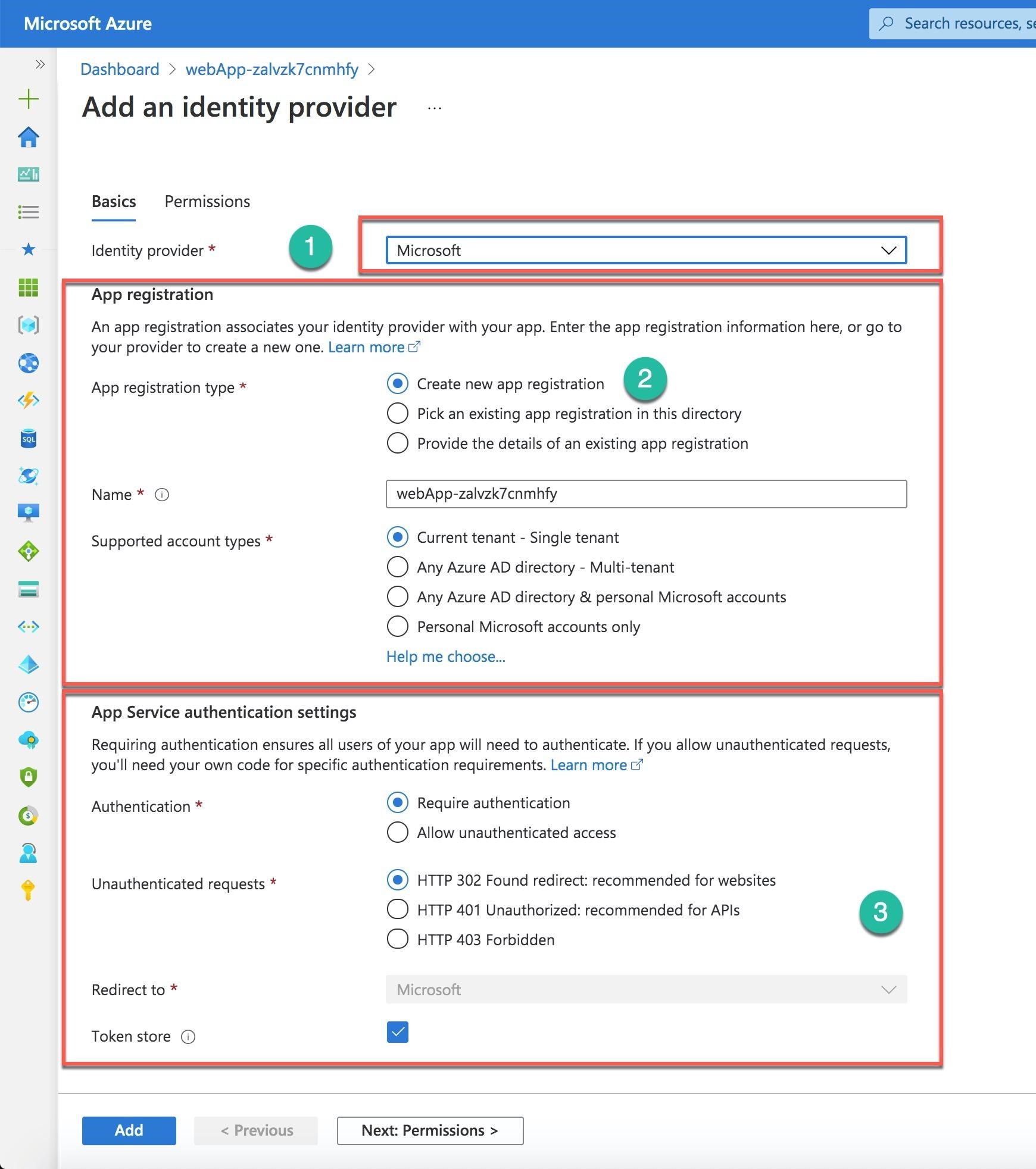
After pushing the Add button, only users of your organization can access your web app. You can verify that if you open the app as an Azure AD registered app (Number 1).
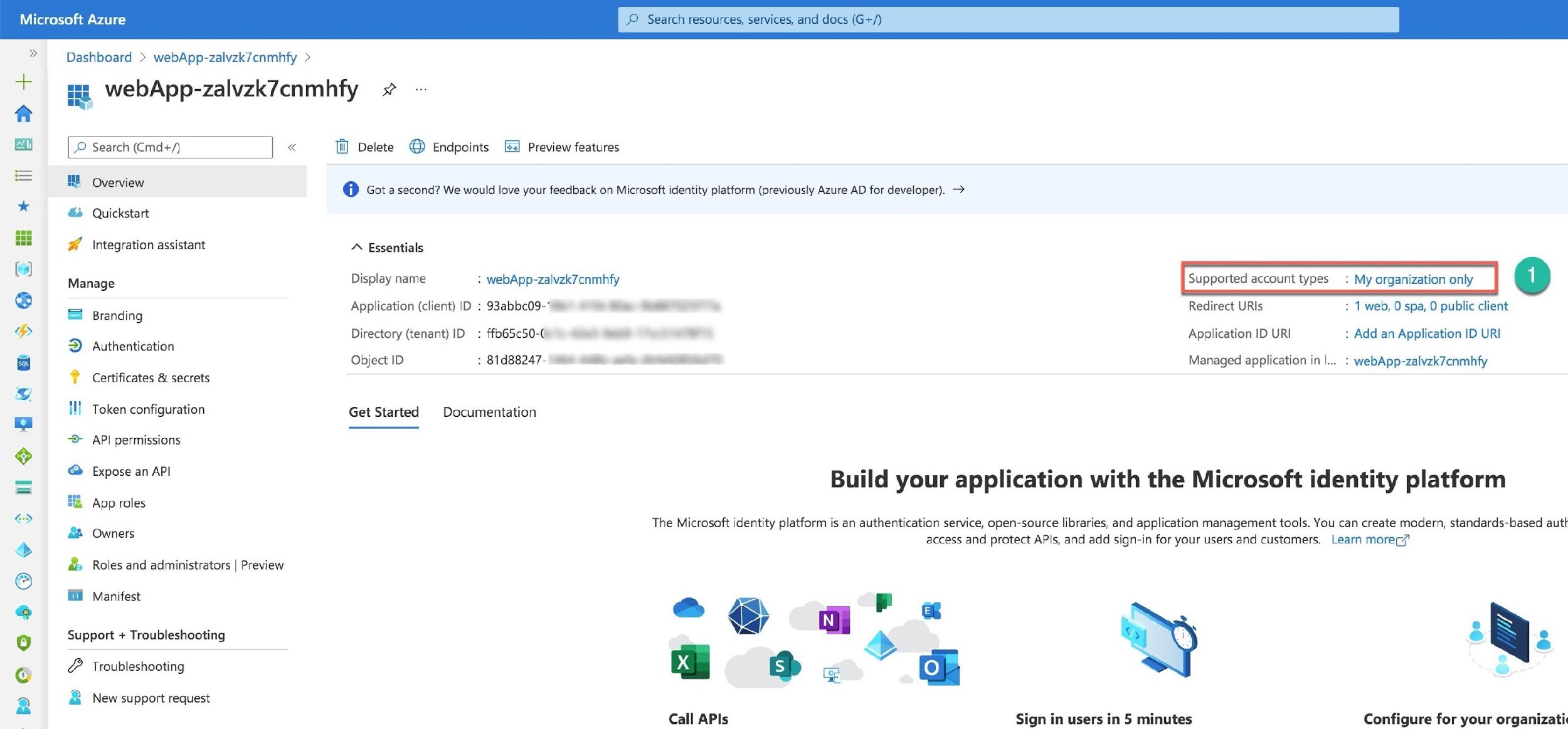
All other options are incorrect.
For more information about App Service security, please visit the below URLs:
You need to create a scheduled backup for your App service app using Azure CLI.
Please select three commands you need to run to achieve your goal.
- A. az storage container create
- B. az webapp config backup update
- C. az appservice plan create
- D. az storage container add
- E. az webapp config backup create
- F. az storage account create
Explanation:
Correct Answers: A, B and F
You can create a manual or scheduled backup for your web application and use the backup to restore your app. There are three main steps to create a web app backup:
- Create a storage account
- Create a storage container
- Create a web app backup
To create a storage account using Azure CLI, you need to run az storage account create command and provide the account name, resource group, location, and account type and redundancy in the form of SKU:
az storage account create --name yourstoragename --resource-group yourrgname --location yourlocation --sku Standard_LRS
Next, you need to create a storage container using az storage container create command:
az storage container create --account-name yourstoragename --name yourcontainername
After creating a container, you need to construct the URL for the container using the SAS token, like this:
sasurl=https://yourstoragename.blob.core.windows.net/yourcontainername?$sastoken
You can generate the SAS token by using az storage container create generate-sas command.
And finally, you can run the az webapp config backup update command, like this for a backup every 3 days and 21 days of retention:
az webapp config backup update --resource-group yourrgname --webapp-name yourwebappname --container-url $sasurl --frequency 3d --retain-one true --retention 21
You can back up not only your web app but also the database that it uses. However, the total size of your web app backup, including the database, should not exceed 10 GB. The backups are stored as .zip files in a storage container. The database backup is stored in the root of the zip file.
All other options are incorrect.
For more information about App Service app backups, please visit the below URLs:
You have set up a computer named whizlabclient1. It has a point-to-site VPN connection to an Azure virtual network named whizlabnetwork. The point-to-site connection uses a self-signed certificate. You now have to establish a point-to-site VPN connection to the same virtual network from another computer named whizlabclient2. The VPN client configuration package is downloaded and installed on the whizlabclient2 computer.
You have to ensure that you can establish a point-to-site VPN connection from the whizlabclient2 computer.
You decide to set the Startup type for the IPSec Policy Agent service to Automatic on the whizlabclient2 computer.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
Here you have to ensure that the client certificate is installed on every client computer. It needs to establish a Point-to-Site VPN connection to the Azure virtual network.
For more information on Point-to-Site VPN connections, please visit the following URL-
You have setup a computer named whizlabclient1 that has a point-to-site VPN connection to an Azure virtual network named whizlabnetwork. The point-to-site connection makes use of a self-signed certificate. You now have to establish a point-to-site VPN connection to the same virtual network from another computer named whizlabclient2. The VPN client configuration package is downloaded and installed on the whizlabclient2 computer.
You have to ensure that you can establish a point-to-site VPN connection from the whizlabclient2 computer.
You decide to modify the Azure AD authentication policies.
Would this fulfil the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
Here you have to ensure that the client certificate is installed on every client computer that needs to establish a Point-to-Site VPN connection to the Azure virtual network
For more information on Point-to-Site VPN connections, please visit the following URL
You have setup a computer named whizlabclient1 that has a point-to-site VPN connection to an Azure virtual network named whizlabnetwork. The point-to-site connection makes use of a self-signed certificate. You now have to establish a point-to-site VPN connection to the same virtual network from another computer named whizlabclient2. The VPN client configuration package is downloaded and installed on the whizlabclient2 computer.
You decide to export the client certificate from whizlabclient1 and then install the certificate on whizlabclient2.
Would this fulfil the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
The right approach is to install the client certificate on every computer that needs to establish a Point-to-Site VPN connection to the Azure virtual network
The Microsoft documentation mentions the following
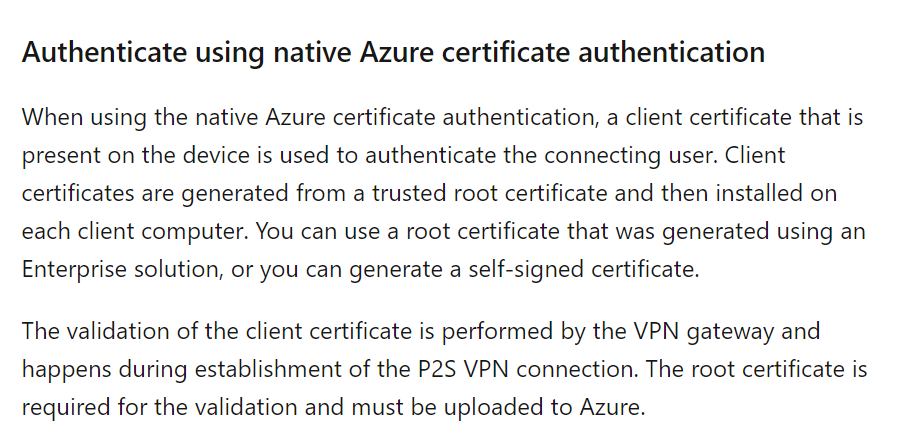
For more information on Point-to-Site VPN connections, please visit the following URL
You have set up a computer named whizlabclient1 that has a point-to-site VPN connection to an Azure virtual network named whizlabnetwork. The point-to-site connection makes use of a self-signed certificate. You now have to establish a point-to-site VPN connection to the same virtual network from another computer named whizlabclient2. The VPN client configuration package is downloaded and installed on the whizlabclient2 computer.
You decide to use Azure Active Directory to authenticate the whizlabclient2 computer.
Would the above decision fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
There is no need to use the Azure Active Directory to authenticate the whizlabclient2 computer.
Azure accepts a P2S VPN connection, but the user has to be authenticated first.
There are two mechanisms that Azure offers to authenticate a connecting user.
-
Authenticate using the native Azure certificate authentication
-
Authenticate using the native Azure Active Directory authentication
So there is already native Azure Certificate authentication used for clients connecting to a VNet over a Point-to-Site VPN connection.
Once you obtain a root certificate, you upload the public key information to Azure. The root certificate is then considered 'trusted' by Azure for connection over P2S to the virtual network. You also generate client certificates from the trusted root certificate and then install them on each client computer. The client certificate is used to authenticate the client when it initiates a connection to the VNet.
In the question, it is already mentioned that a VPN client should have a VPN client certificate so there is no need for AD authentication. Hence B is the right answer.
For more information on Point-to-Site VPN connections, please visit the following URL
You have to create an Azure Command Line Interface script that would carry out the following tasks
- Create a new Azure virtual network with an address space of 10.2.0.0/16
- The virtual network needs to have a subnet with an address space of 10.2.0.0/24
- Create a new private DNS zone named whizlab.local
- Create a virtual network link for the virtual network with the DNS Zone
You have to complete the below CLI script for these requirements
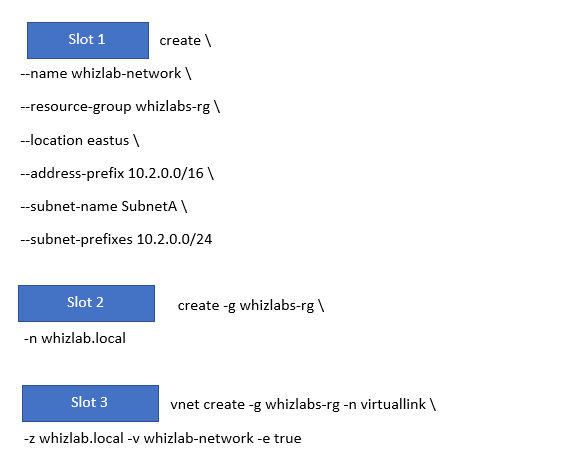
Which of the following should go into Slot 1?
- A. az network private-dns zone
- B. az network vnet
- C. az dns-zone link
- D. az network private-dns link vnet
- E. az group create
Explanation:
Answer – B
First, we need to create a virtual network.
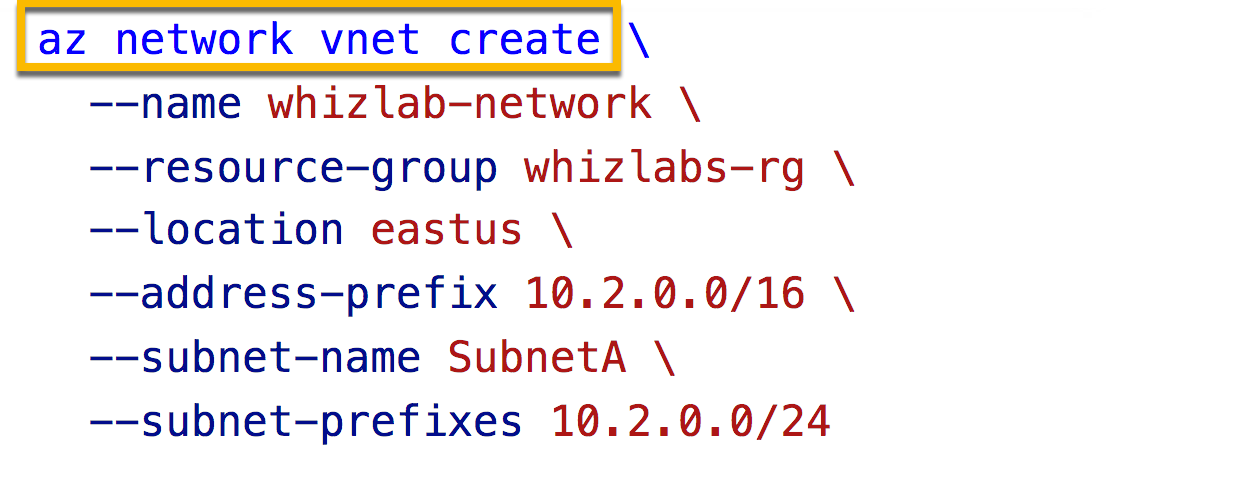
All other options are incorrect.
For more information on working with Private DNS, please visit the following URL
You have to create an Azure Command Line Interface script that would carry out the following tasks
- Create a new Azure virtual network with an address space of 10.2.0.0/16
- The virtual network needs to have a subnet with an address space of 10.2.0.0/24
- Create a new private DNS zone named whizlab.local
- Create a virtual network link for the virtual network with the DNS Zone
You have to complete the below CLI script for these requirements
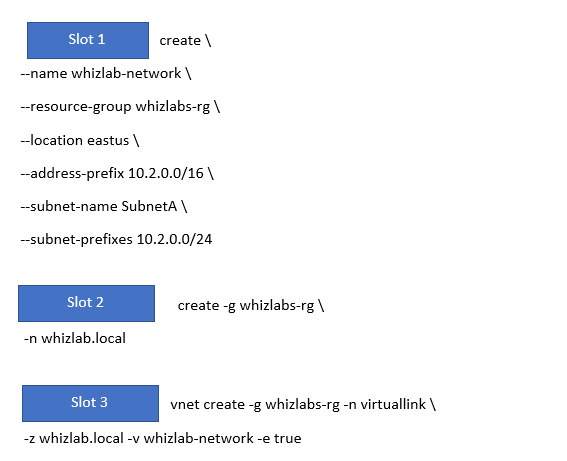
Which of the following should go into Slot 2?
- A. az network private-dns zone
- B. az network vnet create
- C. az dns-zone link
- D. az network private-dns link vnet
- E. az network dns record-set
Explanation:
Answer – A
Next, we have to go ahead and create the private dns zone
All other options are incorrect.
For more information on working with Private DNS, please visit the following URL
You have to create an Azure Command-Line Interface script that would carry out the following tasks.
- Create a new Azure virtual network with an address space of 10.2.0.0/16.
- The virtual network needs to have a subnet with an address space of 10.2.0.0/24.
- Create a new private DNS zone named whizlab.local
- Create a virtual network link for the virtual network with the DNS Zone.
You have to complete the below CLI script for these requirements.
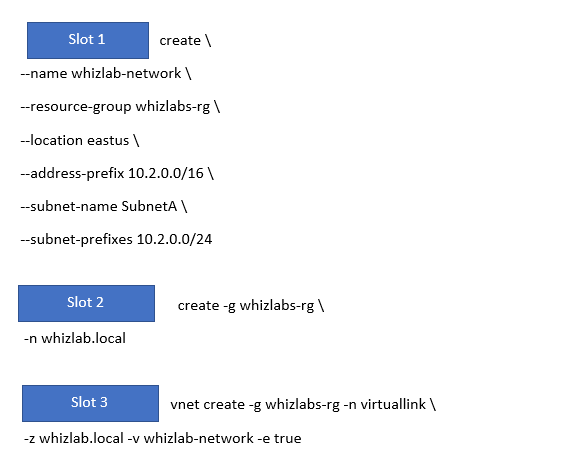
Which of the following should go into Slot 3?
- A. az network private-dns zone
- B. az network vnet create
- C. az dns-zone link
- D. az network private-dns link
- E. az network dns record-set
Explanation:
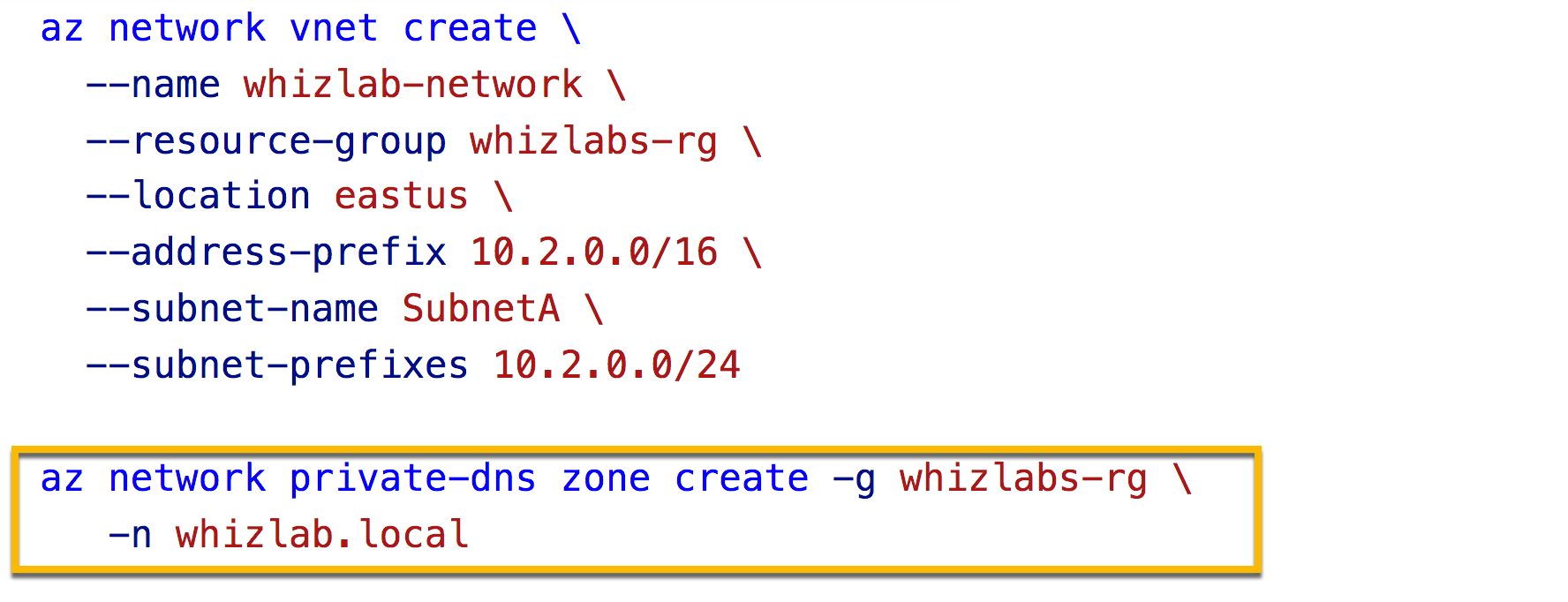
Correct Answer – D
Slot 3 will be az network private-dns link
We have to create a virtual network link for the zone. See the example given below.
Below example creates a virtual network named myAzureVNet. Then it creates a DNS zone named private.whizlabs.com in the MyAzureResourceGroup resource group, links the DNS zone to the MyAzureVnet virtual network, and enables automatic registration.
az network vnet create \
--name myAzureVNet \
--resource-group MyAzureResourceGroup \
--location eastus \
--address-prefix 10.2.0.0/16 \
--subnet-name backendSubnet \
--subnet-prefixes 10.2.0.0/24
az network private-dns zone create -g MyAzureResourceGroup \
-n private.whizlabs.com
az network private-dns link vnet create -g MyAzureResourceGroup -n MyDNSLink \
-z private.whizlabs.com -v myAzureVNet -e true
All other options are incorrect.
For more information on working with Private DNS, please visit the following URL-
You have to deploy a web application for your company by using the Azure App Service. The backup and restore option should be available for the web application. Costs should also be minimized for hosting the application.
Which of the following would you choose as the underlying App Service Plan?
- A. Free
- B. Basic
- C. Standard
- D. Premium
Explanation:
Answer – B
Option B is correct because it is the cost-effective option.
Option A is incorrect: Backup & restore was not available for the Free plan.
Options C and D are incorrect because these are not cost-effective options and are costlier than Basic Plan.
In Azure App Service, you can easily restore app backups. Backup and restore are supported in Basic, Standard, Premium, and Isolated tiers.
For the Basic tier, only the production slot can be backed up and restored. For more information about scaling your App Service plan to use a higher tier, see Scale up an app in Azure.
This is also mentioned in the Microsoft documentation.
Reference: Back up an app - Azure App Service | Microsoft Learn
Your company has an Azure subscription that has the following providers registered.
- Authorization
- Automation
- Resources
- Compute
- Network
- Storage
- Billing
- Web
You have a virtual machine named whizlabvm that has the following configuration.
- Private IP address – 10.1.0.4
- Network Security Group – whizlabnsg
- Public IP Address – None
- Subnet – 10.1.0.0/24
- Location – East US
The Network Watcher was created and enabled automatically with the creation of the virtual network.
You have to record all of the successful and failed connection attempts to the virtual machine.
Which of the following actions would you implement for this requirement? Choose 3 answers from the options given below.
- A. Ensure to register the Microsoft.Insights resource provider.
- B. Ensure to add the Network Watcher connection monitor.
- C. Enable the Azure Network Watcher service in the West US region.
- D. Create a storage account.
- E. Enable the Azure Network Watcher flow logs.
Explanation:
Answer – A, D, and E
To record the successful and failed connection requests, we should use Azure Network Watcher flow logs. The Network Watcher is already enabled in the region, and we can utilize the Network Watcher NSG's flow log functionality. For that, we need to register the microsoft.insights resource provider and create a storage account for storing the flow logs.
The Microsoft documentation mentions the following.
Since this approach is given in the documentation, all other options are incorrect.
For more information on Azure Network Watcher flow logs, please visit the following URL-
You are working as an Azure administrator for an e-commerce company. Your performance team has given the following scenario for load variation requirements
You have to implement a solution that meets the following requirements
The workload for 100 users will be applicable for 24×7*365
The workload for 400 users will be 4 hours daily
The overall cost is to be optimized
The administrator decided that the Standard_B4ms (4cpu, 16 GB) VM will be the best fit for the above workload requirements. He also decided to use scale set for meeting the load variation requirements and recommended the following setting:
- A. Enabling auto-scaling in the scale set
- B. Min number of VM = 4 and max no of VM is 16
- C. You purchase 4 VMs in pay as you go purchase option
- D. You configure proper scaling out and scaling in rule
Explanation:
Correct Answers: A, B and D
- Option A is correct because the Azure scale set can be used for auto-scaling.
- Option B is correct because we need to configure the min and max number of VM for auto-scaling.
- Option D is correct, as we need to define the auto-scaling rule, both for scaling out and scaling in.
- Option C is incorrect because pay using the pay as you go option is not the correct purchase option for a VM which is going to run 24×7×365. The best option for this type of VM is the reservation option, which can provide nearly 70% saving in the cost.
You have to create the Azure Kubernetes cluster. You need to complete the following Azure CLI script for this requirement.
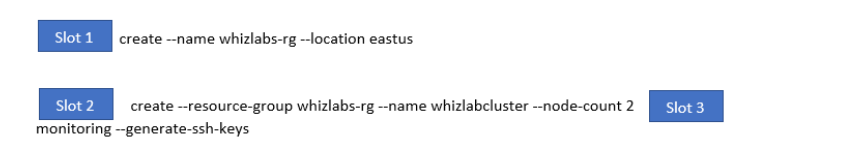
Which of the following would go into Slot 2?
- A. --enable-addons
- B. az group
- C. az aks
- D. --create
Explanation:
Answer – C
The next step is to go ahead and create the Kubernetes cluster.
An example of this is also given in the Microsoft documentation.
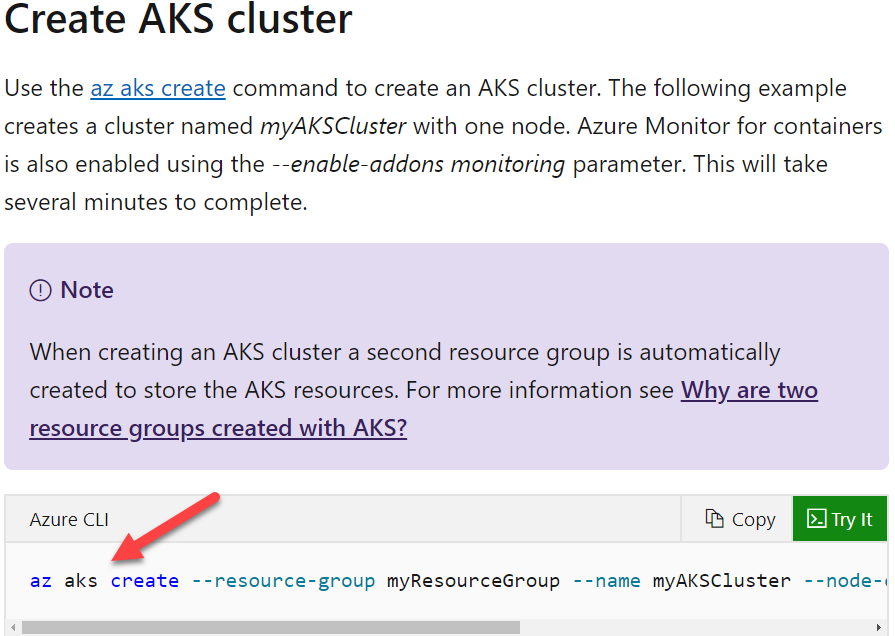
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on working with Azure Kubernetes, please visit the following URL-
You have to create the Azure Kubernetes cluster. You need to complete the following Azure CLI script for this requirement.
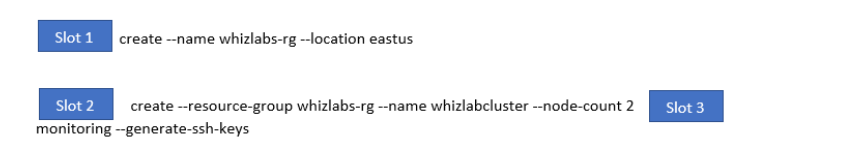
Which of the following would go into Slot 3?
- A. --enable-addons
- B. az group
- C. az aks
- D. --create
Explanation:
Answer – A
We have to ensure that monitoring is enabled for the cluster. We have to use the --enable-addons switch.
An example of this is also given in the Microsoft documentation.
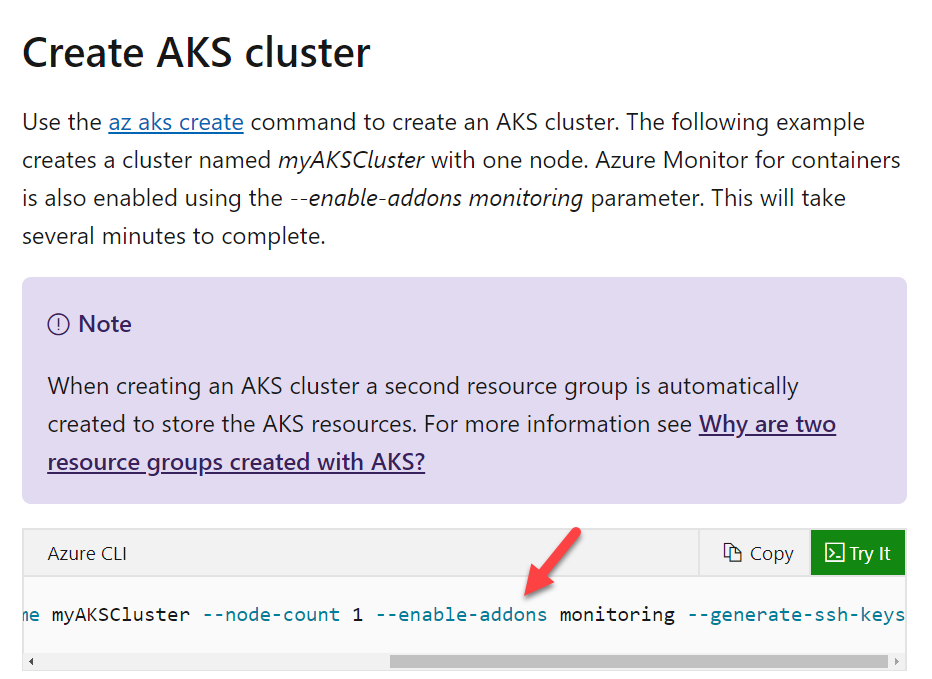
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on working with Azure Kubernetes, please visit the following URL-
Which of the following do you need to configure for whizlabgateway1?
- A. Multi-site listener
- B. A URL path-based routing rule
- C. A basic listener
- D. A basic routing rule
Explanation:
Answer – B
Here we need to route traffic based on different URL’s . This is clearly mentioned the case study
Hence we should use a URL path-based routing rule.
Hence Answer B is correct and all other answer are wrong.
This is also given in the Microsoft documentation. 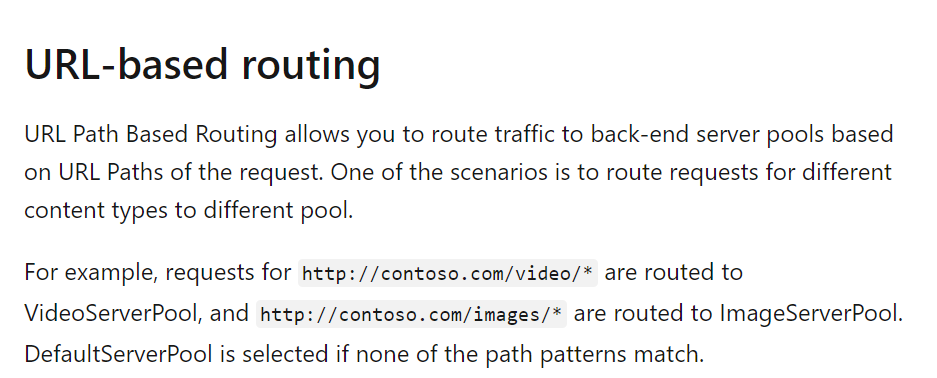
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on the Azure Application Gateway, please visit the following URL-
Which of the following do you need to configure for whizlabgateway2?
- A. Redirection
- B. A URL path-based routing rule
- C. A basic listener
- D. A basic routing rule
- E. Multi-site listeners
Explanation:
Answer – E
Please see the link for case study on the top of the right-hand corner. This case study clearly mentions that whizlabgateway2 must rout request to 2 backend pool - whizlabpool3 and whizlabpool4.
Since we need to direct requests based on different sites, we need to use multi-site listeners. Hence E is the correct answer and all other answers are wrong. This is also given in the Microsoft documentation. 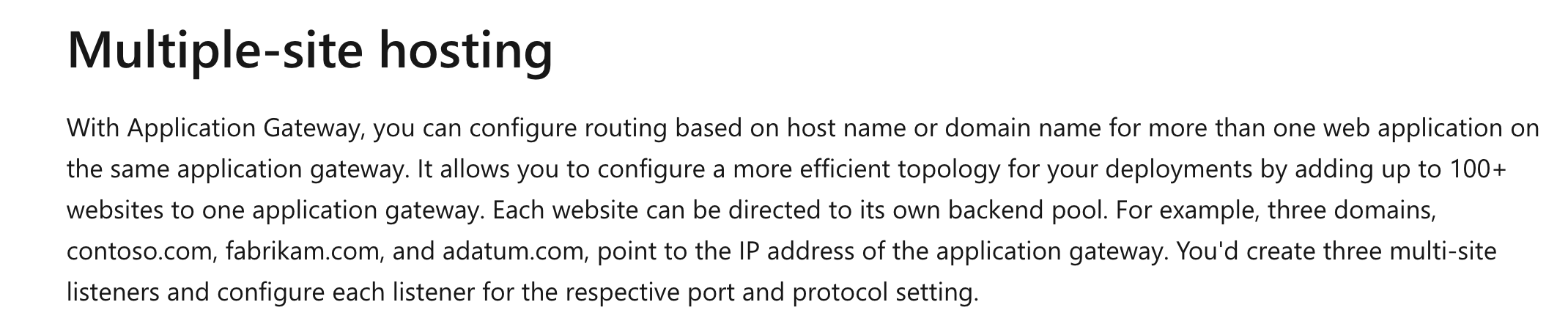
Since this is clearly given in the Microsoft documentation, all other options are incorrect.
For more information on the Azure Application Gateway, please visit the following URL-
You have to implement the security objective for the below case study requirement.
A storage account named whizlabappstore would be created. This storage account only needs to be accessed from the virtual network hosting the virtual machines.
You decide to generate a shared access signature.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – B
You have to create a service endpoint and configure network access to the storage account for this requirement.
For more information on service endpoints, please visit the following URL-
You have to implement the security objective for the below case study requirement.
A storage account named whizlabappstore would be created. This storage account only needs to be accessed from the virtual network hosting the virtual machines.
You decide to enable virtual network peering.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer - B
For this requirement, you have to create a service endpoint and configure network access to the storage account.
For more information on service endpoints, please visit the following URL-
You have to implement the security objective for the below case study requirement.
A storage account named whizlabappstore would be created. This storage account only needs to be accessed from the virtual network hosting the virtual machines.
You decide to enable service endpoints.
Would this fulfill the requirement?
- A. Yes
- B. No
Explanation:
Answer – A
Yes, this would fulfill the requirement.
First, you should add a service endpoint for the virtual network.
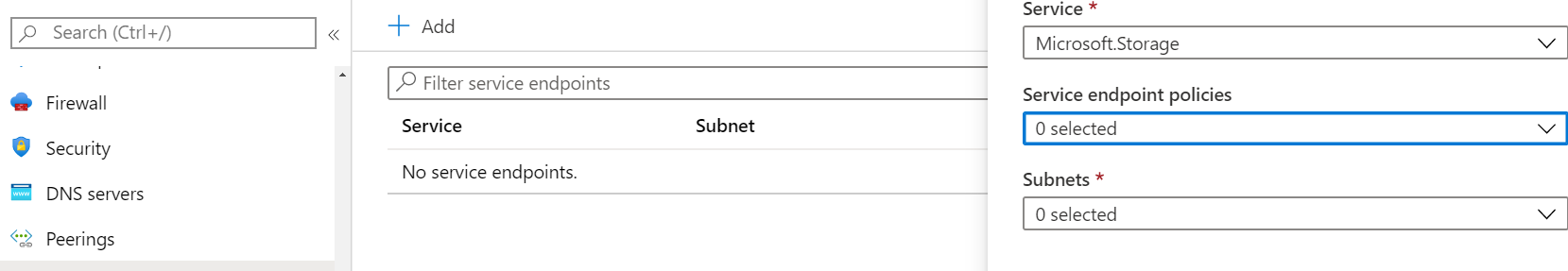
And then ensure to limit the traffic from the virtual network in the storage account.
For more information on service endpoints, please visit the following URL-


